Digital technology and data will undoubtedly become crucial to some elements of your life in the modern world. Your job, relationships, housing situation, and other factors could all play a role. For instance, you depend on technology and data if you manage a business. Unfortunately, some with malicious intent are eager to steal the data that your company and you need to run. Even though their motives vary, malevolent actors typically aim to profit from your devices and data or cause them to malfunction.
It is also startling to learn that, according to a recent Insight survey, more than 70% of corporate executives need more confidence in the resilience of their organizations against potential cyberattacks. Due to these worries, many businesses develop optimal frameworks to maintain, monitor, and turn off cybersecurity dangers in advance.
Table of Contents
- What Can You Do In These Conditions To Get The Best Cybersecurity?
- What Is A Cybersecurity Framework?
- Why Cybersecurity Standards And Frameworks Are Needed?
- Risks Involved In The Absence Of Cybersecurity Standards And Frameworks
- Top Cybersecurity Frameworks
- How Service Providers Can Help Organizations In Implementing Cybersecurity Frameworks
- Conclusion
- FAQs
What Can You Do In These Conditions To Get The Best Cybersecurity?
Data security solutions and database security are two strategies for achieving a suitable level of cybersecurity. Adopting a cybersecurity framework is frequently the most effective approach to achieving this goal. The methodology and structure needed to safeguard your critical digital assets are provided by a framework.
Although cybersecurity frameworks provide various “recommended practices” for assessing risk levels and establishing controls, choosing the right one for your organization can be daunting.
What Is A Cybersecurity Framework?
It’s a compilation of guidelines, suggestions, and optimal practices for managing threats in the digital realm. Security objectives, like thwarting unauthorized system entries, frequently align with controls, such as necessitating a username and password.
If that still needs to be clarified, it could be helpful first to comprehend a framework. A framework in the real world is a structure of beams that support a building. A framework is a supporting structure for a system or concept in the world of ideas. A framework is a method of categorizing data and, most often, associated tasks.
Frameworks have existed for a very long time. Accounting frameworks, for instance, assist accountants in keeping track of financial transactions. Concepts like assets, liabilities, costs, and controls are the foundation of an accounting framework.
Cybersecurity blueprints address the defense of digital assets from threats through a structured approach. Such blueprints offer security professionals a reliable, systematic method to minimize cyber threats, no matter the intricacy of the setting.
For enterprises aiming to align with domestic, sector-specific, and global cybersecurity norms, these blueprints are often mandated or, at minimum, highly recommended. For example, a business must clear an evaluation confirming its adherence to the Payment Card Industry Data Security Standards (PCI DSS) blueprint to process credit card transactions.
Why Cybersecurity Standards And Frameworks Are Needed?
Cybersecurity standards and frameworks are crucial for various reasons, as they help organizations, governments, and individuals protect their digital assets and data in an increasingly interconnected and digital world. Here are some key reasons why cybersecurity standards and frameworks are needed:
- Establish Best Practices: Cybersecurity standards and frameworks provide a set of best practices and guidelines organizations can follow to secure their systems and data. These best practices are developed based on industry expertise, research, and lessons from past cyberattacks.
- Consistency: Standards and frameworks create consistency in cybersecurity practices across industries and organizations. This consistency helps ensure that security measures are implemented uniformly, reducing vulnerabilities that cybercriminals can exploit.
- Risk Management: Cybersecurity standards and frameworks help organizations identify and mitigate cybersecurity risks. They provide a structured approach to assessing risks, implementing controls, and monitoring for threats and vulnerabilities.
- Compliance and Regulation: Many industries and governments have established cybersecurity regulations and requirements. Compliance with these regulations is often mandatory and can have legal and financial consequences for non-compliance. Standards and frameworks help organizations meet these compliance requirements.
- Vendor and Supply Chain Security: Organizations often rely on third-party vendors and suppliers for products and services. Cybersecurity standards can help organizations assess the security practices of their vendors and ensure that their supply chain is not a weak link in their cybersecurity defenses.
