Key Takeaways
- Dedicated server security provide exclusive resources and enhanced performance.
- Strong security measures protect sensitive information and maintain customer trust.
- Regular updates and patch management are foundational to server security.
- Advanced security technologies and practices, such as encryption for data in transit.
- Proactive monitoring and dedicated support from hosting providers can enhance security through constant vigilance and rapid response to potential threats.
- Backups and disaster recovery plans ensure data integrity and availability.
- Server security is a continuous process that requires regular evaluation and adaptation to new threats.
In today’s digital world, keeping your data safe is more important than ever. When you use a dedicated server, your data gets top-notch security. This type of server is just for you. Unlike shared hosting, where you share space with others, a dedicated server means everything is under your control. This setup is like having your guard for your online space.
Dedicated servers offer strong protection because they can be customized to fit your security needs. You can set up firewalls, security software, and other tools just how you like them. This is great for protecting your data from hackers and other online threats.
Plus, since you’re not sharing the server, there’s less chance of getting caught in any issues caused by others. In short, dedicated servers give you a private, secure space on the internet, making them a smart choice for anyone serious about their online security.
Table of Contents
- Key Takeaways
- What Are Dedicated Servers?
- Advantages of Server
- Disadvantages of Server
- Why Is Server Security Important?
- Benefits of Secure Server Hosting
- 11 Ways for Optimum Dedicated Server Security
- Patch Management and Routine Updates
- Setting Up a Firewall
- Systems for detecting and preventing intrusions (IDS/IPS)
- Safe SSH Connection
- Employ Password Policies and Strong Passwords
- Put into Practice 2FA, or Two-Factor Authentication
- Turn Off Any Unused Ports and Services
- Secure Network Services
- Continual Backups
- Protection against malware and viruses
- Vulnerability scanning and security audits
- Five Additional Tips for Dedicated Server Security
- Conclusion
- FAQs
What Are Dedicated Servers?
Credits: Freepik
What are dedicated servers? These are strong, high-end physical servers hosting the data, apps, and services for a single client, company, or project. Servers give customers access to the server’s resources and powers. This is different from shared hosting and virtual private servers (VPS). On those, resources like CPU time, memory, and storage space are split among many users.
These servers are the best option for companies and people with complex applications, sensitive data, or high-traffic websites. The servers are exclusive, which brings big benefits in performance, dependability, and security.
The key component of this server is its capacity for complete customization to match the unique requirements of its users. Clients can customize the server to fit their applications’ needs. They can do this because they control the operating system, program installations, and hardware setup. Clients have root or admin access to the server. They use it to do installations, upgrades, or modifications. This gives them control over server administration.
Furthermore, these servers are renowned for their improved dependability and performance. Clients have fast, reliable connections. They have their own storage and processing power. This is because the server’s resources are not shared. This results in faster page loads, more seamless application performance, and the capacity to handle massive traffic volumes without experiencing a drop in service.
Advantages of Server
Credits: Freepik
Let’s discuss the advantages of a server.
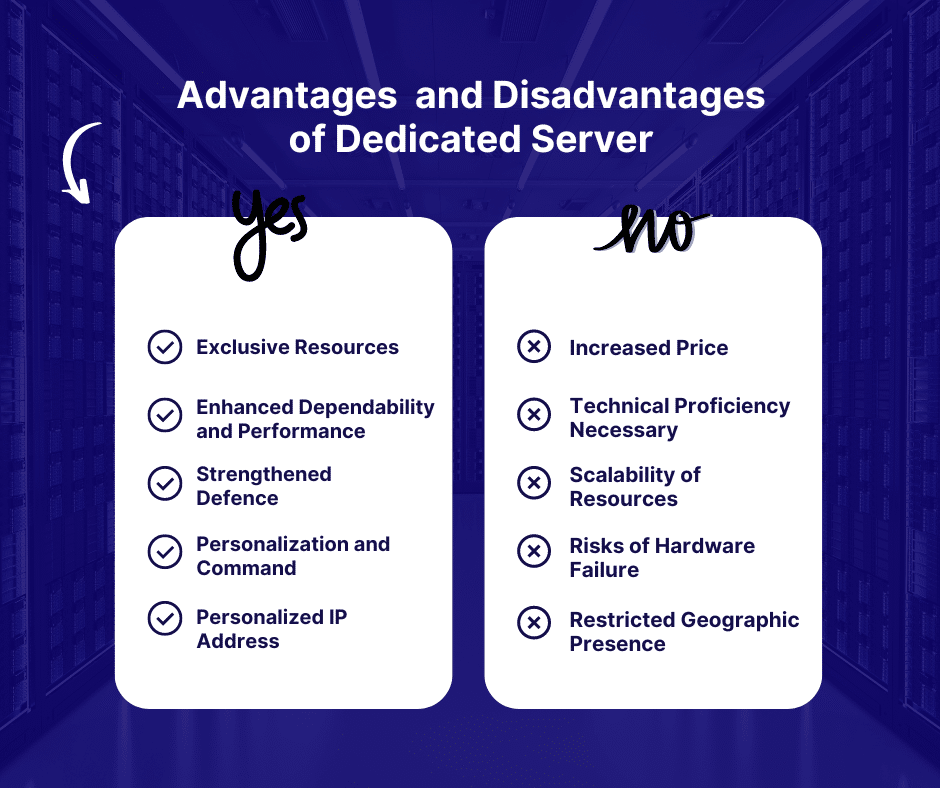
Exclusive Resources
A single client has access to all of the server’s resources in a server environment, including the CPU, RAM, disc space, and bandwidth. This exclusivity guarantees that no other user’s operations will interfere. Owning dedicated resources ensures steady and predictable performance. This is for firms with resource-hungry applications, like large databases, complex SaaS apps, or busy websites. This can improve user experiences and possibly increase conversion rates.
