In today’s digitally dominated landscape, web security gateways protect our sensitive data from myriad cyber threats. They are pivotal in a world where security breaches and data leaks are commonplace.
The importance of web security is highlighted by the robust growth in the Global Secure Web Gateway Market, valued at US$ 7.4 billion in 2021 and expected to expand at a CAGR of 21.2% in the forthcoming years. This article aims to simplify the complex world of web security gateways, offering insights and guidance to help readers navigate this intricate realm.
Credit: Pixabay
We’ll explore the pivotal role of these web security gateways in defending our digital spaces, delve into the evolving market trends, and provide a glimpse into the innovations shaping the future of web security, ensuring readers are well-informed and prepared to traverse the digital world safely.
Table Of Contents
- What is a Web Security Gateway?
- How Does a Web Security Gateway Work?
- Benefits of a Web Security Gateway
- Primary Features of Web Security Gateway
- Secure Web Gateways and Firewalls
- How Do Web Security Gateways Enforce Security Policies?
- Conclusion
- FAQs
What is a Web Security Gateway?
A Web Security Gateway is essentially a security solution that protects networks and users from potential cyber threats and attacks. It acts as a filter between the user and the internet, ensuring that harmful content and malicious entities do not breach the security parameters set by an organization or individual.
Key Functions:
- Filtering Web Traffic:
- It scrutinizes incoming and outgoing web traffic to detect and block malicious activities or harmful content, maintaining a secure online environment.
- Data Loss Prevention:
- It safeguards sensitive data, preventing unauthorized access and potential data leaks.
- Policy Enforcement:
- It helps enforce security policies to ensure that users adhere to the security guidelines, maintaining the overall safety of the network.
- Application Control:
- It provides control over the use of unauthorized applications and ensures that only secure and authorized applications are accessed by the users.
Why is it Essential?
The risks of cyber-attacks and data breaches are ever-present in our interconnected world.
A Web Security Gateway is not just a tool but a necessity, especially with the exponential increase in online transactions, the surge in remote working, and the escalating reliance on digital platforms for personal and professional activities.
It provides peace of mind, allowing users to navigate the internet without the constant fear of cyber threats, ensuring a secure and seamless online experience.
By understanding what is web security gateway is, individuals and organizations can better appreciate their significance in maintaining the sanctity of our digital lives and make more informed choices to safeguard their online presence.
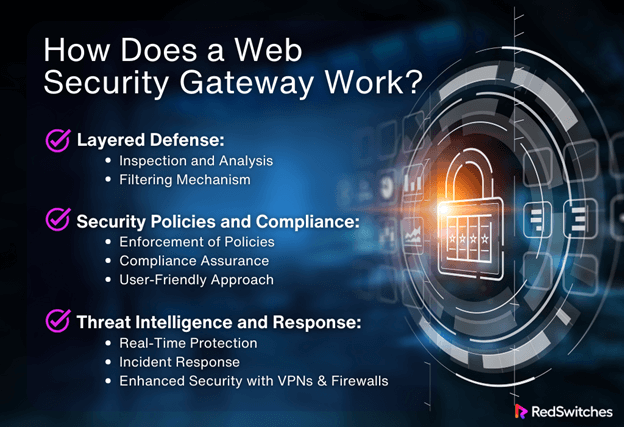
How Does a Web Security Gateway Work?
Web Security Gateways operate as meticulous scrutineers of web traffic, providing a shield between users and the boundless expanses of the internet, ensuring the sanctity of sensitive information and protecting against potential threats. Understanding how they work is akin to deciphering the operation of a vigilant watchman, meticulously screening everything that passes through the gateway.
Layered Defense:
Inspection and Analysis:
A Web Security Gateway meticulously inspects and analyzes every piece of incoming and outgoing data, assessing whether it adheres to established security protocols and policies. It scrutinizes URLs, IP addresses, and content to identify potential threats or malicious activities.
Filtering Mechanism:
It employs advanced filtering mechanisms to sift through web content, blocking inappropriate or harmful content and preventing it from reaching the user. This includes malware, phishing sites, and other malicious entities.
Security Policies and Compliance:
Enforcement of Policies:
It operates based on predefined security policies, enforcing rules and regulations to maintain a secure and compliant online environment. These policies dictate what kind of web content and applications are permissible and align user activities with organizational security objectives.
Compliance Assurance:
The gateway ensures that all online activities, data transactions, and user behaviors comply with regulatory requirements, minimizing the risk of legal repercussions and safeguarding organizational reputation.
