Key Takeaways
- The relationship between attack vectors and surfaces is fundamental to understanding cybersecurity threats and defenses.
- Both attack vectors and surfaces are constantly evolving.
- Effective cybersecurity strategies require addressing both attack vectors and surfaces.
- A proactive approach to security involves both technical measures (like secure coding practices and regular updates) and organizational measures (such as user education and strong access controls).
- The effectiveness of an attack often depends on the size and complexity of the attack surface.
- Reducing the attack surface and mitigating attack vectors are complementary strategies.
- Organizations must continuously monitor, update, and educate to protect against evolving cyber threats.
It’s like reading complex code. You need to grasp the interplay between attack vectors and attack surfaces in the complicated dance of cybersecurity. In this dance, digital defenders tango with possible dangers. Imagine it as a strategic game of chess between massive numbers, where each move impacts the destiny of a digital kingdom. This cyber symphony focuses on the mysterious interaction between attack surfaces and vectors. We will uncover the attack surface vs attack vector debate in detail.
Join us as we reveal the secrets of this techno-theater production. We will discover 10 big points of disagreement in the ongoing discussion. This fascinating investigation aims to clarify. It will focus on the dance between attack surfaces and the paths of incursion. It focuses on attack vectors and paths of vulnerability. Here, on the vast platform where cybersecurity meets its digital destiny.
Let’s answer the key point: attack vector vs attack surface.
Table of Contents
- Key Takeaways
- What is an Attack Surface?
- What is an Attack Vector?
- How Do Hackers Exploit Attack Vectors?
- Most Common Attack Vectors
- How to Prevent Attack Vectors?
- Key Differences: Attack Vector vs Attack Surface
- Attack Vector vs Attack Surface: Scope
- Attack Vector vs Attack Surface: Levels of Abstraction
- Attack Vector vs Attack Surface: Concerns
- Attack Vector vs Attack Surface: Dynamic Nature
- Attack Vector vs Attack Surface: Design Considerations
- Attack Vector vs Attack Surface: Metrics and Measurement
- Attack Vector vs Attack Surface: Temporal Aspect
- Attack Vector vs Attack Surface: Dependencies
- Attack Vector vs Attack Surface: Response and Mitigation
- Attack Vector vs Attack Surface: Exploitation Persistence
- How are Attack Vectors and Attack Surfaces Related
- Conclusion
- FAQs
What is an Attack Surface?
Credits: Freepik
These are the totality of weaknesses, routes, or techniques. They are sometimes called attack vectors. Cybercriminals may use them to launch a cyberattack or get illegal access to a network or private information. They make up an organization’s attack surface.
Organizational networks are getting bigger and more complex due to their growing use of cloud services and hybrid work models.
Randori is a subsidiary of IBM Corp. The State of Attack Surface Management 2022 (link lives outside ibm.com) says that 67% of organizations have seen their attack surfaces grow in the last two years. Expanding attack surfaces is the top trend for 2022 security and risk management. This is according to industry analyst Gartner.
Security experts split the attack surface into three sub-surfaces: the digital, physical, and social engineering assault surfaces.
Types of Attack Surface
Credits: Freepik
After defining it, we will explain the three types of Attack Surfaces.
Digital Attack Surface
First, let’s use a real-world example. Think of your home as a company.
Your home has many entry points, including its doors, windows, balconies, second entrance, and garage doors. These make up the attack surface. Should these access points remain unguarded, your home may be open to intrusions like burglaries. You can secure the assault surface by installing alarms, security cameras, grills, and strong locks. They keep intruders out.
Every digital access point in your home, like the Wi-Fi network, cell phones, laptops, and desktop computers, is called the “digital attack surface.” This includes Internet of Things (IoT) devices.” This includes exposed ports.” Hackers might target these digital access points with ransomware, phishing, denial-of-service, malware, and other cyberattacks.
Also read: Top 15 Critical Cyber Security Challenges and How to Fix Them.
Example
One of the biggest misconfiguration vulnerabilities in 2019 was the Atlassian JIRA data disclosure issue. More than 100,000 organizations utilize JIRA project management software.
When users created a filter or dashboard in JIRA, they were assigned the wrong permissions, resulting in misconfiguration. Access was set to “Everyone” (public) and “All users” by default. The user selection function also displayed each user’s email address and username, which was due to misconfigured authorization.
Attackers might have had access to much data. It included staff names, email addresses, and more.
Physical Attack Surface
People call the vulnerabilities and entry points in the visible, physical parts of a system, infrastructure, or facility the physical attack surface. A breach in this surface can have many bad results, including theft, asset tampering, and unauthorized access.
Example
A physical security breach occurred in a data center that housed vital IT infrastructure in an incident that happened in 2021. Intruders could get in without permission. They can avoid access controls and exploit flaws in the surveillance system. The attackers seized many servers and networking equipment. They did this by using social engineering. And took advantage of non-working security cameras.
The hack disrupted service for several businesses and stole their vital services, which were housed on the servers. It showed the link between digital and physical security.
The occurrence showed how vital it is to have strong physical security. It guards against theft, illegal entry, and data breaches. These measures should include surveillance, access controls, and personnel training.
