Key Takeaways
Here are the Key Takeaways:
- Recognize how different hosting types (shared, VPS, dedicated, cloud) fit various needs.
- Choose hosting that aligns with your website’s size, traffic, and performance needs.
- Opt for hosting that offers robust security features like firewalls, SSL/TLS encryption, and DDoS mitigation.
- Implement and maintain a schedule for regular, automated backups to safeguard your data.
- Keep all software up-to-date to protect against vulnerabilities and improve performance.
- Use complex passwords and implement Two-Factor Authentication (2FA) for better security.
- Set up and maintain strong firewalls to act as a barrier against various online threats.
- Implement intrusion detection systems and real-time monitoring for proactive threat detection.
- Follow the principle of least privilege, giving users only the access they need.
- Adhere to industry-specific data handling and processing regulations to avoid legal issues.
Securing your virtual domain is more important than ever. The internet is vast, and each website is a small realm of data and offerings. Imagine your website as a strong fortress in the internet wilderness. Potential attackers constantly watch it. Imagine this: the secret to protecting its walls and riches is not in magic but in a practical method. It is a regular backup.
We explore web hosting security in this article. We emphasize the critical role of backups in protecting your digital stronghold. We will discuss secure hosting services as well.
We explore web hosting security in this blog. We emphasize the critical role of backups in protecting your digital stronghold. Come along as we reveal the top 10 secure web hosting security practices. Each one can powerfully defend against online threats. It’s time to strengthen your defenses. Arm yourself with info. And make sure your virtual kingdom is impenetrable against online assaults.
- Key Takeaways
- What is Web Hosting?
- Types of Website Hosting
- Features of Web Hosting
- What is Secure Hosting
- Why is Secure Web Hosting Important?
- Consequences of Less Secure Web Hosting
- Six Key Elements for Your Website’s Success
- What Hosting Security Features to Look for in Web Hosting Providers
- 10 Best Web Hosting Security Practices
- Continual Updates for Software
- Robust Authentication Systems
- Setting Up a Firewall
- Continual Testing for Recovery and Backups
- Malware Inspection and Elimination
- Hosting Secure TLS/SSL Encryption
- Tracking and Identifying Intrusions
- The Principle of Least Privilege and Access Control
- Auditing and Compliance With Security
- Inform and Prepare Users
- Five Additional Best Secure Hosting Tips
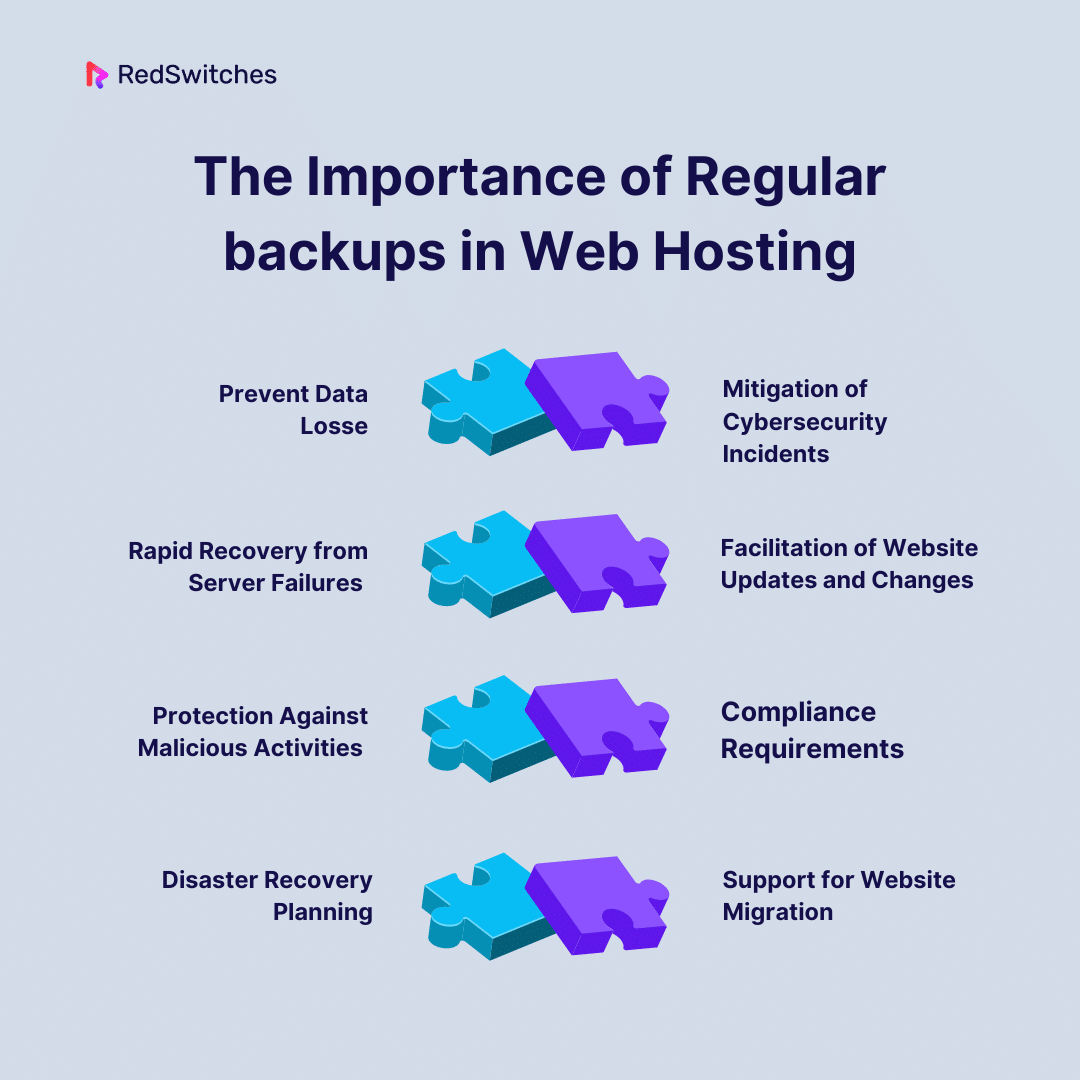
- The Importance of Regular Backups in Web Hosting
- Hosting Secure: Prevent Data Loss
- Hosting Secure: Mitigation of Cybersecurity Incidents
- Hosting Secure: Rapid Recovery from Server Failures
- Hosting Secure: Facilitation of Website Updates and Changes
- Hosting Secure: Protection Against Malicious Activities
- Hosting Secure: Compliance Requirements
- Hosting Secure: Disaster Recovery Planning
- Hosting Secure: Support for Website Migration
- Conclusion
- FAQs
What is Web Hosting?
