In a digital age where data breaches make headlines and personal information is a prized commodity, understanding online security protocols is more than just tech jargon—it’s a fundamental life skill.
Two names that have dominated this conversation for years are TLS and SSL. But as we venture into 2023, the debate around these two protocols intensifies, with professionals, enthusiasts, and everyday users seeking clarity. Which one takes the crown in offering supreme internet security? Dive with us into the intricacies of SSL vs TLS, unpacking their history mechanisms and evaluating their performances in today’s cyber landscape.
Welcome to the ultimate showdown: TLS vs SSL. Which is the internet’s gold standard in 2023? Let’s find out.
Table of Contents
What is SSL?
Secure Sockets Layer, colloquially known as SSL, is an illustrious name in the annals of internet security. Introduced in the nascent days of the digital age, its journey chronicles the evolving landscape of web-based secure communications. A thorough exploration of its development and mechanisms offers unparalleled insight into the history and challenges of internet safety protocols.
SSL Protocol
- Origin & Evolution:
- Born out of an increasingly interconnected digital realm, Netscape developed SSL in the early 1990s. It was envisioned as a solution to the burgeoning need for secure online communications in a world where data breaches were becoming all too common.
- Core Objective:
- The essence of the SSL protocol lies in its capability to encrypt data. By transforming readable, plaintext data into a complex encrypted code, it ensures that sensitive information—be it personal details, financial transactions, or confidential communications—remains protected from prying eyes during transit.
- Scope & Applications:
- While the advent of the Transport Layer Security (TLS) protocol has overshadowed SSL in many applications, the legacy of SSL continues to linger. Many still colloquially refer to secure connections as ‘SSL,’ and traces of its methodologies persist in specific applications and systems today.
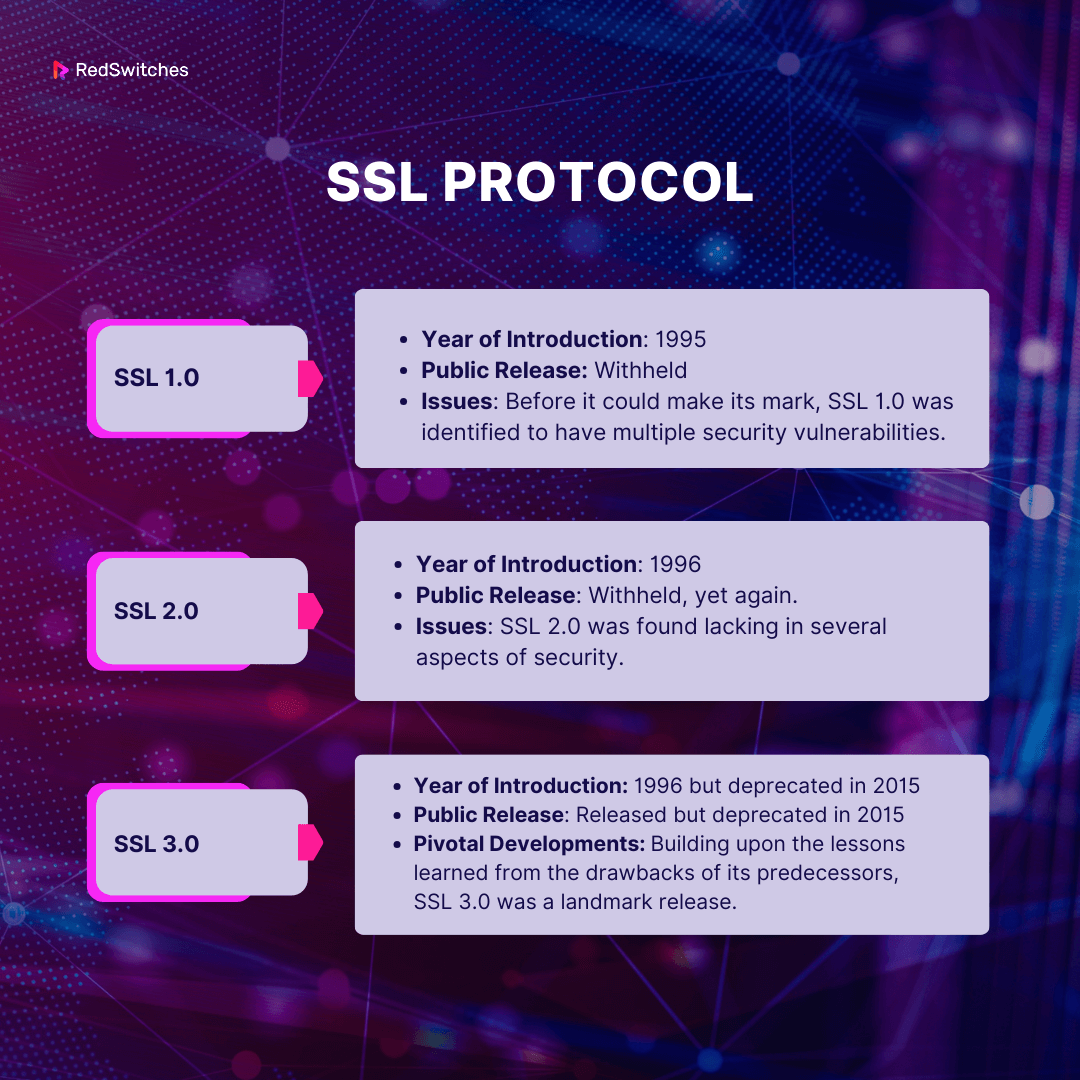
SSL 1.0 and SSL 2.0
- SSL 1.0:
- Year of Introduction: 1995
- Public Release: Withheld
- Issues: Before it could make its mark, SSL 1.0 was identified to have multiple security vulnerabilities. The nature of these flaws was so severe that Netscape decided against a public release to prevent potential exploitation.
- SSL 2.0:
- Year of Introduction: 1996
- Public Release: Withheld, yet again.
