Do you know that, at the very minimum, a DDoS attack costs $8,000 for every hour of downtime?
Distributed Denial of Service (DDoS) attacks have become a significant danger to online businesses and organizations in today’s connected world. These attacks can destroy networks, impair services, and harm finances and reputations.
The good news is that it is now easier to answer the question on your mind: how to prevent DDoS attacks on your infrastructure.
Businesses can take steps to harden their network and infrastructure security against DDoS attacks and guarantee the continuous availability of their online services.
This article will look at eight tried-and-true strategies to stop a DDoS attack. The combined impact of these tactics ensures robust protection for your network by covering all major loopholes cybercriminals use to launch DDoS attacks.
You’ll see that these tactics aim to reduce the effects of DDoS attacks and safeguard digital infrastructure so that it continues to function during the attack.
But before that, let’s understand what happens during a DDoS attack.
Table Of Contents
- What is a DDoS attack?
- How Does a DDoS Attack Work?
- The Eight Best Practices to Prevent DDoS Attacks
- Best Practice # 1: Harden Network Infrastructure Security
- Best Practice # 2: Traffic Monitoring and Analysis
- Best Practice # 3: Rate Limiting and Traffic Shaping
- Best Practice # 4: Leverage Load Balancing
- Best Practice # 5: Regularly Patch and Apply Updates
- Best Practice # 6: Redundancy and Scalability
- Best Practice # 7: Incident Response Planning
- Best Practice # 8: Close Collaboration with ISPs and Network Providers
- Conclusion
- FAQ
What is a DDoS attack?
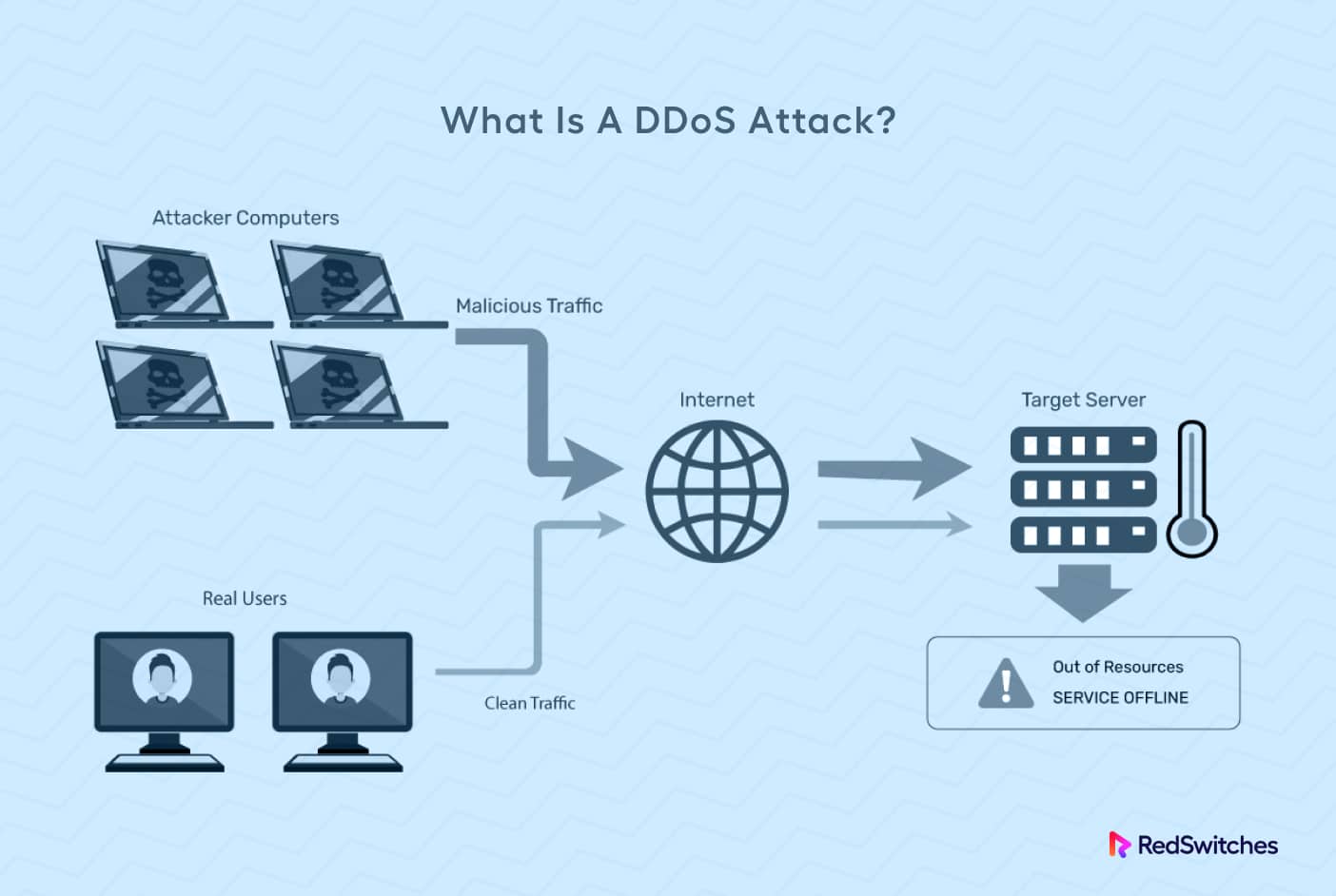
A Distributed Denial of Service (DDoS)attack is a deliberate attempt to stop a network, system, or website from operating normally by flooding it with traffic.
During the assault, numerous compromised computers—often called a “botnet”— send excessive traffic or requests to the target network. As a result, the network is unable to respond to valid user requests.
A DDoS attack aims to overwhelm and exhaust the target network’s computational resources (bandwidth, processing power, and memory) to deny service to actual users. The assault may target an infrastructure application, transport, or network layer.
DDoS assaults often take advantage of infrastructure flaws in the target, like exposed network ports, unsafe protocols, or improperly configured servers.