Enhanced Dependability and Performance
These servers can process large amounts of data and handle traffic better than shared hosting or virtual private servers (VPS). This is so your activities can fully utilize the server’s memory and processing power. These results are: faster web page loads, quicker data processing, and higher uptime. The server’s performance doesn’t depend on other users’ stress. This is a frequent problem in shared hosting. So, this improves reliability.
Also Read: Dedicated Servers for Gaming: Transforming the Multiplayer Experience
Strengthened Defence
Choosing a server allows you to put strong security measures customized to meet your needs. This covers intrusion detection systems, sophisticated firewall setups, and frequent security audits. You can implement stronger access controls to lower the risk of data breaches greatly. You can also use stronger encryption mechanisms for data in transit and at rest. These servers are a good choice for companies operating in sectors like healthcare or finance. They are subject to strict data protection regulations.
Personalization and Command
Having server root access to the server gives you many more customization choices. You can install any software. You can set up the server to your exact specifications. You can adjust settings to boost the performance of your websites or apps. This control is vital for developers and IT specialists. They use it to optimize for maximum effectiveness, security, and dependability. They may be for specific databases, server-side tech, or custom software.
Personalized IP Address
When using shared hosting, your website may suffer by association if another website on the same server participates in malicious activity or is blacklisted. When you have a dedicated IP, you have total control over your IP address’s reputation, which is important for keeping visitors trusting you and guaranteeing email delivery.
Also Read : Advantages of Dedicated server , Role of Dedicated server hosting and Ecommerce dedicated server hosting
Disadvantages of Server
Credits: Freepik
After discussing the merits, let’s focus on some of the shortcomings of these types of servers.
Increased Price
One of its biggest drawbacks is the increased cost of servers compared to shared hosting or virtual private servers (VPS). The cost results from the advanced hardware, degree of support, and exclusive use of server resources. The server cost may be out of reach for startups or small enterprises with tight budgets, particularly when considering the total cost of ownership, which includes setup, upkeep, and possible hardware updates.
Technical Proficiency Necessary
Managing a server frequently takes a certain level of technical know-how. Users need to be able to manage security protocols, install software and updates, configure the server, and carry out regular maintenance. Although these services are included in some hosting providers’ managed server solutions, they are expensive. The technical requirements of administering a server can be very difficult for businesses without a professional IT staff.
Scalability of Resources
Increasing server capacity might be more difficult and time-consuming than cloud hosting options, even when they permit hardware upgrades. Upgrading the CPU, RAM, or server storage usually requires physical modifications to the server and downtime. In contrast, cloud infrastructures frequently allow instantaneous resource scaling with little downtime.
Risks of Hardware Failure
Like any physical gear, servers might malfunction due to power supply problems, hard drive crashes, and other component failures. Even though trustworthy hosting companies frequently reduce these risks with redundant systems and backups, hardware breakdowns can still cause downtime and data loss. This danger is not as great since data in cloud hosting systems is spread across several physical servers.
Also Read: Dedicated server hardware
Restricted Geographic Presence
Depending on the provider, servers could be situated in particular data centers, which might be far from your user base. This may lead to increased latency for visitors far from the server, impairing your website or application’s functionality and user experience. Because cloud services frequently provide a wider range of locations and data centers, it is possible to optimize latency more effectively depending on the location of your audience.