- Issues: Learning from the shortcomings of SSL 1.0, Netscape developed SSL 2.0 to rectify earlier mistakes. However, SSL 2.0 was found lacking in several aspects of security. Recognizing the potential risks, Netscape chose not to release this version to the public.
SSL 3.0
- Year of Introduction: 1996 but deprecated in 2015
- Public Release: Released but deprecated in 2015
- Pivotal Developments:
- Building upon the lessons learned from the drawbacks of its predecessors, SSL 3.0 was a landmark release. Netscape introduced many improvements, both in terms of encryption methodologies and overall protocol design.
- Legacy & Widespread Adoption:
- The enhancements in SSL 3.0 made it the most resilient and reliable version of the SSL protocol. Its robust features quickly became the industry standard for secure online communications during its prime. This version fortified web security and paved the way for subsequent advancements in digital security protocols.
Here is a summarized breakdown of SSL:
| Aspect | Details |
| Origin | Developed by Netscape in early 1990s. |
| Objective | Encrypt data for secure online communication. |
| Legacy | Influential in internet security, superseded by TLS. |
| SSL 1.0 | 1995, release withheld due to vulnerabilities. |
| SSL 2.0 | 1996, release withheld, improved but still flawed. |
| SSL 3.0 | 1996, released, deprecated in 2015; major improvements in security. |
Interested in diving deeper into website security? Don’t miss our comprehensive guide on the various SSL certificates available to fortify your online presence further. Read our article: “Explore the Six Types of SSL Certificates for Your Website,” to ensure you make the most informed choices for your digital assets.
What is TLS?
As digital communication evolved, the necessity for bolstered security became paramount. Transport Layer Security (TLS) emerged as a testament to this evolution, building on the foundation of its predecessor, SSL, while incorporating enhancements to meet the security demands of a more connected world.
Internet Engineering Task Force (IETF)
- Overview:
- The IETF stands as a beacon of standardization across the vast landscape of the internet. This organization, which has shaped much of the internet’s foundational protocols, sought to bring cohesion to the myriad of technologies that make up the web.
- Role & Significance:
- As the primary body behind the standardization of Internet protocols, the IETF has a critical role in ensuring consistency and interoperability across the digital realm. Its impact spans various facets of online communication, including (but not limited to) security, routing, addressing, and even the core TCP/IP protocol.
- Working Mechanism:
- Within the IETF are specialized working groups, each dedicated to specific areas of Internet technology. For instance, the Transport Layer Security Working Group was the driving force behind the creation and refinement of the TLS protocol, taking lessons from SSL’s journey and iterating upon them.
TLS Protocol
- Origin & Purpose:
- Introduced as an advancement over SSL, the TLS protocol aimed to offer heightened security measures for online data exchange. It replaced and evolved, addressing vulnerabilities and incorporating contemporary cryptographic techniques.
- Development Trajectory:
- Over the years, TLS has undergone numerous revisions, each building on the successes and learnings of its predecessors, ensuring its continued relevance and robustness in the ever-changing cybersecurity landscape.
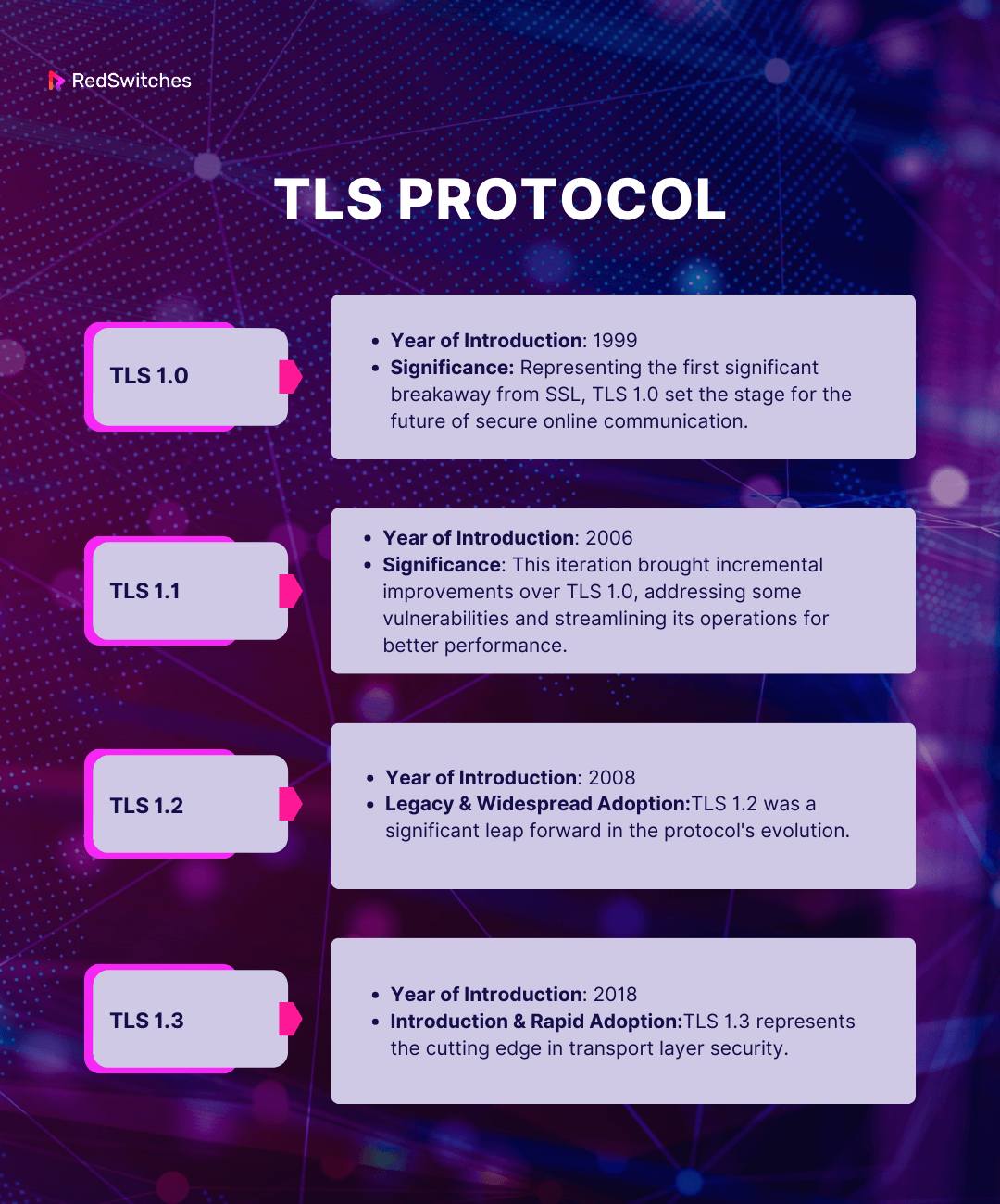
TLS 1.0 and 1.1
- TLS 1.0:
- Year of Introduction: 1999
- Significance: Representing the first significant breakaway from SSL, TLS 1.0 set the stage for the future of secure online communication.