Once the attack has run its course, identifying the attackers’ true identities is a serious challenge because of how DDoS attacks are executed. Hackers deploy these attacks through compromised botnets that run the attack script in a loop. This tactic allows attackers to conceal their identities because the logs of the affected network show only the IP addresses of the botnet devices.
In our opinion, the first step toward preventing DDoS attacks is understanding how these attacks play out. Let’s discuss this in some detail.
How Does a DDoS Attack Work?
A DDoS attack works by overwhelming a target system, network, or website with excessive traffic, rendering it unable to function correctly, and denying service to legitimate users.
Let’s explore how a DDoS attack typically unfolds:
Stage # 1: Botnet Creation
The attacker starts by creating a network of compromised computers called a botnet.
These compromised computers, also known as “zombies,” are often ordinary devices (desktop computers, servers, IoT devices, or even smartphones) infected with malware. The attacker gains control of these devices without their owners’ knowledge, making them unwitting participants in the attack.
Stage # 2: Command and Control (C&C)
The attacker sets up an infrastructure for communication and management of the botnet. While the C&C infrastructure might vary, the purpose remains the same. The attackers use the C&C infrastructure to deliver instructions to the compromised devices and coordinate the simultaneous attack launch.
In most cases, C&C is a node in the botnet that initializes a DDoS attack by running an activation script. This script accesses other components of the attack network and instructs them on the type and frequency of the requests sent to the target network.
Stage # 3: Reconnaissance
The attacker identifies potential target systems or websites. The choice of targets depends upon factors such as the target’s popularity, the financial impact of the attack, and personal motivations.
Stage # 4: Attack Initiation
Under the attacker’s control, the compromised devices in the botnet start sending a massive volume of traffic or requests to the target. This flood of traffic aims to exhaust the target’s resources and deny services to legitimate users.
How Attackers Mask Their Identity
Attackers often employ several techniques to obfuscate their identity and hide the source of the attack. The list includes using proxy servers, spoofing IP addresses, or utilizing botnets with diverse geographical locations to complicate tracking the attack traffic back to the source.