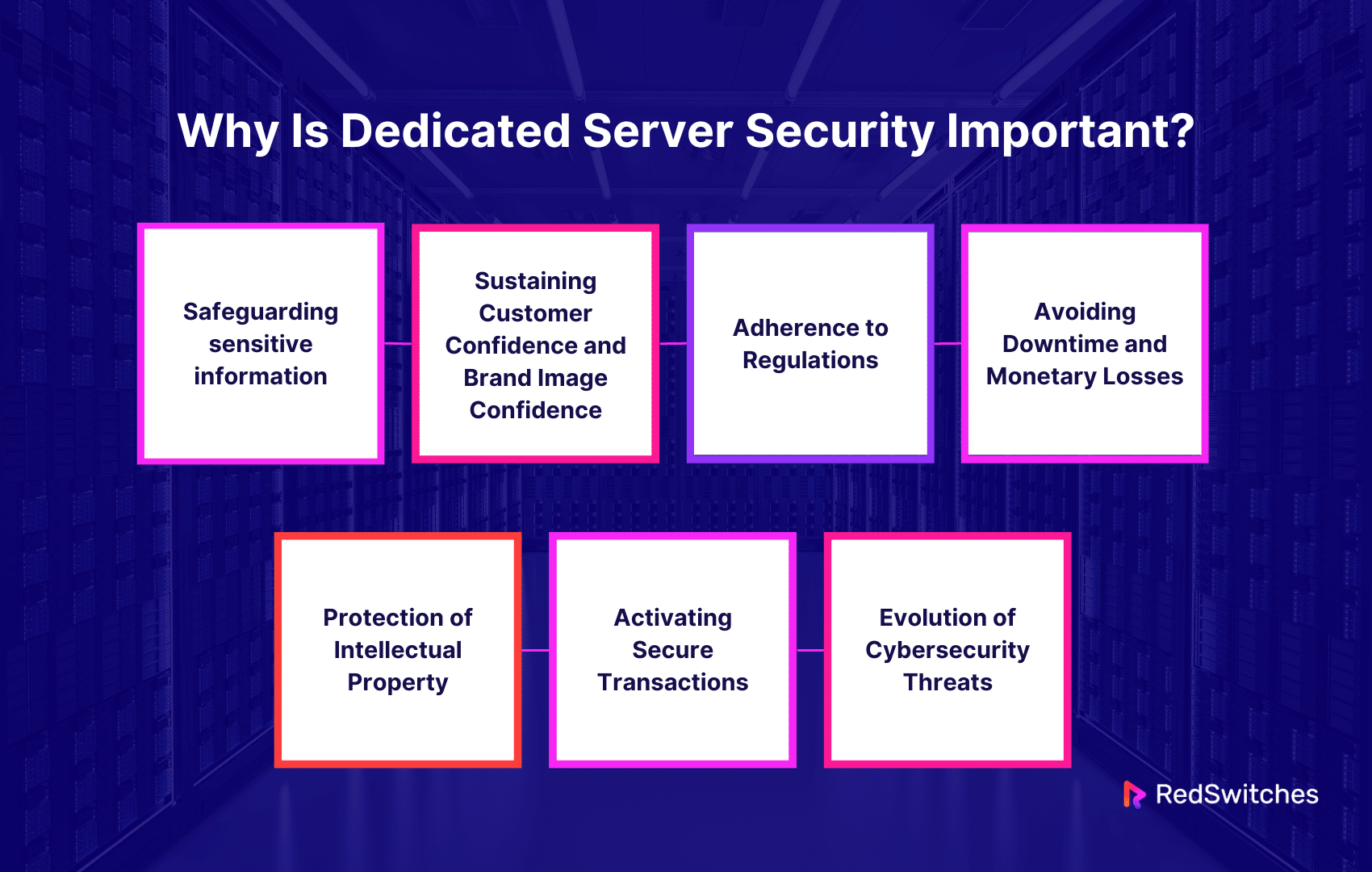
Why Is Server Security Important?
Let’s understand the reasons behind the importance of server Security.
Safeguarding sensitive information
Sensitive data, like financial records and ideas, is often processed and stored on servers. Other private business information is also commonly handled this way. Unauthorized access or a data breach might lead to theft of identities, financial fraud, and loss of competitive advantage. Strong security measures are put in place. They help shield this sensitive data from online threats. They also ensure adherence to data protection laws. And they protect client privacy and corporate operations.
Sustaining Customer Confidence and Brand Image Confidence
It is the foundation of any successful customer relationship. A single security event or data breach can severely harm a company’s brand, erode client confidence, and even result in lost revenue. Consumers anticipate responsible and secure handling of personal data. By valuing client data security, servers keep trust and protect the brand.
Adherence to Regulations
Strict regulations about data security and privacy govern many industries. These regulations include HIPAA in the US, the GDPR in the EU, and similar rules in other countries.
There may be severe fines, legal repercussions, and reputational harm for non-compliance. You must use servers to meet regulations. They protect secrets and prevent legal and financial problems.
Avoiding Downtime and Monetary Losses
Cyberattacks can impair server function. They include ransomware, spyware, and DDoS attacks. They can cause big financial losses and downtime. It can mean missed revenue, lower productivity, and higher recovery costs. This is for companies that rely on online operations, like e-commerce platforms.
Businesses may guarantee the availability and dependability of their services. They can do this while lowering the risk of downtime and the resulting financial losses. They can do this by protecting servers against these risks.
Protection of Intellectual Property
Secure hosting servers are crucial for businesses. They use proprietary technology or data as a competitive edge. This is because IP is vulnerable to theft and espionage. A violation may lead to declining competitive advantage, legal disputes, and large monetary losses. Sufficient security protocols aid in thwarting unwanted entry and guarantee the preservation of intellectual property.