- TLS 1.1:
- Year of Introduction: 2006
- Significance: This iteration brought incremental improvements over TLS 1.0, addressing some vulnerabilities and streamlining its operations for better performance.
TLS 1.2
- Year of Introduction: 2008
- Legacy & Widespread Adoption:
- TLS 1.2 was a significant leap forward in the protocol’s evolution. With a more robust suite of cryptographic tools and improved security measures, it quickly became the favored choice for most online platforms and continues to dominate usage.
TLS 1.3
- Year of Introduction: 2018
- Introduction & Rapid Adoption:
- TLS 1.3 represents the cutting edge in transport layer security. Not only does it streamline many of the complexities found in previous versions, but it also introduces new features that bolster security and improve connection speeds.
- Endorsements & Mandates:
- Institutions like the National Institute of Standards in Technology (NIST) have recognized the protocol’s superiority. NIST’s directives highlight the urgency for government entities to adopt TLS 1.2 with FIPS-compliant cipher suites.
- Still, they also underline the importance of transitioning to TLS 1.3, with a recommendation to have migration plans in place by January 1, 2024. This endorsement underscores TLS 1.3’s role as the new standard bearer for secure online communications.
Here is a summarized breakdown of TSL:
| Aspect | Details |
| IETF Role | Standardizes internet protocols, impacting areas like security and TCP/IP. |
| TLS Evolution | Advanced from SSL for improved online security, continually revised for robustness. |
| TLS 1.0 | Introduced in 1999, significant evolution from SSL. |
| TLS 1.1 | Launched in 2006, improved upon TLS 1.0. |
| TLS 1.2 | Debuted in 2008, widely adopted for its advanced cryptographic tools. |
| TLS 1.3 | Released in 2018, streamlined with superior security features; recommended by institutions like NIST. |
Want to bolster the security of your business website further? Equip yourself with the latest tricks and techniques. Check out our detailed guide on “5 Website Security Best Practices For Businesses” to ensure your online operations remain uncompromised and resilient against threats.
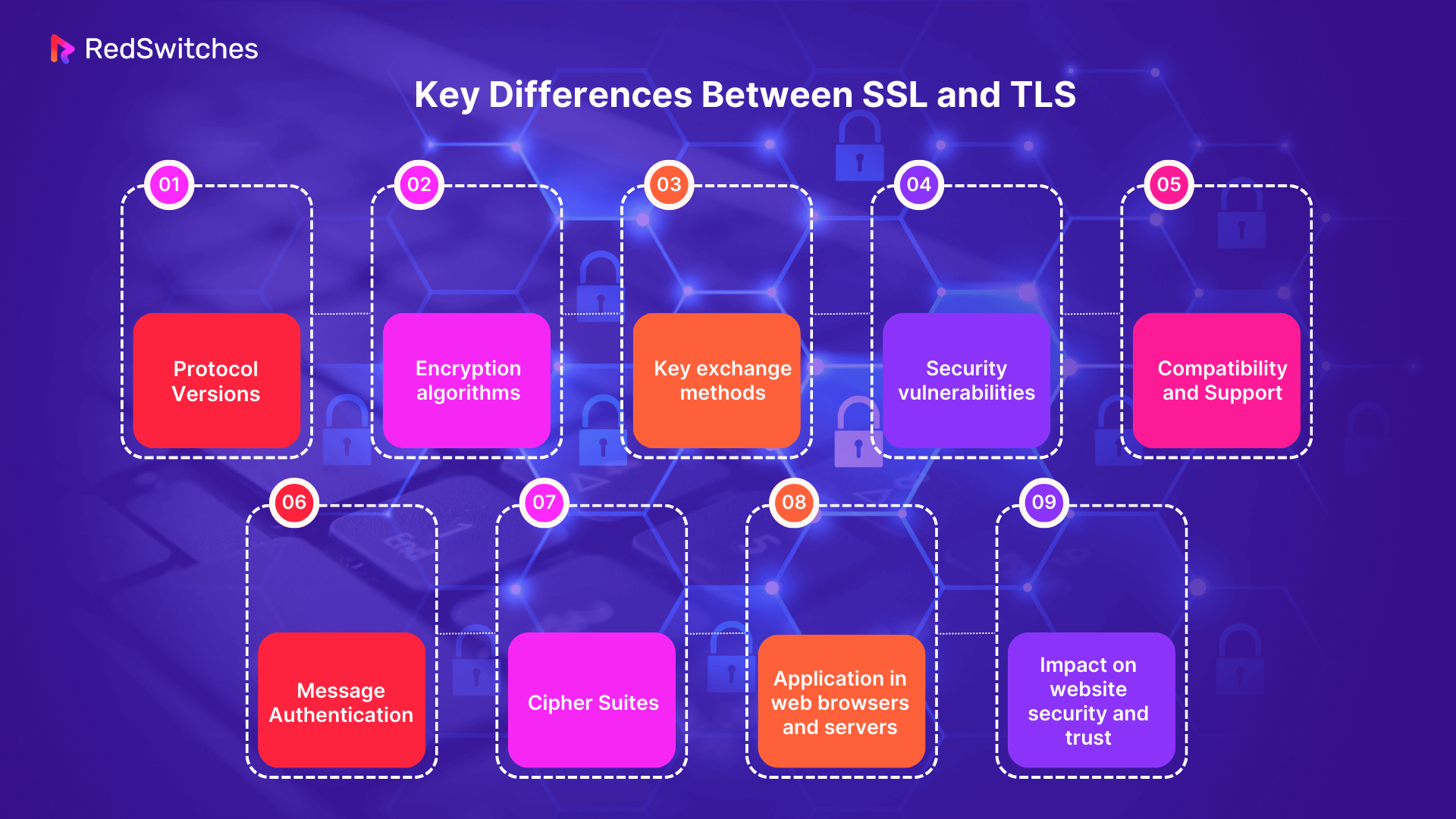
Key Differences Between TLS vs SSL
Two titans have long been spotlighted in the vast labyrinth of internet security protocols: SSL and TLS. Their names often echo synonymously in conversations, yet they harbor distinct identities, features, and legacies.