Credits: Freepik
A hosting provider hosts a website when they set up space on a web server for the website’s data files. Code, photos, and other data that make up a website can be seen online, thanks to web hosting. All of the websites you have ever visited are stored on servers.
The type of hosting determines how much space a website is allotted on a server. Shared, dedicated, VPS, and reseller hosting are the four primary categories. The server uses a certain type of technology. It offers a certain degree of management and extra services. These things set it apart.
There are numerous web hosting alternatives to suit various requirements and tastes. Shared hosting is affordable for small websites. Several websites share resources on a single server.
Dedicated hosting offers better performance and control. But, it costs more because it dedicates a whole server to one user. Also, cloud hosting uses virtualization. It spreads website data across many servers. This ensures scalability and dependability.
Websites are essential for personal, business, and informational activities. So, it’s vital to grasp the basics of web hosting. To guarantee a flawless online presence and great user experience, choose the right hosting plan and provider. Consider performance, security, and support.
A customer with dedicated server hosting has complete control over the server, which improves security, speed, and website customization possibilities.
To guarantee a flawless online presence, it’s imperative to find a reputable provider for server hosting, whether you go with dedicated server or shared.
We will discuss the website hosting types in our next section.
Types of Website Hosting
After discussing the definition, let’s discuss the types of web hosting.
Shared Hosting
Several websites share the same server resources. These include disk space, bandwidth, and processing power. They share these resources when they use shared hosting. For small to medium-sized websites with moderate traffic, it’s an affordable solution. Conversely, Sharing a server with other websites can hurt a website, even if it is cheaper.
VPS Hosting
A compromise between dedicated and shared hosting is provided by VPS hosting. Every website can access a dedicated virtual server space and resources with a VPS. It offers more control and customization than shared hosting. Companies needing a scalable solution often choose it.
Dedicated Web Hosting
Users can get a whole physical server for their website(s) when they choose dedicated hosting. Maximum performance, security, and customization are provided with this option. Dedicated hosting is for large websites. They have big resource needs or high traffic.
Cloud hosting
Cloud hosting uses the combined power of several networked servers to distribute website content dynamically. Because of its scalability, users can adjust resource levels in response to demand. Websites with different traffic volumes can benefit from cloud hosting, renowned for its dependability.
Features of Web Hosting
Credits: Freepik
Web Hosting comes with various features that cater to different needs, whether it’s for a personal blog, a business website, or an e-commerce platform. Here are some key features commonly offered by web hosting services:
Disc Space
The hosting company provides the space. It holds all the files, databases, photos, and other website data. It’s called disc space.
Enough disc space is essential to support the material on your website and guarantee seamless operation. The size and type of your website determine the amount of space needed.
Bandwidth
The quantity of data that can be sent over a predetermined length of time between your website’s visitors is known as bandwidth.
Sufficient bandwidth is necessary to manage website traffic. Too little bandwidth causes slow load times. It can even cause outages in peak times.
Registration of Domain Names
Some hosts let you register and control your website’s domain through their interface.
It is easier to maintain your online identity. This is thanks to convenient domain management. It includes domain transfers, DNS changes, and renewals.
This article will help you if you want to know more about DNS Records, their types, and how they work.
Email Hosting
You may set up and maintain email accounts linked to your domain with email hosting services.
Using email addresses with your domain improves your image. For example, [email protected]. Features like webmail interfaces and spam filtering may be provided by hosting companies.
Uptime Guarantee
The proportion of time that your website is available and the hosting servers are running is known as uptime.
A higher uptime percentage indicates better dependability. Hosting companies often provide uptime guarantees. They do this to reassure customers that their websites will be accessible.
What is Secure Hosting
Credits: Freepik
Secure Hosting guarantees data privacy, availability, and integrity. It offers a stable and safe environment for hosting websites and online apps.
Protecting against cyber risks and unauthorized access requires many security measures. It also needs processes to put them in place.
The aim of secure hosting is to build a digital fortress. It will protect private data. It will stop data breaches and keep websites running well.
The use of data encryption is a basic component of safe hosting. Data is encoded during both transmission and storage using encryption techniques. Encryption preserves data confidentiality. It makes data unreadable to unauthorized parties. It guarantees a secure connection between clients and servers.
Secure hosting requires strong firewalls and intrusion detection systems. As barriers, firewalls monitor and regulate network traffic to stop illegal access. Intrusion detection systems offer an extra defense against malicious activity. They identify and respond to security risks at the same time.
