Key Takeaways
- Being aware of the idea and procedure behind rooting.
- Understanding the importance of root access for control and customization for server owners.
- Recognizing the differences between dedicated servers and the significance of root access in this particular situation.
- Root access for server owners has benefits and disadvantages, such as greater flexibility and accountability.
- Techniques for getting root access and the things that owners of servers can do with it.
- There are several applications for root access, including installing software and configuring security.
- Things to think about before changing the root password and knowing if rooting is safe and lawful.
Gaining root access to a server is like having a digital master key. It opens up many opportunities and duties in the world of server ownership. Consider it as having access to the behind-the-scenes knowledge of the complex orchestration of servers. Owners with root access, the key to the server kingdom, can shape, hone, and exert control over their digital landscapes.
We will look into the dual sides of this powerful tool. We will do this as we begin our journey, exploring its possibilities and the careful practices needed to avoid dangers.
Come along as we explore the good and bad of root access for server owners. We will learn about the responsibility of holding server power and its advantages.
Table Of Contents
- Key Takeaways
- What is Rooting?
- What is Root Access?
- Why Root Access is Important for Server Owners?
- What Is a Dedicated Server?
- What Is Dedicated Server Root Access?
- Pros of Root Access for Server Owners
- Cons of root access for Server owners
- How Do Server Owners Get Root Access?
- What Can Server Owners Do With Root Access To Their Servers?
- Root Access For Server Owners: Use Cases
- How To Reset Your Root Password?
- Is Rooting Legal and Safe?
- Conclusion
- FAQs
What is Rooting?
Getting root access or administrative privileges on a device or system is sometimes called “rooting.” Rooting applies to mobile devices, like tablets or smartphones. It means removing operating system limits imposed by the cellular carrier or device maker. This opens up normally restricted system files and settings for people to access and edit.
Getting root access means having superuser or administrator access. It’s called “rooting” with servers or computer systems.
Credits: Freepik
Users with root access have the most authority. They have the most permissions, which let them alter system configurations and essential files. Rooting is sometimes used to install custom software. It carries out complex setups and other mods that are impossible with standard user permissions.
What is Root Access?
Credits: Freepik
Root access denotes the highest administrative privileges on a computer system or server. The superuser or admin is called “root” in Unix-like operating systems. Examples are Linux and Android. With root rights, a user can install and remove programs. They can also change settings that regular users can’t and edit system files, giving them full power over the operating system.
Although root access offers unmatched flexibility and control, it carries a heavy responsibility. Errors or unauthorized modifications with root access rights may create unstable systems. They can also cause security flaws. Because of this, users are usually encouraged to use caution. They should limit their use of root access to tasks that require elevated privileges.
But, root access has a major drawback: the chance of unforeseen repercussions. Mistakes and unauthorized changes with root access might make systems unstable. They might also cause security flaws.
Because of these hazards, root users must be prudent. They should only use these rights for specialized tasks requiring advanced admin powers.
The key to good system management is balancing root access’s benefits with the need for stability.
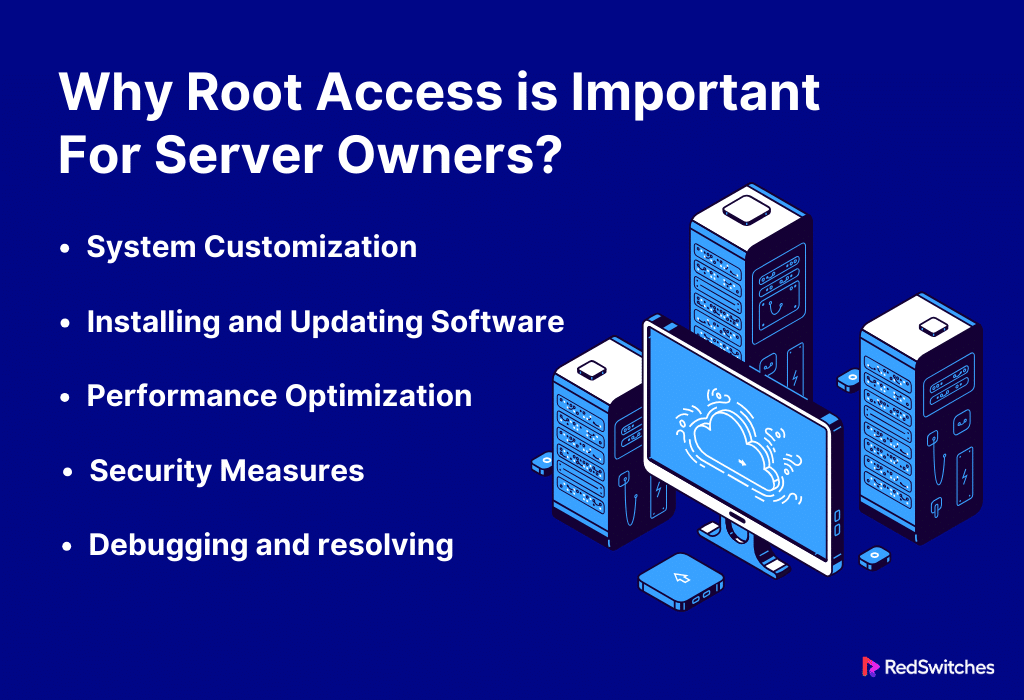
Why Root Access is Important for Server Owners?