As the digital era continues to change at an unparalleled pace, understanding the nuances of “TLS vs SSL” becomes not just a matter of technical discernment but a vital component in ensuring the secure exchange of data in an increasingly interconnected world.
In this section, we’ll embark on a journey to demystify the distinctions, unraveling the intricacies that set these two protocols apart and shaping the fabric of online security.
Protocol Versions
In the intricate world of internet security, the discourse on TLS vs SSL often takes center stage. Both serve as cornerstones of secure communication over digital networks. As cryptographic protocols, they encrypt data in transit, ensuring confidentiality and integrity. However, the journey of SSL versus TLS has been marked by evolution, improvements, and deprecations. Let’s dive deep into their protocol versions to discern the critical difference between SSL and TLS.
SSL Protocol Versions
- Overview:
- SSL (Secure Sockets Layer) is the pioneering cryptographic protocol, setting the foundational principles of secure communication.
- Version History:
- SSL 2.0: An early attempt at secure communication, now deprecated due to inherent vulnerabilities.
- SSL 3.0: Improved from its predecessor but still faced challenges. Was the bridge leading to TLS 1.0. Currently deprecated.
- TLS 1.0: Although often grouped under TLS, this version is essentially an extension of SSL 3.0. With the increasing need for stronger security, this, too has been deprecated.
TLS Protocol Versions
- Overview:
- TLS (Transport Layer Security) took the baton from SSL, introducing refinements and innovations to cater to modern security needs.
- Version History & Comparison:
- TLS 1.0 (1999): An initial stride into a new realm, now deprecated.
- TLS 1.1 (2006): Incorporated fixes for vulnerabilities of its predecessor. Deprecated in favor of more robust versions.
- TLS 1.2 (2008):
- Status: Active
- Features: Introduced more robust encryption algorithms, an enhanced handshake process, and improved overall performance with reduced latency.
- TLS 1.3 (2018):
- Status: Active
- Features: A quantum leap over its predecessors, boasting top-tier encryption, streamlined operations, and reduced connection establishment time.
Guidance on Protocol Usage
- Recommendation:
- For those still anchored to TLS 1.0 or 1.1, a shift to TLS 1.2 or 1.3 is not just recommended but vital. These modern versions encapsulate the best in protocol security.
- How to Ascertain Your Version:
- For web browsers, delve into the developer tools and scout for the “Protocol” section. In cases of other applications, a perusal of their respective documentation can offer insights into the supported TLS versions.
Navigating the waters of TLS vs SSL might seem daunting, but the choice, in essence, is clear. TLS, especially its recent versions, offers unparalleled security. Lingering on SSL or older TLS versions is not just outdated but a security risk. Embrace the future, upgrade to the latest TLS, and fortify your digital communications.
Encryption algorithms
Amid the vast matrix of cybersecurity tools, encryption algorithms are pivotal in ensuring data integrity and confidentiality. They act as cryptic shields, preventing unauthorized access and ensuring our digital conversations remain private. But when it comes to TLS vs SSL, which protocol offers better armor? Let’s delve into their encryption algorithms’ intricate world to discern the difference between SSL and TLS.
SSL Encryption Algorithms
- Overview:
- SSL, being the predecessor, initially banked on several encryption algorithms. Over time, some of these became susceptible to threats.
- Key Algorithms:
- RC4: An antiquated encryption algorithm vulnerable to multiple attacks, including the infamous FREAK attack. No longer deemed secure.
- DES & 3DES: Older ciphers that once stood the test of time but, like all things vintage, have vulnerabilities that modern cyber threats exploit.
TLS Encryption Algorithms
- Overview:
- Transitioning from SSL, TLS heralded a new era of encryption, leveraging more contemporary, robust, and efficient algorithms. This is one key distinction when considering SSL vs TLS certificate security.
- Key Algorithms:
- AES (Advanced Encryption Standard): A reigning champion in the encryption arena. Adopted across various platforms, AES offers potent security, making it a favorite for numerous applications, including browsers and email clients.
- ChaCha20: A sprightly contender to AES, ChaCha20 is known for its efficiency. Its adoption by giants like Google Chrome and Mozilla Firefox is a testament to its reliability and security.
- GCM (Galois/Counter Mode): Not just an encryption mode, GCM provides the dual advantage of encryption and authentication. A favorite among modern applications, it’s synonymous with security and efficiency.
TLS vs SSL is marked by evolution in protocols and encryption standards. TLS, with its avant-garde encryption algorithms, offers a sanctuary against modern cyber threats. For those still tethered to SSL, transitioning to TLS isn’t just a suggestion—it’s a cybersecurity imperative.
Credit: Freepik
Key Exchange Methods
In the arcane encryption dance, the cryptographic keys exchange choreograph initial steps. It’s a pivotal process, ensuring a secure channel for communication. But when juxtaposing TLS vs SSL, which protocol has the superior essential exchange repertoire? This comparison spotlights the critical exchange methods inherent in both, emphasizing the SSL certificate vs TLS certificate distinction.
