SSH port forwarding is an essential aspect of securely accessing remote servers.
Before going into the details of how to use port forwarding, let’s break down the term SSH Port Forwarding to understand it better.
SSH stands for Secure Shell. It’s a protocol that allows you to securely connect to another computer over a network, typically the Internet. Port forwarding is a technique to redirect network traffic from one port to another. Ports are like numbered doors on a computer, and each service (for instance, web server and email server) often uses a specific port.
Hence, SSH port forwarding (also known as SSH tunneling) securely encrypts the communication between computers, making it more difficult for others to intercept sensitive information.
In this comprehensive introduction, we will explore SSH (or PuTTY) port forwarding to improve network access and security.
Table of Contents
How to Use Port Forwarding in SSH (and PuTTY)
You can use SSH tunneling (port forwarding) in three configurations: local, remote, and dynamic. However, before exploring these , let’s look at the prerequisites for these modes.
Prerequisites
Before we dive into different types and usage of SSH port forwarding, you need the following things in place:
- An SSH Client: You should install an SSH client on your computer. Most Unix-like operating systems have a basic SSH client installed by default. For Windows users, tools like PuTTY provide SSH client functionality.
- Access to a Remote Server: You need access to a remote server you want to connect to using SSH Port Forwarding. Ensure you have the SSH credentials for this server, including the password or SSH key and the username.
How to Use Local Port Forwarding
SSH local port forwarding (tunneling) securely transports the data over the Internet by encrypting it within an SSH session. This tunnel safeguards network traffic on insecure networks.
Here’s how it works:
- Select The Local Port: Start by choosing a localhost port on your machine. Make sure that this port is not used by any service on your machine.
- Use the SSH Client: The SSH client receives data from the user, encrypts it, and sends it to the security checkpoint (the SSH server).
- SSH Server Receives the Data: The SSH server receives the encrypted data, decrypts it, and then forwards it to the destination service, typically on the same machine as the SSH server or within its local/internal network.
- The Destination Service: This could be a web server, database, or any other secure service you want to access on the destination.
- The Response Path: The response from the destination service is sent back to the SSH server, which encrypts it and sends it back to the SSH client on the source. The client then decrypts the response and sends it to the local application via (local) port.
This process effectively creates a secure “tunnel” through which data can move back and forth. The best part is that this tunnel works even if the intermediate route between the source and destination is not trustworthy.
This secure route makes SSH tunneling the preferred way of accessing remote network services or bypassing network restrictions securely.
Accessing remote servers that aren’t visible on the network is a critical use case of SSH port forwarding. In this scenario, the source system sends data through a secure tunnel to the SSH server, which then redirects it to the destination web server. The underlying tunneling mechanism is invisible during this process, and you can directly see the target machine and services.
Local Port Forwarding with OpenSSH
This is the most common form of port forwarding in Linux environments.
When using local port forwarding with OpenSSH on a Linux system, you must provide the following information to set up SSH port forwarding efficiently.
- Source (the starting point of the tunnel)
- Destination port number(s)
- Location of the destination server (This can be an IP address or a hostname).
Here’s the basic syntax for creating a local port forward using the -L flag with the ssh command:
# ssh -L local_port:destination_server_ip:remote_port ssh_server_hostname
Let’s break down this syntax into its components:
- ssh: This is the native Linux SSH utility that the system uses for opening a secure connection to the distant SSH server.
- -L local_port:destination_server_ip:remote_port: The -L flag takes the local port information and the destination server information. The local SSH client directs data forwarding from a local port on your machine to a designated port on the remote server.
- ssh_server_hostname: The hostname or IP address of the remote SSH server that you want to connect to the specified port.
Let’s run the following SSH port forwarding scenario that uses the following command:
# ssh -L 5901:184.107.122.14:4492 [email protected]
In this example, all data sent to port 5901 on your source machine will be seamlessly forwarded to port 4492 on the remote server, situated at the IP address 184.107.122.14.
Local Port Forwarding with PuTTY
You can use PuTTY to leverage local port forwarding in Windows. It is a user-friendly SSH client designed for Windows and offers a simple way of securely connecting to a remote server and accessing services through an encrypted tunnel.
Using PuTTY, you can configure the local machine to forward specific ports to the remote server. This ensures that sensitive data is encrypted during transmission, enhancing security, especially when dealing with untrusted networks like the Internet.