User-Friendly Approach:
Simply put, imagine a Web Security Gateway as your personal online bodyguard, carefully examining everything you interact with on the internet, allowing only the safe and the legitimate to reach you while warding off the dangerous and the deceptive. It’s like having a filter that only lets in the clean, pure water while keeping out the dirt and impurities.
Threat Intelligence and Response:
Real-Time Protection:
A Web Security Gateway provides real-time protection, leveraging advanced threat intelligence to identify and respond to emerging threats promptly. It continually updates its knowledge base to recognize new threats, ensuring optimal security at all times.
Incident Response:
In case of any security incidents or breaches, the gateway swiftly initiates response protocols to contain and mitigate the threat, minimizing damage and preventing the propagation of malicious activities.
Enhanced Security with VPNs and Firewalls:
Many Web Security Gateways also integrate seamlessly with Virtual Private Networks (VPNs) and firewalls, offering an additional layer of protection. VPNs encrypt the user’s online activities, making them incomprehensible to any prying eyes, while firewalls serve as an additional barrier, blocking unauthorized access to the network.
Want a seamless, secure browsing experience? Dive into RedSwitches’ advanced VPN services and unlock a safer internet. Check it out now at RedSwitches VPN Hosting!
By understanding the workings of a web security gateway, users and organizations can leverage its capabilities to navigate the online world safely, avoiding the pitfalls and traps laid by cyber miscreants. In a world where digital interactions are integral to our daily lives, having such a guardian ensures we can explore, interact, and transact in the digital realm with peace of mind and assurance.
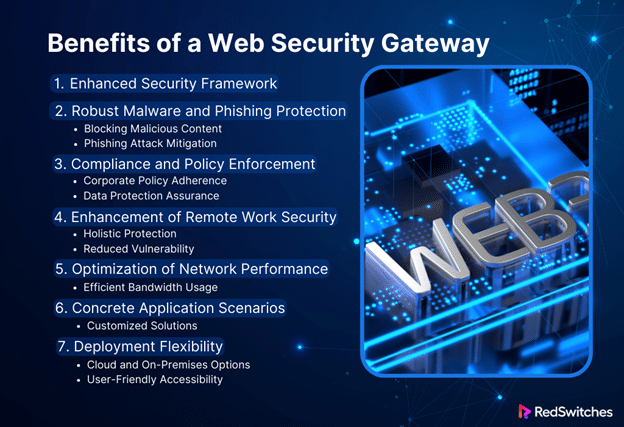
Benefits of a Web Security Gateway
As we delve deeper into the digital age, the demand for robust cyber security solutions, such as Web Security Gateways (SWG), is more pronounced than ever. This is substantiated by the anticipated surge in the Global Secure Web Gateway Market, projected to increase by USD 11710.84 million from 2022 to 2027. In this light, understanding the extensive benefits of SWGs becomes paramount for organizations aiming to fortify their digital frontiers against security threats.
Enhanced Security Framework:
Web Security Gateways, or SWGs, are indispensable tools in the digital landscape, fortifying organizational defenses against an array of web-based threats and ensuring secure, seamless online interactions.
Robust Malware and Phishing Protection:
Blocking Malicious Content:
SWGs provide an essential line of defense, denying access to harmful websites and preventing malware downloads, thus securing the network environment.
Phishing Attack Mitigation:
They can identify and counteract phishing attempts, protecting users from deceptive communications to harvest sensitive data.
Compliance and Policy Enforcement:
Corporate Policy Adherence:
These gateways enforce organizational web usage policies effectively, blocking access to specific or category-based websites and aiding in adherence to industry regulations.
Data Protection Assurance:
They mitigate the risk of unauthorized sensitive data uploads, safeguarding intellectual property and confidential information from potential leaks and breaches.
Enhancement of Remote Work Security:
Holistic Protection:
Remote employees, potentially more susceptible to cyber threats, are shielded effectively from web-based attacks, even when operating outside the corporate network’s safety.
Reduced Vulnerability:
This advantage is paramount in today’s era of flexible work arrangements, ensuring the security perimeter extends beyond the traditional office space.
Optimization of Network Performance:
Efficient Bandwidth Usage:
Credit: Pixabay
By caching frequently accessed web content, SWGs can reduce bandwidth consumption, improving network performance and user experience.
Concrete Application Scenarios:
Customized Solutions:
For instance, a financial services entity might leverage an SWG to restrict access to high-risk gambling sites. At the same time, a healthcare provider could utilize one to avert unauthorized patient data uploads.
Deployment Flexibility:
Cloud and On-Premises Options:
Whether deployed in the cloud or on-premises, SWGs offer versatility to suit organizational needs. The rising preference for cloud-based solutions stems from their ease of deployment and management.
