In this increasingly digital world, web applications have become integral to our daily lives. From online shopping to social networking and everything in between, web applications are the backbone of our online experiences.
This ubiquity makes them a prime target for cyber security challenges. This is where web application security comes into play. Based on an analysis of 7 million websites, SiteLock reports that websites presently encounter 94 attacks daily and receive 2,608 weekly bot visits.
This is why every layer of security matters, from the basics of online security to strengthening applications with secure coding techniques. This comprehensive guide will delve deep into the complex universe of web applications security, covering everything from its definition and importance to testing methods, common risks, best practices, and key takeaways.
Let’s Begin!
Table of Contents
- What is Web Application Security?
- What is Web Application Security Testing?
- How Does Web Application Security Work?
- Common Application Security Risks
- Broken Access Control
- Cryptographic Failures
- Injection (Including XSS, LFI, and SQL Injection)
- Insecure Design
- Security Misconfiguration (Including XXE)
- Vulnerable and Outdated Components
- Identification and Authentication Failures
- Software and Data Integrity Failures
- Security Logging and Monitoring Failures
- Server-Side Request Forgery
- Web Application Security Best Practices
- Best Tools For Web Application Security
- Key Takeaways
- FAQs
What is Web Application Security?
Web application security protects web applications from vulnerabilities and threats compromising data and services’ confidentiality, integrity, and availability. It encompasses a wide range of techniques, technologies, and best practices designed to ensure that web applications remain secure throughout their lifecycle.
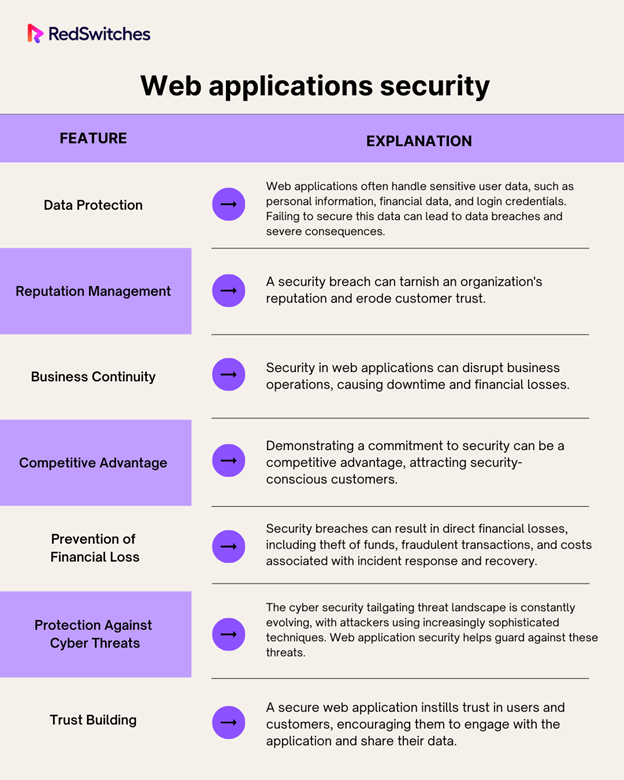
Why Web Application Security is Important?
The market for progressive web application development showed a rise of 31.9% CAGR from 2017 to 2027, according to Emergen Research. This market had a 2019 valuation of $1.13 billion.
However, with the increase in usage of Web Applications and cloud computing, the importance of web applications security cannot be overstated.
Here are several compelling reasons why it should be a top priority for any organization or individual:
What is Web Application Security Testing?
Web application security testing is a critical process that involves evaluating the security of a web application by identifying vulnerabilities, weaknesses, and potential threats. This testing helps organizations uncover and remediate security issues before exploitation by malicious actors.
