Key Takeaways
- DDoS Attacks Overload Websites. They flood sites with too much traffic, causing disruption.
- Various Attack Types Include volumetric, protocol, application layer, amplification, and multi-vector attacks.
- Spotting DDoS Attacks, Look for sudden traffic spikes, slow network, disrupted services, odd server logs, and user complaints.
- Be Prepared, Strengthen your network, set security measures, and have a response plan.
- Use Technology and implement firewalls, content delivery networks (CDNs), and anti-DDoS tools.
- Quick Response is Key, Detect attacks early, activate your plan, and communicate effectively.
- Work with ISPs, Collaborate with your Internet Service Provider for additional support.
- After the Attack, Analyze what happened, update security, and learn from the experience.
- Amazon’s 2020 Attack was the Largest DDoS attack in history, showing the need for strong security.
- Stay Updated and Informed, Regularly monitor your network, update systems, and keep abreast of new threats.
Distributed Denial of Service (DDoS) attacks are a growing threat in our digital world. In recent years, these attacks have become more common and damaging. They can shut down websites, disrupt services, and cause significant inconveniences. In 2023, a report showed a significant increase in these attacks. Retail and public relations websites were mainly targeted during busy times like Black Friday.
This article is designed to help you understand DDoS attacks and how to respond effectively. We will cover these attacks, their dangers, and how they affect your online presence. Whether you’re an IT expert, a business owner, or just someone who uses the internet, this guide will provide valuable information.
Our goal is to offer clear, straightforward advice. We will give you practical steps to protect your digital space from these cyber threats. The article is easy to read and understand, making it accessible.
Table Of Contents
- Key Takeaways
- What is a DDoS Attack?
- How to Identify a DDoS Attack
- Preparation and Prevention Strategies
- Responding to DDoS Attacks: Emergency Procedures
- The Largest DDoS Attack in History
- Minimize Your Risk of a DDoS Attack
- Conclusion: Stay Ahead in the Fight Against DDoS Attacks
- FAQs
What is a DDoS Attack?
Credits: Freepik
A DDoS attack is when many computers flood a website with too much traffic. Imagine a road jammed with cars so that no one can move. That’s like a DDoS attack on a website. The website gets so many requests it can’t handle them all. This can make the website slow or unavailable. Hackers often use hijacked computers or devices for these attacks. They aim to overload websites or networks, causing significant problems. These attacks can target any online service, big or small. Understanding DDoS is vital to protecting your digital space.
How Does a DDoS Attack Work?
Credits: Freepik
A DDoS attack is like a traffic jam on the internet. It starts when hackers control many devices across the globe. They use malware to create a ‘botnet,’ a big group of infected devices. The hackers then pick a target, such as a website. They command their botnet to flood this website with requests. These requests are overwhelming in number and speed, far more than the website can handle.
This flood of requests is like too many cars on a road. The website tries to handle them all, but soon, it gets overwhelmed. It becomes very slow or stops working altogether. This is the disruption that the hackers aim for. It stops legitimate users from accessing the website. This can lead to lost business, damage to reputation, and other problems.
There are different types of DDoS attacks. Some fill the website with massive amounts of data. Others target the network layer, where data gets transferred. Some are even more complex, focusing on specific parts of a website or service. No matter the type, the goal is always to cause disruption and damage.
Also, Read What Is Cloud Data Security? Definition, Types & Benefits
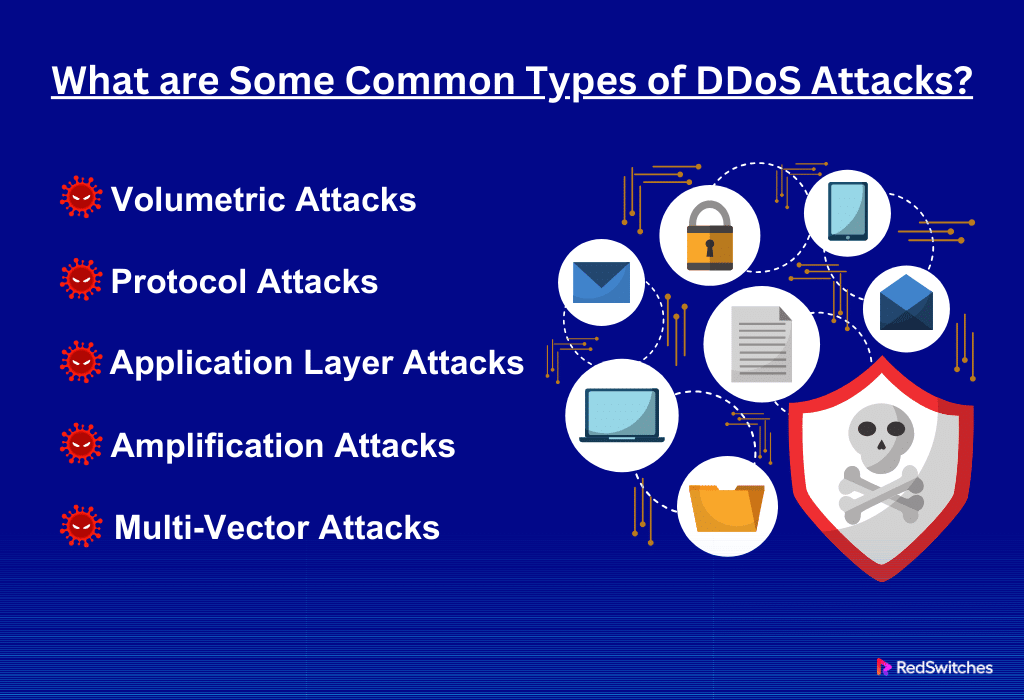
What are Some Common Types of DDoS Attacks?
