Key Takeaways
- Firewalls are critical in safeguarding servers from cyber threats, acting as the primary defense against data breaches and unauthorized access.
- From basic traffic monitoring to advanced threat prevention, firewalls offer a range of functions tailored to enhance server security.
- Stateful firewalls provide advanced security by remembering connection states, while proxy firewalls offer enhanced protection by acting as intermediaries.
- NGFWs bring high-tech tools for deeper security, while virtual firewalls offer flexible cloud-based protection.
- Cloud-native firewalls provide tailored security for cloud environments, whereas hybrid firewalls combine physical and virtual security measures.
- Firewalls provide robust protection and traffic management but require careful configuration and regular updates to address complex and evolving threats.
- Firewalls control network traffic to prevent unauthorized access, while antivirus software protects against internal threats by detecting and removing malware.
- Effective firewall configuration and management are crucial for maintaining robust network security and adapting to evolving cyber threats.
- Common misconceptions about firewalls can lead to a false sense of security; understanding their true capabilities and limitations is key.
- The future of firewalls and server security points towards smarter, AI-integrated systems with advanced threat detection, predictive capabilities, and seamless integration with other security tools.
In our digital world, the security of servers is crucial. They hold valuable data and are the backbone of many businesses and organizations. However, they are also prime targets for cybercriminals. According to recent research, cybercrime costs businesses an astonishing 2.9 million per minute, and data breaches expose a staggering 36 billion records in just the first three quarters of 2020. This underscores the need for robust server security measures.
One of the key players in the defense against these threats is the firewall. Think of a firewall as a security guard for your server, meticulously inspecting incoming and outgoing traffic to ensure nothing harmful gets through. But how exactly do firewalls contribute to server security?
This article dives into the depths of firewall technology. Shedding light on its vital role in safeguarding servers from the myriad of cyber threats lurking in the digital landscape.
Let’s embark on this journey to unravel the complexities of firewalls and appreciate their indispensable contribution to server security.
Table of Contents
- Key Takeaways
- What Is a Firewall?
- Types of Firewalls
- Advantages and Disadvantages of Firewalls
- How Firewalls Contribute to Server Security?
- Difference Between a Firewall and an Antivirus
- Firewall Configuration and Management
- Common Misconceptions About Firewalls
- Future of Firewalls and Server Security
- Advanced Threat Detection
- Integration with AI and Machine Learning
- Cloud-Based Firewalls
- Automated Responses
- Focus on Zero Trust Models
- Tighter Integration with Other Security Tools
- Enhanced User Authentication
- Greater Emphasis on Encryption
- Pervasive Use of IoT Device Protection
- Customizable and Scalable Solutions
- Predictive Security Posture
- Continuous Policy Enforcement
- Wrapping It Up
- FAQs
What Is a Firewall?
Credits: Freepik
A firewall is like a barrier between your computer or network and the internet. It’s a security tool. Its job is to check all the data coming in and going out. It makes sure that harmful data or unauthorized users do not get through.
Why Do We Need a Firewall?
We need firewalls to keep our networks safe. They are the first line of defense. Like a lock on your door, they keep out things you don’t want. Without a firewall, your network is open to anyone. This could mean hackers, viruses, or malware. These can steal, damage, or mess with your data. Firewalls also help control what type of content can be accessed, ensuring that inappropriate or harmful websites are blocked.
How Do Firewalls Work?
Firewalls act as gatekeepers for your network. They control the data flow to and from your network based on security rules. Here’s a simplified breakdown of how they work:
- Traffic Monitoring: Firewalls constantly monitor the data entering and leaving your network. This data travels in small packets.
- Applying Security Rules: Each data packet is examined. The firewall looks at where it’s coming from, where it’s going, and what information it contains. Firewalls use a list of security rules to decide if a packet is safe or potentially harmful.
- Allowing or Blocking Dat If the data packet meets the safety criteria set by the rules, the firewall allows it to pass through. If not, it’s blocked. This prevents unauthorized access and data breaches.
- Protecting from Various Threats: Firewalls are designed to recognize and stop many threats. These include hackers trying to break into your network, viruses that can damage your system, and spam that can clutter your network.
- Logging and Alerting: Firewalls also keep logs of network activity. This helps in understanding and analyzing attempted breaches or security threats. They can also be configured to send alerts in case of suspicious activities.
In essence, firewalls scrutinize every bit of data against a set of rules, act on the data based on these rules, and safeguard your network from various cyber threats.
Also read Web Security Gateways: Primary Features, Benefits, How It Works & More
Types of Firewalls
In the world of cybersecurity, firewalls come in different types. Each type has its way of keeping networks safe, like different kinds of door locks. Some are simple, while others are very advanced.
There are several types of firewalls, including packet filtering firewalls, application firewalls, proxy firewalls, stateful inspection firewalls, and next-generation firewalls.
This part of the article will go through the various kinds of firewalls. We’ll see how each one works and what makes it unique. Each type is essential, from the basic ones that filter data to the advanced ones that do much more.
Understanding these types will help you know more about keeping networks safe. It will also help you choose the proper firewall for your needs. So, let’s get into it and learn about the different firewalls and how they protect against digital dangers.