Server owners need root access. It is crucial for several reasons. It gives them unmatched control and flexibility over their servers. For server owners, root access is essential for the following main reasons:
System Customization
With root access, server owners can set up and modify the system to meet their own needs. This means setting performance parameters and installing software. They must also optimize the software and customize the server to fit the needs of their applications.
Installing and Updating Software
Owners of servers with root access can install, update, and administer system-level software. This is needed to keep the server up to date. It needs the newest compatibility fixes, security patches, and new features.
Performance Optimization
Server owners with root rights can enhance the server’s performance. They can modify system settings, resource allocation, and other options. This is essential to guaranteeing effective and quick server operations.
Security Measures
Server owners can apply and enforce system-wide security measures if they have root access. To improve security, this means putting up firewalls. It also means controlling user permissions and watching system logs.
Debugging and Resolving
Root access is essential for debugging and resolving server problems. Owners of servers can check system logs. They can review error warnings and make needed fixes to solve problems quickly.
What Is a Dedicated Server?
Credits: Freepik
A dedicated server is a hosting service in which a single client or organization exclusively uses an entire physical server. A dedicated server gives the client total control and exclusive access to the server’s resources. Shared hosting, in contrast, divides a single server’s resources among many users.
These are businesses and groups with specific hosting needs. They include big e-commerce websites. They also include apps that use a lot of resources. This includes gaming servers. It also includes apps that value security and compliance. They often use dedicated servers.
Dedicated servers have more exclusive resources than shared hosting or VPS options. They are more expensive, even if they have several advantages.
Also read How To Pick the Right Dedicated Server Specs [Ultimate Guide]
What Is Dedicated Server Root Access?
Credits: Freepik
The user gets administrative rights on a dedicated server. These are often called the “root user” or “superuser.” They are known as dedicated server root access. Regarding Unix-like operating systems (like Linux), “root” refers to the highest degree of system access and control. With root access, the user has full control over operations and can modify the operating system and configuration of the server.
Having root access on a dedicated server has many benefits. It offers flexibility and control. But it’s essential to use these rights carefully. Wrong setups or unauthorized changes with root access may make systems unstable. They may also create security holes. Server administrators with root access should follow best practices. They should be careful and add security measures. This is to ensure the dedicated server runs well and stays secure.
Key features of root access on a server consist of:
Administrative Privileges: The root user has the most administrative privileges on the dedicated server. This includes doing things that standard user accounts are not allowed to do. For example, installing and uninstalling software, changing system files, and setting system settings.
Total System Control: The user has total authority over all aspects of the server when they have root access. This control covers critical system files. It also covers user account management, network setups, and other essential OS parts.
Customization and Configuration: With root access, users can set up the server environment to meet their unique needs. Installing software, adjusting security settings, and optimizing performance parameters are a few examples.