Activating Secure Transactions
Firms that do transactions online, such as e-commerce websites, need secure financial transactions. We need to safeguard servers. This is to stop fraud and ensure the integrity of transaction data. This means using encryption, secure socket layer (SSL) certificates, and other security procedures. They ensure that client financial information is transferred safely.
Evolution of Cybersecurity Threats
The world of cybersecurity is always changing as new methods and weaknesses are discovered and used by attackers. Because servers frequently hold sensitive data, they might be easy targets for these attacks. Sustaining server environments and guarding against new threats requires constant security procedures, such as vulnerability assessments, proactive threat monitoring, and frequent updates.
Also Read Cybersecurity Frameworks: Exploring Security Frameworks, Standards, Risks, & More
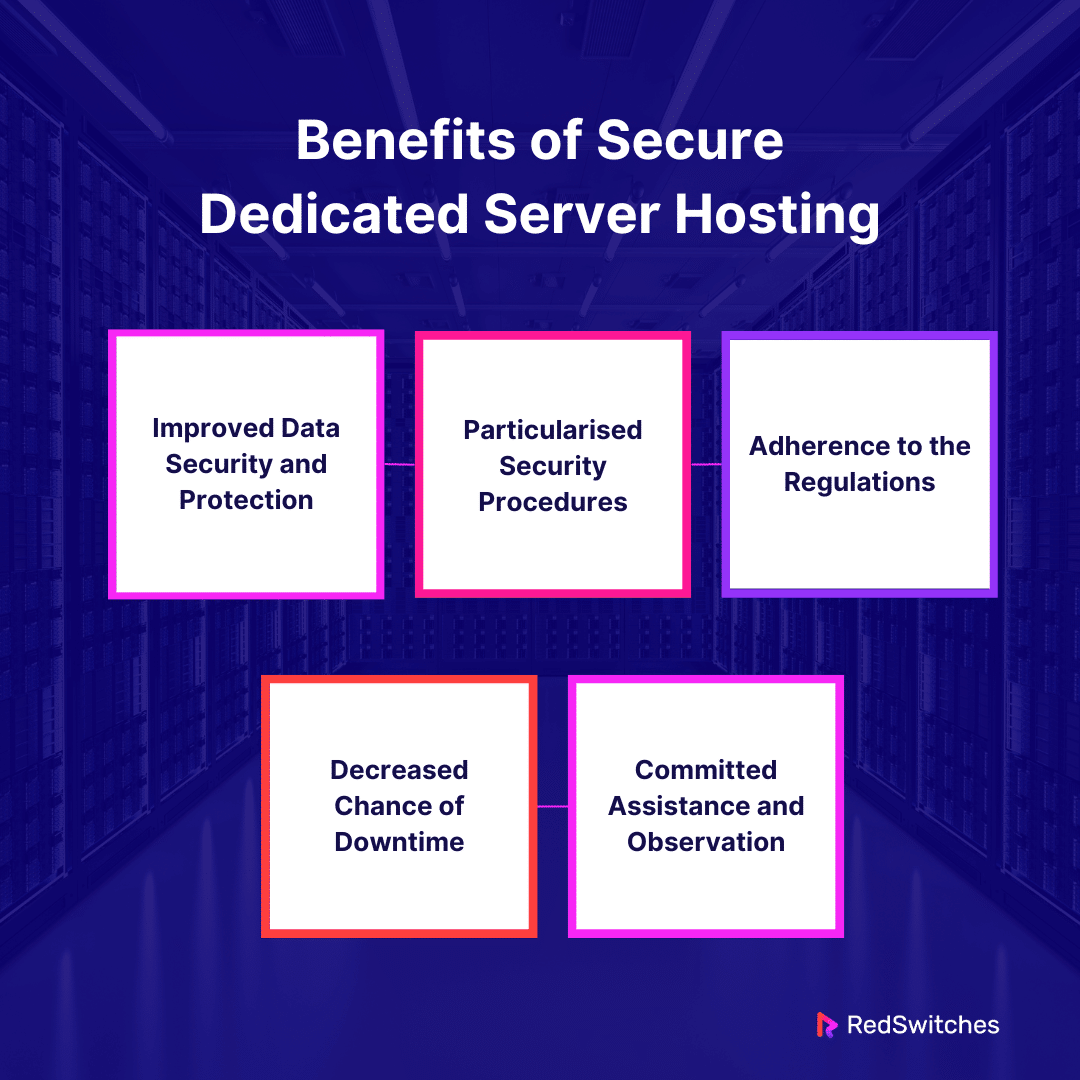
Benefits of Secure Server Hosting
Let’s discuss the benefits of Secure Server Hosting in detail.