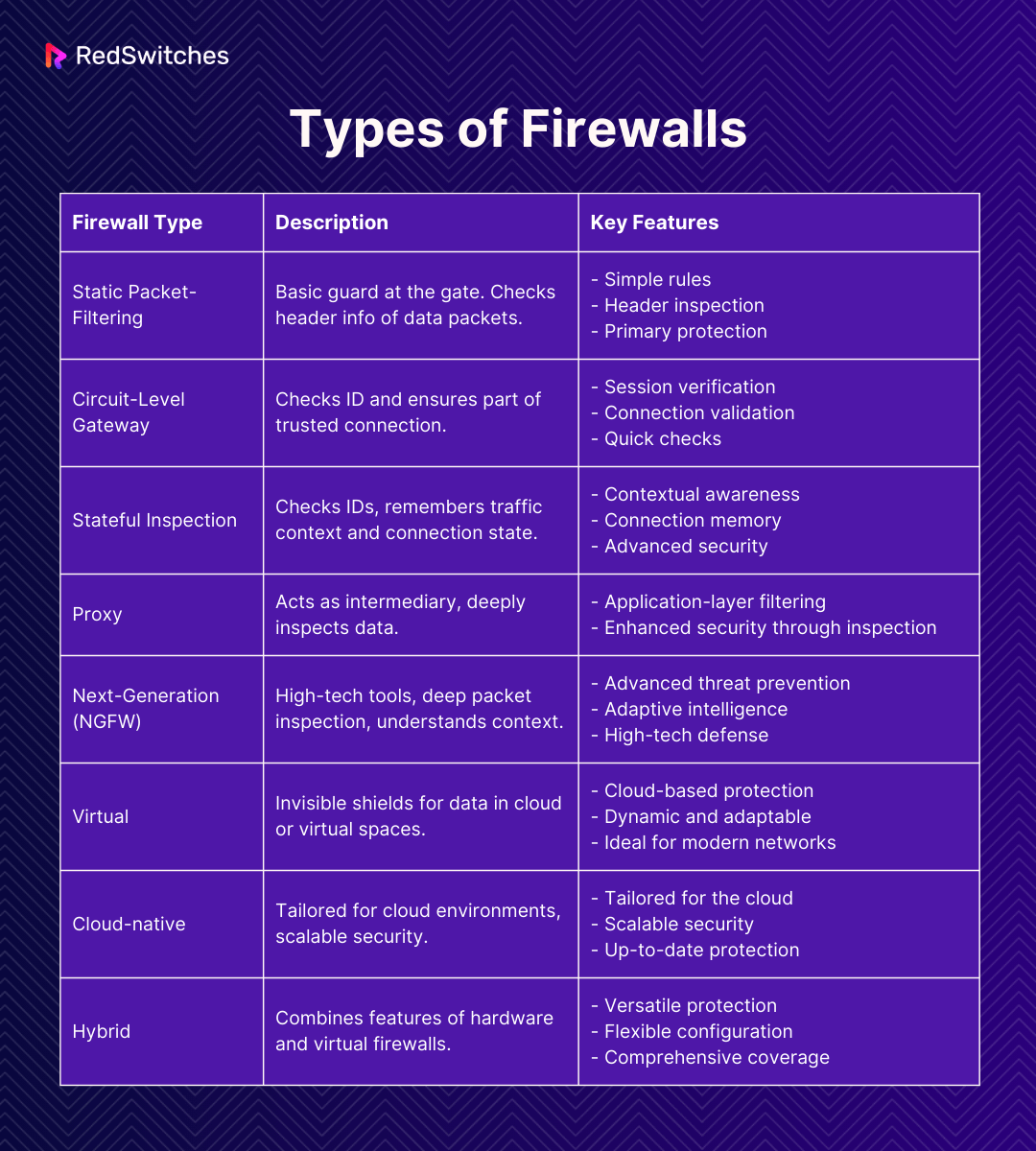
Static Packet-Filtering Firewall
Imagine your network as a private club, and the Static Packet-Filtering Firewall is the security guard at the entrance. This guard, or firewall, is responsible for checking the credentials (or headers) of each data packet that arrives. It examines where the packet is coming from, its intended destination, and the type of data it carries.
Detailed Operation
Here’s a detailed overview of how it functions:
- Header Inspection: The firewall scrutinizes the header of each data packet. This is like checking the ID of a person entering a club. The header contains crucial information about the packet, similar to how an ID holds details about a person.
- Rule-Based Decisions: The firewall operates based on predefined rules. These rules are like the club’s entry criteria. They specify which packets are allowed and which aren’t. If a packet meets the criteria set in the rules, it’s like a guest whose name is on the list and it’s allowed to enter. Otherwise, it’s turned away.
- Primary Protection: Despite being one of the simpler forms of firewalls, the Static Packet-Filtering Firewall is fundamental in network security. It’s particularly effective for networks with straightforward needs, as a diligent guard ensuring that only the right data enters or leaves the network.
Circuit-Level Gateway Firewall
The Circuit-Level Gateway Firewall takes security a notch higher. It’s akin to a more discerning bouncer who checks IDs and ensures you’re on the guest list for an exclusive event. This firewall doesn’t limit its scrutiny to the superficial details of the data packets. Instead, it delves deeper, examining the session information to ensure the integrity of the connection.
Detailed Operation
Here’s a detailed overview of how it works:
- Session Verification: Beyond looking at the packet’s header, this firewall monitors the session, ensuring the data exchange is part of an established and secure connection. It’s like a bouncer who checks your ID and then verifies that you’re on the guest list.
- Connection Validation: The firewall ensures that the connection through which the data is sent is trustworthy. It doesn’t concern itself with the content of the data packets but focuses on the legitimacy of the connection. If the connection meets the security criteria, the data is allowed to flow through.
- Enhanced Security: The Circuit-Level Gateway Firewall offers a more nuanced security layer than basic packet filtering. It’s adept at making quick, informed decisions about the data traffic, ensuring that only safe and verified connections are maintained. This type of firewall adds depth to your network’s security, safeguarding against more sophisticated threats.
Stateful Inspection Firewall
The Stateful Inspection Firewall is like a highly skilled security officer. This officer doesn’t just check IDs at the door and keeps a detailed log of everyone’s comings and goings, understanding the context of each person’s visit.
Detailed Operation
Below is a thorough explanation of its working process.
- Contextual Awareness: Unlike simpler firewalls, this one is aware of the context. It looks at each data packet within the larger framework of its connection. It’s like a security officer who knows not just who you are but also where you came from, where you’re going, and why you’re here.
- Connection Memory: This firewall remembers past connections. It doesn’t treat each packet in isolation but sees it as part of an ongoing conversation. If a packet is part of a known, safe dialogue, it’s allowed through. It’s like a security officer who remembers regular visitors and understands their patterns.
- Advanced Security: Because it understands context and remembers connections, a Stateful Inspection Firewall provides a deeper level of security. It’s smart, vigilant, and capable of making informed decisions about the data passing through your network.
Also Read Database Defense Blueprint: Ensuring Data Security in a Connected World
Proxy Firewall
The Proxy Firewall serves as an intermediary, like a diplomatic translator or a careful messenger. It stands between your network and the outside world, managing and inspecting the data that flows in both directions.
Detailed Operation
Let’s take an in-depth look at its operational mechanism.
- Acting as an Intermediary: The Proxy Firewall receives incoming data first, then sends it to your network’s destination. It’s like a gatekeeper who opens the mail, checks it, and delivers it safely.
- Application-Layer Filtering: This firewall operates at a higher level – the application layer. This means it can understand and filter out more complex data, like web page content or specific types of transactions. It’s like having a gatekeeper who doesn’t just check IDs but also understands the nature of each person’s visit.