Attack Surface Access Points
The surface access points are all potential entry points for cybercriminals to get into your system and steal your data. The following are a few typical surface access points:
Applications Programming Interfaces, or APIs
Through a clever API, client-side applications—including web and mobile applications—interact directly with the application’s server side. Furthermore, a small gap in the planning, creation, and testing of APIs could allow malicious parties to gain access. Brands must, therefore, provide strong security while setting up and utilizing APIs.
Networks
Every network interface has the potential to be rather open to cyberattacks. These include servers, clouds, VPNs, WiFi, IoT, and remote access. Providing strong authentication security across the board in a network could lessen the dangers involved.
Devices, Users, and Employees
Hackers most frequently target consumers, staff, and their devices to obtain sensitive data from an organization. Cybercriminals constantly seek ways to steal personal information from company devices, including user or employee credentials.
Also read 10 Best VPN for Linux in 2023: Conquering the Digital World
What is an Attack Vector?
Credits: Freepik
An attack vector is a way for a hacker or attacker to enter a computer system or network server and deliver a harmful payload. Attack vectors allow hackers to take advantage of flaws in the system, including human weakness.
Viruses, malware, email attachments, webpages, pop-up windows, instant messaging (IMs), chat rooms, and deceit are common cyber assault vectors. All techniques involve programming or, in some circumstances, hardware, except deceit. Deception occurs when a human operator is tricked into disabling or weakening system defenses.
Firewalls and antivirus programs can restrict attack vectors to a certain extent. However, no defense mechanism is impenetrable to all attacks.
When hackers are always searching for new ways to breach security and change their attack vectors, defense strategies can easily become antiquated.
The most frequent malicious payloads are Trojan horses, worms, malware, and viruses, which can all act as independent attack vectors. Third-party suppliers and service providers are considered potential attack vectors who pose a danger to an organization if they obtain sensitive data.
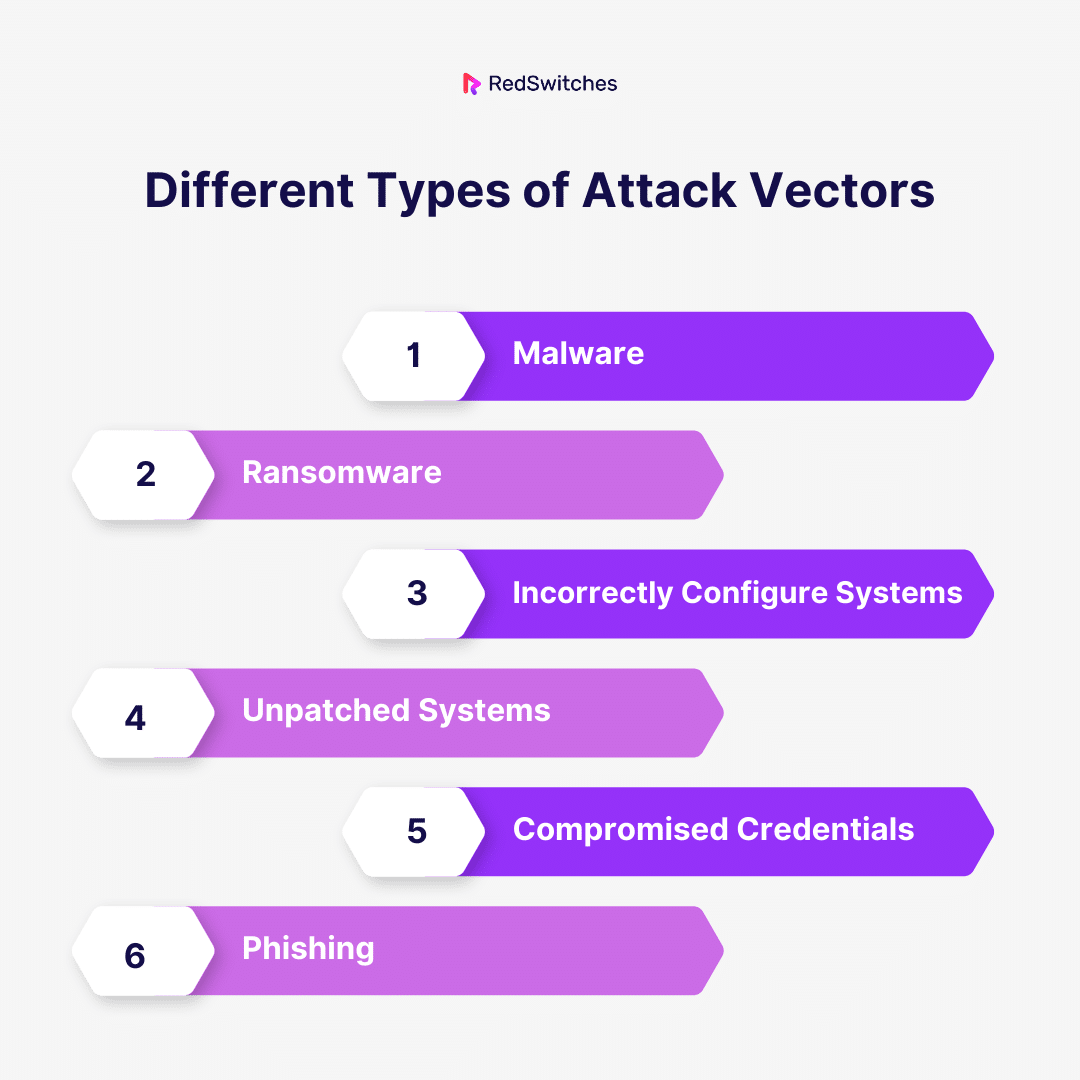
Different Types of Attack Vectors
Now, we will understand the different types of Attack Vectors in detail.