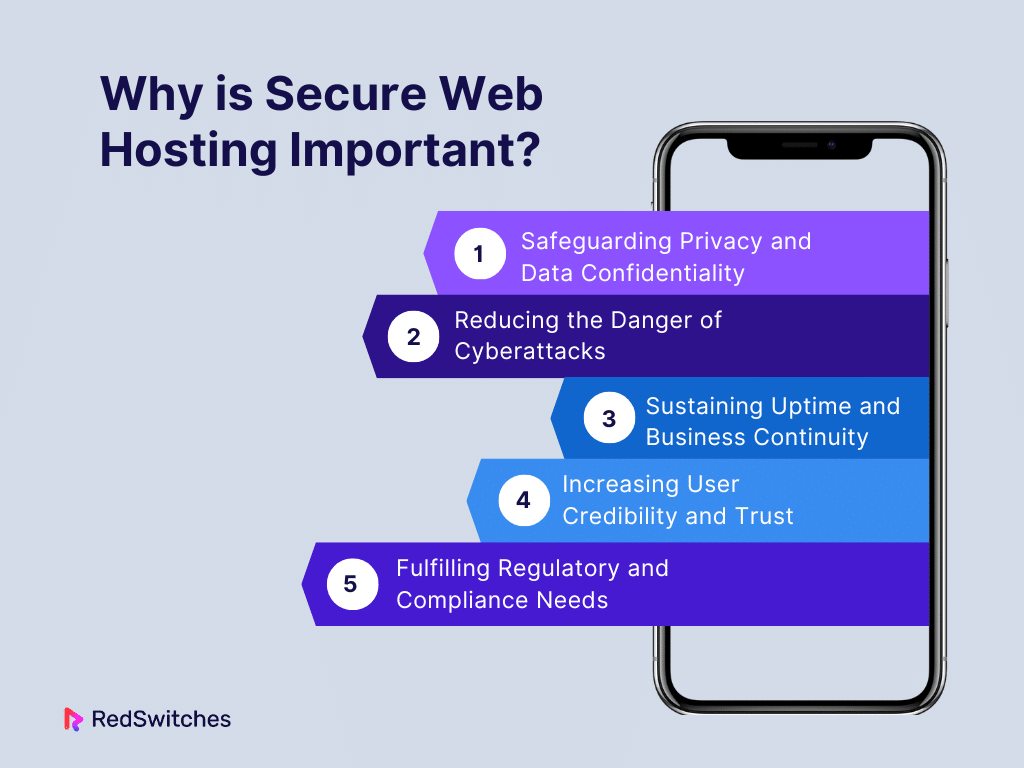
Why is Secure Web Hosting Important?
Secure web hosting is crucial because it protects your website and visitors from cyber threats. Here’s why it’s important:
Safeguarding Privacy and Data Confidentiality
This is the era of digital technology. Sensitive data is always moving across the internet. So, privacy and confidentiality protection are critical. Secure web hosting is vital. It protects user data from breaches and access. Secure hosting guarantees that critical information is kept private. It does this by using encryption and strict access controls. This builds user trust in the hosted website.
Reducing the Danger of Cyberattacks
Cyber threats abound online, ranging from sophisticated hacking attempts to virus attacks. Secure web hosting is one of the best defenses against these attacks. Adding intrusion detection systems, firewalls, and frequent security audits can help hosting companies. They can quickly find and fix security flaws. This reduces the risk of cyberattacks. These attacks could endanger the integrity of the hosted website and its data.
Sustaining Uptime and Business Continuity
Companies and organizations rely on their internet presence. So, they need to keep services running. Uptime and business continuity are greatly enhanced by secure web hosting.
Hosting companies may guarantee that websites stay up despite unanticipated occurrences. They do this by investing in reliable backup protocols. They also invest in disaster recovery plans and robust server systems. This lowers downtime and eliminates the possibility of online activities being disrupted.
Increasing User Credibility and Trust
Any internet business that wants to succeed must first build user trust. Secure web hosting increases a website’s trustworthiness. It shows dedication to protecting user information. It keeps a safe online environment. Users are more willing to interact. They will share sensitive info on a website they believe is secure. This is especially true. It has features like SSL certificates for encrypted connections. This promotes a reliable and pleasant online experience.
Fulfilling Regulatory and Compliance Needs
Strict rules control how data is handled in some businesses. They focus on compliance and regulation and sensitive data. Businesses and organizations must follow these standards. So, they need secure web hosting. Following industry guidelines ensures the hosting meets legal requirements. This protects against legal trouble.
Secure web hosting is crucial for safeguarding your data, upholding the integrity of your website, and inspiring trust in your visitors—especially when using a dedicated server. It is an investment in your website’s dependability and long-term success.
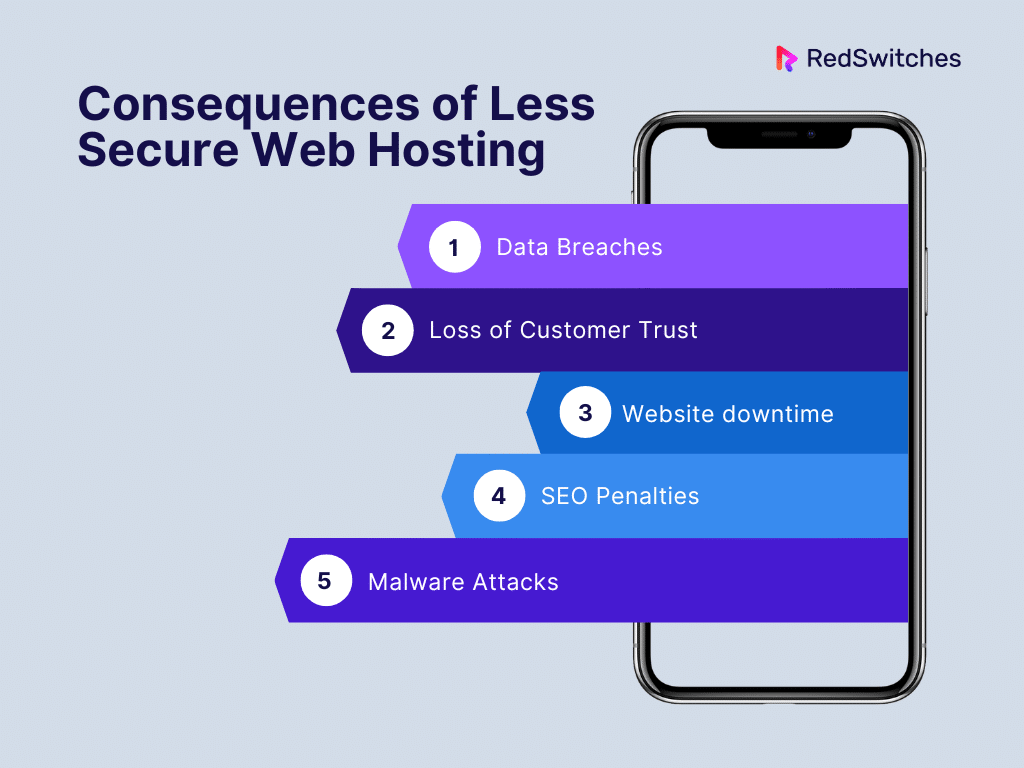
Consequences of Less Secure Web Hosting
Using less secure web hosting can have serious consequences, impacting both the website owner and the users. Here are some potential risks:
Data Breaches
Unauthorized access is a bigger risk in less secure hosting setups. They can lead to data breaches. Cybercriminals may use weaknesses to get private information. This includes financial records or sensitive user data. Beyond just monetary damages, a data breach can harm your brand.