The Impact of the DDoS Attack
The target system, network, or website gets overwhelmed by the flood of traffic, leading to severe performance degradation or a complete loss of service. This denial of service disrupts normal operations and prevents legitimate users from accessing the targeted resources.
Even when the attack is over, the consequence of the attack can last for months. The business needs to recover from damaging its reputation and try to bring back the lost visitors. In addition, the business needs to recoup the financial loss caused by the attack.
Types of DDoS Attacks
The next step in DDos attack prevention is to understand the various formats of the attack. Each type targets different layers of the network stack and exploits vulnerabilities differently.
Here are some common types of DDoS attacks that you may encounter:
Volume-Based Attacks
Volume-based attacks overwhelm the target’s network bandwidth by flooding it with massive traffic. These attacks consume the available network resources, making it difficult for legitimate users to access the targeted service. Examples include:
- UDP Floods: Attackers send many User Datagram Protocol (UDP) packets to the target to overload the network.
- ICMP Floods: Attackers flood the target with Internet Control Message Protocol (ICMP) packets, often using spoofed IP addresses to make it harder to trace the source.
Protocol Attacks
Protocol-based attacks exploit vulnerabilities in network protocols to consume server resources and disrupt service. By targeting weaknesses in how protocols handle connections, these attacks can exhaust available resources and prevent legitimate connections from being established. Examples include:
- SYN Floods: Attackers send a high volume of TCP SYN requests, overwhelming the server’s ability to process and respond. After a while, this attack effectively denies service to legitimate users.
- ICMP Smurf Attacks: Attackers send ICMP echo requests to broadcast IP addresses, causing all hosts in the network to respond simultaneously. You can imagine the network-wide traffic overload that could result from this attack.
Application Layer Attacks
Application layer attacks target specific resources or vulnerabilities in web applications. The idea is to disrupt the application’s functionality and deny access to users. Examples include:
- HTTP Floods: Attackers send many HTTP requests to a web server, overwhelming its capacity to process them and causing the server to become unresponsive.
- Slowloris Attacks: Attackers establish multiple connections to a web server but send HTTP requests very slowly, keeping the links open for as long as possible. Gradually, these open channels exhaust server resources, causing the server to reject connection requests from legitimate users.
Reflective/Amplified Attacks
Reflective or amplified attacks exploit legitimate services to boost the attack traffic, making it more challenging to trace the source back to the attacker. These attacks send a small request to a vulnerable server, which then responds with a much larger reply, amplifying the volume of traffic directed at the target. Examples include:
- DNS Amplification: Attackers send small DNS queries with spoofed source IP addresses to vulnerable DNS servers. During the process, the target network gets overwhelmed by the much larger DNS responses.
- NTP Amplification: Attackers use Network Time Protocol (NTP) servers that respond with large NTP packets to small requests, amplifying the traffic directed at the target.
These are just a few examples of DDoS attacks that can target your infrastructure. Attackers constantly evolve tactics, finding new vulnerabilities to exploit and developing more sophisticated attack techniques.
This brings us to the final step towards how to prevent a DDoS attack. We’ll now discuss the ways and preventive measures businesses can implement to protect against DDoS attacks.
Let’s look at these multi-layered defense strategies in detail.
The Eight Best Practices to Prevent DDoS Attacks
Implementing security measures and industry best practices is an essential aspect of a larger strategy for DDoS attack prevention.
Here’s a short discussion on the industry best practices you should adopt to stop DDoS attacks on your network.
Best Practice 1: Harden Network Infrastructure Security
Network infrastructure protection is a critical aspect of DDoS attack prevention.