Malware
Malware is a catch-all used to describe any type of software, such as Trojan horses or ransomware, that appears to be a legal file but launches malicious code upon human interaction or download.
Ransomware
Ransomware is malware that encrypts data on a victim’s computer and prevents its owner from accessing it in return for a ransom. Access to the data is restored upon payment receipt.
BitSight research shows flaws and bad security hygiene make ransomware assaults more likely. Visit our blog to learn more about the report’s conclusions and how to lessen your chances of becoming the next ransomware victim.
Incorrectly Configured Systems
Misconfigured systems contribute to data breaches and loss, especially in the cloud. For instance, a poorly designed web application firewall caused a significant Capital One data leak.
Additionally, there is a direct link between ransomware assaults and improperly setup systems. For example, a BitSight investigation discovered that the likelihood of ransomware attacks is almost four times higher for organizations with TLS/SSL setups rated C or lower.
Unpatched Systems
Every day, new vulnerabilities appear that hackers can easily exploit if you don’t watch for unpatched systems or apply a patch quickly enough. BitSight researchers discovered that ransomware attacks were more than seven times more likely to occur in organizations with a patching cadence of D or F events than those with an A grade.
Also read Difference Between SSL vs TLS: 2024’s Best Internet Security Protocol
Compromised Credentials
On the dark web, compromised usernames and passwords are frequently found and can provide hackers unheard-of access to your network. To ensure that you can respond promptly, think about investing in systems that search for compromised credentials due to breaches that are made public.
Phishing
Phishing is a type of social engineering in which an evil actor poses as a trustworthy individual or organization, usually through email. It requests that the target take a step to grant the phisher access to sensitive information or systems.
Attack Vector Access Points
There are countless attack vector access points; the list is limitless. The following are a few of the most typical attack vectors:
Attacks by Phishing
Phishing attacks are deliberate assaults wherein fraudsters obtain credentials and other crucial data through social engineering techniques. By guaranteeing that your staff members and users receive regular cybersecurity hygiene training, you can reduce the impact of these assaults.
Stuffing Credentials
The automatic insertion of pre-compromised passwords and usernames in pairs is known as “credential stuffing,” because it allows users to access accounts. Attackers get access to accounts with compromised passwords by employing the hit-and-trial technique.
Brute-Force Attacks
Fraudsters will use compromised credentials from users or employees to access the company network. Each year, brute force attacks result in losses of millions of dollars.
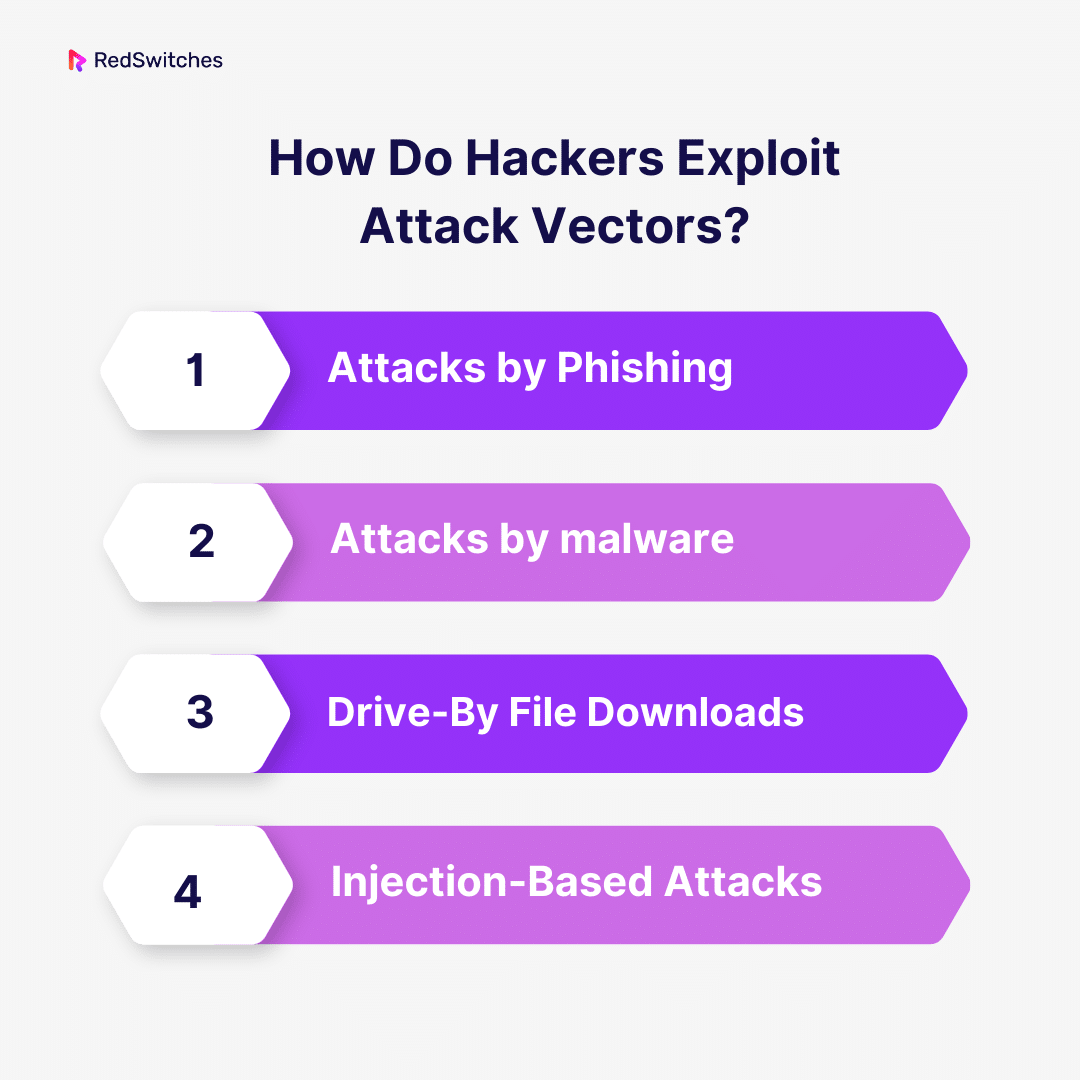
How Do Hackers Exploit Attack Vectors?