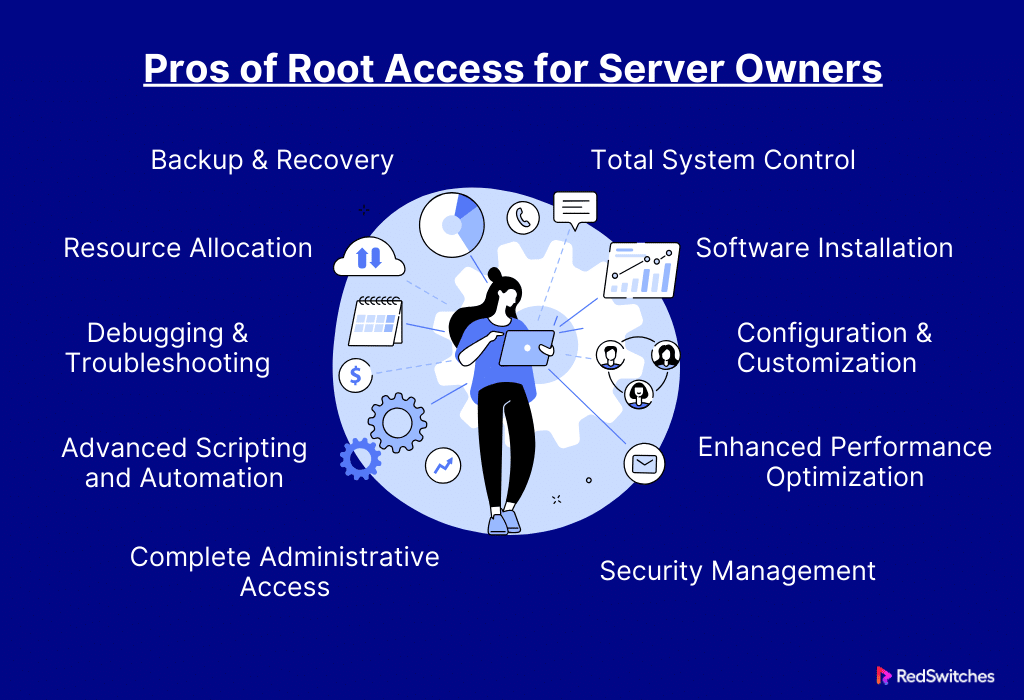
Pros of Root Access for Server Owners
Root access is a potent tool. It gives server owners higher administrative privileges. It gives them unmatched control and customization capabilities over their servers.
This in-depth analysis explores the many benefits of root access. It lets server owners customize their environments to meet their needs better and improve efficiency.
Total System Control
Owners of servers with root access have total authority over the server environment. Thanks to their degree of authority, they can make choices and changes at the most fundamental levels of the server’s operating system. Owners of servers can make detailed changes. Ordinary users can’t do this. These changes let owners set the server to fit their needs.
Software Installation
Owners of servers with root access can install, update, and uninstall software at the system level. This benefit is great for server owners. They need it to meet the demands of their operations. They need it for their specialized software stacks, apps, or updates. Thanks to root access, these changes can be made without the usual limitations of regular user accounts.
Also read Cracking the Server Code: Understanding Server Machines
Configuration and Customization
Root access allows server owners to customize their systems deeply. They do this by exploring the details of system configurations. With this feature, owners can customize the server. So They can meet the specific needs of their services and applications. The server evolves into a precise tool for peak performance. It goes beyond being a generic platform.
Enhanced Performance Optimization
With root access, server owners can modify resource allocations and fine-tune performance metrics. This control is essential. It ensures the server is as responsive and effective as possible. Owners can handle the special needs of resource-intensive websites or applications. They can do this by granting root access.
Security Management
It enables server owners to apply security measures. They can also oversee them at the system level. Root access is essential for this. This includes establishing access limits, creating firewalls, and monitoring system logs. Fine-tuning security settings improves the server’s security. It offers a strong defense against future threats.
Debugging and Troubleshooting
Root access dramatically increases the efficiency of debugging and troubleshooting. Server owners can view detailed logs. They can also investigate system-level problems. And they can fix issues fast. This feature makes finding and fixing server problems easier. It also minimizes downtime and guarantees a seamless environment.
Backup and Recovery
Root access makes additional backup and recovery plans easier. Owners of servers can put in place complete backups. They guarantee the safety of important data. They enable quick recovery in case of data loss or system problems. The server’s overall data management plan is further protected by the capability to execute full system backups.