- Enhanced Security through Inspection: Because it inspects data so thoroughly, a Proxy Firewall offers high security. It’s like having a bodyguard who checks everyone’s ID, listens to their story, and decides if they’re safe to enter.
Credits: Freepik
Next Generation Firewall (NGFW)
The Next-Generation Firewall (NGFW) is akin to an elite security team equipped with the latest technology. Far more than just a barrier, this firewall is a comprehensive security solution.
Detailed Operation
Here is an elaborate breakdown of its operational functionality.
- Deep Packet Inspection: NGFW looks beyond the surface, examining the details within each data packet. It’s like a security team scrutinizing every mail piece, not just the address on the envelope.
- Advanced Threat Prevention: This firewall can stop viruses and other harmful software. It can monitor applications in real-time, halting any that behave suspiciously. It’s like having a team that checks IDs and monitors everyone’s behavior at the party.
- Adaptive Intelligence: NGFWs are intelligent. They learn from the data they process and from the threats they encounter. This allows them to adapt and improve their defense strategies over time. It’s like having a security team that learns from every incident, becoming more adept at protecting your network.
- High-Tech Network Defense: With its advanced capabilities, an NGFW is like a high-tech fortress. It offers a level of protection that is sophisticated, comprehensive, and proactive.
Also, Read What’s System Hardening and How It Works: A 5-Phase Process
Virtual Firewalls
Virtual Firewalls are the invisible protectors of the digital realm. They operate within virtual environments, safeguarding data as it moves through cloud-based systems and virtual machines.
Detailed Operation
The following provides a detailed description of its mode of operation.
- Cloud-Based Protection: These firewalls secure data in the cloud. They’re not bound to any physical device. It’s like having a security force that can protect your data wherever it is in the digital world.
- Dynamic and Adaptable: Virtual Firewalls are incredibly flexible. They can adjust as your network grows or as your needs change. It’s like having a security system that can expand or transform to protect new rooms as you add them to your building.
- Ideal for Modern Networks: For networks that are spread out, use cloud services, or have virtual components, Virtual Firewalls are ideal. They provide robust protection tailor-made for modern digital infrastructures’ complexities.
Cloud-native Firewalls
Cloud-native Firewalls are specialized protectors for the cloud. They’re like security experts who know every corner of the cloud environment.
Detailed Operation
Here’s an in-depth explanation of its operational process:
- Tailored for the Cloud: These firewalls are designed specifically for cloud systems. They understand how the cloud works and how data moves within it. It’s like having a security guard who knows every hallway and room in a building.
- Scalable Security: As cloud usage grows, so does the protection from cloud-native firewalls. They can handle vast amounts of data and adapt to changes quickly. It’s like having a security team that can grow instantly when you host a bigger event.
- Up-to-Date Protection: Being part of the cloud, these firewalls are always current with the latest threats and security measures. It’s like having a guard who’s constantly trained on the newest security protocols.
- In Tune with the Cloud: These firewalls ensure your data in the cloud is secure. They provide a layer of protection that’s perfectly matched with the dynamic nature of cloud environments.
Hybrid Firewall
Hybrid Firewalls offer a comprehensive security solution, combining the strengths of both hardware and virtual firewalls.
Detailed Operation
Here’s an in-depth explanation of its working process
- Versatile Protection: These firewalls protect both physical servers and virtual environments. It’s like having a security team that can guard a building and protect a virtual online conference.
- Flexible Configuration: Hybrid Firewalls can adjust based on the nature of the threat or the direction of data flow. They’re flexible and can shift their focus where it’s needed most. It’s like having a security team that can redeploy based on where they’re needed at a moment’s notice.