Hackers use various techniques to infiltrate systems and obtain unauthorized access using attack vectors. This is a synopsis of how they make use of typical attack vectors:
Attacks by Phishing
Technique: Send false emails or messages from reputable companies to fool recipients into opening dangerous links, downloading malicious files, or divulging personal information.
Attacks by Malware
Technique: Spread harmful software via compromised websites, email attachments, or removable media (viruses, trojans, ransomware). Take advantage of weaknesses to take over systems.
Drive-By File Downloads
Technique: Take advantage of holes in plugins or web browser security on hacked websites. Users unintentionally download and install malware by going to the compromised website.
Injection-Based Attacks
Technique: Insert malicious code into databases or input fields using SQL injection. Take advantage of software flaws to alter or compromise data.
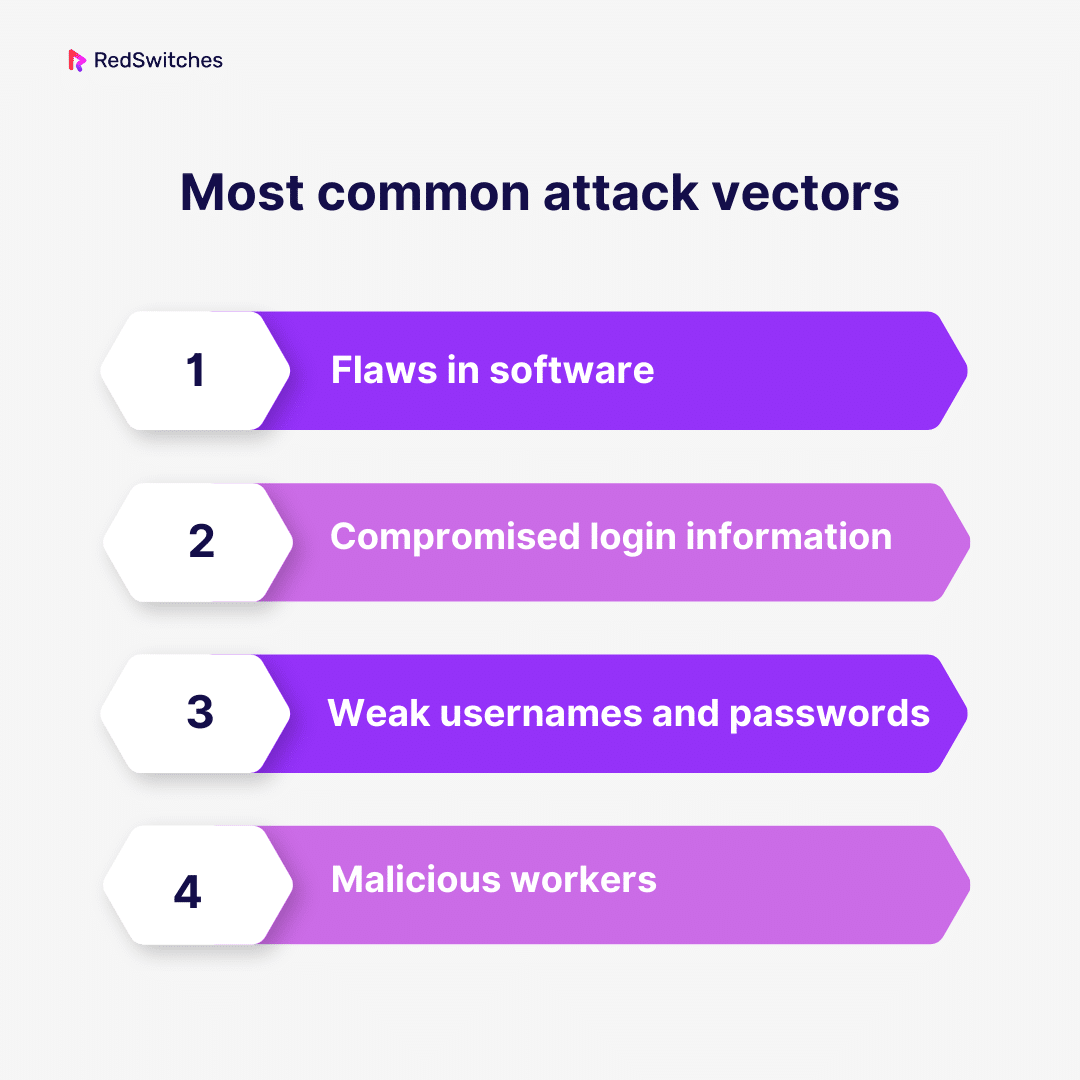
Most Common Attack Vectors
Before moving to our ultimate attack vector vs attack surface debate, we will explore this section’s most common attack vectors. Hackers are always looking for new ways to get access. These are some of the most typical assault vectors:
Flaws in Software
Unpatched security vulnerabilities in a network, operating system, computer system, or application might allow an attacker to access it without authorization through threat vectors like malware.