Businesses must strengthen their network infrastructure and reduce the probability of DDoS attacks by implementing robust security measures. The following are some crucial components of network infrastructure defense:
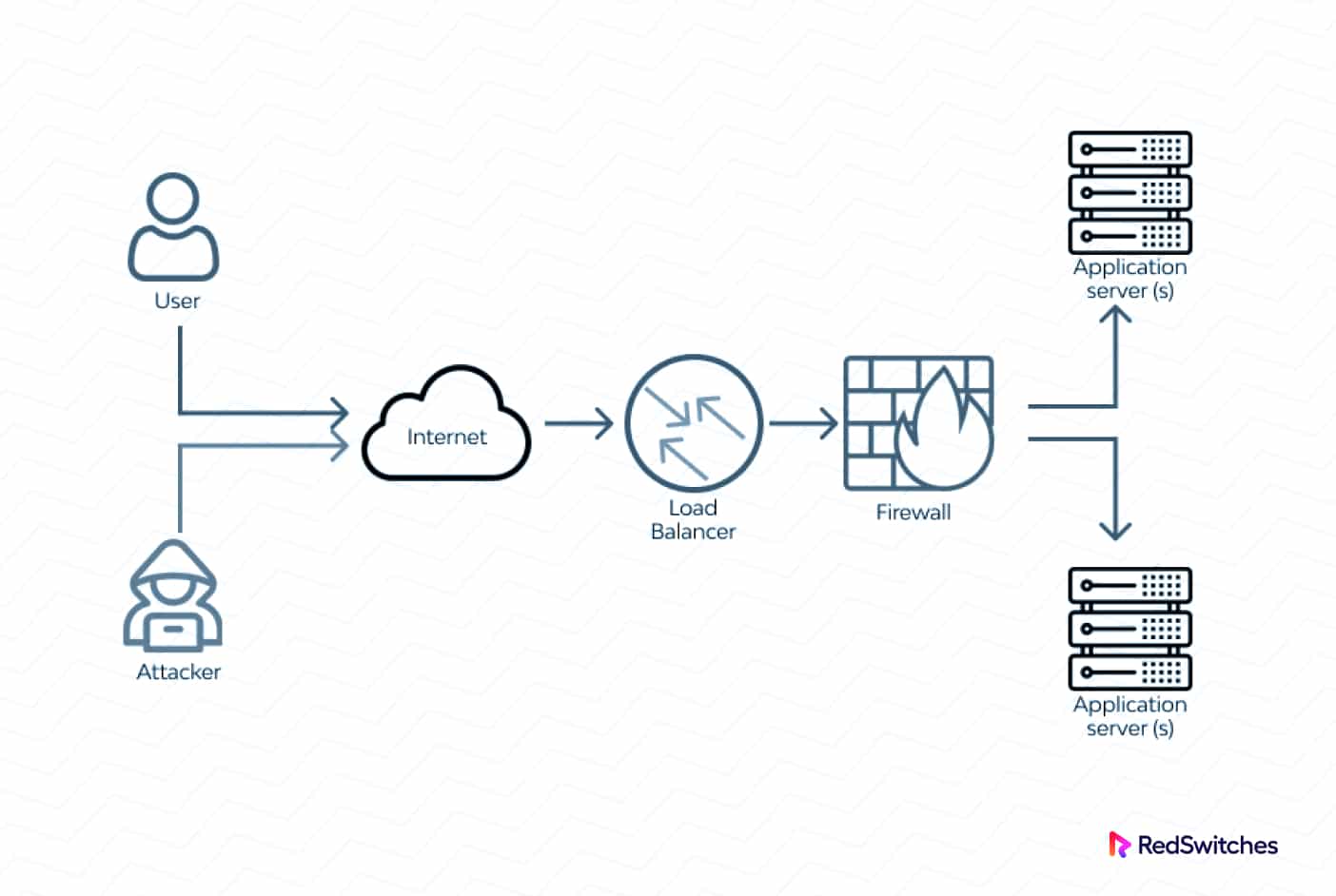
Firewalls
Deploying firewalls at network perimeters and critical infrastructure points helps filter incoming and outgoing traffic based on predefined security policies. Firewalls can be configured to block traffic from suspicious or unauthorized sources, reducing the attack surface for potential DDoS attacks.
Intrusion Detection and Prevention Systems (IDS/IPS)
IDS/IPS systems keep track of network activity, look for oddities, and spot probable DDoS attack trends. These systems can quickly analyze traffic patterns, payload contents, and packet headers to spot malicious activity. They can then start the proper reactions, such as informing administrators or stopping the attack-related traffic.