DDoS attacks come in various forms, each with its unique method of disrupting services. Understanding these types helps in better preparing and responding to such attacks.
Volumetric Attacks:
The most common type, these attacks flood a network with excessive traffic.
The aim is to use up all available bandwidth so legitimate traffic can’t get through. Attackers often use techniques like UDP or ICMP (Ping) floods in these attacks.
Protocol Attacks:
These target the network layer and dedicated server resources. Protocol attacks aim to consume server resources or those of intermediate communication equipment like firewalls and load balancers.
A common example is a SYN flood, where the attacker sends a flood of SYN requests to a server but never completes the handshake. It leaves connections hanging open, using up the dedicated server’s resources.
Application Layer Attacks:
These are more sophisticated and target-specific applications. The goal is to crash the web dedicated server. This type of attack is harder to detect because it can mimic or involve legitimate requests. A common method is a slow loris attack, where the attacker sends partial requests to a web server, keeping connections open for as long as possible.
Amplification Attacks:
These involve a reflection and amplification strategy. The attacker sends a small query to a server, which responds with a much larger reply to the targeted victim’s IP address. DNS amplification attacks are a typical example, where the attacker exploits vulnerabilities in DNS dedicated servers to turn small queries into large payloads aimed at the victim.
Multi-Vector Attacks:
Modern DDoS attacks often combine several of these methods. This makes them more complex and more challenging to defend against. For instance, an attacker might use a volumetric attack to distract the defense while launching a more subtle application layer attack.
Each type of DDoS attack poses unique challenges and requires tailored defense strategies. Understanding these common types is the first step in building effective defenses against these disruptive cyber threats.
Also, Read Top 10 Secure Web Hosting Practices for 2024
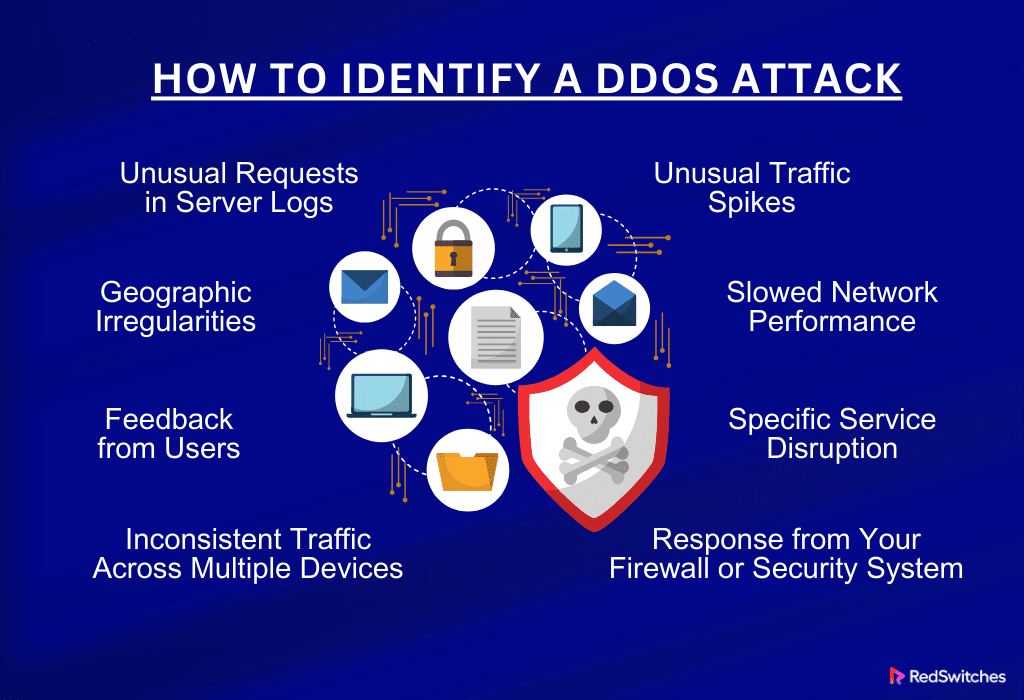
How to Identify a DDoS Attack
Credits: Freepik
Recognizing a DDoS (Distributed Denial of Service) attack early is crucial in mitigating its impact. Several signs can help identify these attacks. Understanding these indicators will enable you to respond swiftly and effectively.