Compromised Login Information
Users may accidentally or purposefully share passwords and user IDs. This can be accomplished verbally, but hackers can also obtain credentials by using a brute-force assault, which involves trying various user ID and password combinations until a set of authorized credentials is discovered. The hacker then gains access to a network, system, or application using these credentials.
Weak Usernames and Passwords
Brute-force assaults concentrate an attacker’s efforts on breaking into user IDs and passwords that are simple to guess or are weak. However, hackers can also obtain credentials by employing software designed to track when users enter their access credentials on public Wi-Fi networks.
Malicious Workers
With their security clearances, malicious or dissatisfied personnel can hack into networks and systems to obtain sensitive data, including customer lists and intellectual property (IP), which they can sell to third parties for illicit purposes or demand ransom.
Inadequate or absent encryption: Sometimes, workers—or IT—forget to encrypt private data on laptops and mobile devices when in the field. In other situations, encryption methods only use a small number of keys to encrypt and safeguard data, or they have recognized design problems.
Also read Types of Database Encryption: Best Practices for Securing Your Data
How to Prevent Attack Vectors?
Credits: Freepik
Before moving towards the core topic of our blog, attack vector vs attack surface, let us understand three ways to prevent attack vectors.
Awareness and Education of Users
Provide users with frequent cybersecurity training and education, stressing the value of identifying phishing efforts, adopting safe browsing practices, and exercising caution when opening emails and messages.
Patching and Updating for Security
To mitigate the risk of exploitation through known vulnerabilities, promptly deploy software updates and security patches to fix operating systems, programs, and plugin vulnerabilities.
Multiple Layers of Security
Implement a multi-layered security approach that includes firewalls, antivirus software, intrusion detection/prevention systems, and safe network configurations to offer thorough defense against a range of attack vectors.
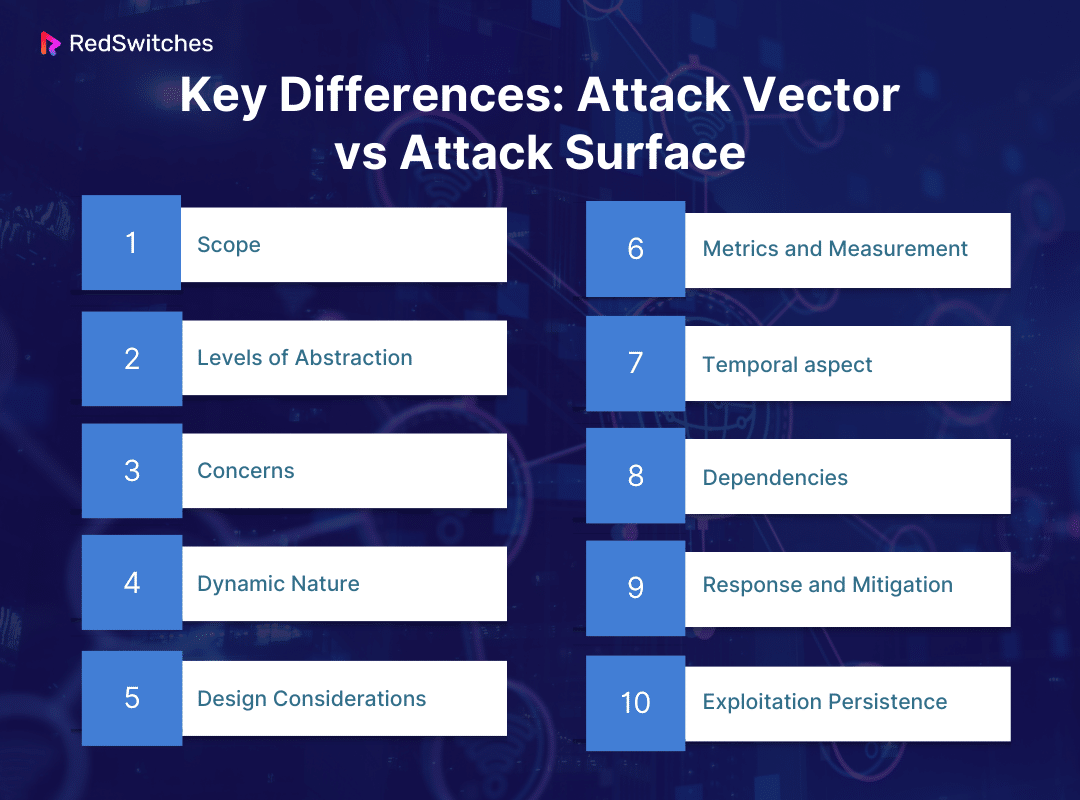
Key Differences: Attack Vector vs Attack Surface
In this core section of our blog article, we will understand the key differences in the attack vector vs attack surface debate. Let’s have a look.