Network Segmentation
Implementing network segmentation helps isolate critical infrastructure and services from the rest of the network. By dividing the network into smaller segments, businesses can limit the impact of DDoS attacks by containing them to less critical components and preventing the spread to other parts of the network.
Traffic Filtering and Rate Limiting
Rate limitations and traffic filtering are two related strategies to protect your infrastructure from the high DDoS-related traffic volume. Admins can place filtering rules to recognize and block specific attack traffic patterns and filter traffic from known malicious sources. Rate limitation can limit the volume of traffic permitted to reach particular resources, preventing the damage caused by too many requests consuming server resources.
Anycast and Load Balancing
Anycast routing and load-balancing techniques distribute incoming traffic across multiple servers or data centers. By spreading the traffic load, businesses can prevent a single server or resource from being overwhelmed by a DDoS attack. This approach also enhances the availability and resilience of network resources.
Best Practice # 2: Traffic Monitoring and Analysis
Traffic analysis and monitoring are essential to preventing DDoS attacks. During the process, network admins can spot irregularities, identify possible dangers, and successfully minimize the effects of DDoS attacks.
The process involves carefully observing and analyzing network data to gain insights about incoming and outgoing traffic patterns, volume, and behavior.
Businesses can set up dedicated tools to monitor their network infrastructure in real-time, effectively detecting abnormal traffic activity that may indicate an ongoing or imminent DDoS attack.
Why Should You Invest in Traffic Analysis & Monitoring
- Investing in Traffic analysis and monitoring results in several benefits, including:
Early Detection
Traffic analysis helps identify the warning signs of a DDoS attack, enabling businesses to initiate proactive countermeasures. Unusual surges in traffic volume, irregular patterns, or a sudden influx of requests from specific IP addresses or geographical locations can indicate a potential attack. - Differentiating Legitimate Traffic from Malicious Activity
Practical traffic analysis helps businesses distinguish legitimate user traffic from malicious activity. Any deviations from this baseline can be detected and scrutinized by establishing a baseline of normal traffic behavior. Businesses can then automate identifying and filtration of negative traffic patterns associated with DDoS attacks. - Fast Mitigation and Response
Traffic analysis provides valuable insights for effectively responding to DDoS attacks. Businesses can tailor their mitigation efforts by understanding the attack vector and traffic characteristics. This includes redirecting or dropping suspicious traffic, implementing rate-limiting measures, or activating DDoS mitigation services. - Trend Analysis and Capacity Planning
Traffic analysis allows businesses to identify trends and patterns, helping them anticipate and prepare for future DDoS attacks. Businesses can proactively strengthen their infrastructure by understanding their network capacity requirements and potential vulnerabilities and allocate resources accordingly.
Tips for Proactive Traffic Monitoring and Analysis
Here’re some tips businesses can apply for effective traffic monitoring and analysis.
- Implement Network Traffic Monitoring Tools
Consider deploying specialized tools and solutions to monitor and analyze real-time network traffic. These tools should provide comprehensive visibility into the network, including traffic flow, protocols, and application-level insights. - Establish Baseline Traffic Patterns
Create a baseline of normal traffic behavior by monitoring and recording regular network activity. This baseline is the reference point for identifying anomalies and suspicious patterns that may indicate a DDoS attack. - Utilize Anomaly Detection Techniques
Implement advanced anomaly detection techniques to identify and flag deviations from normal traffic behavior automatically. Businesses can use machine learning algorithms, statistical analysis, and behavior-based anomaly detection systems. - Integrate a Security Information and Event Management (SIEM)
Integrate traffic monitoring and analysis tools with a SIEM system to connect network traffic data with other security events and alarm systems. With this arrangement, network admins can see the security posture holistically and take action to stop DDoS attacks as early as possible. - Regularly Review and Update Monitoring Policies
Admins should continuously review and update monitoring policies to adapt to threats and new attack vectors. They should stay informed about emerging DDoS attack techniques and ensure monitoring systems are configured to detect and respond to the latest threats. Traffic monitoring and analysis are crucial components of an effective DDoS prevention strategy. By implementing the best practices outlined above, businesses can fortify their defenses and significantly reduce the intensity and final impact of DDoS attacks.