Improved Data Security and Protection
The increased level of security that secure server hosting provides is its main advantage. The server has security procedures like firewalls, encryption, and intrusion detection systems. It also has regular security audits. The company can customize these procedures to fit its unique requirements. It can use dedicated resources to do so. Sensitive data, such as bank records, intellectual property, and customer information, is well protected in this dedicated environment. It lowers the risk of data breaches and cyber-attacks.
Particularised Security Procedures
You can customize security settings and measures to meet the organization’s needs. You can do this with secure, dedicated hosting. Servers can implement specific firewall rules, security software, and access restrictions. These comply with the organization’s security policies and compliance needs.
This contrasts with shared hosting. In shared hosting, security settings are generic to fit many users. This level of personalization guarantees that the server’s defense systems are tuned for top security.
Adherence to the Regulations
Strict rules apply to data security and privacy. They are for specific industries. They include GDPR, HIPAA, and PCI DSS. Following these rules is easier with secure server hosting. It offers a controlled environment. Security measures may be strictly implemented and recorded. Showing a commitment to data protection and privacy helps businesses. It helps them avoid fines and other consequences. It also builds confidence with partners and customers.
Decreased Chance of Downtime
Cyberattacks can overwhelm a server. They cause downtime and financial loss, especially for online businesses. These attacks include distributed denial of service (DDoS) attacks. Secure dedicated hosting packages often include DDoS protection and other security measures. They reduce these risks and ensure the server is always accessible and functional, even during an attack. Sustaining consumer happiness and business continuity depends heavily on this dependability.
Committed Assistance and Observation
Hosting providers offer proactive monitoring and better support to keep the server safe. This entails constant watch for bad activities. You must quickly apply security patches. You must also get professional help to fix security problems.
Also Read: Unveiling the Hidden Risks of Dedicated Servers
11 Ways for Optimum Dedicated Server Security
We detail each tactic below to provide a thorough how-to to safeguard your server.
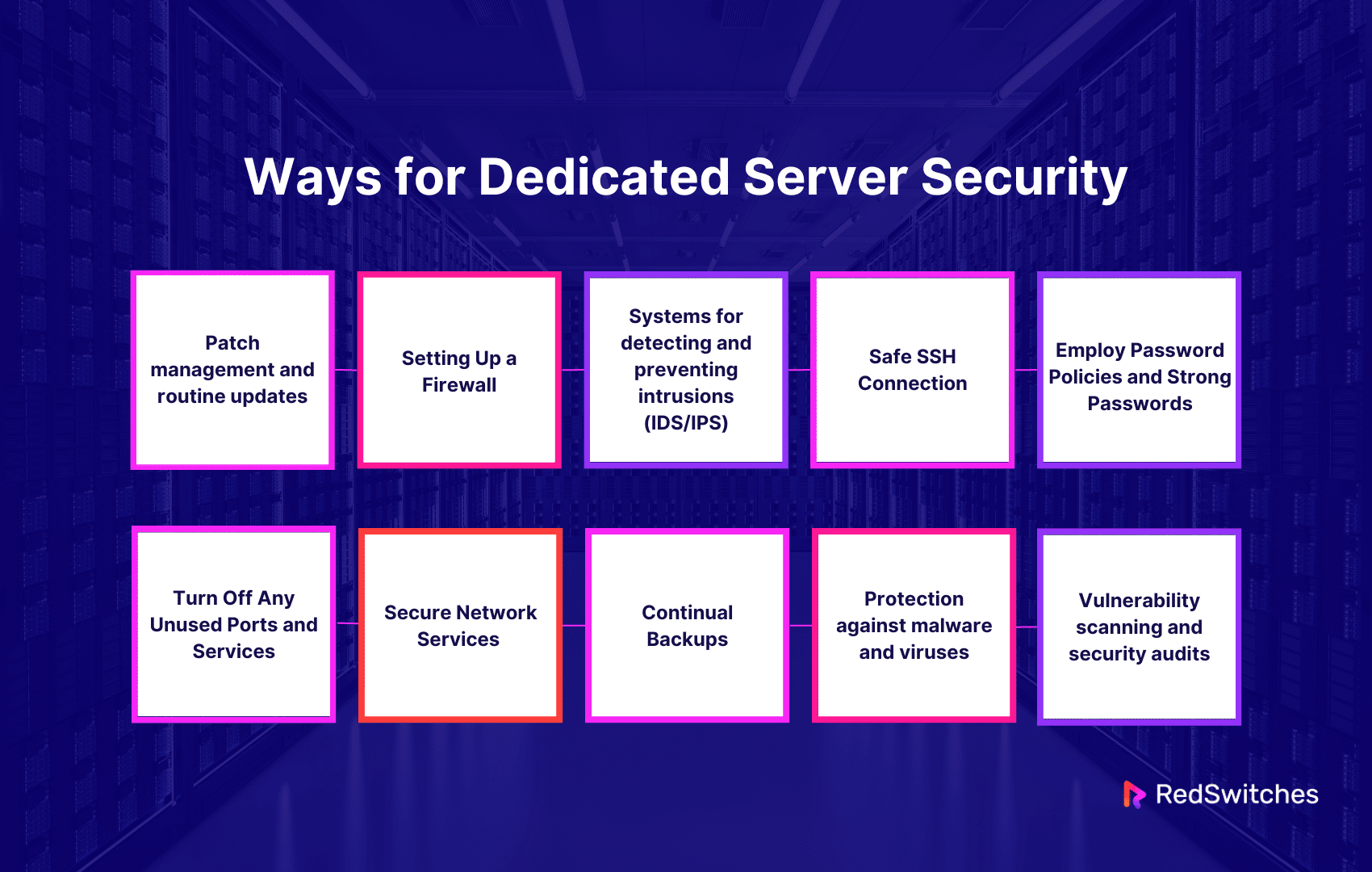
Patch Management and Routine Updates
Keeping the operating system and all installed software on the server up to date is the cornerstone of server security. Cyber attackers often exploit vulnerabilities in unpatched software and operating systems. These are security fixes. They fix flaws and block paths for attackers. The flaws let them access your server without authorization. These fixes are part of routine upgrades. A regular patch management procedure guarantees that all software is updated often. It also ensures that vulnerabilities are fixed fast. To minimize interruption, do three things. Keep an eye out for updates. Evaluate their impact. Carefully organize their deployment.