User-Friendly Accessibility:
Understanding the utility of a Web Security Gateway need not be a complex affair. Visualize it as a diligent security officer, overseeing and controlling the flow of information between users and the vast expanse of the internet, allowing only safe and compliant interactions.
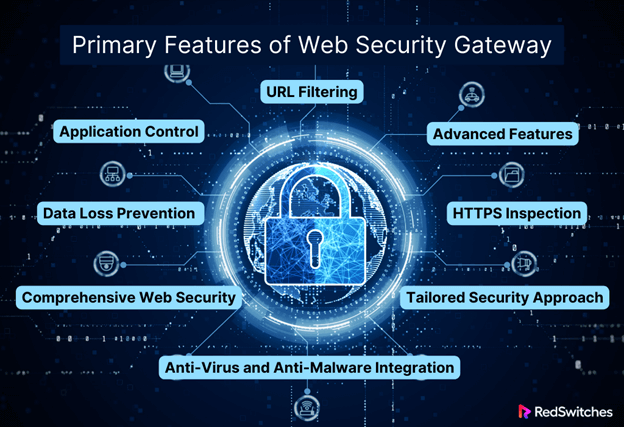
Primary Features of Web Security Gateway
The comprehensive nature of Web Security Gateways (SWGs) positions them as indispensable assets in any organization’s cybersecurity arsenal. Here, we unfold the myriad of features that SWGs bring to the table, which collectively work towards fortifying digital realms against potential cyber threats.
URL Filtering:
- Access Blockage:
- SWGs excel in blocking access to harmful websites, preventing malware downloads, and restricting entry to specific categories of sites, like social media or gambling, thus establishing a secure web browsing environment.
Application Control:
- Managed Access:
- They meticulously manage access to cloud and web-based applications, averting data leaks and safeguarding users from harmful applications, enabling organizations to maintain control over application usage and data flow.
Data Loss Prevention (DLP):
- Sensitive Data Protection:
- By preventing unauthorized uploads of sensitive data to external websites or cloud services, SWGs protect intellectual property and confidential information, mitigating risks associated with data exposure.
Anti-Virus and Anti-Malware Integration:
- Traffic Scanning:
- Integrated anti-virus and anti-malware capabilities allow SWGs to scan web traffic for malicious entities, protecting against malware infections and ensuring device safety.
HTTPS Inspection:
- Encrypted Traffic Scrutiny:
- Given the escalating web traffic encryption, the ability to inspect encrypted HTTPS traffic is crucial. This feature identifies and blocks hidden malware and threats within encrypted data streams.
Advanced Features:
- Content Filtering:
- SWGs extend their functionality to block specific content types, such as explicit or violent material, maintaining a professional and safe online environment.
- Bandwidth Management:
- They facilitate efficient bandwidth usage by limiting access to specific sites or applications, optimizing network performance, and ensuring uninterrupted workflow.
- Reporting and Analytics:
- With the capability to generate detailed reports and analytics on web usage and security threats, organizations can gain insights and stay informed about the prevailing security posture.
Comprehensive Web Security:
Web Security Gateways serve as a holistic security tool, crucial for organizations of varying sizes, aiming to protect against a spectrum of web-based threats, including malware, phishing, and data leakage. The relevance and priority of each feature may vary based on organizational needs and requirements, but collectively, these features form the backbone of comprehensive web security.
Credit: Pixabay
Tailored Security Approach:
Understanding and leveraging these multifaceted features of SWGs allow organizations to tailor their security approach, meeting specific needs and requirements and ensuring the integrity and safety of their digital interactions and transactions.
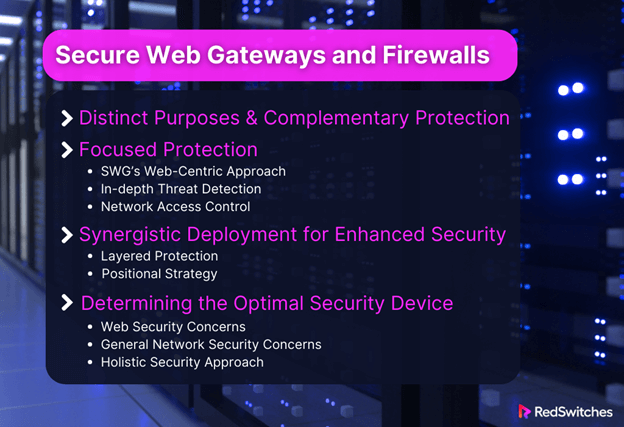
Secure Web Gateways and Firewalls
Web security gateways (SWGs) and Firewalls are the linchpins in constructing a robust network security infrastructure, each bringing unique capabilities to shield organizations from diverse threats. To navigate the maze of network security effectively, a profound understanding of the roles, functionalities, and optimal application of both these components is indispensable.