Resource Allocation
Exact control over the distribution of resources, such as CPU, memory, and disc space, is provided by root access. This feature is vital. It maximizes the use of available resources and avoids bottlenecks. It guarantees good server performance. Root access offers flexibility. It lets you modify needs in changing contexts. These contexts may have different resource requirements.
Advanced Scripting and Automation
Advanced scripting and automation features are built-in to root access. Owners of servers can write complex scripts. These scripts automate repeat tasks, cutting labor costs and improving operations. Modern server management relies heavily on automation. Root access lets you use complex automation plans.
Complete Administrative Access
Owners of servers have full administrative access. They control user administration and system monitoring. This involves watching user activity. It also involves giving different access levels. And it involves adding, removing, or changing user accounts. Root access allows complete server control. Owners can manage every part of their server.
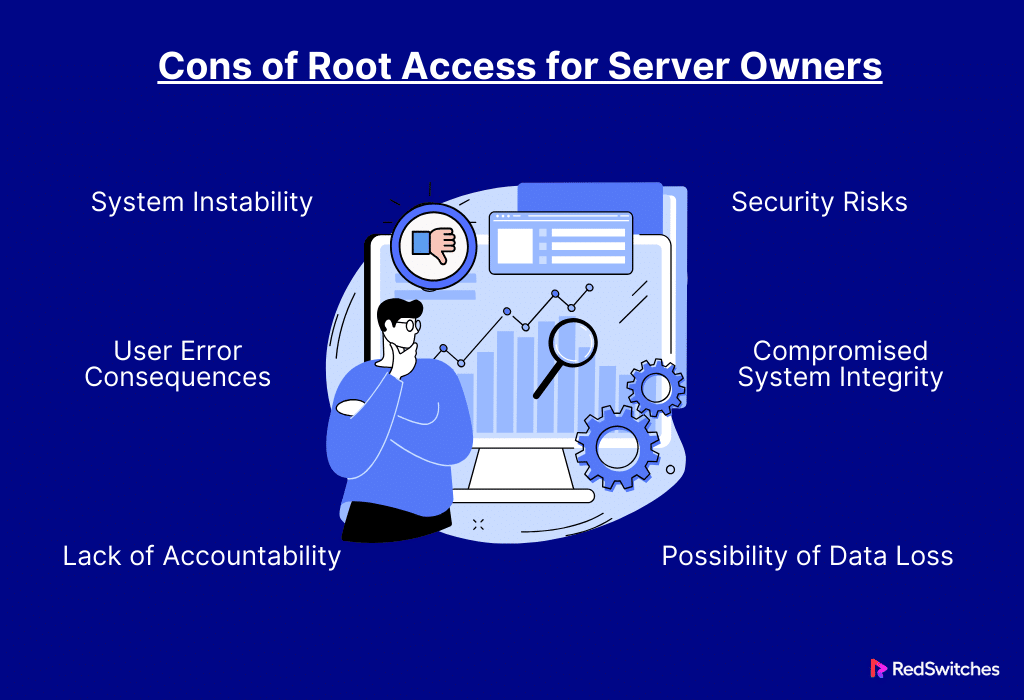
Cons of root access for Server owners
After discussing the benefits, let’s discuss the Cons of root access for Server owners.
Security Risks
Users who possess root access have the power to alter important system files, putting the server at risk for security breaches. There are no limitations. Changes to configurations or permissions could accidentally create vulnerabilities.
For example, if access controls change. Or, if the firewall is configured wrong. Then, the server may become vulnerable to exploitation or unauthorized access. To avoid accidental security breaches. But, the higher access level needs a deep knowledge of best security practices.
Also read 11 Dedicated Server Security Best Practices
System Instability
Inexperienced users could modify the system when given root access, affecting its stability. This could involve adding incompatible software. Or, it could involve changing settings or files. These changes can cause crashes or odd behavior.
With root access, users can make big changes to the system. Novice users might accidentally make changes that jeopardize the server’s reliability.
This may mean making critical system file changes. It can also mean installing software that doesn’t work with current settings. Or it can mean changing critical settings. Unpredictable behavior, performance problems, or even system failures could arise from these acts.
Possibility of Data Loss
Mistakes in administrative jobs, especially those involving root access, could cause data loss. For example, mishandling storage setups can do it. So can accidentally erase crucial files. This can result in losing vital data.