Follow these steps to use PuTTY to establish local port forwarding in the Windows environment:
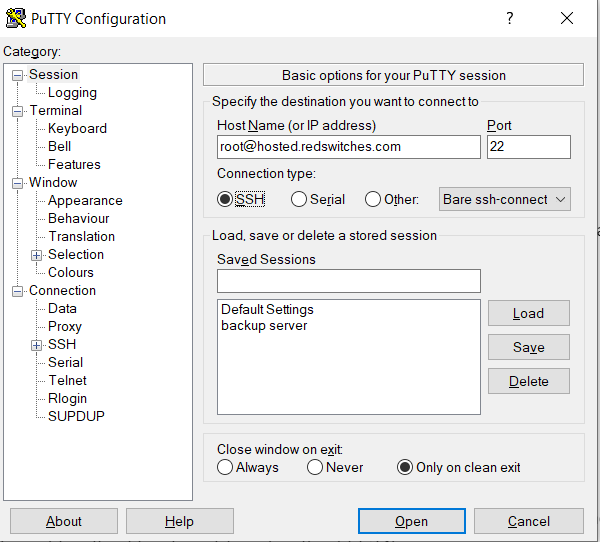
1. Launch PuTTY and access the Sessions screen to input the destination SSH server’s hostname, IP address, and port number. For this demonstration, we’ll enter [email protected] and port number 22.
2. Add the hostname of the SSH server you wish to access remotely.
3. Use the Category list on the left to go to Connection > SSH > Tunnels.
4. Select Local to choose the type of the SSH port forward.
Follow these steps to set up SSH forwarding/tunneling in PuTTY:
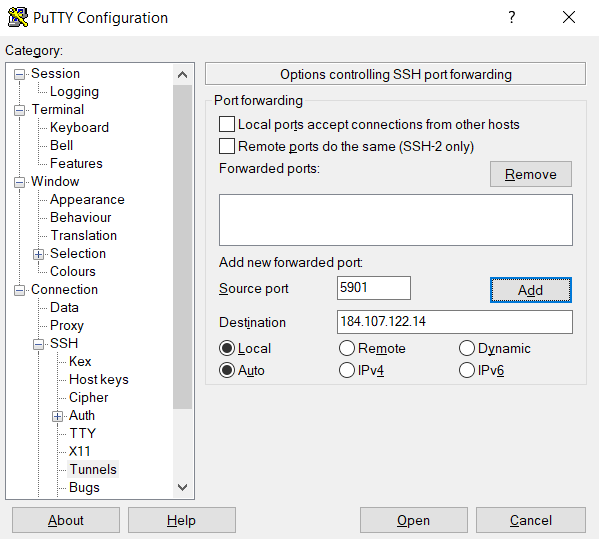
- Enter the local port number in the Source port field.
- In the target box, provide the target address and port number in the following format: destination_server_ip:remote_port. For this demonstration, we’ll use: source port: 5901, Destination: 184.107.122.14:4492.
- Confirm the details are accurate and click Add.
5. At this point, the connection’s parameters have now been set up. Now click Open to start the local SSH port forward.
How to Use Remote Port Forwarding
SSH remote port forwarding, or reverse SSH tunneling, is a process that allows a user to expose a local service to a remote server.
The term reverse indicates that the traditional data direction (source to destination) is flipped. So, instead of initiating a connection from your local machine to a remote server, as is typical in SSH communication, you’re allowing the remote systems to initiate a connection back to your local machine.
This process is essential when you wish to allow remote access to your local services. This tunnel can work across firewalls and network restrictions.
Let’s see how to use remote port forwarding with OpenSSH and PuTTY.
Remote Port Forwarding with OpenSSH
Facilitating remote port forwarding with OpenSSH involves using the following command syntax. Note that the -R flag with the SSH command indicates the reverse connection:
# ssh -R remote_port:localhost:local_port ssh_server_hostname
For instance, in the following command, we have instructed the hosted.redswitches.com remote server to send all incoming connections on port 8080 to a local resource on our machine listening at port 5534:
# ssh -R 8080:localhost:5534 [email protected]
In this setup, users who have access to the hosted.redswitches.com SSH server can effortlessly use resources on this server.