Unusual Traffic Spikes
One of the most apparent signs of a DDoS attack is a sudden, unexplained increase in traffic. This can be observed in your website’s analytics. Unlike regular traffic spikes, which might occur during a sale or a marketing campaign, these are unexpected and dramatic. Monitoring your traffic patterns regularly helps in noticing these anomalies.
Slowed Network Performance
Another common symptom is a significant slowdown in network performance. This does not just mean a slow website; it can also affect other online services. If your website, email, or other online systems become unusually slow without an apparent reason, it could indicate a DDoS attack.
Specific Service Disruption
DDoS attacks may target specific parts of your service. For instance, if a particular feature of your website, like the checkout process or the login page, stops working while others usually function, it could be under attack.
Unusual Requests in Server Logs
Checking server logs is a more technical but effective way to identify DDoS attacks. Look for patterns like an unusually high number of requests from a single IP address or a range of IP addresses. These could be bots involved in the attack.
Response from Your Firewall or Security System
Modern firewalls and security systems are designed to detect potential DDoS attacks. If your system sends alerts about blocking unusually high traffic levels or specific network requests, it’s worth investigating further.
Feedback from Users
Sometimes, the first signs of a DDoS attack come from the users. If multiple users report issues like not being able to access your website or specific features, it’s a potential warning sign.
Geographic Irregularities
If your analytics show an unusual amount of traffic from regions where you normally don’t have many users, it could be a part of a DDoS attack. Attackers often use botnets spread across various locations.
Inconsistent Traffic Across Multiple Devices
Lastly, if the traffic on your website or network shows inconsistency across different devices or platforms, it might be due to a DDoS attack. For example, the site might work fine on a mobile phone but not on a desktop.
Recognizing these signs promptly can help you take immediate action, minimizing the attack’s impact.
Preparation and Prevention Strategies
Credits: Freepik
To defend against DDoS attacks, preparation and prevention are key. Implementing proactive strategies can significantly reduce the risk and impact of these attacks. Here’s how you can prepare and prevent DDoS attacks effectively.
Strengthen Your Network Infrastructure
Building a robust network infrastructure is crucial. Ensure your web hosting service has sufficient bandwidth to handle unexpected traffic surges. Cloud-based services can also be beneficial as they offer better scalability and security.
Also, Read Server Downtime: Causes, Effects, and How to Prevent It
Implement Network Security Measures
Deploy advanced firewall configurations and intrusion detection systems. These can identify and mitigate suspicious traffic patterns. Regularly update your security systems to protect against the latest threats.
Credits: Freepik
Create a DDoS Response Plan
A response plan can significantly reduce the time it takes to react to an attack. This plan should include identifying the attack, notifying the team, and implementing mitigation strategies. Regular drills will help your team respond effectively under pressure.
Employ Content Delivery Networks (CDNs)
CDNs can distribute your content across multiple dedicated servers. This not only speeds up content delivery but also makes it harder for attacks to target your primary server.
Monitor Traffic Regularly
Regular monitoring of network traffic can help you identify potential DDoS threats early. Set up alerts for unusual traffic patterns or spikes in network activity.
Keep Your Systems Updated
Ensure all your software, including operating systems and applications, is current. This reduces vulnerabilities that attackers can exploit.
Train Your Staff
Educate your staff about DDoS attacks and the importance of following security protocols. They should be aware of how to recognize and report potential threats.
Collaborate with Your ISP
Credits: Freepik
Your Internet Service Provider (ISP) can be a valuable ally in mitigating DDoS attacks. Discuss potential threats with them and understand the services and support they can offer in case of an attack.
Back-Up Your Data
Regularly back up your data. In the event of an attack, you will have a secure copy of your critical data, which can be crucial for recovery.