Loss of Customer Trust
Following a security incident, customer trust frequently suffers the most damage. Users give websites their personal information. A breach can undermine their confidence. A hacked website casts doubt on user information security. It could cost you business clients and harm your reputation.
Website downtime
Distributed Denial of Service (DDoS) attacks are more likely to occur in less secure hosting setups. These attacks can overload your website’s resources. This can cause downtime and make it unavailable to users. Regular outages affect your search engine rankings negatively in addition to annoying visitors.
Be sure to read our comprehensive guide, which includes 8 proven tactics you can try right now to prevent DDoS attacks.
SEO Penalties
Safe websites are ranked higher by search engines. Search engines may penalize your website. They will give it a lower rating if it was compromised due to less secure hosting. This may hurt your web presence. It will reduce natural search traffic and potential clients.
Malware Attacks
Hosting environments with lower levels of security are more vulnerable to malware attacks. Malicious software can steal user data. It can also interfere with websites. It can even inject malicious code. Malware infections can harm your website’s security. They can also harm its visitors and its reputation.
Selecting dedicated server hosting greatly reduces these dangers and gives your website a more controlled and safe environment. It’s a preventative measure to preserve client confidence, protect your internet reputation, and guarantee the accuracy of your data.
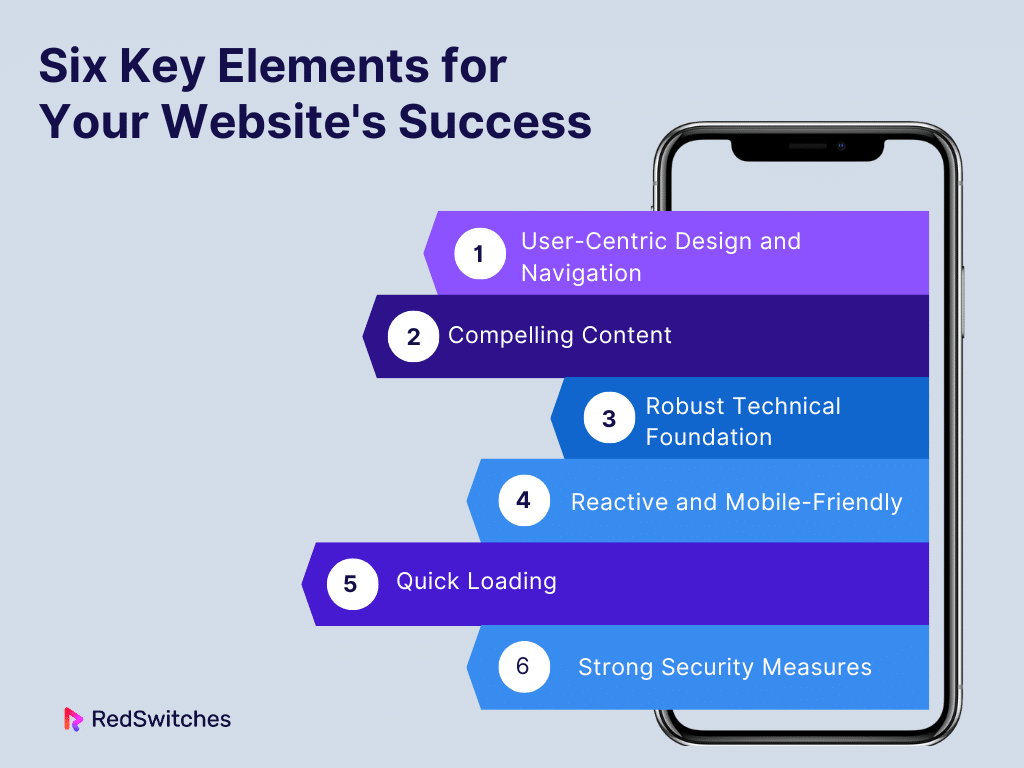
Six Key Elements for Your Website’s Success
In this section, we will discuss six key elements for the website’s success concerning hosting secure.
User-Centric Design and Navigation
A website’s user-friendly design and navigation are essential components for its success. An intuitive navigation system is essential for users to navigate a website easily. A logical layout, well-organized content, and clear menus are crucial elements that help consumers locate information quickly.
In today’s digital world, responsive design is equally important since it can adapt to the variety of devices users use to visit websites. Better engagement and satisfaction are fostered by a responsive website, which guarantees a consistent and pleasurable experience. Furthermore, optimizing loading speed is critical because poorly designed pages can result in high bounce rates and a bad user experience.
Improved loading times can be achieved using techniques like content delivery networks (CDNs), browser caching, and picture optimization. Moreover, website accessibility is an important factor. In addition to expanding the audience, ensuring the website complies with online accessibility guidelines and offers alternative language for images enables individuals with impairments to access it, which also complies with ethical and legal requirements.
Compelling Content
Another essential component for the success of a website is compelling content. Making good and relevant information is the key. It draws in and holds the target audience. Sustained engagement requires regular content updates to make it relevant to users’ needs. Visual appeal is crucial. Adding eye-catching components, like clear photos, movies, and infographics, improves the user experience.
Building trust and recognition among visitors is key. It comes from consistent branding in speech and visual identity. This builds a strong and memorable brand. Strategically placing calls-to-action (CTAs) on the website helps users through the conversion funnel. It entices them to buy something, complete a form, or sign up.
Robust Technical Foundation
A solid technical base is the cornerstone of any successful website. Security precautions are essential for preserving confidence and safeguarding user data. To protect sensitive data, use secure protocols (like HTTPS). Also, upgrade software often and use encryption.