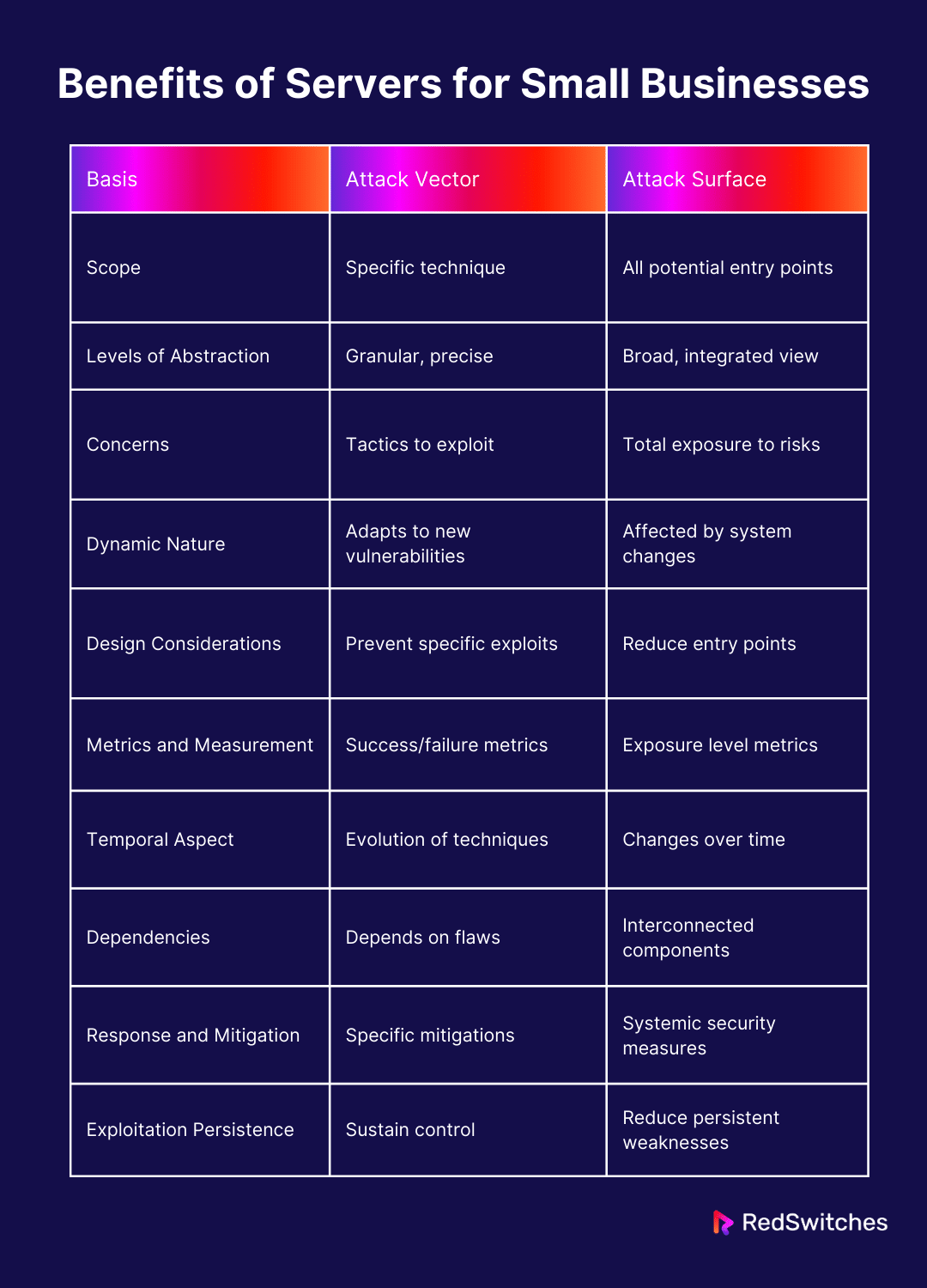
Attack Vector vs Attack Surface: Scope
The first differential parameter in our attack vector vs attack surface debate is scope.
Attack Vector
The precise route or technique an attacker uses to take advantage of weaknesses and breach a system, network, or application is referred to as the attack vector. It is the exact method used to carry out an attack or intrusion. Attack vectors might include injection attacks, phishing emails, malware distribution, and physical breaches.
Attack Surface
In contrast, the attack surface is a broader concept encompassing all potential entry points, vulnerabilities, and interactions between a system and its external environment. It represents the sum of all possible avenues through which an attacker could gain unauthorized access. The attack surface includes network interfaces, software interfaces, user accounts, physical access points, and other elements that expose the system to potential threats.
Attack Vector vs Attack Surface: Levels of Abstraction
Another essential aspect of the attack vector vs attack surface argument is their respective levels of abstraction.
Attack Vector
Within the context of cybersecurity, the attack vector functions at a more precise and granular level of abstraction. It represents an attacker’s precise strategies, methods, or tactics for finding weaknesses and breaching a particular target. Highly specialized attack vectors include code injection strategies, social engineering tactics, and particular software vulnerabilities.