Use Anti-DDoS Services
There are specialized services and tools designed to protect against DDoS attacks. Consider investing in these services for enhanced security.
Taking these preventive measures can significantly strengthen your defenses against DDoS attacks. While it’s impossible to prevent all attacks, being well-prepared can minimize their impact and ensure a quick recovery.
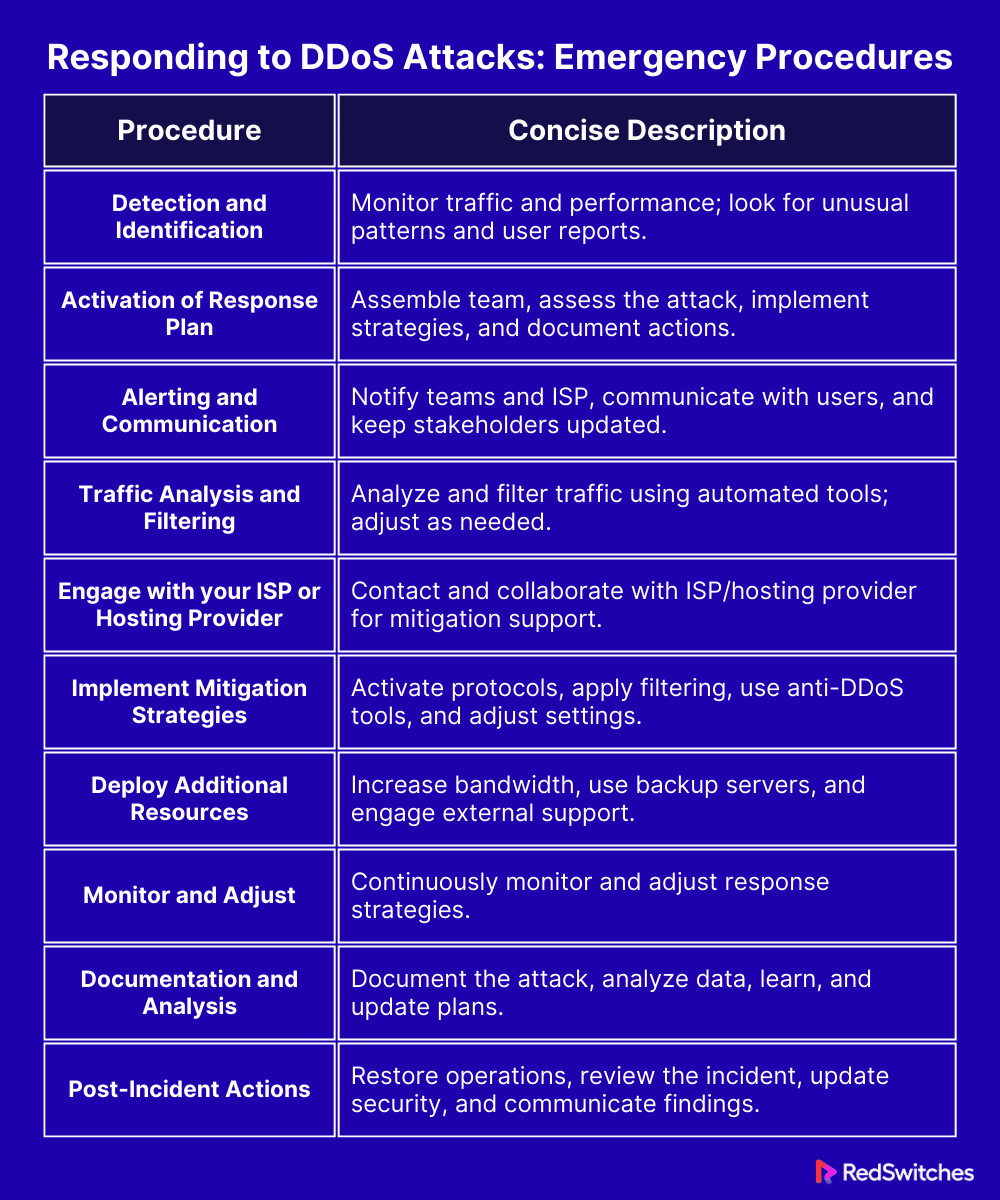
Responding to DDoS Attacks: Emergency Procedures
Credits: Freepik
Before delving into the specifics of emergency procedures for responding to DDoS attacks. It’s important to understand that the response phase is critical. Once an attack is identified, your actions can either minimize the damage or, if mismanaged, exacerbate the situation. The following section outlines essential steps to take during a DDoS attack. This guidance aims to help you navigate the crisis efficiently and restore normal operations as swiftly as possible.