Setting Up a Firewall
A well-configured firewall is The first defense for protecting a server. A firewall controls inbound and outgoing network traffic. It follows a set of security rules to prevent unwanted server access. The least privilege principle says only needed traffic is allowed. All other traffic is blocked by default. To improve the server’s security, add advanced firewall settings. These settings can include installing intrusion prevention systems (IPS). The IPS actively blocks discovered attacks.
Systems for detecting and preventing intrusions (IDS/IPS)
It keeps an eye out for unusual activity. This might point to a security breach or an ongoing assault. IDS/IPS adds an essential layer of protection. To notify administrators of potential dangers, an intrusion detection system (IDS) examines network and system traffic for odd patterns that could indicate an incursion. An Intrusion Prevention System (IPS) blocks bad traffic or activity. It finds and stops threats. IDS and IPS systems offer a flexible defense system that can respond to emerging threats and protect the server from various online attacks.
Safe SSH Connection
A popular technique for safely gaining remote access to a server is SSH (Secure Shell). A few procedures should be followed to improve SSH security. Key-based authentication—which uses cryptographic keys rather than passwords—should be implemented first to lower the danger of brute-force attacks. Moreover, altering the SSH port by default, usually 22, will assist in avoiding automated attacks that specifically target default installations. Ensuring that only authorized users can attempt to connect further strengthens security by restricting SSH access to particular IP addresses or networks.
Employ Password Policies and Strong Passwords
One of the most important aspects of server security is password strength. Brute-force and dictionary attacks make it simple to exploit weak passwords. It is imperative to establish and enforce a robust password policy. This policy should mandate that passwords be changed regularly and combine capital and lowercase letters, numbers, and special characters. Additionally, using a password manager helps lower the risk of password-related breaches by assisting in creating and safely storing complicated passwords.
Put into Practice 2FA, or Two-Factor Authentication
Because two-factor authentication (2FA) requires more than simply a password, it greatly improves security. A code produced by a mobile app or a message delivered to a mobile device could serve as this second component. 2FA stops unwanted access even if a password is hacked by requiring this extra verification, which is unlikely to be known by the attacker. One of the best practices for protecting sensitive information and services is implementing 2FA for server access and any web apps hosted on the server.
Turn Off Any Unused Ports and Services
Every server service in use and every open port poses a security risk. Turning off ports and services that aren’t necessary for the server to function reduces the attack surface and lessens the likelihood of an exploit. This calls for routinely checking and inspecting the server’s running services and ports and turning off any that aren’t needed. Maintaining the server streamlined in this way can boost performance and security.
Secure Network Services
Encryption should be used to protect network-exposed services like file transfers and web servers. This includes adopting protocols like HTTPS for online services, SMTPS for email services instead of SMTP, and SFTP for file transfers instead of FTP. Sensitive information is protected during transit thanks to encryption, ensuring that data transported to and from the server is safe from interception and eavesdropping.
Continual Backups
It is impossible to emphasize frequent backups’ importance. A speedy recovery is possible with current backups in case of data loss via a cyberattack, human error, or hardware malfunction. Regular snapshots of important data should be part of backup plans, and backups should be kept off-site in a safe location. An extra degree of protection is added when backup data is encrypted, guaranteeing the data is safe even if backup media is stolen or lost.
Protection against malware and viruses
Malware can occasionally infiltrate a server even with the greatest of security measures. Malicious software must be identified, isolated, and eliminated with the help of antivirus and anti-malware software. Selecting trustworthy security software that can defend against the most recent attacks and perform automated upgrades in real time is crucial. It is recommended to arrange for routine, thorough system scans to identify and remove any malware that might have evaded real-time security measures.