SSL Key Exchange Methods
- Overview:
- As the earlier protocol, SSL facilitated secure conversations using several key exchange algorithms. Over the evolution of cyber threats, some methods, while revolutionary in their time, revealed limitations.
- Key Methods:
- RSA (Rivest–Shamir–Adleman): A public-key cryptosystem extensively utilized for key exchange and establishing digital signatures.
- Diffie-Hellman: Pioneering the arena of key exchange, this protocol enabled two entities to concoct a shared secret key even over non-secure channels.
TLS Key Exchange Methods
- Overview:
- Advancing from the SSL foundation, TLS introduced an expanded suite of essential exchange methods. This diversification underscores the SSL vs tls certificate
- Key Methods:
- RSA: Carrying forward the legacy of SSL, RSA remains a stalwart in the TLS key exchange paradigm.
- DHE (Diffie-Hellman Ephemeral): An evolved version of Diffie-Hellman, DHE employs transient keys, further fortifying security.
- ECDHE (Elliptic Curve Diffie-Hellman Ephemeral): Marrying the principles of DHE with elliptic curve cryptography, ECDHE promises enhanced security and optimized performance.
- SRP (Secure Remote Password): A notable addition, SRP enables a covert key exchange without divulging passwords to the counterparty.
- PQKE (Post-Quantum Key Exchange): Exclusive to TLS 1.3, PQKE is the futuristic armor designed to thwart potential quantum computing threats.
Their choice of crucial exchange methods like TLS vs SSL illuminates the strategic advance from SSL to TLS. TLS, armed with modern key exchange algorithms, is better equipped to face the dynamic cyber challenges of our era. Organizations operating within the SSL realm are encouraged to transition to TLS, optimizing for either TLS 1.2 or 1.3 to harness superior security and performance.
Security Vulnerabilities
The digital realm requires protocols to encrypt and protect data. While SSL and TLS serve this purpose, they have different evolutionary junctures in the cryptographic timeline. When you set TLS vs SSL against each other, the latter, being older, reveals specific susceptibilities. This dissection highlights the vulnerabilities inherent in SSL, accentuating the need for the superior security blanket of TLS.
SSL’s Security Vulnerabilities
- Overview:
- Since its inception, SSL has been the testing ground for many cyber threats. Over time, vulnerabilities emerged, which were subsequently exploited by nefarious entities.
- Key Vulnerabilities:
- POODLE (Padding Oracle On Downgraded Legacy Encryption): A loophole specific to SSL 3.0, POODLE lets malicious actors decrypt traffic. Given that SSL 3.0 is a relic of the past, it stands as a testament to the obsolescence of this protocol version.
- BEAST (Browser Exploit Against SSL/TLS): This exploit endangers data within web browsers utilizing either SSL or TLS. Its discovery spotlighted the need for fortifications in these protocols.
- Heartbleed: Not exclusive to SSL, this notorious vulnerability jeopardized servers employing TLS. It exposed vast troves of data, emphasizing the importance of robust, up-to-date cryptographic protocols.
While the narrative might seem tilted against SSL, it’s pivotal to acknowledge that TLS, especially in its nascent iterations, wasn’t impervious either. Throughout its evolution, however, most security chinks in TLS’s armor were identified and rectified.
Recommendation
In the constant skirmish against cyber threats, staying updated is the key. TLS 1.2 and 1.3 epitomize the zenith of secure cryptographic communication. If your operations are still entrenched in the SSL domain or earlier versions of TLS, consider migrating.
In an age where data breaches can spell disaster, shielding your database from potential threats is paramount. Dive deeper into the world of data protection with our comprehensive guide, “Database Defense Blueprint: Ensuring Data Security in a Connected World.” Equip yourself with strategies to fortify your data infrastructure against cyberattacks.
Credit: Freepik
Compatibility and Support
Navigating the virtual highways of the internet requires ensuring secure and seamless communication. While both SSL and TLS protocols provide this conduit, it’s evident that one outshines the other in compatibility and support. Here’s a breakdown contrasting TLS vs SSL on these parameters.
TLS Compatibility:
- Overview: If you’re vested in the TLS framework, communicating with other TLS devices should be straightforward.
- Backward Compatibility: TLS retains compatibility with SSL 3.0 and even 2.0. This feature enables more modern systems to communicate with those still on older SSL versions.
- Forward Compatibility Limitations: However, one pivotal distinction is the lack of forward compatibility. Devices leveraging TLS protocols can’t establish communication channels with those confined to the antiquated SSL 2.0.
TLS Support:
- Wide Adoption: The latter enjoys broader acceptance in the spectrum of SSL vs TLS. Be it major web browsers or web servers, TLS 1.2 and 1.3 have universal support.
- Legacy TLS Versions: TLS 1.0 and 1.1, although supported by the majority of browsers and servers, have been relegated to deprecated status, making them less ideal for use.
SSL’s Diminishing Stance:
- SSL 3.0: Once a standard, SSL 3.0 has been dethroned from its revered position due to inherent security flaws. Its support in modern-day browsers and servers is now virtually non-existent.
- SSL 2.0: Delving further back, SSL 2.0’s security vulnerabilities make it an unsuitable choice. Unsurprisingly, contemporary browsers and servers have discontinued its support entirely.
Recommendation
Ensuring you’re on the best platform between TLS vs SSL is crucial as the digital environment evolves. If your operations still orbit around the SSL universe, it’s time for a paradigm shift. Transitioning to TLS isn’t merely a suggestion; it’s a requisite for enhanced security and widespread compatibility.
Furthermore, be vigilant about updates about your web browser and other integral applications. In the ongoing tug-of-war between cyber threats and security measures, software updates play a pivotal role. Not only do they introduce innovative features, but they also act as fortifications against emerging vulnerabilities. So, keep your software arsenal updated to reap its functional and protective benefits.