- Incident Response: Standards and frameworks include guidelines for incident response planning and execution. They help organizations effectively prepare for and respond to cybersecurity incidents, minimizing damage and downtime.
- Education and Awareness: Standards and frameworks promote cybersecurity education and awareness by providing a common language and set of concepts that both technical and non-technical stakeholders can understand. This helps organizations build a cybersecurity-aware culture.
- Continuous Improvement: Cyber threats constantly evolve, and new vulnerabilities are discovered regularly. Standards and frameworks encourage organizations to continuously assess and improve their cybersecurity posture to adapt to changing threats.
- International Collaboration: Cybersecurity is a global issue, and international collaboration is essential to address it effectively. Standards and frameworks provide a common foundation for organizations worldwide to work together to combat cyber threats.
- Public Trust and Reputation: A strong cybersecurity posture can enhance an organization’s reputation and build trust with customers, partners, and stakeholders. Conversely, a security breach can have a severe negative impact on an organization’s reputation.
Cybersecurity standards and frameworks are needed to provide guidance, consistency, and structure for organizations to protect themselves against cyber threats, comply with regulations, and continually improve their cybersecurity practices. They play a vital role in safeguarding digital assets and data in an increasingly interconnected and digital world.
Risks Involved In The Absence Of Cybersecurity Standards And Frameworks
There are numerous and severe dangers associated with not following international cybersecurity standards and guidelines, concerns that affect not only organizations but also the people who work for them and use their services. These standards must be followed to avoid data breaches, adverse reputational effects, and legal and financial repercussions.
Here are the top eleven dangers associated with disregarding international cybersecurity guidelines and standards:
- Data Breaches: Businesses are custodians of sensitive customer and employee data. Without cybersecurity standards, data breaches are more likely to occur, potentially exposing confidential information, causing financial loss, and damaging reputations.
- Financial Losses: Cyberattacks and data breaches can result in direct financial losses for businesses. These losses may include costs associated with investigating the incident, mitigating the damage, and compensating affected parties.
- Reputation Damage: Data breaches and cyber incidents can harm a business’s reputation. Customers and stakeholders may lose trust in a company that cannot adequately protect their data, leading to a loss of business and decreased market value.
- Legal and Regulatory Consequences: Many countries have data protection and privacy laws that require businesses to safeguard customer and employee data. The absence of cybersecurity standards can lead to non-compliance with these laws, resulting in legal consequences and fines.
- Intellectual Property Theft: Businesses often possess valuable intellectual property, trade secrets, and proprietary information. Without cybersecurity standards, these assets risk theft, potentially giving competitors an unfair advantage.
- Operational Disruption: Cyberattacks, such as ransomware, can disrupt business operations, causing downtime, loss of productivity, and revenue loss. The absence of cybersecurity frameworks can leave businesses ill-prepared to respond to and recover from such incidents.
- Supply Chain Vulnerabilities: Businesses rely on suppliers and vendors for goods and services. If these third-party partners do not follow cybersecurity best practices, they can introduce vulnerabilities into the business’s supply chain, which attackers may exploit.
- Loss of Customer Trust: Customers are increasingly concerned about the security of their data. Without cybersecurity standards, businesses may struggle to convince customers that their information is adequately protected, leading to customer churn.
- Competitive Disadvantage: Businesses that do not prioritize cybersecurity may face a competitive disadvantage. Partners and customers may prefer working with companies with solid cybersecurity practices.
- Lack of Cyber Insurance Eligibility: Many insurance companies require businesses to meet specific cybersecurity standards to qualify for cyber insurance coverage. In the absence of these standards, businesses may be unable to obtain essential insurance protection against cyber risks.
- Inadequate Incident Response: Without established incident response frameworks, businesses may not know how to react effectively to a cyber incident, leading to further damage and increased recovery costs.
- Increased Target for Attacks: Cybercriminals often target businesses with weak cybersecurity defenses. In the absence of standards, businesses become more attractive targets for cyberattacks.