Vulnerability scanning and security audits
The server’s security posture may include vulnerabilities, which routine security audits and vulnerability scans should find. These evaluations can reveal obsolete software, incorrect setups, superfluous services, and other security holes that hackers might exploit. Automated scanning can be achieved using tools like Nessus, OpenVAS, or commercial solutions, which offer remedial actionable findings. Frequent audits guarantee that security precautions work and can gradually adjust to new threats.
Five Additional Tips for Dedicated Server Security
Let’s go through the Five Additional Tips for Server Security.
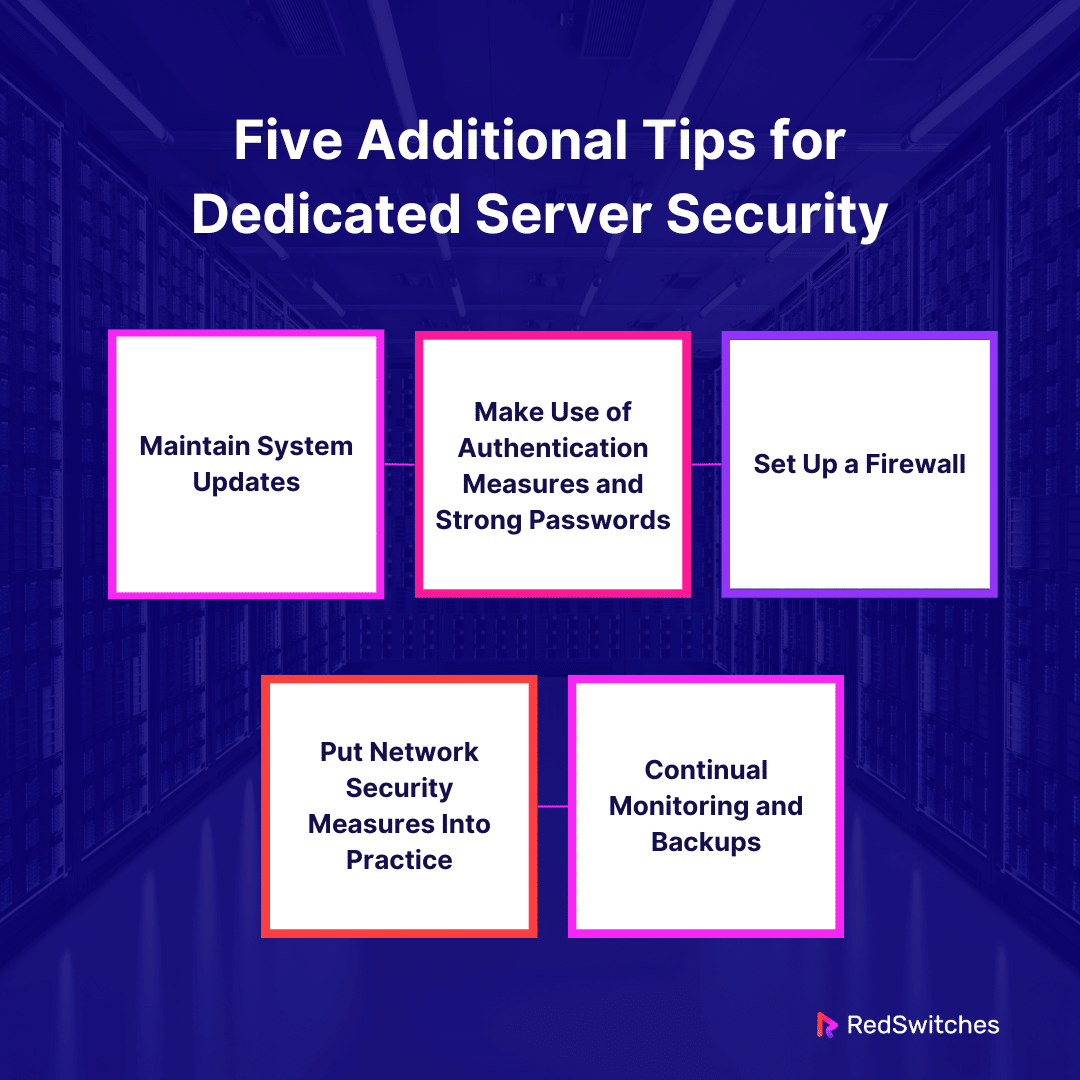
Maintain System Updates
The Reasons for Its Significance Operating systems and software are always changing. Updates are frequently released by developers, fixing security flaws in addition to introducing new features. Known software weaknesses are frequently exploited by hackers, making obsolete systems easy prey.
How to Put It Into Practice
Updates Automatically: Automatic updates are provided by most operating systems. You will receive security patches as soon as they are published if you enable them.
Join the Security Advisories Subscription List: Several software providers provide mailing lists or RSS feeds for security alerts. You can be informed about software vulnerabilities and critical upgrades by subscribing to them.