Credit: Freepik
Message Authentication
In the expansive world of online communication, ensuring that messages remain untampered with is paramount. Both SSL and TLS protocols rise to this occasion, albeit in distinct ways. Delving into the TLS vs SSL debate from the lens of message authentication reveals some stark contrasts.
SSL’s Message Authentication
- MD5 (Message-Digest algorithm 5):
- Function: SSL predominantly relies on the MD5 algorithm to craft a message authentication code (MAC). The significance of MAC lies in its ability to confirm the integrity of a message and ensure it remains unaltered during transmission.
- Nature: MD5 is a cryptographic hash function designed to churn out a unique digital ‘fingerprint’ for every message it processes.
- Critique: Over the years, vulnerabilities associated with MD5 have surfaced, drawing concerns about its robustness as a security tool.
TLS’s Superior Authentication Methods
- SHA-256 (Secure Hash Algorithm 2):
- Function: In the SSL vs TLS certificate message authentication arena, TLS has transitioned to the SHA-256 algorithm for MAC generation.
- Advantages: Not only is SHA-256 recognized as a more formidable cryptographic hash function than its MD5 counterpart, but its efficiency also augments overall performance.
- AEAD (Authenticated Encryption with Associated Data) in TLS 1.3:
- Incorporation: With the advent of TLS 1.3, a novel message authentication paradigm has been introduced — AEAD.
- Dual Role: What sets AEAD apart is its dual functionality. It isn’t merely confined to authentication; it simultaneously encrypts the data. This concurrent operation enhances performance metrics and trims down latency.
As the tussle between TSL vs SSL continues, it’s evident that TLS offers a more contemporary and fortified approach to message authentication. By constantly evolving and adopting advanced algorithms like SHA-256 and AEAD, TLS showcases a commitment to superior security and efficiency.
If you’re still anchored in SSL’s framework, it’s an opportune moment to consider transitioning to TLS, especially given the latter’s advances in message authentication. This shift will ensure your data remains confidential and unaltered during its online journey.
Cipher Suites
The realm of digital communication thrives on ensuring security and integrity. One pivotal facet is cipher suites – combinations of cryptographic algorithms that dictate how data is encrypted and authenticated. Both SSL and TLS employ an array of cipher suites. However, when diving into the TLS vs SSL debate, TLS emerges with a more advanced and secure repertoire.
SSL’s Cipher Suites
- RC4-MD5:
- Description: An age-old cipher suite that has become antiquated in the contemporary cybersecurity scenario.
- Vulnerabilities: Its susceptibility to several attacks, notably the FREAK attack, has rendered it obsolete.
- DES-CBC3-SHA:
- Description: Another of SSL’s dated cipher suites.
- Evolution: Its days are numbered as the more robust AES has taken its place in newer protocols.
TLS’s Advanced Cipher Suites
- AES-GCM-SHA256:
- Description: A modern cipher suite that stands tall in security.
- Adoption: Favoured by many platforms – from web browsers to email clients and file encryption software.
- ECDHE-RSA-AES128-GCM-SHA256:
- Specialty: This cipher suite integrates elliptic curve cryptography, ensuring enhanced performance.
- Security: Its contemporary architecture ensures that data remains fortified against potential breaches.
In the juxtaposition of tls vs ssl cipher suites, TLS undeniably possesses the upper hand. The progressive nature of TLS cipher suites underscores the importance of transitioning from SSL. If the security of your data is paramount, an upgrade to TLS is not just a suggestion – it’s a necessity.
For those navigating the waters of TLS, opting for TLS 1.2 or 1.3 is a prudent choice, given their superior security frameworks. Moreover, in this ever-evolving digital epoch, staying updated is key. Ensure your web browsers and applications are always on the latest versions. These shields protect you from vulnerabilities and provide access to the latest cipher suites. The onus is on us to remain one step ahead in the cybersecurity game.
Application in web browsers and servers
In today’s internet landscape, data security is paramount, and the tools of choice for ensuring this security are cryptographic protocols like TLS vs SSL. Both are crucial in safeguarding sensitive data during transit, but their applications, especially in the context of modern web browsers and servers, vary significantly.
Transport Layer Security (TLS)
- Widespread Adoption: All major web browsers and servers utilize TLS to encrypt data traffic between them.
- TLS Handshake: A secure web browser and server connection is negotiated before data encryption commences. This TLS handshake process involves certificate exchanges and cipher suite agreements. Successful completion of the handshake signals that both parties can safely exchange encrypted information.
- Diverse Web Traffic Encryption: TLS isn’t just for website content. It encrypts various web traffic components, from HTTP headers to cookies and sensitive data like credit card numbers.
- Extended Application: Beyond web browsing, TLS plays a significant role in encrypting traffic between web servers and various applications, including email and file servers.
- Identification: A quick glance at the address bar is enough to ascertain if a website employs TLS. The presence of a lock icon and the “https://” prefix are clear indicators.
- Imperativeness of TLS: Given the abundance of cyber threats, using TLS becomes non-negotiable. It protects against unauthorized interception and tampering, especially when transmitting sensitive data.
Secure Sockets Layer (SSL)
- Legacy Protocol: SSL can be considered TLS’s predecessor. Over time, vulnerabilities in SSL led to its gradual phasing out in favor of the more robust TLS.
- Limited Modern Support: Due to the aforementioned vulnerabilities, most contemporary browsers and servers have deprecated SSL, opting instead for the enhanced security of TLS.
- Historical Importance: While TLS has largely overshadowed SSL in today’s applications, the importance of SSL in paving the way for secure web communication cannot be understated.
While both TLS vs SSL have played vital roles in web security, the modern web predominantly revolves around TLS, given its enhanced security features. As cyber threats evolve, so does the need for robust, dynamic security mechanisms. TLS stands as a testament to this evolution, safeguarding user data across the vast expanses of the digital realm.
Impact on website security and trust
The online landscape has become a battlefield where the trustworthiness and security of a website are equivalent to its success. TLS vs SSL are foundational pillars, offering encryption capabilities that safeguard data from malicious interception. However, how do they measure against each other when bolstering website trust and security?
