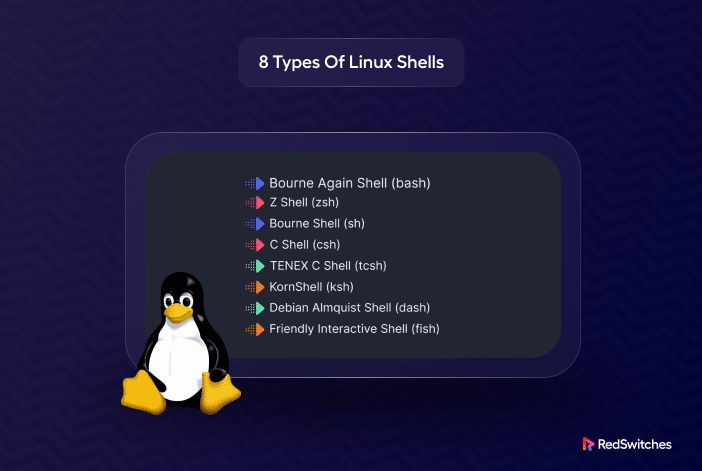
The Bash shell in Linux relies on configuration files, such as .bashrc and .bash_profile, to customize the environment...
RedSwitches Blog
Resources and Insights
The latest industry news, interviews, technologies, and resources.
Common Types of Cyber Attacks and Prevention Techniques
Key Takeaways The top types of cyber attacks include malware, phishing, ransomware, DDoS, SQL injection, IoT attacks, et...
In simple terms, the Temporary failure in name resolution error happens when the system can't...
January 13, 2024 - 5 min
FFmpeg is a free and open-source software utility that provides a collection of libraries and...
January 13, 2024 - 4 min
Welcome to our detailed examination of Redis and Memcached, two robust in-memory data storage solutions....
January 12, 2024 - 19 min
In the fast-paced world of web development, a website's performance is not just a priority—it's...
January 12, 2024 - 16 min
Kubernetes has become a cornerstone in modern software deployment, offering a robust platform for automating...
January 12, 2024 - 9 min
SSH (Secure Shell) is a widely used network protocol in Linux that allows you to...
January 12, 2024 - 4 min
Did you know that, as of 2023, Python has been labeled the most widely used...
January 11, 2024 - 18 min
In the ever-evolving landscape of programming languages, Java stands out as a perennial favorite, demonstrating...
January 11, 2024 - 16 min
If you ask a couple of MySQL database admins to list down their most frequent...
January 11, 2024 - 4 min
The cut command in Linux is a powerful utility for extracting specific text sections from...
January 11, 2024 - 7 min
Guido van Rossum created Python as a versatile programming language in 1991. You can find...
January 11, 2024 - 4 min
Ruby on Rails, often called Rails, is a powerful and renowned web application framework that...
January 10, 2024 - 26 min
Run a simple package manager update, and your screen is filled with rows upon rows...
January 10, 2024 - 5 min
The localhost refused to connect error is a common issue when accessing a service or...
January 10, 2024 - 9 min
In the vibrant programming universe, the distinction between Ruby vs Ruby on Rails often sparks...
January 10, 2024 - 17 min
Ask sysadmins about their worst fears, and you’ll see that “running out of server resources”...
January 9, 2024 - 8 min
The SSH protocol is used for establishing secure connections between remote machines. In modern system...
January 9, 2024 - 14 min
Starting a web development adventure is similar to entering a world where Ruby on Rails...
January 9, 2024 - 16 min
Welcome to the fascinating world of machine learning and artificial intelligence (AI), a dynamic battleground...
January 9, 2024 - 17 min
SSH port forwarding is an essential aspect of securely accessing remote servers. Before going into...
January 8, 2024 - 9 min
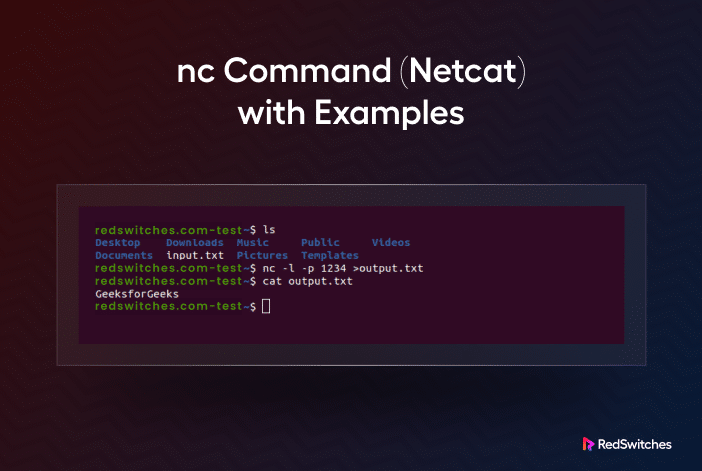
The nc (Netcat) is a command-line utility that uses TCP or UDP protocols to read...