Frequent evaluations of security: Conduct security assessments regularly to ensure all software is up to date and to look for out-of-date versions.
Make Use of Authentication Measures and Strong Passwords
The Reasons for Its Significance One of the simplest methods for hackers to obtain unauthorized access is using weak passwords. Security is greatly increased with strong, one-of-a-kind passwords and extra authentication techniques.
How to Put It Into Practice
Password Policies: Put regulations mandating secure passwords with a minimum of 12 characters comprising capital and lowercase letters, digits, and symbols in place. Change your passwords frequently, and don’t use the same ones for several accounts.
Multifactor authentication (MFA): MFA requires an additional form of verification in addition to the password, such as a code from an authenticator app or a tangible token, which adds an extra degree of protection.
SSH Keys: SSH keys can offer higher security for servers instead of password authentication for remote access.
Set Up a Firewall
The Reasons for Its Significance Your server’s firewall serves as a gatekeeper, permitting or prohibiting traffic by pre-established regulations. An array of assaults can be efficiently mitigated and unauthorized access prevented with proper settings.
How to Put It Into Practice
First Setup: Identify the services your server requires to function and only open the ports for those services. Ports 80 and 443 are frequently required for web traffic, but other ports should be closed by default.
Ongoing Maintenance: Check firewall rules frequently to ensure they reflect any modifications to your server’s use case. Eliminate any regulations that are no longer required to reduce vulnerabilities.
Put Network Security Measures Into Practice
The Reasons for Its Significance Malicious actors may intercept data while it is in transit. This data is safeguarded by encryption, which guarantees that information that has been intercepted is kept private and unchangeable.
How to Put It Into Practice
SSL/TLS Certificates: Use SSL/TLS certificates to encrypt data while it is transmitted by websites and services that handle sensitive data.
VPN Access: A VPN offers a secure connection to your server remotely. Ensure that your network is protected from unwanted access and that all remote access is conducted via a VPN to encrypt data.
Safe File Transfer: Steer clear of more antiquated, unencrypted protocols like FTP and instead use secure protocols like SCP or SFTP for file transfers.
Continual Monitoring and Backups
The Reasons for Its Significance There is always a chance of data loss or compromise, even with strong security. Frequent backups guarantee that, in the event of a security problem, you can return your server to a known, good state. Early detection of possible security breaches or performance problems is facilitated by monitoring.
How to Put It Into Practice
Backup Strategy: Put a regular backup schedule in place and ensure backups are safely kept, ideally off-site or in a cloud service with backup capabilities. To be sure your backups can be restored, test them from time to time.
Tools for Monitoring: Use monitoring tools to monitor server security and performance. Create alerts to be notified of any odd activity that might point to a security problem, such as traffic spikes or unsuccessful login attempts.
Conclusion
Dedicated hosted servers offer superior security for your data for several key reasons. They allow for customized security settings. Businesses can greatly increase their defenses against cyber threats. They can do this by using techniques. These include firewall setup, strong authentication, system updates, network security, and regular backups with watchful monitoring. However, achieving this level of protection can be difficult and resource-intensive.
Here’s when working with a server provider like us can help. RedSwitches gives organizations peace of mind. They know their digital infrastructure is safeguarded by top security tech and support. We offer reliable server security solutions built with security at their core.
FAQs
Q. What is server security?
The procedures, instruments, and guidelines used to shield data, programs, and services housed on servers against illegal access and online threats are called server security.
Q. What are the different types of security servers?
Firewalls, intrusion prevention systems (IPS), intrusion detection systems (IDS), and antivirus servers are among the various security servers; each has a specific function in network defense.
Q. What is SSH used for?
SSH (Secure Shell) allows encrypted communication between two devices and is used for secure remote login and other secure network services over unprotected networks.
Q. What are the risks of server security?
Server security risks include potential exposure to targeted cyber attacks. They also include ensuring constant, up-to-date protection against evolving threats.
Q. What are the disadvantages of having a security team?
A security team can be costly and requires continuous training to keep up with cybersecurity trends and threats.
Q. What are the disadvantages of security as a service?
SECaaS has downsides. These include data privacy concerns and reliance on the provider’s reliability and effectiveness.
Q. What are the benefits of SECaaS?
SECaaS has many benefits. These include affordable access to advanced security and expertise. They also include less complexity in managing security in-house.
Q. Why is server security important for web hosting?
server security is important for web hosting as it helps protect sensitive data, ensures high uptime and availability, prevents security breaches, and builds trust with clients and customers.
Q. What are the security risks associated with shared hosting?
Security risks associated with shared hosting include sharing server resources with unknown parties, potential for malware infections from neighboring sites, limited control over server settings, and increased vulnerability to DDoS attacks.
Q. How can I ensure the security of my server?
You can ensure the security of your server by regularly updating software, conducting security audits, implementing security best practices, monitoring server activity in real time, and engaging in regular security training for staff members.