Best Practice # 3: Rate Limiting and Traffic Shaping
Rate limitation and traffic shaping are critical to prevent DDoS attacks in the first place and reduce the effects of an ongoing DDoS situation. These techniques aid in managing network traffic flow, ensuring proper resource allocation, preventing resource wastage, and preventing heavy traffic from taxing the network infrastructure.
Here is how to use rate limitation, traffic shaping, and several other related tactics to prevent DDoS attacks:
Rate Limiting
Rate limiting sets thresholds on the volume of incoming traffic permitted to access particular resources and services. Businesses can avoid excessive traffic spikes frequently linked to DDoS attacks by restricting the number of requests or packets sent/received per second. Rate limitations can be applied to several components, including network devices, firewalls, and load balancers.
Traffic Shaping
Traffic shaping aims to manage the bandwidth allotted to various types of traffic. Businesses can allocate network resources and prioritize traffic for specific services based on predetermined policies. This guarantees essential services always have appropriate bandwidth. Traffic shaping restricts the bandwidth for non-critical or harmful traffic. Giving priority to genuine traffic and lowering the capacity available for attack traffic lessens the impact of DDoS attacks.
Source IP Rate Limiting
Source IP rate limiting is setting restrictions on the number of requests or connections permitted from a specific IP address or IP range. This method aids in thwarting DDoS attacks that launch a considerable number of requests or connections from a single or a small block of source IP addresses. This simple restriction can reduce the impact of such attacks by restricting the number of requests or connections permitted from a source IP address.
Dynamic Rate Limiting and Traffic Shaping
Dynamic rate limiting and traffic shaping techniques automatically adjust the limits and allocations based on the current network conditions.
These techniques use traffic analysis, anomaly detection, and traffic profiling to dynamically adapt the rate limits and traffic shaping policies to respond to changing traffic patterns. This approach proactively manages traffic during DDoS attacks by dynamically adjusting thresholds and allocating resources as needed.
Deep Packet Inspection (DPI)
Deep packet inspection involves inspecting the content and characteristics of network packets in real time.
DPI can identify and classify traffic based on its nature and behavior by analyzing packet headers, payloads, and other metadata. Network admins can combine this information with rate limiting and traffic shaping policies to effectively target specific types of traffic associated with DDoS attacks (such as malformed packets, excessive connection requests, or specific attack signatures).
Best Practice # 4: Leverage Load Balancing
Load balancing is commonly used in network infrastructure to distribute incoming traffic across multiple servers or resources.
While load balancing is not a natural defense against DDoS attacks, it can help mitigate the impact of such attacks by distributing the attack traffic and preventing a single server or resource from being overwhelmed and going offline.
Here’s how load balancing can be effective in the context of DDoS attacks:
Traffic Distribution
Load balancers distribute incoming traffic across multiple servers or resources in a balanced manner. By evenly distributing the traffic load, load balancers prevent a single server from becoming a bottleneck or a single point of failure. In the case of a DDoS attack, the attack traffic is distributed across multiple servers, reducing the impact on individual resources and improving overall availability.
Scalability and Redundancy
Load balancing enables businesses to scale their infrastructure horizontally, adding more servers or resources to handle increased traffic demands. This scalability helps absorb the additional traffic and cushions the infrastructure against the rising demand for server resources created by the attack.
Load balancers provide redundancy by monitoring the health and availability of servers. If a server is overwhelmed by a DDoS attack, the load balancer can redirect traffic to healthy servers and keep the overall level of service availability.
Traffic Filtration
Load balancers can be configured with filtering rules to block or divert traffic from suspicious or malicious sources. This can include blocking traffic from known DDoS attack sources or implementing rate limiting to control the volume of traffic allowed from specific IP addresses. By filtering out attack traffic at the load balancer level, businesses can prevent malicious traffic from reaching the servers and affecting critical components and services. Eventually, these policies help reduce the attack’s impact.
Layer 7 Load Balancing
Layer 7 load balancing operates at the Application layer and can inspect the content and characteristics of incoming traffic. This enables load balancers to identify and block specific types of traffic associated with DDoS attacks. Load balancers can identify excessive requests or specific attack patterns and divert or filter out such traffic. This can shield the backend servers from the brunt of the attack.