Compromised System Integrity
Unintentional or deliberate modifications to system files may jeopardize the server’s overall integrity. This could be a conflict. It could also be inconsistent behavior. Or, it could be a decline in performance.
User Error Consequences
Human faults can have serious repercussions and are common when users have elevated rights such as root access. These mistakes could involve erasing files by accident. Or setting up the network incorrectly. Or making changes that harm the server.
Lack of Accountability
Attributing modifications to a particular user can be difficult when several people have root access. The lack of accountability might impede security inquiries and troubleshooting. Finding the cause of a specific change or problem becomes hard.
How Do Server Owners Get Root Access?
Credits: Freepik
Root access is usually obtained by server owners using the following techniques:
First Server Setup
Server owners frequently create an administrator user account with elevated privileges during the initial server setup process. Root access is provided to this first user so they can carry out necessary administrative functions.
SSH (Secure Shell)
SSH is a popular protocol for safely connecting to distant servers. Owners of servers can use the credentials they were given at setup to access their server using SSH. After logging in, they can obtain root access by using the “su” (substitute user) or “sudo” (superuser do) commands.
Control panels for web hosting
Control panels such as Plesk or cPanel frequently offer a graphical interface for server management in web hosting setups. Through these panels, server owners can access root-level settings and perform various administrative operations without command-line interfaces.
Management Interfaces Offered by Hosting Providers
Many hosting companies provide web-based interfaces that let server owners control their configurations. These interfaces frequently have functions allowing you to run administrative operations or grant root access without SSH.
Operating System-Specific Techniques
There may be particular techniques for providing root access depending on the operating system (such as the Linux distribution). For Ubuntu, individuals can acquire superuser rights by adding themselves to the “sudo” group.
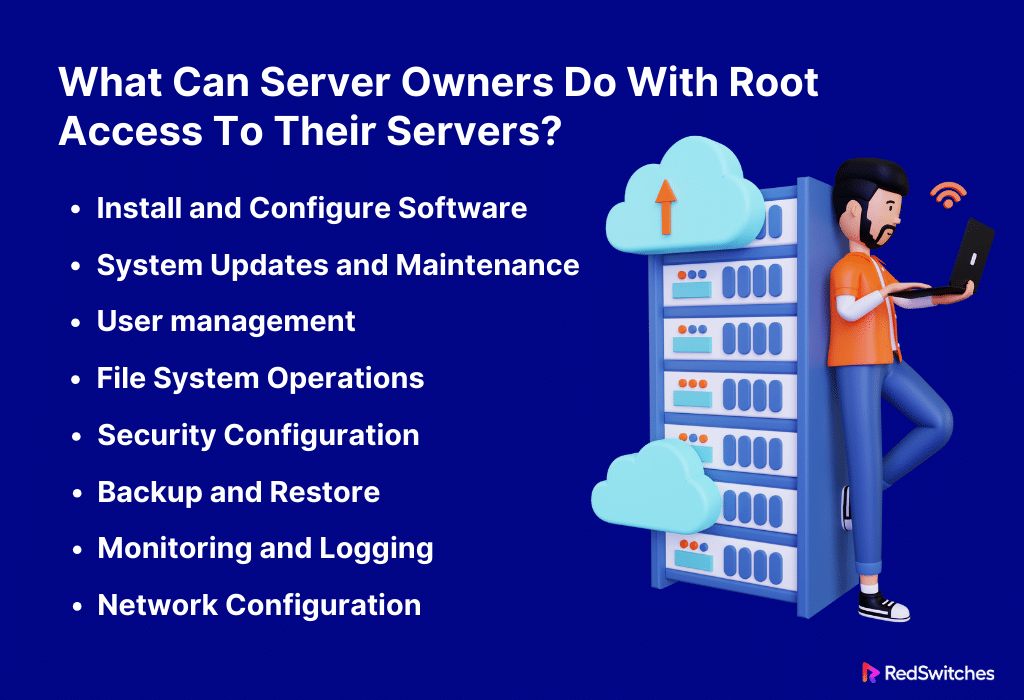
What Can Server Owners Do With Root Access To Their Servers?