Increasing a website’s exposure in search results requires Search Engine Optimisation or SEO. You need thorough keyword research. You also need on-page optimization. And, you need to produce excellent, shareable content. To increase organic traffic and the website’s discoverability, SEO is essential.
Performance and scalability are other vital factors. Consider scalability. It ensures your website can grow. It prevents performance issues as traffic and content increase. Sustaining optimal performance and dependability requires regular monitoring and optimization of server resources.
A successful website needs a mix of user-centric design. It also needs compelling content and a solid technical base. These things offer users a satisfying online experience.
Reactive and Mobile-Friendly
A responsive, mobile-friendly design is critical. More people visit websites from various devices. Make sure your website displays well on PCs, tablets, and smartphones. It should adjust smoothly to many screen sizes and resolutions.
Quick Loading
A website’s speed significantly impacts search engine rankings and user happiness. Use content delivery networks (CDNs). Use browser caching and image compression. These will maximize the speed of your website. A website that loads quickly enhances user experience and lowers bounce rates.
Strong Security Measures
Your website’s security and that of its visitors are of utmost importance. Use strong security measures. These include SSL encryption, regular audits, and secure logins. Protecting confidential information and ensuring a safe online journey build visitor confidence. They also help your website last.
By putting these components in place—especially on a dedicated server—your website’s foundation for success is strengthened and its security, performance, and dependability are improved.
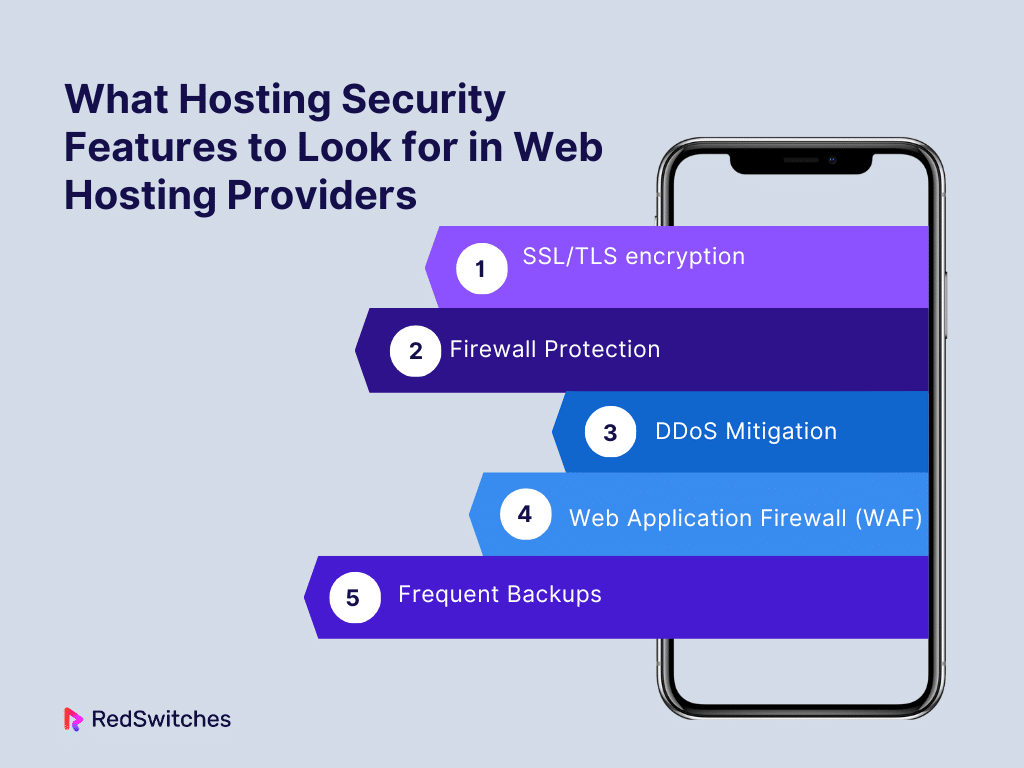
What Hosting Security Features to Look for in Web Hosting Providers
Let’s discuss the security features to look for hosting secure for your website.
SSL/TLS encryption
SSL/TLS encryption is a cryptographic technique. It creates a secure channel between a user’s web browser and the hosting server. It uses public and private keys to encrypt data. This guarantees the privacy of sensitive data in transit. It includes login passwords, personal info, and financial transactions. SSL/TLS certificates authenticate the server’s identity. They give customers peace of mind. The certificates show that they communicate with a reputable and secure website.
Firewall Protection
A firewall examines inbound and outgoing network traffic. It acts as a barrier between a website’s internal network and the outside world. It blocks unwanted access. It filters out harmful data packets by enforcing access control policies. These policies are based on preset security criteria.
Firewalls offer layered security against cyber threats. They can be installed at several levels. These include network, host-based, and application-layer firewalls.
If you’re about to select 2024’s best internet security protocol, this guide based on the difference between SSL vs TLS will surely help you.
DDoS Mitigation
DDoS attacks try to overwhelm a website by sending a large amount of traffic at once. We use hardware, software, and networks in DDoS mitigation. They identify and deflect these attacks.
Sophisticated DDoS mitigation systems stop malicious traffic from bothering legitimate users. They do this by studying incoming traffic to find anomalies. Then, they redirect or block the malicious traffic.
Web Application Firewall (WAF)
A Web application firewall (WAF) is a special security solution. It is made to defend online applications from many cyber threats. It intercepts and examines HTTP communication. This is the data between users and online apps at the OSI model’s application layer.
WAFs use pre-established security rules and algorithms. They find and stop common web attacks, like XSS and SQL injection. They also stop other bad actions that exploit web app flaws.
Frequent Backups
An effective disaster recovery plan must include regular and automated backups. The backups include databases, files, and configurations. They capture the complete state of a website at a certain time.
Backups provide quick and reliable restoration. They help when data is lost, systems fail, or security events happen. They reduce downtime and prevent data loss.