There are several approaches to web application security testing, each with its own advantages and use cases. The three primary types of web application security testing are:
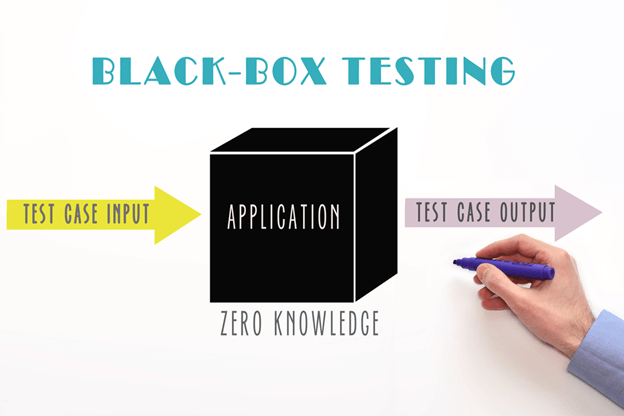
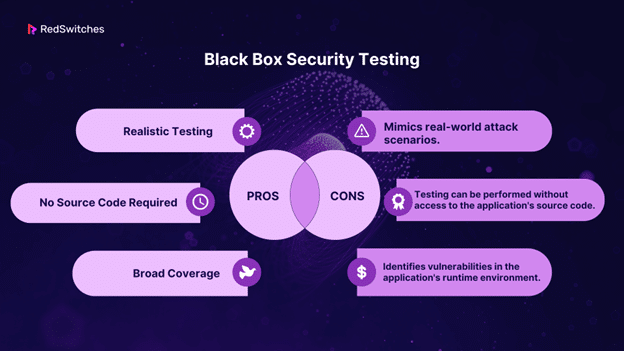
Black Box Security Testing
Black box testing, known as dynamic analysis, simulates an attacker’s perspective. Testers do not know the application’s internal workings or source code. They interact with the application as a regular user would, attempting to identify vulnerabilities through various inputs and interactions.
Black box testing is a robust testing methodology as it comprehensively assesses a system from start to finish. Like end-users who are primarily concerned with the functionality and responsiveness of a system, regardless of its internal coding or architecture, a tester can mimic user interactions to gauge if the system meets its expected outcomes. Throughout this process, black box testing scrutinizes all pertinent subsystems, encompassing UI/UX, web servers or application servers, databases, dependencies, and interconnected systems.
Standard Tools for Black Box Testing: Burp Suite, OWASP ZAP, Acunetix.
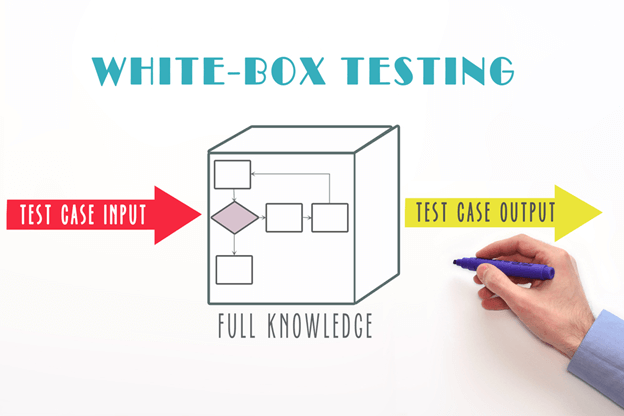
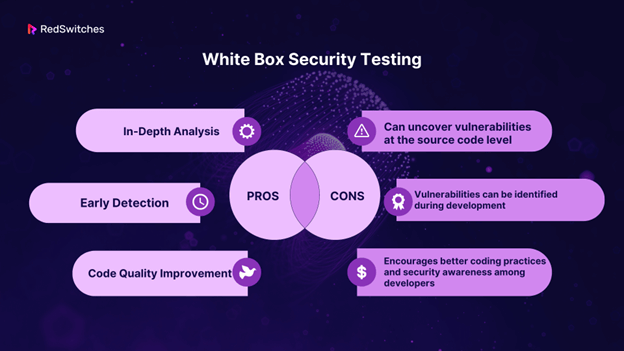
White Box Security Testing
White box testing, also known as static analysis or code review, involves inspecting the application’s source code, architecture, and design for security vulnerabilities. Testers have access to the application’s inner workings, allowing them to identify potential flaws from a code and design perspective.
Standard Tools for White Box Testing: Checkmarx, Fortify, SonarQube.