Distinct Purposes & Complementary Protection:
- Firewalls:
- Firewalls are the sentinels at the gateway between a network and the internet, scrutinizing every piece of incoming and outgoing traffic and enforcing predefined rules to block unauthorized access, curb malware propagation, and fend off varied network attacks.
- Web security gateways:
- Tailored to thwart web-based threats, SWGs meticulously inspect web traffic in both directions, safeguarding organizations from malware phishing and enforcing adherence to web usage policies by blocking access to specified websites or categories.
Focused Protection:
- SWG’s Web-Centric Approach:
- The critical differentiator between SWGs and Firewalls is their focus; while SWGs specialize in securing against web-centric threats, firewalls emphasize broader network security.
- In-depth Threat Detection:
- Due to their specialized nature, SWGs hold an edge in detecting and neutralizing web-based threats like malware and phishing attacks.
- Network Access Control:
- Conversely, firewalls excel in barricading unauthorized network access and mitigating malware spread across the network, offering a holistic network security umbrella.
Synergistic Deployment for Enhanced Security:
- Layered Protection:
- Deploying SWGs and Firewalls in tandem provides a layered security posture, with SWGs acting as the first line of defense against web-based threats and Firewalls bolstering the security against broader network intrusions.
- Positional Strategy:
- Placing SWGs in front of firewalls adds an extra security layer against web-centric threats, and situating firewalls behind SWGs enhances the defenses against potential network incursions.
Determining the Optimal Security Device:
Credit: Pexels
The right choice between an SWG and a firewall hinges on your organization’s needs and concerns.
- Web Security Concerns:
- If the primary focus is web security, SWGs are the go-to option, specializing in combating web-centric threats.
- General Network Security Concerns:
- For concerns enveloping overall network security, firewalls are the optimal choice, offering a broader protective scope.
- Holistic Security Approach:
- For organizations aiming for a well-rounded protection strategy, integrating both SWGs and Firewalls is the optimal pathway to ensure both web and general network security are uncompromised.
Discover the diverse world of firewalls and how they can fortify your network! Dive deep into our comprehensive guide on ‘Different Types of Firewalls For Your Networks.’
How Do Web Security Gateways Enforce Security Policies?
Web Security Gateways (SWGs) are paramount in establishing a fortified digital environment, meticulously enforcing security policies to shield against many web-based threats. By implementing varied security protocols and controls, SWGs ensure that organizations’ digital interactions remain secure and uncompromised. Below, we delve into how SWG effectively executes and upholds these security policies.
URL Filtering:
Purposeful Navigation Control:
URL Filtering is pivotal in controlling and managing web access, allowing organizations to block access to malicious, inappropriate, or unauthorized websites, thus preventing exposure to harmful content and potential security threats.
Enhanced Security Posture:
By restricting access to specific categories of websites, organizations can mitigate risks associated with phishing, malware, and other cyber threats, maintaining a secure and productive online environment.
Customizable Access Parameters:
Organizations can tailor the URL filtering parameters to align with their unique security needs and organizational policies, ensuring optimal protection and compliance with regulatory standards.
Credit: Pixabay
Anti-Malware Scanning:
Proactive Threat Identification:
Anti-malware scanning serves as the frontline defense against malicious software, enabling SWGs to scrutinize and identify potential threats within web traffic and promptly neutralize them before reaching the end-user.
Comprehensive Protection:
This feature offers broad-spectrum protection against various forms of malware, including viruses, worms, Trojans, and more, safeguarding organizational data and infrastructure from potential breaches and damages.
Timely Updates & Evolving Defense:
Regular updates to anti-malware definitions ensure that the SWGs are equipped to combat the latest threats, evolving with the ever-changing cyber threat landscape.
Application Control:
Managed Application Access:
Application control is crucial for managing access to web-based and cloud applications, allowing organizations to prevent unauthorized use and potential data leakage, thereby ensuring data security and integrity.
Optimized Resource Utilization:
Organizations can optimize bandwidth and resource utilization by controlling access to non-essential applications, improving overall network performance and productivity.
Granular Control & Policy Enforcement:
It empowers organizations to enforce granular policies on application usage based on user roles, time, and other parameters, offering flexibility while maintaining stringent security controls.