- Comprehensive Coverage: By combining features of physical and virtual firewalls, they offer full-spectrum protection. Whether your data is on a physical server or in the cloud, a Hybrid Firewall covers you. It’s like having a security system that covers the entrance, every room, and the virtual space where your data might reside.
Here’s an overview of the types of firewalls discussed above:
Also Read Does Your Organization Needs An Intrusion Detection System? A Detailed Breakdown
Advantages and Disadvantages of Firewalls
Firewalls are like guardians of our digital space. They have strong points and some limitations. In this part, we’ll look closely at both. We’ll see what makes firewalls so crucial for protecting our networks. We’ll also discuss the challenges they bring. Knowing both helps us use firewalls well and be ready for any issues. Let’s dive in and learn about the whole role of firewalls in keeping our digital world safe.
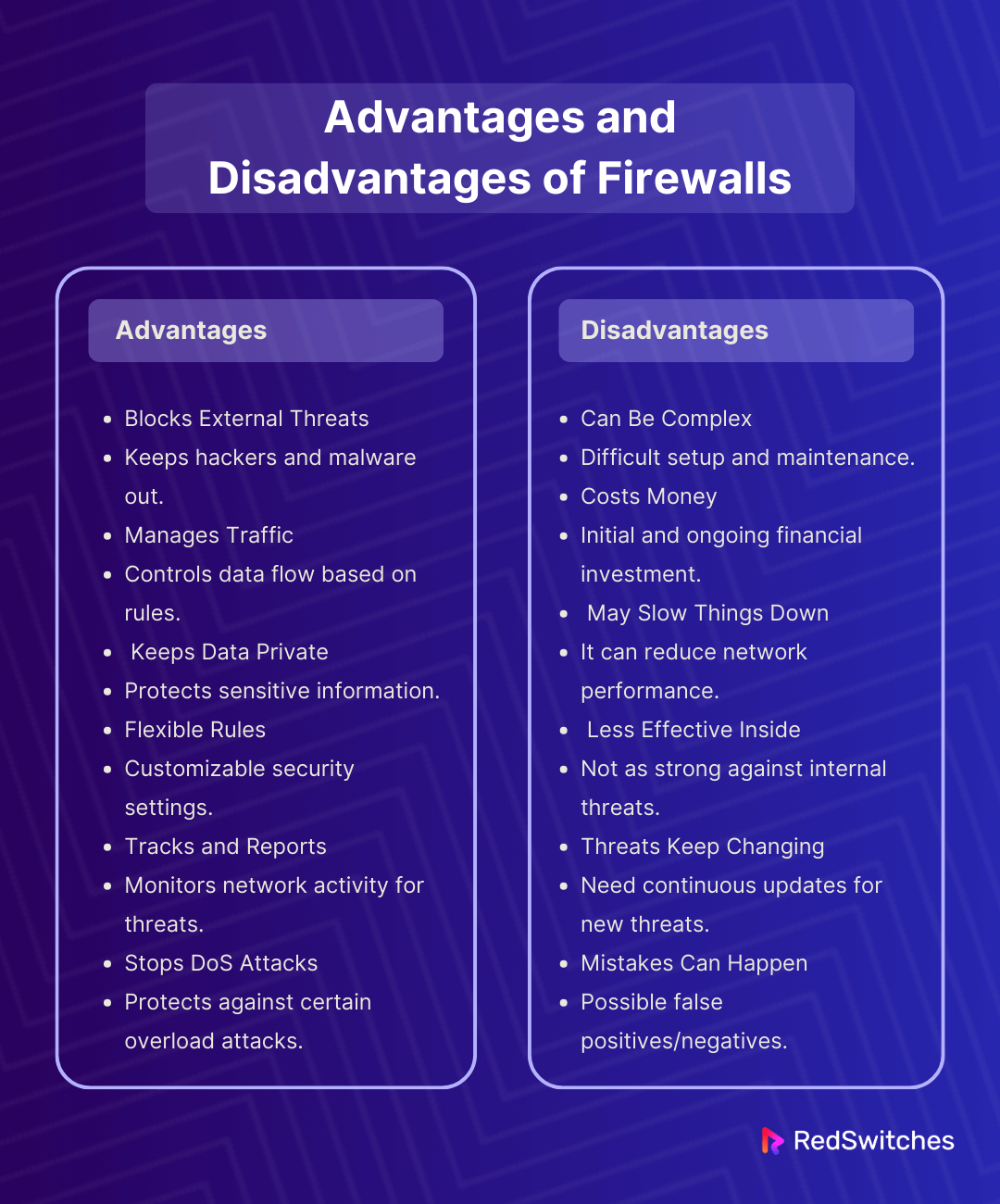
Advantages of Firewalls
Firewalls, whether they are software-based or hardware-based, offer several key advantages in network security and management:
- Blocks External Threats: Firewalls are the main guard against hackers and harmful software. They check all data coming in or going out, stopping unwanted access.
- Manages Traffic: Firewalls control how data moves based on set rules. They make sure only safe and needed data gets through. This helps avoid too much traffic and keeps the network safe.
- Keeps Data Private: Firewalls stop outsiders from getting into your network. They protect your private data from being seen or stolen.
- Flexible Rules: You can set your own rules on firewalls. This lets you decide how to handle different kinds of data. You get to control how tight your security is.
- Tracks and Reports: Firewalls keep records of all network activities. They show you patterns and possible threats. This helps spot dangers and for looking into issues.
- Stops DoS Attacks: Firewalls can spot and stop some attacks that try to overload your system. They block harmful traffic, keeping your network services safe and running.
Disadvantages of Firewalls
While firewalls are essential for network security, they also have some disadvantages:
- Can Be Complex: Setting up and caring for firewalls can be tricky. It can leave weak spots or block good data if not done right.
- Costs Money: Good firewalls, especially the advanced ones, can be costly. You also have to pay for keeping them up-to-date and working well.
- May Slow Things Down: Some firewalls check data deeply and keep many records. This can slow down your network, affecting your work.
- Less Effective Inside: Firewalls are great against outside threats. But they’re not as good at spotting dangers that start inside your network.
- Threats Keep Changing: Bad software and hacking methods are constantly changing. Firewalls need regular updates to keep up, adding to their complexity and cost.
- Mistakes Can Happen: Firewalls might block good data by mistake. Or, they might not catch bad data. This can either stop your work or let threats in.
Understanding these pros and cons is important. It helps you make the best use of firewalls. It also prepares you to deal with any challenges they might bring.
Also Read How To Prevent DDoS Attacks [8 Proven Tactics You Can Try Right Now!]
Also Read: Unveiling the Hidden Risks of Dedicated Servers
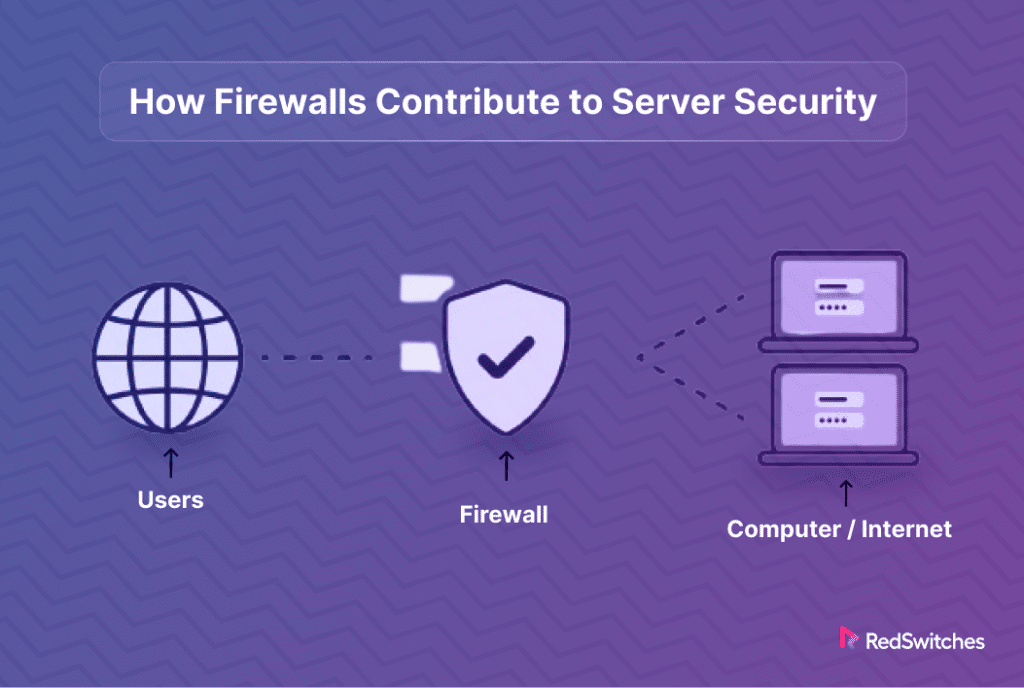
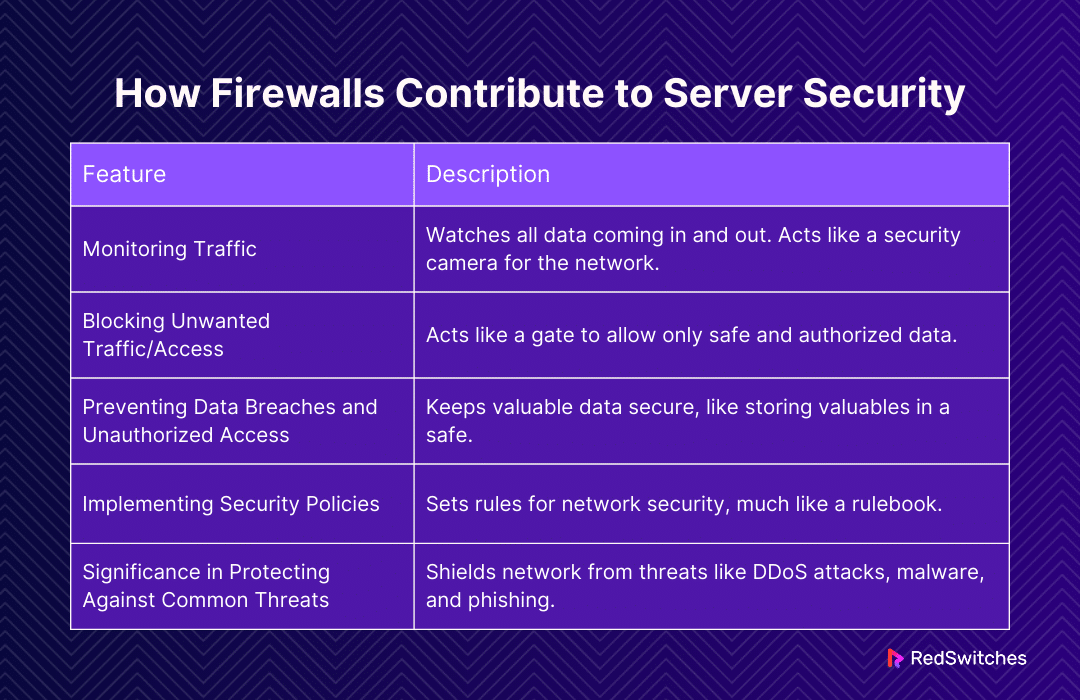
How Firewalls Contribute to Server Security?
Credits: Freepik
Servers hold essential data. But they face threats like hackers and viruses. Firewalls can be used to protect servers from these dangers. In this section, we’ll see how firewalls work hard to keep servers safe. They check data, block threats, and ensure only good traffic gets through. Let’s explore how firewalls are vital in keeping servers secure.
Monitoring Traffic
Monitoring traffic is like having a security camera for your dedicated server. It means watching all the data that comes in and goes out. This is important for keeping your dedicated server safe.
- Watching Every Data Packet: Firewalls keep an eye on each piece of data. They check where it’s from, where it’s going, and what’s inside it. It’s like checking every person who comes near your dedicated server.