The absence of cybersecurity standards and frameworks for businesses can result in many risks, including data breaches, financial losses, reputation damage, legal consequences, operational disruption, and diminished customer trust. To mitigate these risks, businesses must adopt and adhere to cybersecurity best practices and standards.
Top Cybersecurity Frameworks
Cybersecurity frameworks offer defined methods and rules for managing and enhancing cybersecurity practices for organizations. The most well-known and extensively used cybersecurity frameworks exist in many different countries. Some of the most notable ones are listed below:
A few of the most prominent ones include:
- The U.S. National Institute of Standards and Technology (NIST) introduced the NIST Cybersecurity Framework, offering a comprehensive approach to managing and mitigating cybersecurity threats. Its core functions encompass identification, protection, detection, response, and recovery.
- As per ISO/IEC 27001, there’s a need to set up, execute, maintain, and enhance an Information Security Management System (ISMS).
- The CIS Controls are a prioritized list of measures for enhancing an organization’s cybersecurity posture. They were developed by the Centre for Internet Security (CIS). Of the size and resources of an organization, they are divided into three Implementation Groups.
- Often utilized by the government and vital infrastructure domains, NIST SP 800-53 is a compilation of security and privacy guidelines for federal data systems and entities. It offers extensive controls that enterprises can tailor to their specifications.
- COBIT (Control Objectives for Information and Related Technologies) represents a collection of standards for synchronizing IT and business objectives formulated by ISACA.
- Payroll Card Industry Data Security Standard (PCI DSS): To safeguard cardholder data, the PCI DSS specifies security rules for companies with payment card data. For organizations that process credit and debit card payments, compliance is required.
- Health Insurance Portability and Accountability Act (HIPAA): HIPAA sets standards for safeguarding electronic protected health information (ePHI), predominantly relevant to the U.S. healthcare industry
- Although not a framework, the GDPR (General Data Protection Regulation) is a European Union regulation that imposes stringent criteria for protecting personal data. It significantly affects data protection and cybersecurity procedures around the world.
- Federal Information Security Management Act (FISMA): A law requiring creating and maintaining information security programs for federal agencies in the United States. It establishes specifications for protecting national information systems.
- NERC CIP (North American Electric Reliability Corporation Critical Infrastructure Protection) is a set of cybersecurity guidelines for safeguarding critical infrastructure specific to the North American electric utility sector.
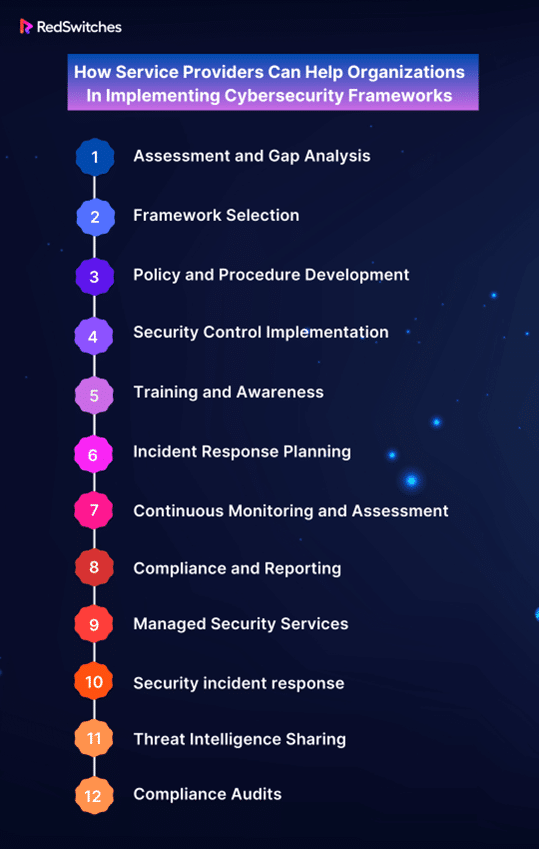
How Service Providers Can Help Organizations In Implementing Cybersecurity Frameworks
Organizations can significantly benefit from the assistance of managed service providers (MSPs) in implementing cybersecurity frameworks. MSPs are independent contractors who provide various IT services, including cybersecurity services.