Also, Read 11 Dedicated Server Security Best Practices
Detection and Identification
When under a DDoS attack, the first step is to detect and identify it accurately. Quick detection is key to reducing damage. Here are simple ways to do this:
- Monitor Traffic: Keep an eye on your website’s traffic. A sudden, unusual increase is often the first sign of an attack.
- Check Website Performance: If your website or services start slowing down for no clear reason, it could be a DDoS attack. This slowdown is because the attack overwhelms your systems with requests.
- Look for Patterns: Sometimes, certain website features stop working while others are fine. This could be a targeted part of the attack.
- Use Security Tools: Employ security tools that can alert you to potential DDoS activity. These tools can detect unusual patterns that humans might miss.
- Listen to User Reports: Pay attention to user complaints. If multiple users are having trouble accessing your services, it could be due to an attack.
You can move swiftly to the next step by quickly identifying a DDoS attack.
Activation of Response Plan
Once a DDoS attack is detected, immediately activate your response plan. This plan should be a well-documented procedure that your team is familiar with. Here’s how to activate it:
- Assemble Your Team: Quickly gather your response team. This team should include members from IT, security, and communications departments.
- Assess the Situation: Evaluate the scope and scale of the attack. Understanding the severity will guide your response efforts.
- Implement Mitigation Strategies: Use pre-defined strategies like rate limiting or IP blocking to reduce the attack’s impact. If you have anti-DDoS services, now is the time to leverage them.
- Document Everything: Keep a record of all actions taken. This documentation will be crucial for post-incident analysis and improving future responses.
Activation of the response plan should be swift and efficient, aiming to minimize the attack’s impact as much as possible.
Alerting and Communication
Effective communication is critical during a DDoS attack. Here’s how to handle alerting and communication:
- Notify Internal Teams: Immediately inform all relevant internal teams about the attack. Clear communication helps in coordinating the response.
- Inform Your ISP: Contact your Internet Service Provider. They can often assist in mitigating the attack and might provide additional resources.
- Communicate with Users: Keep your users informed about the situation. Use social media, email, or your website to relay updates. Transparency builds trust.
- Contact External Support: If you have a third-party security provider, contact them for additional support.
- Continuous Updates: Provide regular updates to all stakeholders. Keeping everyone informed helps manage expectations and reduces panic.
Clear and timely communication during a DDoS attack ensures everyone is on the same page and can respond appropriately.
Traffic Analysis and Filtering
Analyzing and filtering traffic is vital in responding to a DDoS attack. Here’s how to do it:
- Analyze Traffic Patterns: Look at the traffic to identify which is legitimate and which is part of the attack. Pay attention to source IP addresses, types of requests, and traffic volume.
- Set Up Filters: Once you identify malicious traffic, set up filters to block it. This can be IP-based or by the type of traffic. Filtering helps reduce the load on your dedicated server.
- Use Automated Tools: Employ automated tools for real-time analysis and filtering. These can adjust to changing attack patterns more quickly than manual methods.
- Monitor Effectiveness: Continuously monitor the effectiveness of your filters. Adjust them as needed based on ongoing traffic analysis.
Practical traffic analysis and filtering can significantly reduce the impact of a DDoS attack, allowing legitimate traffic to flow normally.
Also, Read What is a Network Firewall? Exploring Server Security and How Firewalls Work in 2024
Engage with your ISP or Hosting Provider
Working with your Internet Service Provider (ISP) or hosting provider is crucial in a DDoS attack. Here’s how to engage with them:
- Immediate Contact: Contact your ISP or hosting provider when you detect an attack. They have more resources and experience in handling such situations.
- Share Information: Provide them with details about the attack. This includes the type of DDoS attack, affected services, and any traffic analysis you have.
- Collaborate on Mitigation: Work together to implement mitigation strategies. Your provider may have additional tools or strategies to help reduce the impact.
- Seek Advice: Ask for their advice on additional steps you can take. They might offer solutions you hadn’t considered.
- Ongoing Communication: Maintain open lines of communication with your provider for the duration of the attack. Regular updates can help in effectively managing the situation.
Engaging with your ISP or hosting provider offers additional expertise and resources to combat a DDoS attack.
Implement Mitigation Strategies
Once you have identified a DDoS attack, implementing mitigation strategies is crucial. Here are key steps to follow:
- Activate Predefined Protocols
Utilize predefined mitigation protocols. This may include rate limiting, IP address blocking, or rerouting traffic.