- Spotting Strange Behavior: Sometimes, data acts oddly. Firewalls notice this. If data is trying to get into your dedicated server in a weird way, the firewall takes note. It’s like having a guard who knows when someone is acting suspiciously.
- Keeping Records: Firewalls write down what happens. They keep a list of all the data they see. This is useful if there’s a problem. You can look back and see what happened, just like checking security footage.
- Alerting You: The firewall will tell you if something bad is trying to get to your dedicated server. It’s like having an alarm that goes off if there’s trouble.
By monitoring traffic, firewalls make sure your dedicated server is constantly watched. They spot problems, keep records, and alert you, helping to keep your data safe and sound.
Blocking Unwanted Traffic/Access
Blocking unwanted traffic or access is like having a strong gate that only lets in the right people and information to your network. It’s a critical job that firewalls do to keep your network secure, especially if you have a dedicated server.
- Setting Strict Rules: Firewalls have rules about what’s allowed and not. These rules are like the criteria for who can enter your gate. If the data doesn’t meet these rules, it’s not allowed in.
- Checking IDs: Every bit of data has information, like an ID. Firewalls check these IDs. If the data is from an unknown or unsafe place, the firewall blocks it. It’s like having a guard who checks IDs before letting anyone in.
- Stopping Harmful Dat Sometimes, data can be harmful, like a virus. Firewalls are good at spotting these threats. They stop this bad data before it can harm your dedicated server.
- Preventing Unauthorized Access: Firewalls ensure that only authorized users can access your dedicated server. They block anyone or anything that’s not supposed to get in. It’s like having a gate that only opens for people with the right key.
By blocking unwanted traffic and access, firewalls act as a strong barrier. They ensure that your dedicated server is shielded from threats and only interacts with safe and authorized data and users.
Credits: Freepik
Also, Read Web Application Security 101
Preventing Data Breaches and Unauthorized Access
Preventing data breaches and unauthorized access is like keeping your most valuable possessions in a safe. Firewalls play a crucial role in this protective measure, ensuring your network’s security is uncompromised.
- Setting Up Strong Defenses: Firewalls defend against anyone trying to sneak into your network. They’re like a combination lock on a safe, only allowing access when the correct code is entered.
- Verifying Users: Firewalls ensure that anyone trying to access the network is who they say they are. It’s like a security checkpoint where everyone must show their ID before passing.
- Encrypting Dat Some firewalls can encrypt data, making it unreadable to anyone who doesn’t have the key to decrypt it. This is like having your valuables within a safe; even if someone gets past the first layer, they can’t get to your valuables without cracking the second layer.
- Detecting and Alerting: Firewalls are constantly alert for any signs of a breach. If they detect an attempt to access the network unauthorizedly, they can alert the network administrators. It’s like having a security system that locks your valuables away and tells you if someone is trying to break in.
By effectively preventing data breaches and unauthorized access, firewalls ensure that your network remains secure, safeguarding your valuable data and maintaining the integrity and privacy of your information.
Implementing Security Policies
Implementing security policies through a firewall is like setting up a rulebook for how things should work in a secure environment. These policies are crucial for maintaining order and safety within a network.
- Defining Rules: Firewalls allow you to set specific rules that dictate how the network should handle different types of traffic. It’s like creating a guidebook that states who can enter a building and at what times.
- Controlling Access: By implementing these policies, firewalls control who has access to what parts of the network. It’s like having different security levels within a building; not everyone can go everywhere.
- Enforcing Regulations: Firewalls enforce these policies consistently. Once the rules are set, the firewall acts like a strict enforcer, ensuring that every data packet follows the rules.