Dynamic Adaptation
Advanced load-balancing solutions can dynamically adapt to changing traffic patterns, including those caused by DDoS attacks.
By analyzing traffic in real-time and utilizing algorithms, load balancers can automatically adjust traffic distribution based on the current conditions. This adaptability allows load balancers to respond to sudden traffic spikes caused by DDoS attacks and effectively distribute the load across available resources.
Best Practice # 5: Regularly Patch and Apply Updates
Keeping your systems and software updated to the latest security patches and releases can help minimize the intensity of a DDoS attack. It is common knowledge that attackers can exploit the vulnerabilities of the operating system, application, or network equipment to launch DDoS attacks. Regular patching helps close these issues and prevents your network from becoming a DDoS attack target.
Best Practice # 6: Redundancy and Scalability
Sysadmins should consider building redundancy and scalability into the infrastructure to increase the overall infrastructure capabilities, especially the traffic-handling processes.
This can involve deploying additional servers, utilizing cloud-based resources, or implementing content delivery networks (CDNs) to distribute content and drive traffic spikes effectively.
Attackers are known to target infrastructure security components in the initial phases of a DDoS attack so that the later stages can deliver the desired results. System admins should consider redundancy for these components to add fail-over capabilities to critical infrastructure security components.
Best Practice # 7: Incident Response Planning
System administrators and infrastructure security teams should have a detailed incident response plan.
We highly recommend including the steps and actions each team member should carry out during and after a DDoS attack. The plan should include a mitigation and recovery strategy, along with information on the duties and responsibilities of each team member. The plan should also outline specific communication channels and procedures for sharing information with management and customers.
Best Practice # 8: Close Collaboration with ISPs and Network Providers
During a DDoS, it is critical that you closely engage with your Internet Service Provider (ISP) and network providers to leverage their expertise in mitigating DDoS attacks. At the minimum, you should work with them to establish traffic filtering and protection mechanisms to block attack traffic closer to its source.
We highly recommend setting up a DDoS emergency management channel with these service providers. As soon as the IDS detects the onset of a DDoS attack, sysadmins should activate this channel and request the ISP for extreme traffic throttling to minimize the attack’s impact.
By implementing these best practices, businesses can enhance their resilience against DDoS attacks and reduce the potential impact on their systems and services. It is essential to regularly review and update your security measures to adapt to evolving threats and stay one step ahead of attackers.
Conclusion
Preventing DDoS attacks requires a multi-faceted approach that combines various techniques and strategies. By adopting these preventive measures, businesses can strengthen their network security against DDoS attacks, minimize service disruptions, and protect their critical infrastructure and resources. Regular assessment, testing, and updating of defense mechanisms are crucial to staying ahead of evolving attack techniques and ensuring the effectiveness of your DDoS prevention strategy.
At RedSwitches, security lies at the heart of everything we do. When delivering bare metal servers to customers, we implement a basic security strategy and inform users about how they can protect their infrastructure. We also help businesses plan backup and recovery policies to recover and continue business operations with minimum downtime. Contact us today for a free consultation about securing your bare-metal infrastructure.
FAQ
Q1: What is a DDoS attack?
A: A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the availability of a network, system, or service by overwhelming it with a flood of Internet traffic from multiple sources.
Q2: How can a business prevent DDoS attacks?
A: Preventing DDoS attacks requires a comprehensive approach combining the abovementioned strategies and techniques.