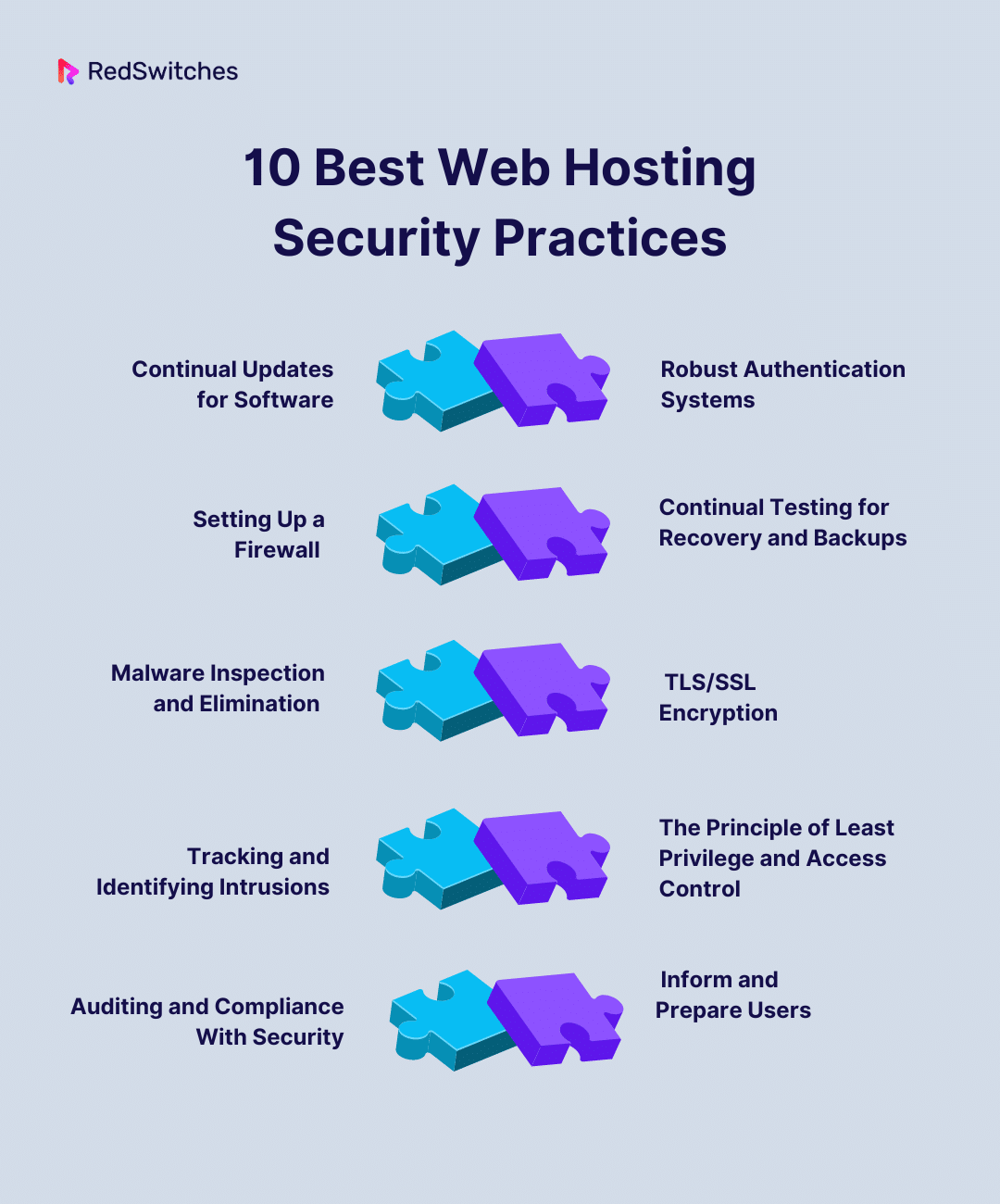
10 Best Web Hosting Security Practices
We just discussed the security features of web hosting providers. Now, we will talk about the 10 best practices for secure hosting.
Continual Updates for Software
You must update all software often for hosting secure. This includes content management systems, web servers, and operating systems. Software updates frequently include security patches. The patches fix known vulnerabilities, reducing the chance of them being exploited by hostile actors. You may improve the general security of your hosting environment by keeping up with upgrades.
Robust Authentication Systems
To prevent unwanted access, implement robust authentication procedures for hosting secure. Demand complex passwords. They should have a mix of digits, special characters, and capital and lowercase letters. Incorporate Two-Factor Authentication (2FA) to bolster security even more.
Strong authentication lessens the chance of credentials being hacked. This lowers the chance of unauthorized access to hosting accounts.
Setting Up a Firewall
This practice is essential for hosting secure. It regulates incoming and outgoing network traffic. It also configures and maintains a strong firewall. In addition to preventing unwanted access, firewalls serve as a barrier against different online risks. Adequately configured firewalls are an important line of defense. They improve the security of your hosting environment.
Continual Testing for Recovery and Backups And for Hosting Secure
Make routine automated backups of the setups and data on your website. Automatic backups act as a buffer against data loss or security breaches. Furthermore, periodically test the recovery process to ensure backups can be restored successfully, reducing downtime and guaranteeing a speedy recovery procedure.
Malware Inspection and Elimination for Hosting Secure
Use automated malware detection tools to periodically check the files and codes of your website for dangerous software. There should be automated removal procedures in place to get rid of any malware that is found quickly. It is essential to perform proactive virus scanning to keep your website secure and intact.
Credits: Freepik
Hosting Secure TLS/SSL Encryption
To secure data transmission between users and the server, utilize SSL/TLS encryption. Sensitive data, including financial transactions and login credentials, is encrypted using this cryptographic technique to guarantee secrecy. Obtaining and setting up SSL/TLS certificates creates a secure connection, fosters user confidence, and further validates the server’s identity.
Tracking and Identifying Intrusions for Hosting Secure
Use intrusion detection systems and monitoring tools to monitor network traffic and server records. These technologies enable the quick discovery of possible security incidents by offering anomaly detection and real-time information. Prompt reactions to threats are essential for reducing risks and maintaining a secure hosting environment.