- Customizing Protection: Each network has different needs. Firewalls allow for customization of security policies to fit these unique requirements. It’s like tailoring the security of a building to meet the specific needs of its occupants.
By implementing security policies, firewalls create a structured and secure environment where data can flow safely and efficiently, ensuring that the network operates smoothly while being protected against potential threats.
The Significance of Firewalls in Protecting Against Common Cyber Threats
Firewalls are critical in defending against common cyber threats such as DDoS attacks, malware, and phishing. They serve as a robust shield, safeguarding the network from these pervasive dangers.
- Defending Against DDoS Attacks: DDoS (Distributed Denial of Service) attacks aim to overwhelm a network with excessive traffic, causing it to crash. Firewalls help filter out this unwanted traffic, keeping the network stable and accessible. It’s like having a filter that keeps unwanted visitors at bay, ensuring the network remains operational.
- Blocking Malware: Malware is malicious software designed to damage or disrupt systems. Firewalls scrutinize incoming data for signs of malware and block these threats from entering the network. It’s like having a security system that detects and stops intruders before they can cause harm.
- Preventing Phishing Attempts: Phishing involves tricking individuals into giving away sensitive information. Firewalls can block access to known phishing sites and scan emails for suspicious links or attachments, reducing the risk of falling victim to these deceitful tactics. It’s like having a vigilant gatekeeper who warns you about potential scams and keeps deceptive messages out.
Credits: Pixabay
The significance of firewalls in protecting against these common cyber threats cannot be overstated. By offering a robust line of defense, firewalls play an essential role in maintaining the security and integrity of networks, ensuring that operations continue smoothly without disruption from malicious actors.
Also Read 12 Steps For Maintaining A Threat-Resistant Secure Server
Difference Between a Firewall and an Antivirus
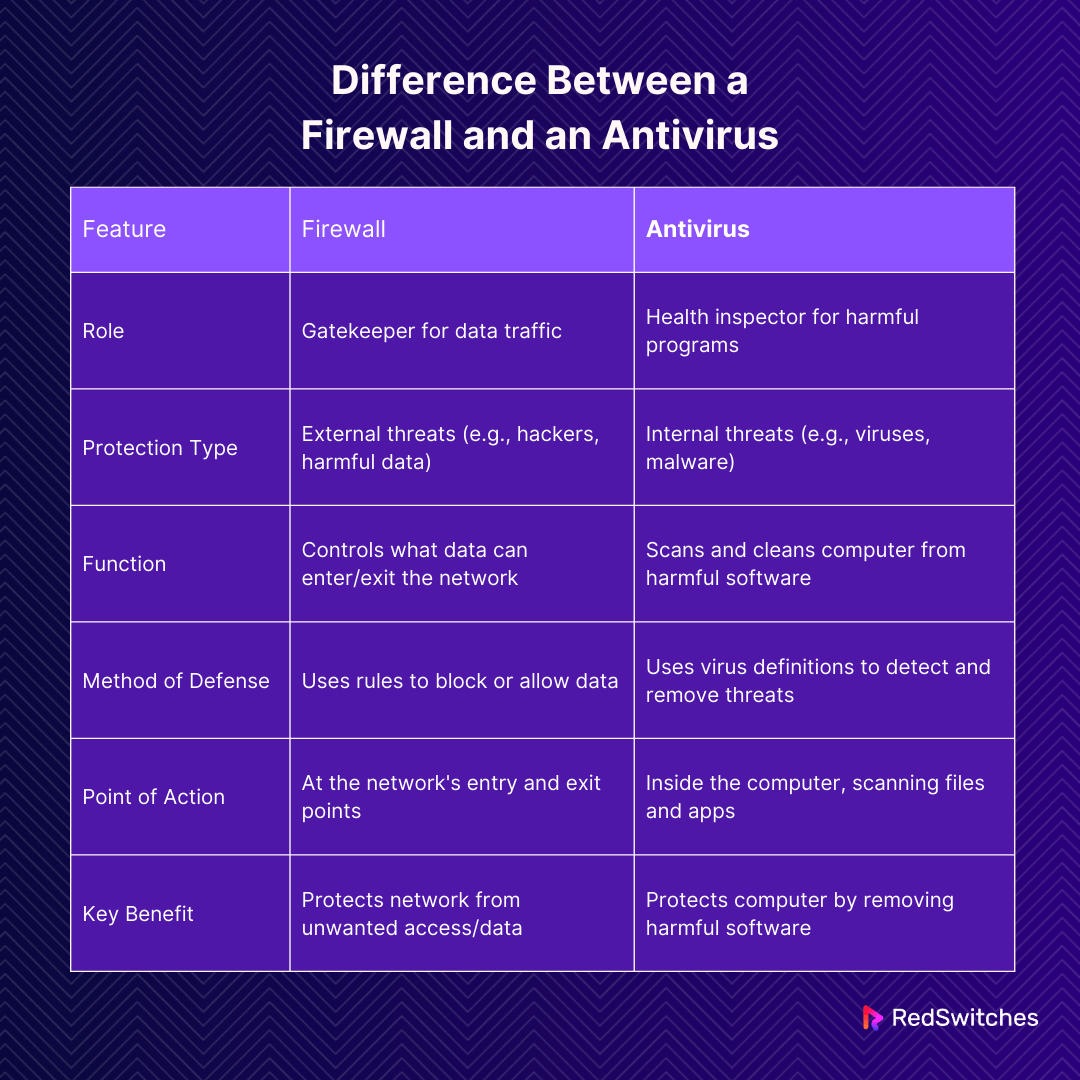
When protecting your computer, both a firewall and an antivirus play crucial roles, but they do different jobs. Understanding the difference is important for effective network firewall security.
A firewall is like a gatekeeper. It decides what data can enter or leave your network. It checks the data against a set of rules. If the data doesn’t follow the rules, the firewall blocks it. This helps keep your network safe from unwanted visitors and harmful data.
An antivirus is like a health inspector. It scans your computer for viruses and malware, which are harmful programs. If it finds any, it tries to remove them. Antivirus software keeps your computer clean and healthy by protecting it from these internal threats.
The Key Differences
Firewalls and antivirus software are both critical components of network and computer security, but they serve different purposes and function in distinct ways. Here are the key differences between the two:
- Role and Function: Firewalls control data flow to and from your network, acting as a barrier. Antiviruses scan and clean your computer, getting rid of harmful software.
- Type of Protection: Firewalls protect against external threats. They stop harmful data before it enters your network. Antiviruses protect against internal threats. They find and remove malware that has made its way onto your computer.