Service providers may assist organizations by offering knowledgeable advice on choosing and putting the best cybersecurity framework to their particular demands and requirements.
Here are some additional ways service providers can help organizations implement cybersecurity frameworks:
- Assessment and Gap Analysis: Service providers can conduct cybersecurity and gap analyses to evaluate an organization’s security posture. By identifying weaknesses and vulnerabilities, service providers can help organizations understand where to improve to align with cybersecurity frameworks.
- Framework Selection: Service providers can assist organizations in choosing the most appropriate cybersecurity framework based on their industry, size, and specific cybersecurity needs. They can explain the pros and cons of various frameworks, such as the NIST Cybersecurity Framework, ISO 27001, CIS Controls, and others, to help organizations make informed decisions.
- Policy and Procedure Development: Service providers can help organizations develop cybersecurity policies, procedures, and guidelines that align with the chosen framework. These policies provide a foundation for implementing security controls and managing cybersecurity risks effectively.
- Security Control Implementation: Service providers can assist organizations in implementing specific security controls and measures recommended by the chosen framework. They can help configure and deploy security technologies, such as firewalls, intrusion detection systems, and antivirus software, as well as provide guidance on secure network architecture and access controls.
- Training and Awareness: Service providers can offer cybersecurity training and awareness programs for employees to ensure they understand their roles and responsibilities in maintaining security. Regular training helps create a cybersecurity-conscious culture within the organization.
- Incident Response Planning: Service providers can help organizations develop and test incident response plans aligned with the cybersecurity framework. They can assist in creating playbooks for responding to various types of cyber incidents and conducting tabletop exercises to ensure the organization is prepared.
- Continuous Monitoring and Assessment: Service providers can establish continuous monitoring solutions to detect and respond to cybersecurity threats and vulnerabilities in real time. Regular assessments and security audits help organizations maintain compliance with the framework and adapt to evolving threats.
- Compliance and Reporting: Service providers can help organizations meet regulatory and compliance requirements associated with the chosen cybersecurity framework. They can assist in generating reports and documentation necessary for demonstrating compliance to auditors and regulatory bodies.
- Managed Security Services: Some service providers offer managed security services (MSS), where they take on the responsibility of monitoring, managing, and responding to cybersecurity threats on behalf of the organization. MSS providers often have advanced tools and expertise to enhance security.
- Security incident response: In the event of a cybersecurity incident, service providers can offer incident response services, including forensic analysis, containment, and remediation. Their expertise can help organizations minimize the impact of a breach and recover more swiftly.
- Threat Intelligence Sharing: Service providers can share threat intelligence and information on emerging threats and vulnerabilities, enabling organizations to protect themselves proactively.
- Compliance Audits: Service providers can conduct regular compliance audits to ensure that the organization’s cybersecurity measures align with the chosen framework and industry standards.
Organizations can leverage their expertise, resources, and experience to implement and maintain effective cybersecurity frameworks by collaborating with cybersecurity providers. This partnership can help organizations enhance security posture, reduce risks, and better protect their data and assets from cyber threats.
Conclusion
To sum up, cybersecurity frameworks are crucial for businesses looking to strengthen their defenses against cyber threats. These frameworks offer organized methods, recommendations, and best practices to assist organizations in efficiently identifying, guarding against, detecting, responding to, and recovering from security issues.
The flexibility to customize security measures to an organization’s specific needs, compliance with regulatory standards, and a systematic approach to managing risks are just a few advantages cybersecurity frameworks offer. They also support continual improvement by encouraging regular reviews and modifications to security procedures.
RedSwitches, with its expertise in digital infrastructure, can play a pivotal role in elucidating and implementing Cybersecurity Frameworks 101, ensures that organizations are equipped with the latest protective measures against online threats.
Invest in premium dedicated server and bare metal servers with robust cybersecurity with RedSwitches. Contact us now to learn more.
FAQs
Q What is a cybersecurity framework?
A cybersecurity framework is a set of guidelines, best practices, and standards that help organizations manage and improve their cybersecurity posture.