The Principle of Least Privilege and Access Control
This principle, integral to robust security practices for Hosting Secure, follows the least privilege concept and imposes strict access constraints. Give users and processes the minimal amount of access required to complete their tasks. Review and change access permissions regularly to reduce security vulnerabilities that may arise from giving people more privileges than they need.
Auditing and Compliance With Security for Hosting Secure
To ensure the highest level of security, adhere to industry security guidelines and participate in frequent security audits. Certifications like ISO 27001 or SOC 2 compliance demonstrate a dedication to upholding high-security standards. Users can feel more secure about the safety of their data when regular audits are conducted to evaluate the efficacy of security measures and guarantee continued compliance.
Inform and Prepare Users
Give security awareness training to all users, including administrators and developers. Inform them about typical security risks, the value of strong passwords, and secure online conduct. By encouraging a culture of alertness against potential threats, security-conscious users play a critical role in enhancing the Hosting Secure environment’s overall security posture.
Users will feel more confident if you implement these practices, which also safeguard your data and the integrity of your website. Consider putting these strategies into practice to strengthen your hosting environment and guarantee a dependable and safe online presence if you’re looking for a dedicated server hosting solution that puts security first.
Also, read the top 10 Cybersecurity frameworks to reduce cyber risk.
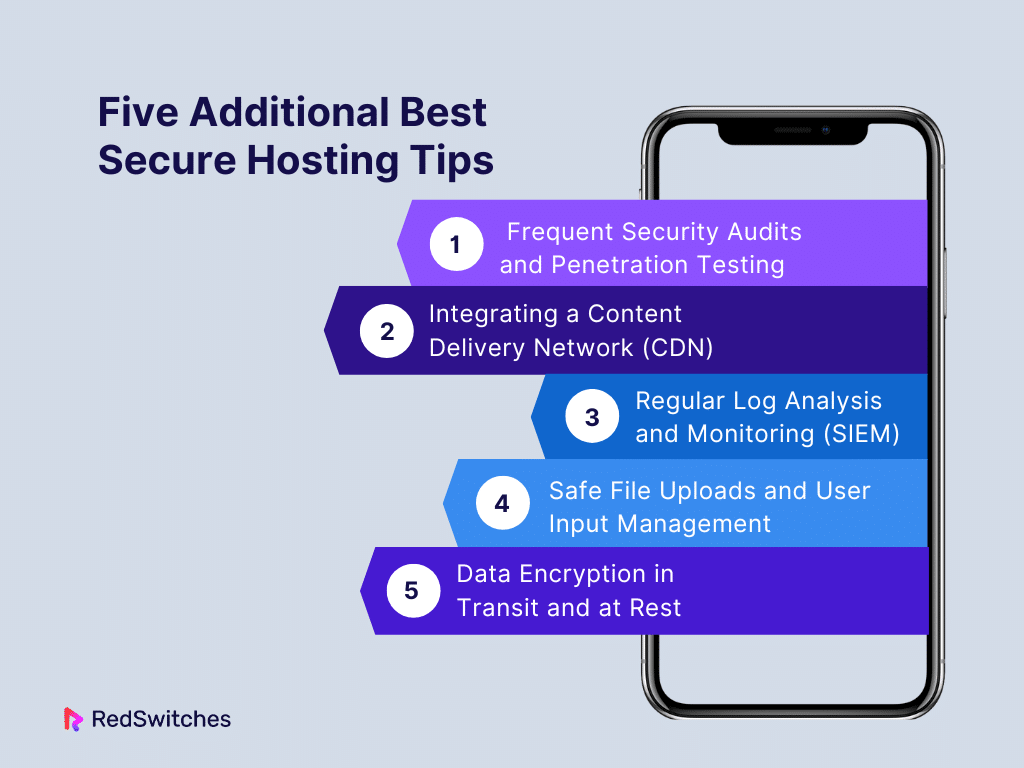
Five Additional Best Secure Hosting Tips
Let’s go through five additional web hosting tips.
Frequent Security Audits and Penetration Testing For Hosting Secure:
Do regular security audits. Also, do penetration tests. They find weaknesses in your hosting infrastructure. Security audits offer a deep look at your security controls. Penetration testing mimics attacks to find possible vulnerabilities. Address the results of these evaluations. This will strengthen your security and keep you proactive.
Integrating a Content Delivery Network (CDN) For Hosting Secure:
You should add a content delivery network (CDN) to your hosting. It is recommended. Placing servers across the globe to cache static material it lightens the burden on your hosting server. This also enhances website speed. A CDN can also offer extra protection. It does this by stopping DDoS attacks and speeding up content delivery to users everywhere.
Also read How Does a CDN Work? Content Delivery Networks Explained
Regular Log Analysis and Monitoring (SIEM) For Hosting Secure:
Thorough log analysis and monitoring need a Security Information and Event Management (SIEM) system. Examine security, access, and server logs regularly to look for and look into any strange or suspicious activity. A strong SIEM system allows quick reactions to new threats. It may provide real-time alerts and insights into security events.
Safe File Uploads and User Input Management For Hosting Secure:
Put strict security procedures in place. Do this if your website handles user input or allows file uploads. This is to guard against vulnerabilities like injection attacks and file inclusion exploits. Limit the kinds and sizes of files to reduce the danger of fraudulent uploads. Check user inputs for validity and use safe coding techniques. To remain ahead of emerging threats, examine and update security measures regularly.
Data Encryption in Transit and at Rest For Hosting Secure:
Encrypt data both at rest and in transit by going beyond SSL/TLS for data in transit. For further security, consider using secure protocols like VPNs or end-to-end encryption. Also, make sure to encrypt backups and databases with sensitive data. Do this while they are stored on the server. Data encryption makes a hosting environment more secure. It prevents unwanted access during data transmission and while the data is at rest.
The Importance of Regular backups in Web Hosting
Finally, in this core section of our blog i.e. hosting secure, we will discuss the importance of regular backups in web hosting.