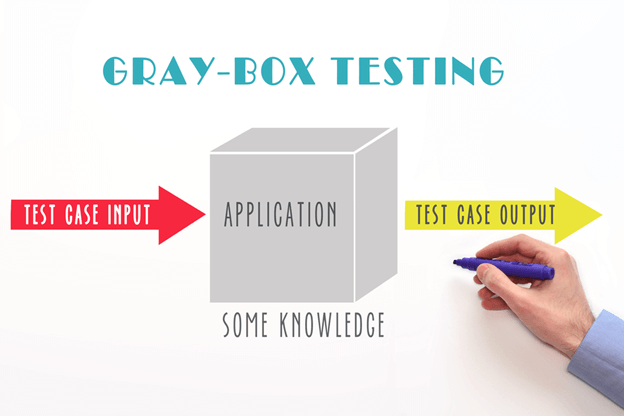
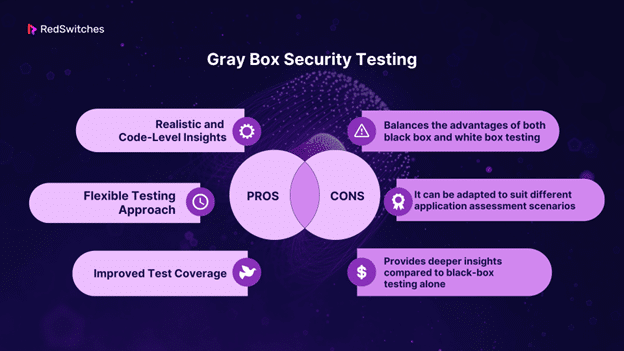
Gray Box Security Testing
Gray box testing combines elements of both black box and white box testing. Testers have partial knowledge of the application’s internals, such as access to design documents or limited source code. This approach offers a balance between realism and code-level analysis.
Standard Tools for Gray Box Testing: AppScan, Qualys Web Application Scanning.
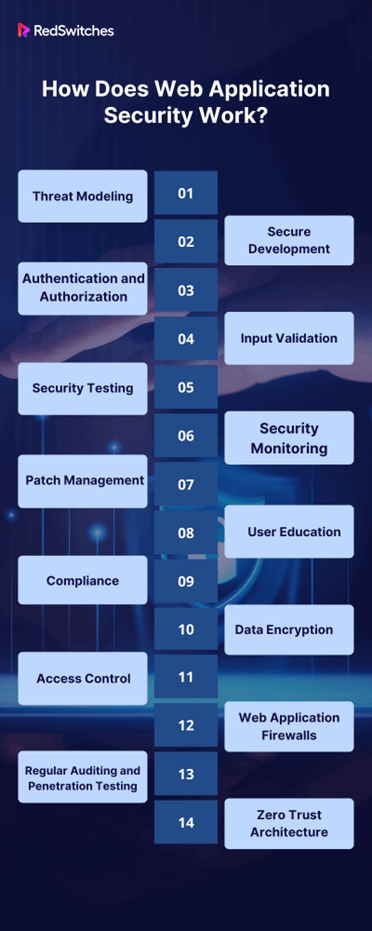
How Does Web Application Security Work?
Web application security is a multi-faceted discipline that employs various techniques and technologies to protect web applications. It is the guardian of the technologies utilized in web application development, furnishing a robust shield against online threats and thereby ensuring the secure functioning of web applications. A pivotal component of establishing web app security is the comprehensive examination of security features in web applications testing.
Web application security testing revolves around identifying and rectifying vulnerabilities before their exploitation by malicious actors. Conducting such tests at various stages of the Software Development Life Cycle (SDLC) is strongly advocated over waiting until after the web application’s launch. Integrating testing throughout every SDLC phase empowers developers to proactively tackle potential security issues, transforming security features in web applications from an afterthought into a foundational element seamlessly woven into the development process.
Here’s a high-level overview of how it works:
Threat Modeling
Security experts analyze the web application’s architecture and identify potential threats and vulnerabilities. This involves considering how attackers might exploit weaknesses in the application.
Secure Development
During the development phase, security best practices are integrated into the development process. This includes writing secure code, using secure libraries, and following secure coding guidelines.
Authentication and Authorization
Implement robust authentication and authorization mechanisms to ensure that only authorized users can access certain application parts. This helps prevent unauthorized access to sensitive data and functionalities.
Input Validation
Input from users should be validated to prevent common attacks like SQL injection and cross-site scripting (XSS). Input validation ensures that the application processes only safe and expected data.
Security Testing
As discussed earlier, web applications undergo various security tests, including black box, white box, and gray box testing. This helps identify and remediate vulnerabilities before the application goes live.
Security Monitoring
Continuous monitoring of the application’s behavior and traffic can detect anomalies and potential security incidents in real-time. Security information and event management systems are often used for this purpose.
Patch Management
Regularly updating the web application and its dependencies to patch known vulnerabilities. This is crucial for staying protected against emerging threats.