January 8, 2024 - 9 min
In the ever-evolving data science landscape, two titans have consistently stood out in the Python...
January 8, 2024 - 21 min
When it comes to programming languages, Scala and Java are two heavyweights that have left...
January 8, 2024 - 17 min
If your browser keeps redirecting from one URL to another in a loop, preventing it...
January 7, 2024 - 11 min
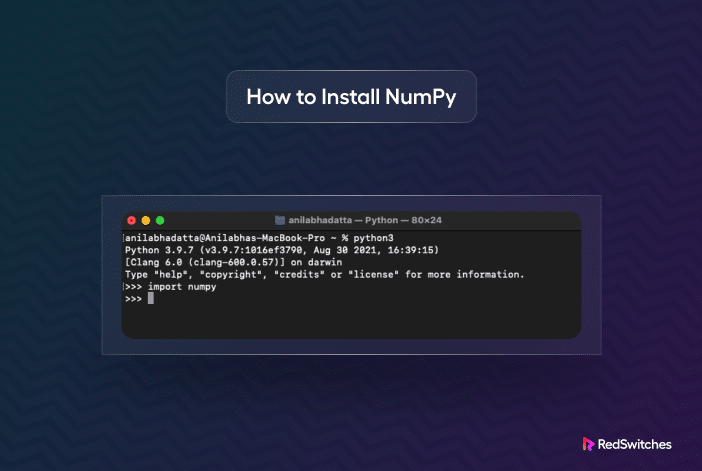
NumPy, short for Numerical Python, is a free and open-source Python library for numerical scientific...
January 6, 2024 - 5 min
Have you ever tried reading someone’s script and figuring out what’s happening? Or, for that...
January 5, 2024 - 8 min
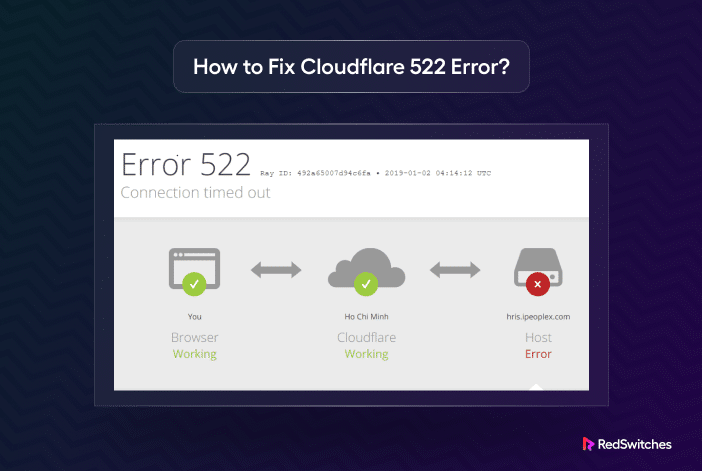
When visitors see the Cloudflare Error 522, they assume the website is unavailable because of...
January 5, 2024 - 8 min
In Linux, directories are the basic component of the file management system. Directories provide a...
January 5, 2024 - 5 min
Drupal and Joomla are two formidable titans in the vast and ever-changing world of content...
January 5, 2024 - 18 min
In the ever-evolving big data landscape, two titans have consistently dominated the conversation: Hadoop vs...
January 4, 2024 - 24 min
Bram Moonlenaar created Vim (Vi IMproved) in the early 1990s as an extended and improved...
January 4, 2024 - 6 min
Want to create a file, open a folder, or execute other programs on your Linux...
January 4, 2024 - 9 min
Linux (and open-source software) has come a long way in providing a robust and versatile...
January 4, 2024 - 7 min
Vim and Vi are commonly used text editor in linux and macOS. Sysadmins and power...
January 3, 2024 - 6 min
Did you know that the first mobile app was launched in 1997 when the Nokia...
January 3, 2024 - 23 min
In the dynamic and ever-evolving programming world, the debate between Perl vs Python is as...
January 2, 2024 - 20 min
Python and Ruby are two prominent programming languages with distinctive strengths and weaknesses. According to...
January 1, 2024 - 17 min
Developed in 1995 by Sun Microsystems, Java is still a preferred development language (and toolkit)...
December 31, 2023 - 5 min
Not sure exactly what you need?
No problem! Our talented engineers are here to help!
We will consult, architect, migrate, manage and do whatever it takes to help your business grow and succeed.