- Rate Limiting:
Rate limiting is a security technique that controls the incoming traffic flow by setting a maximum acceptable rate for requests within a specific timeframe. Think of it as a speed limit for requests to access your system. Any request exceeding the limit gets slowed down, throttled, or blocked entirely.
- IP Address Blocking:
Blocking specific IP addresses suspected of participating in the DDoS attack, preventing them from sending further requests.
- Traffic Rerouting:
Diverting incoming traffic from the targeted server to a scrubbing center or alternate server, filtering out malicious traffic before it reaches the target.
- Apply Advanced Filtering: Implement advanced filtering strategies to differentiate between legitimate and malicious traffic. This helps in reducing false positives.
- Leverage Anti-DDoS Solutions: If you have anti-DDoS software or hardware, now is the time to use it. These solutions are designed to absorb and mitigate DDoS attacks.
- Adjust Scalability Settings: If using cloud-based services, adjust your scalability settings to handle increased traffic without impacting performance.
- Constant Monitoring: Keep monitoring the situation. Be prepared to adjust your strategies as the attack evolves.
Timely implementation of these strategies can significantly diminish the DDoS attack’s impact, helping maintain your services’ availability.
Deploy Additional Resources
Deploying additional resources is crucial to responding to a DDoS attack. Here’s how you can do it effectively:
- Increase Bandwidth: Temporarily increase your bandwidth capacity to handle the excess traffic. This can provide a buffer against the flood of requests.
- Utilize Backup Servers: If you have backup dedicated servers, bring them online. This can help distribute the load and keep your services running.
- Engage External Support: Consider bringing external cybersecurity experts or services specializing in DDoS mitigation.
- Activate Cloud-Based Resources: Use cloud-based resources to absorb and distribute traffic. Cloud services often offer greater flexibility in handling traffic spikes.
- Coordinate with Your Team: Ensure your IT and security teams are fully staffed and prepared for extended operations during the attack.
Deploying these additional resources can support you to withstand a DDoS attack and keep your systems operational.
Monitor and Adjust
Continuous monitoring and adjustment are essential in managing a DDoS attack. Here’s what you need to do:
- Keep an Eye on Traffic: Regularly monitor your network traffic. Look for changes in the pattern or volume of the attack.
- Assess Mitigation Success: Evaluate the effectiveness of your mitigation strategies. Are they reducing the impact of the attack? If not, adjustments are needed.
- Adjust Filters and Settings: Reak your filters and settings based on your observations. The goal is to block malicious traffic while allowing legitimate users access.
- Stay Alert: Be prepared for the attack to evolve. Hackers often change tactics, so your response should be flexible.
- Engage with Your Team: Constantly communicate with your response team. Share insights and make collective decisions on adjustments.
This continuous process of monitoring and adjusting helps you stay one step ahead of the attack, minimizing its impact.
Also, Read Security Benefits of Cloud Computing: Is Your Business Safe?
Documentation and Analysis
Documenting and analyzing every aspect of a DDoS attack is crucial for future preparedness. Here’s how to approach it:
- Record Everything: Document every step of the attack and your response. This includes the time the attack started, its intensity, the measures taken, and their effectiveness.
- Gather Data: Collect all relevant data from your network monitoring tools, security systems, and server logs.
- Analyze the Attack: Post-attack, analyze this data to understand the attack’s nature, source, and impact. Look for patterns or vulnerabilities that were exploited.
- Learn from the Experience: Use this analysis to identify strengths and weaknesses in your response. What worked well? What could be improved?
- Update Your Plan: Based on these insights, update your response plan and mitigation strategies. This ensures better preparedness for future attacks.
Documenting and analyzing the attack helps refine your strategies, making your system more resilient against future threats.
Post-Incident Actions
After a DDoS attack has been mitigated, taking post-incident actions is essential. These steps are vital for recovery and future preparedness. Here’s what you should do:
- Restore Normal Operations: Ensure all systems are back online and functioning normally. Check that all security measures are re-enabled.
- Conduct a Thorough Review: Analyze the incident in detail. What was the extent of the damage? How effective were your response and mitigation strategies?
- Update Security Measures: Based on your analysis, update your security protocols. Patch any vulnerabilities that were exploited during the attack.
- Communicate with Stakeholders: Inform your stakeholders about the attack and how it was handled. Transparency is key to maintaining trust.
- Prepare a Detailed Report: Document the entire incident in a report. Include what happened, how it was addressed, and what measures will be taken to prevent future attacks.
- Review and Update the Response Plan: Revisit your DDoS response plan. Incorporate lessons learned from the incident to strengthen your future response.
Taking these post-incident actions helps you recover from the current attack and fortify your defenses against potential future attacks.