User Education:
Educate users and administrators about best practices, such as creating strong passwords and recognizing phishing attempts. Security awareness is a critical component of web application security.
Compliance:
Ensure the web application complies with relevant security standards and regulations, such as the Payment Card Industry Data Security Standard or the General Data Protection Regulation.
Data Encryption:
Use encryption protocols like HTTPS to protect data in transit. Sensitive data should be encrypted when stored in databases.
Access Control
Implement strict access controls to restrict access to sensitive areas and functionalities of the application. This minimizes the attack surface for potential threats.
Web Application Firewalls
Deploy WAFs to filter incoming traffic and block malicious requests. WAFs use rule-based or behavioral analysis to identify and block suspicious activity.
Regular Auditing and Penetration Testing
Conduct periodic security audits and penetration testing to evaluate the effectiveness of security measures and discover new vulnerabilities.
Zero Trust Architecture
Adopt a zero-trust approach, which assumes that no one—inside or outside the organization—should be trusted by default. This approach emphasizes strict identity verification and continuous monitoring.
Common Application Security Risks
Understanding the common risks and vulnerabilities web applications face is crucial for effective web application security. Let’s explore some of the most prevalent risks:
Broken Access Control
Broken access control occurs when an application fails to enforce proper user access restrictions. This can lead to unauthorized users gaining access to sensitive data or performing actions they shouldn’t be able to.
Example: A user with regular privileges can manipulate the URL to access another user’s account or data.
Prevention: Implement strong authentication, clear authorization rules, secure session management, and regular testing to prevent unauthorized access.
Cryptographic Failures
Cryptographic failures involve weaknesses or misconfigurations in the encryption and decryption processes. These can lead to data leaks, as encrypted data becomes accessible to attackers.
Example: Storing encryption keys insecurely or using outdated encryption algorithms can result in cryptographic failures.
Prevention: Use robust encryption algorithms, secure key management, and TLS for data in transit. Avoid roll-your-own cryptography.
Injection (Including XSS, LFI, and SQL Injection)
Injection attacks occur when malicious code or data is injected into an application, often by exploiting vulnerabilities in user inputs. Common injection attacks include Cross-Site Scripting (XSS), Local File Inclusion (LFI), and SQL Injection.
Example: In an SQL injection attack, an attacker inserts malicious SQL code into an input field to manipulate the application’s database queries.
Prevention: Validate and sanitize user inputs, use parameterized queries, apply output encoding, and provide security training to prevent injection attacks.
Insecure Design
Insecure design refers to flaws in the overall architecture and design of the web application. These flaws can create vulnerabilities that are difficult to mitigate without significant redesign efforts.
Example: Lack of proper authentication and authorization mechanisms in the initial design can lead to insecure access control.
Prevention: Incorporate threat modeling, robust authentication, and authorization mechanisms early in the design phase. Follow secure architecture patterns.
Security Misconfiguration (Including XXE)
Security misconfiguration occurs when the application or its components are not properly configured to protect against common security risks. This can result in unintended exposure of sensitive information.
Example: Exposing sensitive configuration files, default credentials, or unnecessary services can lead to security misconfiguration.
Prevention: Configure with secure defaults, automate scanning, audit access controls, validate configuration inputs, and maintain documentation.
Vulnerable and Outdated Components
Using outdated or vulnerable third-party components, libraries, or frameworks can introduce security risks to the application. Attackers often target known vulnerabilities in these components.
Example: Failing to update a widely used JavaScript library with a known security vulnerability can lead to exploitation.
Prevention: Maintain a dependency inventory, scan for vulnerabilities, apply patches promptly, avoid deprecated components, and follow secure coding practices.
Identification and Authentication Failures
Weak or inadequate identification and authentication mechanisms can allow unauthorized users to access the application. This includes weak passwords, lack of multi-factor authentication, and inadequate session management.
Example: Allowing users to create weak passwords or using session IDs that are easy to predict can result in authentication failures.
Prevention: Enforce strong password policies, encourage multi-factor authentication, secure session management, hash passwords securely, and conduct regular audits.
Software and Data Integrity Failures
Failures related to software and data integrity occur when an attacker can tamper with or modify data, leading to incorrect or malicious outcomes.
Example: Failing to validate data integrity checks, such as checksums, can enable attackers to modify data packets in transit.