Comprehending the attack vector is a narrow and specialized area of cybersecurity study since it entails exploring the attack’s particular technological or procedural aspects.
Attack Surface
The attack surface, on the other hand, functions at a higher level of abstraction and offers a more thorough and integrated perspective of a system, network, or application’s overall security posture. It includes every interaction and entrance point that an attacker could target, including network interfaces, user accounts, physical access points, and other elements.
Attack Vector vs Attack Surface: Concerns
Now let’s discuss the concerns associated with both concerning the debate: Attack vector vs attack surface.
Attack Vector
The main issue regarding attack vectors is the strategies and tactics adversaries use to exploit weaknesses and jeopardize a system’s or network’s security. Security experts concentrate on comprehending and minimizing these distinct assault pathways to avert unapproved entry, compromised data, or interruptions in service.
Attack Surface
The attack surface concerns are more comprehensive, encompassing a system or network’s total exposure to security risks. Since attackers have more access points and potential weaknesses to take advantage of, a bigger attack surface raises the likelihood of successful attacks.
Also read Web Application Security 101: What It Is, How It Works, Best Practices, & More
Attack Vector vs Attack Surface: Dynamic Nature
Now let’s compare the dynamic nature concerning the Attack Vector vs Attack Surface.
Attack Vector
Attack vectors are dynamic because malevolent actors are always changing and adapting them. They adapt to new vulnerabilities, security updates, and technological developments. Cybercriminals are constantly developing new ways to exploit vulnerabilities, while security professionals are working to develop countermeasures to target particular attack vectors.
Attack Surface
The attack surface is also dynamic, considering modifications to a system’s functions, architecture, and external interactions. It grows as companies implement new software, services, or technology. Modifications to user behavior, network setups, or business procedures can also impact the attack surface.
Handling the attack surface’s dynamic nature calls for ongoing observation, risk analysis, and security strategy adaptation to account for changes in the digital landscape.
Attack Vector vs Attack Surface: Design Considerations
Now we’ll explore the design considerations concerning the Attack Vector vs Attack Surface.
Attack Vector
Addressing attack vectors in design considerations aims to create and manage secure systems that can withstand particular forms of exploitation. Anticipating possible attack vectors during development and implementing preventative or mitigating measures are key to security-by-design concepts.
Developers and architects must consider input validation, secure coding techniques, encryption, and the least privilege principle to reduce the attack surface and fortify defenses against certain attack vectors.
Attack Surface
Systems’ architecture and structure must be shaped with the attack surface in mind to reduce potential points of entry and vulnerability. Network designs, service exposure, and user access controls require careful consideration by security experts and architects.
Reducing the attack surface entails segmenting the network, removing pointless services, and using appropriate authentication and permission procedures.
Attack Vector vs Attack Surface: Metrics and Measurement
How do Metrics and Measurements differ for both? Let’s understand this concerning the attack vector vs attack surface debate.
Attack Vector
Specific metrics about the success or failure of an attempted exploit are frequently used to measure and assess attack vectors. Metrics can include the number of successful attacks, the time it takes an attacker to penetrate a system, or how well security measures block particular attack pathways.
Furthermore, monitoring the frequency and seriousness of vulnerabilities found and the exploits linked to them provides insights into how the threat landscape is changing.
Attack Surface
Attack surface metrics measure and assess a system’s or network’s total exposure. Standard metrics include the quantity of active services, the complexity of the network architecture, and the number of open ports. By tracking changes in the attack surface over time, security experts can evaluate the effect of system upgrades or adjustments on security.
Attack Vector vs Attack Surface: Temporal Aspect
Credits: Freepik
Let’s check out the temporal aspect regarding the difference between attack vectors and attack surfaces.
Attack Vector
The temporal component of attack vectors considers the emergence and timing of particular attack techniques. Attack vectors may change as new vulnerabilities are found, exploits get more sophisticated, and attackers modify their strategies. An attack vector’s effectiveness may vary over time due to security patch releases, developments in cybersecurity technologies, or changes in the tactics used by attackers.
Attack Surface
Changes in a system’s total exposure over time constitute the temporal aspect of the attack surface. The attack surface is dynamic and subject to alter in response to software upgrades, system configuration changes, and user behavior shifts. In addition, network design changes and the introduction of new services and technology are included in the category of temporal considerations.
Attack Vector vs Attack Surface: Dependencies
Now, we will compare both dependencies in our attack vector vs attack surface argument.
Attack Vector
Attack vectors frequently rely on certain flaws, deficiencies, or incorrect setups in a system or network. These requirements are necessary for an attack vector to succeed. For example, a malware assault might exploit software flaws, but a phishing attack might rely on consumers’ vulnerability to social engineering.
Attack Surface
The interdependencies between various services and components inside a system or network impact the attack surface. Interconnections between software modules, communication routes, and shared resources are examples of dependencies. Several dependencies frequently lead to an expansive attack surface, and minimizing it necessitates skillfully managing these interdependencies.
Attack Vector vs Attack Surface: Response and Mitigation
Concerning attack vector vs attack surface, it’s essential to understand how each aspect contributes to the overall security posture of a system.
Attack Vector
Attack vectors must be addressed using mitigations and responses unique to attackers’ techniques. Organizations employ specific security measures in response to recognized attack vectors. To detect and neutralize malware, for instance, organizations may use behavioral analysis tools, antivirus software, and routine system scans if a particular malware attack vector is detected.