It gives server owners root access. This gives them total control over the operating system. With root access, server owners can carry out the following several actions:
Install and Configure Software
The server owner can install, change, and run the software. This covers computer languages. It also covers databases like MySQL and PostgreSQL. It includes web servers like Apache and Nginx. And it covers utilities.
System Updates and Maintenance
Owners can install patches and update the operating system. They can oversee its upkeep with root access. Ensuring the server has the most recent security updates and features requires doing this.
User Management
Server owners can add, change, and remove accounts. They can control access to different files and directories, manage user groups, and define user permissions. You have complete control over user management with root access.
File System Operations
Server owners can perform system-level file and directory manipulations with root access. This covers adding, removing, and changing files. It also covers adjusting their ownership and permissions.
Security Configuration
Server owners can modify and improve the server’s security configuration. This means setting up firewalls. It also means creating security policies. And it means keeping access controls. These measures stop unwanted access.
Backup and Restore
Server owners can perform thorough backup and restoration procedures with root access. They can restore their backups of entire systems, databases, or individual files when necessary.
Also read Two Easy Ways of Creating Users in PostgreSQL
Monitoring and Logging
Server owners can monitor server performance and spot problems. They can also examine system logs. They can do this by setting up monitoring tools and customizing logging settings. For optimal server health and troubleshooting, this is essential.
Network Configuration
Using root access, server owners can set up IP addresses, DNS settings, routing tables, and other network parameters. They can administer network-related services and have control over network interfaces.
Owners of servers can alter kernel configurations and parameters. With this access, they can tweak the kernel, enable or disable features, and boost the server’s performance.
Root Access For Server Owners: Use Cases
Credits: Freepik
Root access gives server owners many use cases that enable them to optimize, customize, and control their servers. Common uses for root access include the following:
Software Installation
Owners can install and customize critical software with root access. They can do this to fit their needs. For instance, they can set up a database system, such as MySQL or PostgreSQL. They can install a web server like Apache or Nginx. Or implement content management systems, such as WordPress.
Security Enhancements
Server owners can put strong security measures in place if they have root access. For example, they can install intrusion detection systems. They can also set them up and configure firewalls to allow or prohibit traffic. They routinely deploy security upgrades to guard against threats and vulnerabilities.
System Updates and Maintenance
With root access, server owners can perform regular system updates and maintenance. For best performance and security, this means installing operating system updates. It also means upgrading software. And it means ensuring the server’s environment is up to date.
User Management
Server owners can efficiently manage user accounts with root access. They can alter existing accounts, add new users, and manage user permissions. For more security, they can, for example, allow some users access to certain directories. They can limit others.
Network Configuration
Server owners can use root access to adjust network settings, including IP addresses and DNS setups. They may manage many network interfaces. They optimize network performance and fix connectivity problems to ensure fast data transfer.
File System Operations
At the system level, server owners can modify files and directories. This covers the operations of adding, removing, and altering files in addition to adjusting their ownership and permissions. Users can set up file permissions or make directories to hold application data for added protection.
How To Reset Your Root Password?
Credits: Freepik
In this section, we will discuss ways to reset your root password.
Depending on your operating system, there may be subtle variations in the steps involved in resetting the root password. Here are some general procedures for changing a Linux server’s root password. Remember that these instructions assume you have the proper rights and may need physical or console access to the server.
Access the Server
You can use a remote connection or physical access to the server. Take advantage of a secure shell (SSH) client if you have remote access.
Restart the Server:
You should restart the server if you have physical access. To restart a server with a remote connection, you might need to get into the server’s administrative console or contact your hosting company.
Access GRUB
You must pause the standard startup during the boot process to access the GRUB (GNU GRand Unified Bootloader) menu. This usually entails hitting a key during the boot procedure, such as “Esc” or “Shift.”
Modify Boot Parameters
Inside the GRUB menu, locate the line that begins with “linux” or “linux16” and has the words “ro” or “ro quiet.”
rw init=/bin/bash
Enter Single User Mode
Press the “Ctrl + X” or “Ctrl + B” keys to enter single-user mode. By doing this, you can access a root shell prompt without needing the root password.