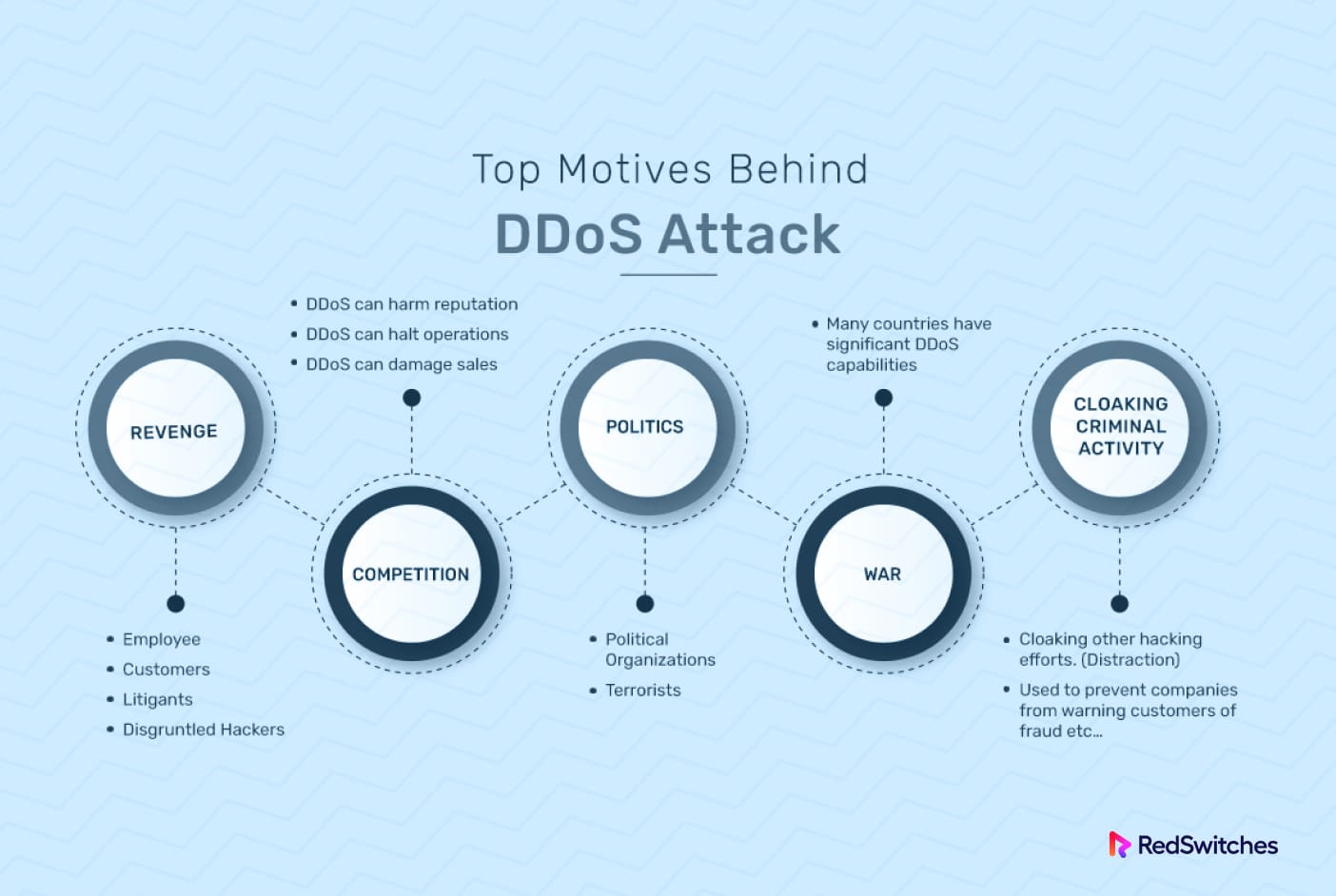
Q3: Why do attackers launch DDoS attacks?
A: Attackers launch DDoS attacks for various reasons, including financial gain, competitive advantage, revenge, activism, or simply causing disruption and chaos.
Q4: What are the benefits of partnering with a DDoS mitigation service provider?
A: DDoS mitigation service providers offer specialized expertise, dedicated infrastructure, and real-time monitoring to detect and mitigate DDoS attacks. They can handle large-scale attacks and provide proactive defense mechanisms, allowing you to focus on your core business operations.
Q5: Can rate limiting and traffic shaping techniques prevent DDoS attacks?
A: Rate limiting and traffic shaping techniques can help prevent and mitigate the impact of DDoS attacks by controlling traffic flow and preventing excessive requests or connections. These vendors combine various techniques with infrastructure preventive measures for comprehensive protection.