Encryption and Data Protection:
- TLS: Encrypts data, ensuring it remains confidential and intact as it travels between the server and the browser. As a result, even if malicious entities manage to intercept the data, they can’t decipher its content.
- SSL: While SSL encrypts data, it relies on outdated cryptographic methods. TLS offers enhanced security with its modern encryption algorithms.
Authentication and Trustworthiness:
- TLS: Through digital certificates verified by reputable Certificate Authorities, TLS ascertains the authenticity of a website. This validation deters phishing attempts where malevolent sites masquerade as legitimate entities.
- SSL: SSL also uses certificates for authentication, but the potential vulnerabilities in its encryption methods can compromise the entire authentication process.
Search Engine Preference:
- TLS: Recognizing the importance of user security, search engines like Google prioritize websites that implement TLS, potentially improving their ranking in SERPs.
- SSL: Despite its historical significance, SSL doesn’t receive the same preference in modern search engines, mainly due to its known vulnerabilities.
Public Perception and Trust:
- TLS: Internet-savvy users often associate the “https://” prefix and the padlock icon with a secure browsing environment. Knowing a website employs TLS boosts their confidence in sharing personal and financial details.
- SSL: While SSL was once a mark of trust, its declining reputation for safety means it’s now less likely to instill the same confidence level among users.
Credit: Freepik
While both TLS vs SSL have their roots in ensuring website security, TLS emerges as the superior choice in the contemporary digital age, reflecting advancements in cryptographic research and a commitment to ironclad data protection. Website owners should prioritize transitioning to TLS for enhanced security and the implicit trust it fosters among users. Adopting TLS is not just a technological upgrade—it’s a pledge to prioritize user safety and data integrity.
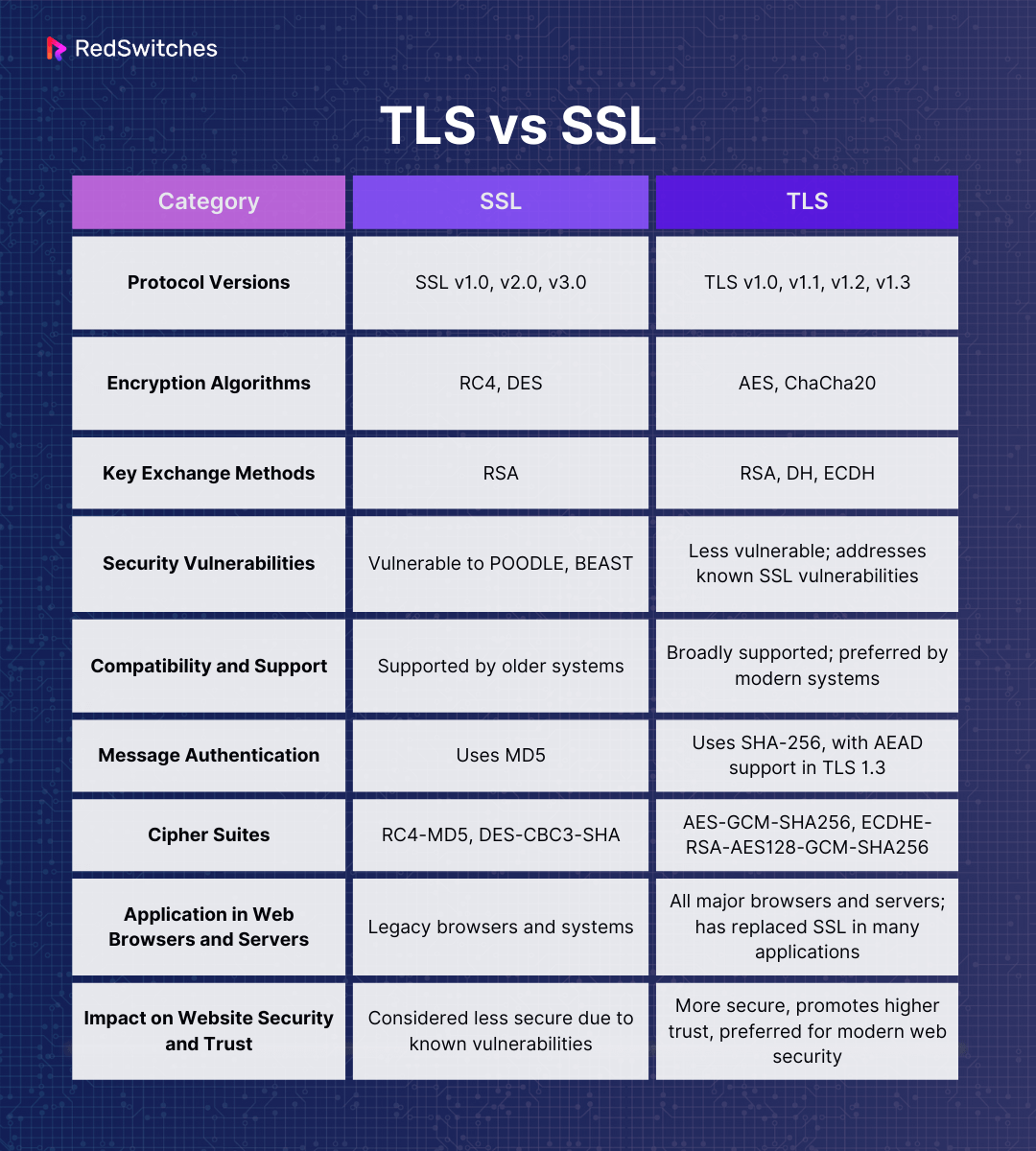
Here is a summarized table of comparison between TLS vs SSL:
Also Read: 12 Ways of Fixing ERR_SSL_VERSION_OR_CIPHER_MISMATCH Error
Is TLS Replacing SSL?
In the rapidly evolving cybersecurity domain, the transition from SSL (Secure Sockets Layer) to TLS (Transport Layer Security) signifies more than just a change—it represents a critical evolution. These frameworks form the backbone of secure online communications, ensuring that data retains its confidentiality and integrity while in transit. With the relentless advancements in the digital realm, the tools we deploy for safeguarding our data have to evolve concurrently.