This table efficiently encapsulates each section’s key points in the DDoS response plan.
The Largest DDoS Attack in History
Credits: Freepik
When discussing cyber threats, DDoS attacks are a big deal. They can shut down websites and services, causing a lot of problems. The largest DDoS attack ever recorded is a key example of how serious these attacks can be.
The Record Attack
The biggest DDoS attack happened in February 2020. It targeted Amazon Web Services (AWS), a major online service many websites use. This attack was huge – the biggest ever seen. It sent massive data to AWS – like 15 million people trying to visit a website simultaneously.
How Big Was It?
This attack was really big. It used a lot of data – 2.3 terabits per second. That’s a lot of internet traffic! The attackers used a smart method to make their attack stronger. This made it a tough challenge, even for a big company like Amazon.
Amazon did a great job in stopping this attack. They had strong security and were ready for such problems. They used special tools and methods to protect their service. This shows how important it is to be ready for cyber attacks.
Learning from the Attack
This big attack teaches us some things. First, everyone must be careful about cyber threats, no matter how big or small their business is. It’s important to have good security on your websites and online services. Also, having a plan for what to do during an attack is very helpful.
Looking Ahead
Cyber attacks are always changing and getting more complex. The attack on Amazon is a reminder that no one is completely safe from these threats. Businesses and services need to keep improving their security. Staying safe online is an ongoing effort.
This big attack was a serious event in the world of cyber security. It showed how important it is to have strong security and always to be ready for new challenges.
Also, Read Top 15 Critical Cyber Security Challenges and How to Fix Them
Minimize Your Risk of a DDoS Attack
Credits: Freepik
In today’s digital world, DDoS (Distributed Denial of Service) attacks are a real threat. They can take down websites and disrupt services. But don’t worry, and there are ways to lower the risk of these attacks. Let’s explore how you can protect yourself and your online presence.
Understanding the Risk
First, know what a DDoS attack is. It’s like a flood of traffic to your website or service. This flood is so much that your site can’t handle it and might stop working. Think of it as a traffic jam on the internet.
Strengthen Your Defenses
The first step in reducing risk is to build strong defenses. This means ensuring your website and network are tough enough to handle unexpected traffic.
Upgrade Your Hardware
Having good hardware is like having strong doors in your house. It can help stop the flood of traffic from a DDoS attack. Upgrade your servers and network equipment to handle more traffic.
Use Security Software
Security software is like a guard for your website. It can spot and stop harmful traffic. Make sure you have the latest security software and keep it updated.
Plan and Prepare
Having a plan is key. If an attack happens, you need to know what to do.
Create a Response Plan
A response plan is a set of steps to follow during an attack. It’s like having a map in a storm. Make sure your team knows the plan and practices it.
Train Your Team:
Your team should know about DDoS attacks and how to handle them. Regular training can keep everyone ready and alert.
Partner with Professionals
Sometimes, you need extra help. This is where professional services come in.
Work with Your ISP
Your Internet Service Provider (ISP) can greatly help. They can offer tools and support to stop DDoS attacks. Talk to them about what they can do.
Use DDoS Protection Services
There are services just to stop DDoS attacks. They can add an extra layer of protection to your website.
Regular Monitoring
Keeping an eye on your website is important. It’s like watching the weather. If a storm is coming, you want to know early.
Monitor Your Traffic
Watch the traffic on your website. Look for sudden changes or spikes. This can be a sign of an attack.
Backup and Update:
Always have a backup. If your website goes down, you can use your backup to get back online quickly. And keep everything updated – your software, your security, everything.
Stay Informed
Lastly, stay informed about cyber threats. The world of technology changes fast. Keeping up with the latest news and updates can help you stay one step ahead.
Following these steps can greatly reduce your risk of a DDoS attack. Remember, preparation and awareness are your best tools in the fight against cyber threats.
Conclusion: Stay Ahead in the Fight Against DDoS Attacks
In this digital age, staying safe online is more important than ever. DDoS attacks are a big challenge, but you can beat them. Remember, the key is to be ready before anything happens. Keep your defenses strong and have a plan. Work with your team and use the right tools to stay safe.
When it comes to fighting DDoS attacks, RedSwitches is a great choice. They offer top-notch protection to keep your online world safe. With RedSwitches, you get strong defenses and expert help. This means you can focus on your business without worrying about cyber threats.
Don’t wait for an attack to happen. Get ahead and stay safe. Check out RedSwitches today and find out how they can help protect you from DDoS attacks. Be smart, be secure, and keep your digital space safe with RedSwitches.