Hosting Secure: Prevent Data Loss
Consistent backups safeguard against unintentional data loss. Keeping current backups reduces data loss. It lets you restore your website to a past state after human mistakes, technical malfunctions, or other surprises. Recovering lost data without backups can be a difficult and time-consuming task.
Hosting Secure: Mitigation of Cybersecurity Incidents
Websites are at risk of ransomware, malware, and hacking. They face many other cybersecurity dangers. Having current backups guarantees that you can restore your website. It will return to its original, uncompromised state in case of a security breach. This reduces the downtime from recovery operations. It helps prevent the harm of cyber disasters.
Hosting Secure: Rapid Recovery from Server Failures
Unexpected occurrences, software conflicts, and hardware problems can all lead to server crashes or failures. In such cases, quick recovery is made possible by regular backups. Having fresh backups ensures that your website may be back online fast, minimizing user disturbances and maintaining business continuity—whether a full server restore or selective data recovery.
Hosting Secure: Facilitation of Website Updates and Changes
Content, functionality, and design are all regularly updated on websites. Making a backup before any big upgrades or changes gives you a safety net in case something goes wrong. You can return to the backup if an upgrade causes unanticipated issues, saving lengthy website downtime.
Hosting Secure: Protection Against Malicious Activities
Malicious activities can jeopardize a website’s functionality and reputation. Examples of these activities include vandalism of websites and unauthorized code modifications. As a countermeasure, regular backups let you restore your website to a safe and secure version. Guaranteeing that users experience a trustworthy and secure online environment helps safeguard the reputation of your brand and user confidence.
Hosting Secure: Compliance Requirements
Regulations requiring data protection procedures, such as frequent backups, may apply to specific industries and enterprises. Respecting these rules can help you avoid trouble with the law and keep the confidence of users, clients, or customers who could confide in you with sensitive information.
Hosting Secure: Disaster Recovery Planning
An extensive disaster recovery strategy must include regular backups as a basic element. A current, easily available backup guarantees that your website can be promptly restored, minimizing downtime and enabling your organization to recover and continue regular operations in the event of a cyberattack, natural disaster, or another calamity.
Hosting Secure: Support for Website Migration
Having backups makes migrating your website easier if you intend to move it to a new hosting company or make big modifications to your hosting environment. When moving your website to a new server or platform, backups provide a dependable source of data that helps the transition go smoothly and minimizes the chance of data loss or service interruptions.
Credits: Freepik
Conclusion
In short, hosting secure is a business need. It’s not just a technical one. We’ve looked at the basics of secure hosting. We emphasized its importance for protecting private info. It ensures continuous operations and builds user confidence.
The discussion was about the top 10 web hosting security measures. It showed the need for a complete strategy. This includes everything from regular software updates to user education.
Furthermore, our investigation into the value of routine backups revealed their critical function. They protect websites from unexpected events, like cyberattacks and accidental data loss. Adopting these security measures is a proactive defense. It is also a commitment to the endurance and dependability of our online presence. This is in the ever-changing digital landscape.
RedSwitches specializes in offering secure hosting solutions that surpass industry norms. We are dedicated to strong security procedures. For businesses requiring dedicated server hosting with a focus on security, our commitment to solid security protocols, such as DDoS defense, secure infrastructure, and adherence to industry standards, makes us a reliable partner.
FAQs
Q. What is secure server hosting?
The website’s data, privacy, and defense against cyber attacks are all protected by strong safeguards. These safeguards are part of secure hosting, guaranteeing a dependable and safe online presence.
Q. What are the four types of hosting?
There are four kinds of hosting: shared, cloud, dedicated, and VPS. Each type of hosting gives website owners different degrees of control and resources.
Q. How to host a website?
A website must be hosted by picking a hosting company and registering a domain. Then, you pick a hosting package and upload its files. Next, you configure the domain settings and make sure SSL and other security are in place. This is all needed for an effective online presence.
Q. What are the top 10 secure web hosting practices for 2024?
The top 10 secure web hosting practices for 2024 include using SSL certificates. You should also use website security tools. Choose a secure hosting provider and managed hosting plan. Use advanced security features and choose the best secure hosting. Consider managed WordPress hosting. Ensure web traffic protection and select a reliable hosting platform.
Q. What is a secure web hosting service?
A secure web hosting service ensures the hosting environment has strong security. It protects websites from threats and cyber-attacks. It includes SSL certificates. It also has advanced security tools and secure hosting.
Q. How do SSL certificates contribute to secure web hosting?
SSL certificates encrypt data. They do so between a website and its visitors. This encryption ensures secure and private communication. They are crucial in securing sensitive information and building trust with website visitors.
Q. What are the key features of a secure web hosting provider?
A secure web hosting provider offers many features. These include high-level security tools. They also have regular updates. They have DDoS protection, malware scanning, and removal. They have SSL support and strong server security.
Q. Why is choosing a reliable hosting platform important for secure web hosting?
A reliable hosting platform ensures high uptime, fast performance, and robust security measures. It plays a pivotal role in maintaining the security and stability of hosted websites.
Q. What is managed hosting, and how does it contribute to secure web hosting?
Managed hosting involves the hosting provider taking care of technical aspects. These include server maintenance, security updates, and performance optimization. It contributes to secure web hosting. It ensures that security measures are monitored and updated.
Q. What are the benefits of using security tools for web hosting?
Security tools, like firewalls and malware scanners, help identify and stop security threats. They make web hosting environments more secure.
Q. How can website owners ensure secure web hosting for WordPress sites?
Owners of websites can ensure secure web hosting for WordPress sites. They can do this by choosing hosting providers that offer managed WordPress hosting. They should also offer SSL support. They should provide regular security updates and special measures for WordPress sites.
Q. What are the best practices to protect web traffic in a secure hosting environment?
To protect web traffic in a secure hosting environment, use best practices. These include encryption protocols. They also include SSL certificates. They prevent unauthorized access and data interception.
Q. How can website owners ensure secure shared web hosting?
Owners of websites can ensure secure shared web hosting. They can do this by picking providers that prioritize security. The providers should offer SSL for shared hosting plans. They should also add security features at the server level. And, they should often update security to protect all hosted sites.