- Method of Defense: Firewalls use a set of rules to block or allow data. It’s like having a list of who can and can’t come in. Antiviruses look for known viruses and malware. They use this knowledge to spot and remove these threats.
- Point of Action: Firewalls work at the point where data enters or leaves your network. Antiviruses work inside your computer, scanning files and applications.
Both firewalls and antiviruses are important for keeping your computer and network safe. They work together to provide a strong defense against various cyber threats. By understanding their differences, you can make sure you’re fully protected.
This table succinctly compares the key aspects of firewalls and antivirus software, highlighting their roles, types of protection, functions, methods of defense, points of action, and key benefits.
Also Read Private Network vs Public Network: A Detailed Breakdown
Firewall Configuration and Management
Properly setting up and managing a firewall is crucial for effective firewall and network protection. This process ensures your firewall does its job correctly, keeping your network safe from threats.
Setting Up Your Firewall
Configuring and managing a firewall is a crucial task for ensuring network security. Here’s a step-by-step guide to setting up your firewall:
- Installing the Firewall: First, you must install your firewall. This is like setting up a new security system in your home. You need to make sure it’s properly in place to start protecting you.
- Configuring Rules: Next, you set the rules for your firewall. These rules tell your firewall what traffic is allowed and what isn’t. It’s like setting up guidelines for who can enter your house and when.
- Testing the Firewall: After setting the rules, you must test your firewall. This makes sure it’s working as expected. It’s like checking your home security system to ensure all sensors are operational.
Managing Your Firewall
Managing your firewall effectively is crucial to maintaining the security and efficiency of your network. Here are key steps and best practices in firewall management:
- Regular Updates: Keep your firewall updated. Just like any software, firewalls need updates to stay effective. These updates can fix problems or add new features.
- Monitoring Traffic: Continuously monitor the traffic that goes through your firewall. This helps you spot any unusual activity. It’s like having a security camera that always keeps an eye on your house.
- Reviewing and Tweaking Rules: Regularly review the rules you’ve set for your firewall. As your needs change, you might need to change the rules, too. It’s like updating your home security settings when your lifestyle changes.
- Managing Access Permissions: Control who can change your firewall settings. Not everyone should have this access. It’s like giving the keys to your house only to people you trust.
Proper configuration and management of your firewall ensure that your network remains protected. It’s a continuous process that keeps your firewall and network protection strong and effective against ever-evolving cyber threats.
Common Misconceptions About Firewalls
Regarding network firewall protection, some common misconceptions can lead to a false sense of security. It’s essential to clear these up so you can rely on your firewall effectively.
Misconception 1: “A Firewall Provides Complete Protection.”
Many think a firewall is all they need to keep their network safe. This isn’t true. A firewall is essential, but it’s just one part of security. You also need other measures like antivirus software and good practices.
Misconception 2: “Once Configured, No Further Attention is Needed.”
Some believe a firewall is good forever once a firewall is set up. But threats change, and so should your firewall’s settings. Regular updates and reviews are needed to keep your firewall strong.
Misconception 3: “All Firewalls Are the Same”
Not all firewalls offer the same level of protection. There are different types for different needs. Choosing the right one and setting it up correctly is key to adequate security.
Misconception 4: “Firewalls Make a Network Slow”
Some people avoid firewalls, thinking they’ll slow down their network. Modern firewalls are designed to be efficient. While they check traffic, they usually don’t cause noticeable slowdowns.
Misconception 5: “Firewalls are Only for Large Organizations”
Every network can be a target, not just those of big companies. Even small networks need firewalls to protect against threats. Security is essential for everyone.
Understanding these misconceptions helps in making better decisions about network firewall protection. It’s about using firewalls as part of a broader security strategy, keeping them updated, and choosing the right one for your needs.
Also read Network Security in Cloud Computing: 7 Things To Know
Future of Firewalls and Server Security
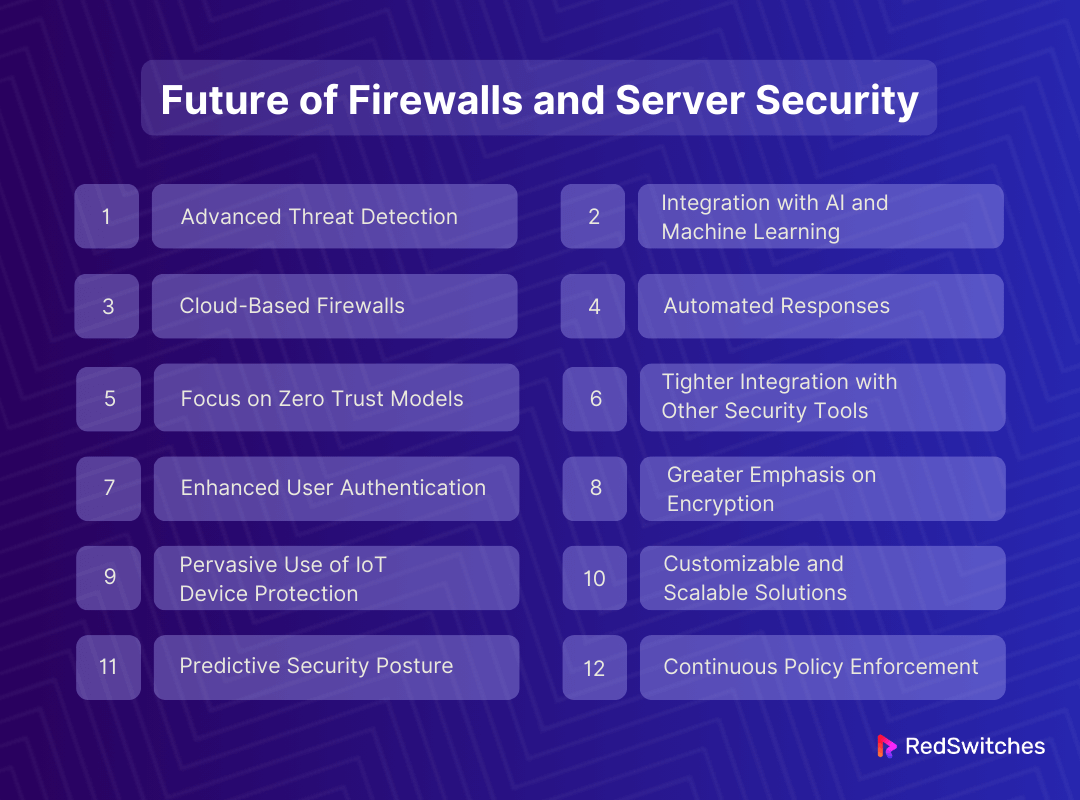
The future of firewalls and server security is evolving rapidly. As technology advances, so do the methods used to protect networks and data.