Prevention: Validate data inputs, implement data integrity checks, encrypt sensitive data, use code signing, and conduct security testing.
Security Logging and Monitoring Failures
Inadequate or improper security logging and monitoring can make detecting and responding to security incidents difficult.
Example: Failing to monitor login attempts or not setting up alerts for suspicious activities can lead to security logging and monitoring failures.
Prevention: Develop a comprehensive log strategy, set up automated alerts, conduct regular log reviews, integrate with SIEM, and have an incident response plan.
Server-Side Request Forgery
Server Side Request Forgery (SSRF) occurs when an attacker tricks the server into making requests on their behalf. This can lead to unauthorized access to internal resources or services.
Example: An attacker manipulates a web application’s input to make the server fetch sensitive data from an internal database and send it to them.
Prevention: Validate user inputs, implement URL whitelisting, use safe APIs, check and validate HTTP parameters, and include SSRF testing in security assessments.
Also Read: Unveiling the Hidden Risks of Dedicated Servers
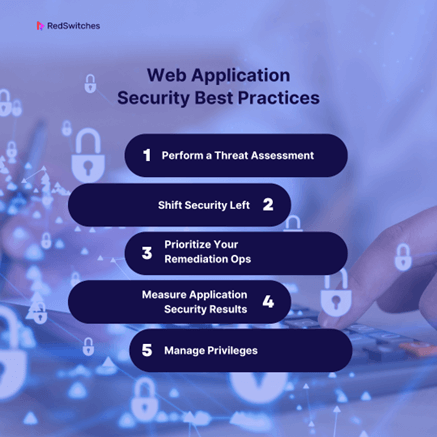
Web Application Security Best Practices
To establish robust web app security, organizations and developers should follow a set of best practices throughout the development lifecycle. Here are some key best practices to consider:
Perform a Threat Assessment
Before developing or deploying a web application, conduct a thorough threat assessment. Identify potential risks and vulnerabilities specific to your application’s architecture and functionality. Understanding the threat landscape will help you prioritize security measures effectively.
Shift Security Left
“Shift left” means integrating security practices early in the development process. Security should not be an afterthought; it should be considered from the project’s inception. Developers should receive security training and know best practices for writing secure code.
Prioritize Your Remediation Ops
Security vulnerabilities are not equally critical. Prioritize and remediate vulnerabilities based on their severity and potential impact. Focus on critical vulnerabilities that can lead to data breaches or system compromise.
Measure Application Security Results
Implement metrics and Key Performance Indicators (KPIs) to measure the effectiveness of your web security efforts. Regularly assess the security posture of your application, track vulnerabilities, and evaluate the success of security controls.
Manage Privileges
Implement the principle of least privilege (PoLP) to ensure that users and processes have the minimum access required to perform their tasks. This reduces the attack surface and limits potential damage from security breaches.
Also Read: A Comprehensive Guide to Application Development Cloud Computing
Best Tools For Web Application Security
As cyber threats continue to increase, the tools we use to defend against them must be robust, reliable, and always a step ahead. Below is a list of the best tools available for ensuring the safety of your web applications. Whether you’re a developer, an IT specialist, or simply someone interested in web security, these tools are essential in your arsenal.
1. OWASP ZAP (Zed Attack Proxy)
Starting with one of the most sought-after free security tools for web application security, OWASP ZAP is an open-source web application penetration testing tool. It assists in identifying vulnerabilities and provides features to test them. With an intuitive UI and powerful scanning capabilities, it is ideal for beginners trying to understand web application vulnerabilities and seasoned professionals.
2. Burp Suite
Burp Suite is one of the most esteemed tools in web application security. It’s an integrated platform providing various tools to identify web application vulnerabilities. With functionalities like intercepting proxy, automated scanning, and the ability to reuse its web vulnerability scanner’s results, it’s a tool many professionals swear by. While there’s a free version available, the paid version offers extended capabilities.
3. Qualys Web Application Scanning (WAS)
Qualys WAS is a cloud-based scanner to identify web application security vulnerabilities. It provides continuous web app discovery and detection of vulnerabilities, ensuring robust coverage. Its automated scans and ability to scale make it suitable for both small and large organizations.
4. Checkmarx
Checkmarx is more than just a vulnerability scanner. It is a comprehensive software security solution. It focuses on identifying and mitigating risks in the codebase before they become actual threats. Ideal for developers, it integrates smoothly into the SDLC (Software Development Life Cycle), ensuring that security checks occur throughout the development process.