The Reign of SSL: A Look Back
Historically, SSL was the undisputed champion for ensuring a secure web environment. It heralded a new era of web security and became an emblem of encrypted browsing, encapsulated by the now-familiar padlock icon in web browsers. But as the intricacies of the internet expanded, so did the nature and scale of potential threats. It wasn’t long before vulnerabilities began to surface within SSL, bringing to light the aging infrastructure and the limitations of its cryptographic techniques.
The Rise of TLS: Meeting Modern Needs
TLS, envisioned as the natural successor to SSL, stepped into this milieu. While it was built upon the foundation laid by SSL, TLS brought a series of refined encryption algorithms coupled with enhanced authentication protocols. Its primary mandate was to address and rectify the vulnerabilities that had become synonymous with SSL, offering users a safer and more secure browsing experience.
The Verdict: A Clear Shift to TLS
The gradual rise in TLS’s popularity wasn’t just due to its superior protective measures. Major web platforms and browsers began endorsing and supporting it, amplifying its reach and significance. In today’s context, it’s evident that TLS isn’t merely a replacement for SSL. In many contemporary digital applications, it has essentially overshadowed SSL, signaling a clear and decisive shift in the direction of web security norms.
Which Should You Pick?
When deciding between TLS vs SSL, the answer, in most cases, leans heavily towards TLS—and for good reason:
Security:
TLS employs state-of-the-art cryptographic methods, offering more protection against data breaches and malicious attacks than the aging SSL.
Authentication:
The rigorous authentication protocols of TLS ensure a higher level of trustworthiness, protecting users from phishing attempts and other deceptive practices that exploit website identities.
Search Engine Preference:
Websites utilizing TLS are given preferential treatment by leading search engines, potentially enhancing their visibility in search results.
Public Trust:
Modern internet users recognize and trust the “https://” prefix and the padlock symbol. Implementing TLS can enhance user confidence, making them more likely to engage with and share sensitive information on a website.
Future-Proofing:
As digital threats evolve, so will cybersecurity measures. Adopting TLS ensures you’re better aligned with the trajectory of digital security evolution instead of clinging to an increasingly obsolete SSL.
Managing your content securely is no longer just an option; it’s necessary. Enhance your CMS knowledge by diving into “CMS Security: 4 Types of Threats and 9 Tips To Prevent It.” Uncover the top threats lurking in the digital shadows and arm your website with proactive measures today.
Conclusion
In the constantly evolving landscape of TLS vs SSL, understanding the distinction and transition from SSL to TLS is crucial. While SSL laid the groundwork for encrypted communications, TLS has emerged as its modern counterpart, offering enhanced security protocols to counter the sophisticated threats of today’s digital world.
At the heart of this commitment to cybersecurity and innovation lie companies like RedSwitches. With their dedication to providing robust and state-of-the-art web hosting solutions, RedSwitches ensures that you’re not just keeping up with the times but also staying ahead of potential threats. Whether you’re an individual, a business, or an enterprise, navigating the waters of web security can be complex. But with partners like RedSwitches, you’re empowered with the tools and expertise to make informed decisions.
Are you ready to fortify your online presence with advanced security measures? Dive into secure hosting with RedSwitches and confidently embrace the future. Explore RedSwitches Now!
FAQs
Q. What is the difference between TLS and SSL?
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are cryptographic protocols that provide secure network communication. SSL is older and has known vulnerabilities, making it less secure than TLS. TLS is the newer protocol that addresses many vulnerabilities in SSL.
Q. Is TLS better than SSL?
Yes, TLS is better than SSL in terms of security and performance. TLS provides more robust encryption algorithms and has addressed the known vulnerabilities of SSL, making it the recommended protocol for secure communications.
Q. Does HTTPS use SSL or TLS?
HTTPS can use SSL or TLS, depending on the server’s configuration and the client’s capabilities. However, modern web servers and browsers predominantly use TLS due to its enhanced security features, and many have phased out support for older versions of SSL.
Q. What is the difference between SSL and TLS?
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are cryptographic protocols that provide secure communication over a computer network. TLS is essentially an updated, more secure version of SSL.
Q. How do SSL and TLS certificates work?
SSL and TLS certificates are used to establish a secure connection between a web server and a browser. They help encrypt data and verify the identity of the server, ensuring secure communication.
Q. What is the history of SSL and TLS?
SSL was first developed by Netscape in the mid-1990s and its subsequent versions, 2.0 and 3.0, had security flaws. TLS was introduced as an improved protocol, with versions 1.0, 1.1, 1.2, and the latest 1.3.
Q. Why is SSL deprecated?
SSL has been deprecated due to several security vulnerabilities and flaws found in its protocols. It is no longer considered secure and has been replaced by TLS for secure communication.
Q. How does the SSL/TLS handshake work?
The SSL/TLS handshake is the process where the client and server establish a secure connection. It involves negotiating the cryptographic algorithms and exchanging keys to encrypt the data.
Q. Which version should I use, TLS 1.2 or TLS 1.3?
TLS 1.3 is the latest and most secure version, offering improved performance and security features compared to TLS 1.2. It is recommended to use TLS 1.3 if supported.
Q. Can I use SSL certificates with TLS?
Yes, SSL certificates can be used with TLS, as TLS is designed to be backward compatible with SSL. However, it is advisable to migrate to TLS certificates for better security.
Q. How can I disable SSL and support only TLS?
You can disable SSL and support only TLS by configuring your web server to prioritize TLS over SSL. This ensures that only TLS connections are accepted for secure communication.
Q. What are the similarities and differences between SSL and TLS?
SSL and TLS both provide secure communication over a network, but TLS is an improved and more secure version of SSL. They share similarities in terms of encryption methods and the handshake process.
Q. Can I install an SSL certificate for HTTPS?
Yes, you can install an SSL certificate for securing your website with HTTPS. However, it is recommended to use TLS certificates for better security and compatibility with modern browsers.