Advanced Threat Detection
Future firewalls will be even smarter. They’ll use advanced methods to spot threats faster and more accurately. This means better protection against complex attacks.
Integration with AI and Machine Learning
Firewalls will use AI and machine learning. These technologies can learn from past attacks. This helps firewalls predict and stop future threats before they happen.
Cloud-Based Firewalls
More firewalls will live in the cloud. This makes them more flexible and easier to manage, especially for businesses that use cloud services.
Automated Responses
Firewalls will not just detect threats. They’ll also respond to them automatically. This quick action can stop attacks before they do much harm.
Focus on Zero Trust Models
The concept of “never trust, always verify” will shape future security. Firewalls will play a big part in this, checking every request as a potential threat.
Tighter Integration with Other Security Tools
Firewalls will work more closely with other security tools like antiviruses. This teamwork makes the overall security stronger and more seamless.
Enhanced User Authentication
Future firewalls will incorporate more sophisticated user authentication methods. Biometrics, multi-factor authentication, and behavior-based access controls will become standard, ensuring only authorized users can access the network.
Greater Emphasis on Encryption
Encryption will be more deeply integrated into firewall technology. As data privacy concerns grow, firewalls will monitor and encrypt data traffic more comprehensively, ensuring data integrity and confidentiality.
Pervasive Use of IoT Device Protection
With the rise of IoT devices, firewalls will also extend their protection to these devices. They will offer specialized features to monitor and secure the data from these devices, preventing them from becoming weak points in the network.
Customizable and Scalable Solutions
Firewalls will become more customizable and scalable. Businesses can tailor their firewall protection to their specific needs and scale it as their operations grow, ensuring that security grows in tandem with the business.
Predictive Security Posture
The future firewalls will not just defend; they will predict. Leveraging big data and analytics, they will analyze patterns to predict potential security breaches before they occur, shifting the approach from reactive to proactive.
Continuous Policy Enforcement
Future firewalls will ensure continuous policy enforcement across all touchpoints in the network. Regardless of where data resides or travels, the firewall will enforce the same security standards, ensuring consistent protection.
The future of firewalls and server security is about being more proactive, smart, and integrated. This evolution aims to stay one step ahead of threats, ensuring better protection for networks and data.
Wrapping It Up
In the vast and ever-changing digital security landscape, navigating the complex web of threats can be daunting. Firewalls stand as the steadfast guardians of our networks, tirelessly defending our data from a myriad of cyber dangers. Each uniquely fortifies our digital defenses, from the diligent Static Packet-Filtering Firewall to the intelligent Next-Generation Firewall.
But why stop at good when you can aim for the best? With RedSwitches, you’re not just protecting your network but empowering it. RedSwitches offers cutting-edge firewall solutions tailored to your specific needs, ensuring that your digital assets are guarded with the utmost precision and expertise.
Embrace the future of cybersecurity with RedSwitches. Whether you’re safeguarding a small startup or a sprawling enterprise, RedSwitches provides the robust protection your digital infrastructure deserves. Don’t just defend; dominate in the realm of digital security.
Ready to elevate your network security? Connect with RedSwitches today, and fortify your digital fortress!
FAQs
Q. What are firewalls used for?
Firewalls are security systems that monitor and control incoming and outgoing network traffic. They act like a bouncer at a club, checking IDs and deciding who’s allowed in and who’s not. Their main purpose is to protect your computer or network from unauthorized access and cyberattacks.
Q. What are the 3 types of firewalls?
The three types of firewalls are packet-filtering firewalls, stateful inspection firewalls, and proxy firewalls (application-level gateways).
Q. What is an example of a firewall?
Most operating systems, like Windows and macOS, have built-in firewalls. You can also install third-party firewall software for more advanced protection.
Q. Why is it called a firewall?
The name “firewall” comes from the analogy of a physical wall that protects a building from fire. Similarly, a firewall protects your computer or network from the “fire” of cyberattacks.
Q. What is a firewall?
A firewall is a security system, either software or hardware, that is designed to monitor and control incoming and outgoing network traffic based on predetermined security rules. In Other words firewall is a network security device that monitors and filters network traffic based on a set of security rules. It is a barrier between a trusted internal network and an untrusted external network, such as the Internet.
Q. What is a hardware firewall?
A hardware firewall is a physical device that is installed between the internal network and the internet to filter incoming and outgoing network traffic. It is an integral component of network security.
Q. What is a software firewall?
A software firewall is a program or application that runs on a computer or server and provides a layer of security by controlling incoming and outgoing network traffic based on predetermined security rules.
Q. What are some best practices for using a firewall?
Firewall best practices include regularly updating firewall software, implementing strong security rules, monitoring network traffic, restricting access to sensitive data, and conducting regular security audits.
Q. What are the limitations of a firewall?
While firewalls are essential for network security, they have limitations such as inability to detect all types of cyber threats, reliance on continuous updates to address new threats, and potential vulnerability to insider attacks.
Q. How do firewalls go beyond network security?
In addition to traditional network security functions, firewalls can be configured to provide advanced security capabilities such as web application firewalls, intrusion prevention systems, and deep packet inspection to enhance overall security posture.
Q. How does a firewall work?
Firewalls filter and inspect network traffic passing through them and determine whether to allow or block specific data packets based on predefined rules and security policies.
Q. What is the role of firewalls in network security?
Firewalls play an important role in network security by serving as the gateway from one network to another, implementing access control, and protecting against unauthorized access and cyber threats.
Q. How are firewalls used in virtual private networks (VPNs)?
Firewalls are often used in VPNs to establish secure communication channels by inspecting and controlling traffic between the VPN endpoints and ensuring that only authorized network traffic is allowed to pass through.
Q. What are the capabilities of modern firewalls?
Modern firewalls offer advanced capabilities such as deep packet inspection, application-layer filtering, network address translation, virtual private network support, and integration with intrusion prevention systems.
Q. Are firewalls still relevant in today’s cybersecurity landscape?
Yes, firewalls are still in use and remain a critical component of cybersecurity strategies, providing essential protection by controlling traffic flow, preventing unauthorized access, and enhancing network security.