FAQs
Q. What is the response to a DDoS attack?
The response to a DDoS attack typically involves several steps. First, detect the attack. Then, activate a response plan. After that, analyze the traffic to distinguish between legitimate and malicious requests. Then implement mitigation strategies such as traffic filtering and rate limiting. Lastly, engage with your ISP for additional support. These strategies must be monitored and adjusted continuously until the attack is mitigated.
Q. How do you defend against DDoS attacks?
Defending against DDoS attacks involves both preparation and real-time response. Key defensive strategies include enhancing network infrastructure, using advanced security systems like firewalls and DDoS protection services, regularly updating and patching systems, and monitoring network traffic for unusual activity. Additionally, having a well-practiced response plan and training staff on DDoS attack recognition and protocols is essential.
Q. How do companies respond to DDoS attacks?
Companies respond to DDoS attacks by identifying the attack through traffic analysis and deploying their pre-arranged response plans. This includes using automated anti-DDoS mechanisms, applying traffic filters, and possibly scaling up bandwidth. Companies also often work closely with their ISPs or cloud service providers for additional support and resources to mitigate the attack. Post-attack, companies analyze the incident for lessons learned and future improvements.
Q. How are DDoS attacks handled?
DDoS attacks are handled by initially identifying the attack, followed by implementing mitigation strategies such as traffic filtering, employing anti-DDoS solutions, adjusting network configurations, and possibly increasing network capacity. Coordination with ISPs and hosting providers is also joint for additional mitigation support. Continuous monitoring and adjustment of strategies are essential until the attack subsides, followed by a thorough post-incident analysis.
Q. What are some common DDoS attack tools and techniques used by attackers?
Attackers use various tools and techniques, including botnets, amplification attacks, application layer exploits, and SYN flood attacks to launch DDoS attacks and disrupt the target’s services.
Q. Why is DDoS protection important for businesses and organizations?
DDoS protection is important for businesses and organizations to ensure the availability and reliability of their online services, mitigate financial losses, and safeguard their reputation from the damaging effects of DDoS attacks.
Q. How can businesses defend against application layer DDoS attacks?
Businesses can defend against application layer DDoS attacks by using web application firewalls (WAFs), implementing HTTP request inspection, and monitoring and filtering incoming traffic for suspicious patterns or requests.
Q. How does a DDoS attack work?
DDoS attacks work by sending an overwhelming amount of traffic to a target, causing it to become slow, unresponsive, or even completely unusable. Attackers often use a network of botnets to carry out these attacks, making it difficult to trace the source of the attack.
Q. How can DDoS attacks be mitigated?
DDoS attacks can be mitigated using various techniques such as deploying DDoS mitigation services, firewalls, and intrusion prevention systems, implementing rate limiting, and partnering with ISPs to filter malicious traffic. One can also employ various strategies such as using specialized DDoS mitigation services, routers to filter attack traffic, and implementing rate limiting or access control lists.
Q. What is the aim of a volumetric DDoS attack?
A volumetric DDoS attack aims to overwhelm the target with massive traffic, consuming all available bandwidth and resources to make the network or service inaccessible to legitimate users.
Q. Are DDoS attacks a form of cyber attack?
Yes, DDoS attacks are considered cyber attack as they involve the deliberate disruption of digital services and networks using unauthorized access and manipulation of internet traffic.
Q. How can DDoS attackers continue their attacks across multiple targets?
DDoS attackers can continue their attacks by leveraging botnets, networks of compromised devices controlled by the attacker. This allows them to distribute attack traffic across multiple sources.
Q. What are some common attack vectors used in DDoS attacks?
Common attack vectors used in DDoS attacks include UDP floods, SYN floods, HTTP floods, and ICMP floods, each targeting different aspects of the network or application infrastructure.
Q. What are the different types of DDoS attacks?
DDoS attacks come in various forms, including volumetric attacks, protocol attacks, and application layer attacks. Volumetric attacks aim to overwhelm a network by flooding it with high traffic volume, while protocol attacks target the network infrastructure. Application layer attacks focus on exploiting vulnerabilities in web applications or servers.
Q. What is the difference between DoS and DDoS attacks?
A single source carries out a DoS (Denial of Service) attack. In contrast, a DDoS (Distributed Denial of Service) attack involves multiple sources, often many compromised devices or systems coordinated to target a single entity.
Q. What is a layer 7 DDoS attack?
A layer 7 DDoS attack, also known as an application-layer attack, targets the application layer of the OSI model. This attack focuses on exploiting vulnerabilities in web applications or servers, aiming to disrupt the normal functionality of the targeted resources.