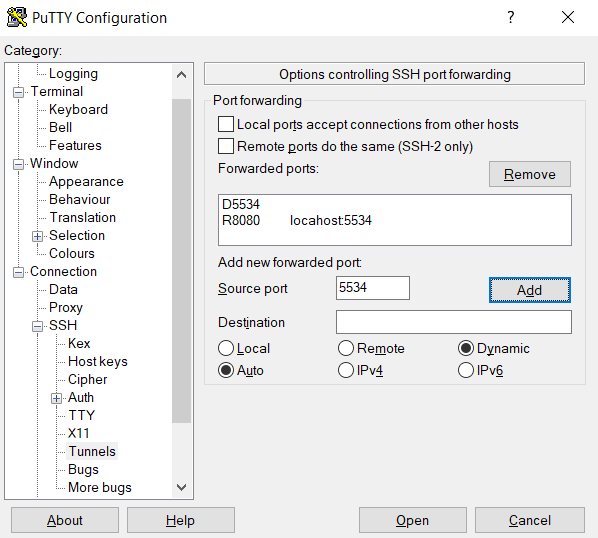
Remote Port Forwarding with PuTTY
Implementing remote port forwarding with PuTTY involves the following steps:
1. Launch PuTTY and enter the SSH server’s IP address and port in the Sessions screen.
2. Add the hostname of the SSH server for the remote SSH tunneling session.
3. Navigate to Connection > SSH > Tunnels using the Category list on the left.
4. Choose Remote to specify the type of SSH port forward.
Follow these steps to establish a remote SSH tunneling connection:
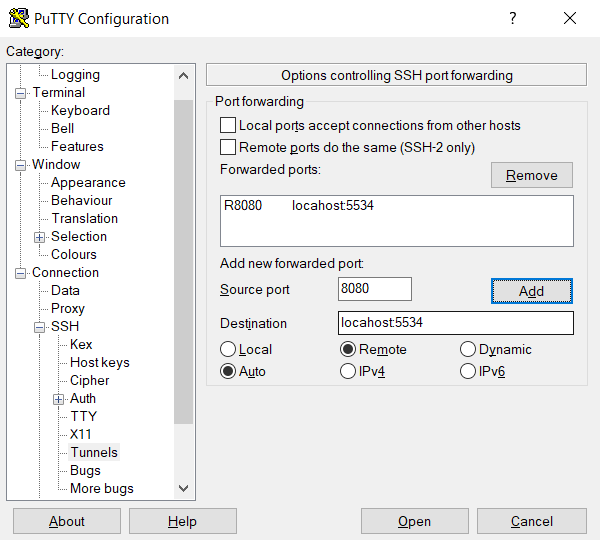
- Choose Remote for SSH port forwarding.
- Enter a remote port (e.g., 8080) in the Source port field.
- Specify the target address and port (e.g., localhost:5534) in the Destination box.
- Verify the details and click Add.
5. Click Open to start the remote SSH port forward.
Now, remote users can connect to our SSH server at port 8080, which will redirect them to the local system at port 5534.
How To Use Dynamic Port Forwarding
SSH dynamic port forwarding is an advanced form of port forwarding using the Secure Shell (SSH) protocol, enabling more flexible and automatic forwarding of network traffic.
It is sometimes called SOCKS proxying because it uses the SOCKS protocol. Here’s how it works:
- Select the Dynamic Port: Choose a local port on your machine. This port will act as a listening point for the SOCKS proxy requests.
- SSH Client Configuration: Configure your SSH client to create a dynamic port forwarding tunnel. This instructs the local SSH client to listen to the chosen local port and forward traffic through the SSH tunnel.
- SOCKS Proxy: The local SSH client becomes a SOCKS proxy server. Now, you can set up local applications to use this proxy. The network requests of these apps go through the SOCKS proxy on the specified local port.
- Traffic Routing: The SSH client takes the applications’ requests and sends them through the SSH tunnel to the SSH server. The server decides where to send these requests based on their destination addresses.
- Response: Responses travel back to the SSH server, through the tunnel to your SSH client, and then to the original application making the request.
The primary benefit of SSH dynamic port forwarding is its flexibility, which results in the following:
- Automatic Routing: No need to set up individual port forwards; applications can dynamically determine destinations.