Q What is the NIST Cybersecurity Framework?
The NIST Cybersecurity Framework is a widely recognized framework developed by the National Institute of Standards and Technology (NIST) to help organizations manage and reduce cybersecurity risks.
Q What are the five functions of the NIST Cybersecurity Framework?
The five functions of the NIST cybersecurity framework are to identify, protect, detect, respond, and recover. These functions provide a structured approach to managing and improving an organization’s cybersecurity.
Q How can I implement the NIST Cybersecurity Framework?
To implement the NIST Cybersecurity Framework, you can follow the steps outlined by NIST, which include assessing your current cybersecurity posture, identifying gaps, developing and implementing a cybersecurity plan, and continuously monitoring and improving your security controls.
Q What are the NIST security controls?
The NIST security controls are a set of safeguards and countermeasures designed to protect information systems from cybersecurity threats. These controls are outlined in NIST Special Publication 800-53.
Q What are some common cybersecurity frameworks?
Some common cybersecurity frameworks include the NIST Cybersecurity Framework, ISO 27001, CIS Critical Security Controls, and COBIT.
Q What are cybersecurity frameworks, and why are they important?
Cybersecurity frameworks are structured sets of guidelines and best practices designed to help organizations manage and reduce their cyber risk. They are important because they provide a systematic approach to addressing cybersecurity challenges and help organizations establish effective cybersecurity programs.
Q How many types of cybersecurity frameworks should an organization consider?
Organizations should consider various types of cybersecurity frameworks to assess their cybersecurity maturity and effectively manage cyber risk. Some popular options include the NIST Cybersecurity Framework, CIS Controls, ISO 27001, COBIT, and PCI DSS.
Q What are the best practices for implementing a cybersecurity framework?
Implementing a cybersecurity framework involves aligning it with the organization’s objectives, conducting a thorough risk assessment, establishing a cybersecurity program, and regularly monitoring and updating the framework to adapt to evolving cyber threats and challenges.
Q How can a cybersecurity framework help in reducing cyber risk?
A cybersecurity framework can help reduce cyber risk by providing a systematic approach to identifying, assessing, and mitigating potential security threats and vulnerabilities. It helps organizations establish robust cybersecurity controls and practices to enhance their overall security posture.
Q What is the role of the Payment Card Industry Data Security Standard (PCI DSS) in cybersecurity frameworks?
PCI DSS is a set of security standards designed to ensure that all companies that accept, process, store, or transmit credit card information maintain a secure environment. It is an important component of cybersecurity frameworks, especially for organizations handling payment card data.
Q How can organizations improve their critical infrastructure cybersecurity using cybersecurity frameworks?
Organizations can improve their critical infrastructure cybersecurity by leveraging cybersecurity frameworks to assess risks, implement security controls, and enhance resilience against cyber threats. Frameworks provide guidance for protecting critical systems and assets.
Q What is the role of the Center for Internet Security (CIS) Controls in cybersecurity frameworks?
The CIS Controls offer a prioritized set of actions that help organizations defend against common cyber threats. They play a significant role in cybersecurity frameworks by providing specific guidance on implementing effective security measures.
Q How do cybersecurity frameworks address the maturity of an organization’s cybersecurity capabilities?
Cybersecurity frameworks incorporate maturity models that allow organizations to assess, benchmark, and improve their cybersecurity capabilities over time. These models help organizations gauge the maturity of their security programs and identify areas for enhancement.
Q What should an organization consider when selecting a cybersecurity framework?
When selecting a cybersecurity framework, organizations should consider their specific industry requirements, regulatory obligations, the scope of their cybersecurity program, and the maturity of their existing security controls to ensure that the chosen framework aligns with their unique needs and goals.
Q How do cybersecurity frameworks contribute to an organization’s information security strategy?
Cybersecurity frameworks contribute to an organization’s information security strategy by providing a structured approach to developing, implementing, and maintaining robust security measures. They help organizations align their security efforts with industry best practices and regulatory requirements to protect their information assets.