Common mitigation measures against different attack vectors include patching security holes on time, updating security setups, and educating users.
Attack Surface
Broader and systemic security measures must be implemented to mitigate the attack surface, lessening exposure to potential threats. This can entail segmenting the network, cutting back on pointless services, and limiting access using the least privilege concept.
Regular security audits and vulnerability assessments help find and fix possible vulnerabilities over the attack surface.
Attack Vector vs Attack Surface: Exploitation Persistence
Understanding the interplay between attack vectors and surfaces is crucial in determining the persistence of exploitation in cybersecurity.
Attack Vector
The ability of an attacker to sustain unauthorized access or control over a system or network for a prolonged amount of time is referred to as the exploitation persistence associated with an attack vector. Specific attack paths enable adversaries to get enduring access, guaranteeing uninterrupted authority long following the original breach. For example, if a malware attack vector is successful, it may install a backdoor, giving the attacker permanent access.
Attack Surface
Exploitation persistence refers to the long-lasting weaknesses and possible entry sites in the context of the attack surface. Attackers are more likely to find opportunities for persistent exploitation when the attack surface is large and complicated. The goal of reducing the attack surface is to minimize recurring weaknesses and points of entry.
Organizations can reduce the risk of persistent exploitation by implementing a least-privilege strategy, regularly updating software, and conducting extensive security evaluations.
Let’s summarize it in a tabular format
How are Attack Vectors and Attack Surfaces Related
After learning the attack vector vs attack surface debate, we will understand how both are interrelated.
Within the cybersecurity ecosystem, attack surfaces and attack vectors are interdependent components. Attack vectors are the exact techniques attackers use to take advantage of weaknesses and breach systems. These attack vectors frequently focus on gaps in the larger attack surface, a system’s total exposure to possible dangers.
Reducing the attack surface is a proactive tactic to reduce possible entry points. Mitigating attack vectors entails identifying and closing particular vulnerabilities. To fully defend against cyber threats, security should address both sides. It should focus on short-term risks, called attack vectors. It should also cover long-term resilience, which means reducing the attack surface.
Security should address both sides of the equation to defend against cyber threats. It should focus on short-term risks, which are attack vectors, and cover long-term resilience, which is attack surface reduction. A good strategy helps organizations defend their systems. It protects them from many threats over time and helps them respond to known attacks.
Conclusion
To sum up, our investigation into attack surfaces and routes has given us a thorough grasp of these crucial elements in cybersecurity. We defined both terms. We analyzed the 10 main distinctions in the attack vector vs attack surface debate. This has prepared us to handle the complex world of cyber threats. The more we work to strengthen our defenses. It’s clear that shrinking the attack surface and minimizing certain attack paths go together.
RedSwitches can be an invaluable friend for organizations striving for cybersecurity excellence.
We are a key collaborator in our joint effort to protect digital assets because we are dedicated to strong security solutions.
Our cutting-edge expertise and the understanding from this discussion open the door to a proactive defense strategy. It will help defend against ever-changing cyber threats.
FAQs
Q. How does an attack surface differ from an attack vector?
An attack surface has all potential entry points and vulnerabilities in a system. An attack vector is a specific path that attackers use to exploit those vulnerabilities.
Q. Threat vector vs attack surface: Why is an attack surface necessary?
An attack surface is necessary for system functionality. It represents the exposure of components to external interactions. However, managing and reducing the attack surface is crucial to mitigate security risks.
Q. What is a modern attack surface?
A modern attack surface includes digital assets such as cloud services, APIs, and mobile applications, reflecting the expanded scope of potential vulnerabilities in contemporary IT environments.
Q. What is used to reduce attack surfaces?
Organizations use security measures, audits, and best practices, often in a FAQ (Frequently Asked Questions) format. They cut unnecessary services, secure configurations, and reduce entry points.
Q. What is the difference between an attack vector and an attack surface?
An attack vector is a path by which an attacker gains access to a target system or network. An attack surface is the sum of all potential entry points where an unauthorized user can try to enter or take data.
Q. How do attackers exploit attack vectors?
Attackers exploit attack vectors. They find vulnerabilities in a system or network and use specific methods or tools to gain unauthorized access or compromise security.
Q. What are the different types of attack surfaces?
There are two kinds of attack surfaces. Digital ones relate to online systems and networks. Physical ones relate to infrastructure and devices. These surfaces encompass all points that are susceptible to attacks.
Q. What are common types of attack vectors?
Common attack vectors include social engineering, cyber-attacks, passive, and active attacks. Attackers use these vectors to exploit vulnerabilities and gain access to sensitive information.
Q. How is an attack surface different from an attack vector?
An attack surface refers to the potential vulnerabilities in a system or network that attackers can exploit. In contrast, an attack vector is a specific path or method attackers use to exploit those vulnerabilities.
Q. What is the difference between a targeted attack and a general attack?
A targeted attack is focused on a specific individual, organization, or system with detailed planning and customization. In contrast, a general attack is broader and aimed at exploiting common vulnerabilities without specific targeting.
Q. What security controls can be implemented to mitigate attack vectors and protect the attack surface?
Security controls such as firewalls, intrusion detection systems, encryption, access controls, and regular security audits can help reduce the risks associated with attack vectors and strengthen the security of the attack surface.