- Privacy and Security: It acts as a secure, encrypted proxy for Internet browsing, ideal for monitored or restricted access situations.
- Easy Configuration: Once set up, any SOCKS proxy-supporting application can use the SSH tunnel without specific configurations for each service.
Dynamic Port Forwarding with OpenSSH
To use dynamic port forwarding with OpenSSH, you must first create a local SOCKS proxy on your computer by running the ssh command with the –D flag:
# ssh –D local_port ssh_server_hostname
For example, the following command sets up a local SOCKS proxy at port 5534 on your computer:
# ssh –D 5534 [email protected]
This enables you to configure a local resource, such as a browser, to utilize port 5534. The SSH connections made for the designated port are then used to redirect all traffic from that resource.
Dynamic Port Forwarding with PuTTY
To enable dynamic port forwarding with PuTTY, follow these steps:
- Enter the target SSH server’s port number and hostname or IP address in the main PuTTY Sessions screen.
- Add the hostname of the SSH server specifically for dynamic port forwarding.
- Utilize the Category list to navigate to Connection > SSH > Tunnels.
- Choose Dynamic to specify the type of SSH port forward.
- Locate the options for establishing dynamic port forwarding.
- Enter the dynamic port number in the Source port field (e.g., 5534). The SOCKS proxy server will use this port on your local machine to forward traffic dynamically.
- Verify the information and click Add.
- The parameters for the connection are now configured. Select the Open option to initiate dynamic SSH port forwarding.
- For dynamic forwarding to function, you must configure and enable each application to utilize the SOCKS proxy server.
Conclusion
SSH Port Forwarding is a robust feature that enhances your network security and enables access to remote services. Whether you’re using OpenSSH on Linux systems or PuTTY on Windows, the ability to forward ports securely is a handy skill for system administrators and developers.
RedSwitches offers the best dedicated server pricing and delivers instant dedicated servers, usually on the same day the order gets approved. Whether you need a dedicated server, a traffic-friendly 10Gbps dedicated server, or a powerful bare metal server, we are your trusted hosting partner.
FAQs
Q. What is SSH Port Forwarding, and how does it work?
SSH port forwarding, also known as SSH Tunneling, allows you to securely forward network ports from your local machine to a remote machine over an SSH connection. This process creates a tunnel for data transmission, encrypting the data and bypassing unencrypted protocols, ensuring secure communication even over the public Internet.
Q. Is SSH port forwarding secure?
SSH port forwarding is secure as it encrypts the data transmitted between your local machine and the remote server, preventing unauthorized access and ensuring privacy over a public IP address.
Q. Can I use SSH port forwarding for file transfers?
Absolutely. SSH port forwarding can be used for secure file transfers using tools like SCP or SFTP, which utilize the secure channel established over an SSH connection to transmit files.
Q. Are there any alternatives to SSH port forwarding?
While VPNs and dedicated proxy servers are alternatives, SSH port forwarding is a lightweight and secure option for many use cases, especially when working within a private network or executing remote commands on a server machine.
Q. Can I use SSH port forwarding for remote desktop access?
SSH port forwarding can securely access remote desktops, such as with the VNC protocol, by forwarding the ports to the remote host.
Q. What are the types of SSH port forwarding?
There are mainly two types: local port forwarding and remote forwarding. Local forwarding allows you to forward a port from the client machine to the server machine. In contrast, remote forwarding enables forwarding from the server to the client, which is valid in scenarios like exposing local network services to a public network.
Q. How do I maintain a session active for SSH port forwarding?
To keep a terminal session active, use tools like Screen or tmux, which allow the SSH connection and port forwarding to persist even if the client host is disconnected.
Q. How can I forward a range of ports using SSH?
Forwarding a range of ports can be done by specifying the range in the SSH command for local and remote forwarding. This is particularly useful when multiple network services or sessions must be accessed or maintained concurrently.
Q. Can SSH port forwarding be configured for a remote machine with a dynamic IP?
Yes, SSH port forwarding can work with dynamic IP addresses. However, network configuration might require more attention, as the public IP address of the remote host can change. Using a dynamic DNS service can simplify this process.
Q. How do I set up SSH port forwarding with a single command?
You can set up SSH port forwarding using a single command line in your terminal. The specific command depends on whether you’re setting up local or remote forwarding and the particular ports and addresses involved.