Holistic Policy Enforcement for Robust Security:
Multi-Layered Security Approach:
Through the amalgamation of URL Filtering, Anti-Malware Scanning, and Application Control, SWGs provide a multi-layered security approach, addressing various facets of web security and ensuring a resilient defense against potential threats.
Adaptive Policy Implementation:
Implementing adaptive and customizable security policies allows organizations to effectively address their unique security concerns and compliance requirements, fostering a secure and compliant digital ecosystem.
Enhanced User Experience:
While maintaining stringent security controls, the user-centric design of SWGs ensures minimal disruption to user experience, promoting a balance between security and usability.
Concerned about potential vulnerabilities in your web security? Dive deeper into potential threats with our ‘Ultimate Guide to What is Tailgating in Cyber Security!
Credit: Pixabay
Conclusion
In the fast-paced, ever-evolving world of the internet, security is not just a necessity—it’s a critical component in safeguarding organizational integrity and data. Imagine navigating this complex digital universe, empowered by advanced web security gateways that promise security, optimized performance, and reliability!
This is where RedSwitches steps in with its diverse and extensive suite of services. Offering Managed Cloud Solutions anchored in their sophisticated Bare-Metal Cloud Platform, RedSwitches is a beacon for organizations aspiring for superior web security solutions.
Dive into RedSwitches’ Advanced Solutions and solidify your organization’s digital realm with unmatched security and optimal performance!
FAQs
Q. What is a web security gateway?
A Web Security Gateway (WSG) is a tool that screens and removes harmful software/malware from web traffic initiated by users while also upholding company and regulatory standards.
Q. What is the difference between SWG and WAF?
SWG (Secure Web Gateway) primarily focuses on filtering outbound internet traffic to protect users from online threats. At the same time, WAF (Web Application Firewall) is designed to protect a specific web application from incoming malicious traffic or attacks.
Q. What is the difference between VPN and SWG?
A VPN (Virtual Private Network) is a system that secures users’ online data by encrypting it and channeling it through a distant server, concealing their online presence and enhancing privacy. On the other hand, SWG (Secure Web Gateway) is a security solution that filters internet traffic to block threats and enforce compliance.
Q. What is web security with examples?
Web security protects websites, web applications, and web services against malicious attacks, unauthorized access, and other cyber threats. Examples include SQL injection, cross-site scripting (XSS), distributed denial-of-service (DDoS) attacks, and session hijacking.
Q. Is SWG a proxy?
Yes, an SWG (Secure Web Gateway) typically functions as a proxy, inspecting and filtering web traffic to block malicious content and enforce corporate policies.
Q. What is a secure web gateway?
A secure web gateway (SWG) is a security solution that prevents access to malicious web resources and inspects web requests to ensure they comply with an organization’s security policies.
Q. How does a secure web gateway work?
A secure web gateway protects an organization’s web traffic by inspecting web requests and filtering out malicious web content. It uses a security stack and cloud-based security service to analyze and control web traffic.
Q. What is the role of a web gateway in network security?
A web gateway acts as a proxy between the organization’s internal network and the internet, filtering and inspecting web traffic to ensure it is safe and compliant with the organization’s security policies.
Q. What is a cloud access security broker (CASB) in relation to a secure web gateway?
A cloud access security broker (CASB) is a security solution that provides visibility and control over the use of cloud-based web applications and services. It can work in tandem with a secure web gateway to enhance cloud access security.
Q. What is a cloud-based secure web gateway?
A cloud-based secure web gateway is a security solution that utilizes cloud-based infrastructure to inspect and filter web traffic, providing superior web security without the need for on-premises hardware or software.
Q. What is a gateway service in the context of a secure web gateway?
A gateway service refers to the secure web gateway solution that is used to filter and inspect web traffic, ensuring it is safe and compliant with the organization’s security policies.
Q. How does Forcepoint One SWG contribute to security architecture?
Forcepoint One SWG is a secure web gateway solution that integrates with an organization’s existing security architecture, enhancing web security by providing granular control and visibility over web traffic.
Q. Why do organizations need a secure web gateway?
Organizations need a secure web gateway to protect their network and users from potential threats and to ensure compliance with company security policies. It helps prevent access to malicious web resources and enforces secure web browsing.
Q. How does a secure web gateway help with web security?
A secure web gateway helps with web security by inspecting web requests and filtering out malicious web content. It ensures that web traffic complies with the organization’s security policies and protects against threats.
Q. What is the difference between a secure and secure web gateway?
A web secure gateway is a security platform providing secure access to an organization’s web resources. On the other hand, a secure web gateway is a security solution that protects an organization’s web traffic and filters out malicious content.