5. WebInspect
Offered by Micro Focus, WebInspect is a dynamic web application security testing tool. It offers interactive and dynamic application security testing for complex web applications and services. Its real-time, runtime testing capabilities ensure it can detect real-world threats, providing actionable insights.
6. Acunetix
Acunetix is a web vulnerability scanner curated to mimic real-world hacking methodologies. It can crawl and analyze different types of web applications, detecting vulnerabilities ranging from SQL Injection to Cross-Site Scripting. With a user-friendly dashboard and detailed reporting, Acunetix ensures you’re always in the loop about your web application’s security posture.
7. Netsparker
Netsparker stands out for its automation capabilities. It’s designed to identify vulnerabilities from the early stages of development, and its Proof-Based Scanning technology automatically verifies the detected vulnerabilities, minimizing the need for manual checks. This automation ensures that the security team can focus on tackling the vulnerabilities instead of verifying them.
Key Takeaways
In this extensive exploration of web app security, we’ve covered many topics, from the importance of web application security to various testing methods, shared risks, and best practices. Here are the key takeaways:
- It is essential to protect sensitive data, maintain trust, comply with regulations, and prevent financial losses and reputational damage is essential.
- Its testing includes black, white, and gray box testing, offering unique insights into vulnerabilities and weaknesses.
- Web security involves a multi-layered approach, from threat modeling and secure development to continuous monitoring and incident response.
- Common application security risks include broken access control, cryptographic failures, injection attacks, insecure design, and security misconfiguration.
- Best practices include performing threat assessments, shifting security left, prioritizing vulnerability remediation, measuring security results, and managing privileges.
- Continuous improvement and vigilance are crucial for maintaining robust web security in the face of evolving threats.
Ready to fortify your web application’s security? Partner with RedSwitches, your trusted cybersecurity ally. Our experts can help you navigate the complex universe of web app security and tailor a comprehensive strategy to safeguard your digital assets. Don’t wait for threats to compromise your online presence.
Contact us today to take proactive steps towards a more secure future and to get in touch with one of our security engineers for advice on enhancing your digital and physical security.
FAQs
Q. What is Web Application Security?
Web application security protects web applications from vulnerabilities and threats compromising data and services’ confidentiality, integrity, and availability. It encompasses various techniques, technologies, and best practices to ensure that web applications remain secure throughout their lifecycle.
Q. How to do web application security?
It involves a multi-layered approach, including threat modeling, secure development, testing (black box, white box, and gray box), security monitoring, incident response, and regular updates. It also includes user education, compliance with security standards, and access control.
Q. Why do we need web application security?
Protecting sensitive data, maintaining trust, complying with regulations, preventing financial losses, and preventing reputational damage is essential. Web applications are vulnerable to cyber threats and attacks without proper security measures.
Q. What is web application security?
Web application security is the practice of protecting websites and web applications from various security threats and vulnerabilities.
Q. Why is web application security important?
Web application security is important because it helps prevent unauthorized access, protect sensitive data, and maintain users’ trust.
Q. What are some common web application security risks?
Some common web application security risks include cross-site scripting (XSS), SQL injection, cross-site request forgery (CSRF), and remote code execution.
Q. What is OWASP Top 10?
OWASP Top 10 lists the top 10 most critical web application security risks published by the Open Web Application Security Project (OWASP).
Q. How can I secure my web application?
There are several ways to secure your web application, including implementing secure coding practices, conducting regular security testing, using firewalls and intrusion detection systems, and keeping software and plugins up to date.
Q. What is static application security testing?
Static application security testing (SAST) identifies potential security vulnerabilities in an application’s source code without actually running the application.
Q. What is runtime application self-protection?
Runtime application self-protection (RASP) is a security technology that is designed to detect and prevent attacks against web applications and APIs at runtime.
Q. How can I identify potential security vulnerabilities in my web application?
You can identify your web application’s potential vulnerabilities by conducting regular security assessments, penetration testing, and code reviews.
Q. What is the Open Web Application Security Project (OWASP)?
The Open Web Application Security Project (OWASP) is a non-profit organization that provides information and resources to help secure web applications.
Q. What should be included in a web application security checklist?
A web application security checklist should include secure authentication and authorization mechanisms, input validation, protection against known vulnerabilities, secure error handling, and secure communication.