Read/Write Remounting of the Root File System
To make modifications, remount the root file system as read/write after seeing the root shell prompt.
mount -o remount,rw /
Modify the root password
To alter the root password, type in the following command. Put your preferred new password in lieu of “new_password”:
passwd root
Revert GRUB Configuration
Take back the modifications you made to the GRUB setup. Remove the previously added “rw init=/bin/bash” from the boot parameters by editing the GRUB configuration file.
Restart the server
To implement the modifications, restart the server:
reboot
Is Rooting Legal and Safe?
Typically, “rooting” means giving a mobile device administrative access or privileges. This is especially true for Android smartphones. On Unix-based systems (including Linux servers), obtaining administrative access is called “root access.” Both ideas require getting high permissions. But, there may be context and effect differences.
Rooting Android Devices
Here are some important safety points to consider before rooting your Android device:
Legality
In general, rooting an Android device is acceptable. Because the Android operating system is based on open-source software, users are free to alter it by the conditions of the licenses that go with it. However, manufacturers or carriers may void warranties if a device is rooted. And some actions taken after rooting may break the terms of service.
Safety
There are security dangers associated with rooting an Android device. Users can change system settings and data. They do this by gaining root access. This opens the device to possible vulnerabilities or harmful apps. Furthermore, some apps might not function on rooted devices because of security issues. Before rooting their smartphones, users should be aware of the hazards and proceed with prudence.
Rooting Unix-Based Systems
Here are some important safety points to consider before rooting your Unix-based systems:
Legality
On a Unix-based system, root access is allowed. It is often required for system administration. System administrators often use root access. They use it for tasks like setting up the system, updating or installing software, and maintaining security.
Safety
On a Unix-based system, root access comes with a lot of responsibility. It allows users to make changes that could affect the system. Errors or unauthorized activities could compromise it or cause instability. To stay safe, follow best practices. Use the principle of least privilege. Only use root access when needed.
Although legal, rooting an Android smartphone might violate warranties and pose security risks. Users should weigh the advantages against the potential disadvantages to secure rooted devices. And they should follow recommended practices.
For system administrators, gaining root access to Unix-based systems is a regular and essential procedure. It is safe and legal when carried out by authorized users aware of the obligations that come with enhanced privileges.
Users should always be mindful of the hazards involved, strictly adhere to policies and recommended procedures, and think through the ramifications of obtaining more rights on their devices or systems.
Conclusion
As a result of our investigation into rooting, we now thoroughly comprehend its importance, having examined the fundamentals of root access and its consequences for server owners. The advantages and risks of using such strong privileges have been made clear by exposing the pros and downsides.
As we traverse this complex terrain, it becomes clear that using root access sensibly and strategically is essential to maximizing server security and performance. RedSwitches is a trustworthy ally by providing customized solutions that maximize root access advantages while minimizing potential downsides.
Server owners can easily manage the challenges of root access by working with RedSwitches, guaranteeing a strong and secure digital infrastructure for their online ventures.
FAQs
Q. How do I give root access?
Using the “sudo” command and the desired action in the terminal to grant root access temporarily elevates privileges for the designated task.
Q. How to unlock root access?
Using the “passwd” command in the terminal, one may usually unlock root access by changing or modifying the root user password, guaranteeing safe and regulated access to system-wide configurations.
Q. What is the root user password?
The root user password is the primary way to access and control root rights on the system. The system administrator sets a private and secure authentication key during installation.
Q. What is root access?
Root access refers to the highest level of access to a computer system or device, such as a server or Android phone. It allows users to make changes to the system that are normally restricted for security reasons.
Q. What are the benefits of rooting an Android device?
Rooting an Android device can allow users to customize the device’s operating system, install special apps that require root access, and improve overall performance by removing bloatware.
Q. What are the risks of rooting an Android device?
Rooting can void the device’s warranty, potentially brick it if not done properly, and expose it to security vulnerabilities if not managed carefully.
Q. How can I root my Android phone or access on an Android device?
Rooting methods vary depending on the device model and manufacturer. It commonly involves using software such as KingoRoot or Magisk and may also require unlocking the bootloader.
Q. Can I root my Android device without a computer?
Yes, there are methods to root some Android devices without using a computer, known as one-click root methods. However, these methods may not be available for all devices and could carry additional risks.
Q. What is the difference between systemless root and traditional root?
Systemless root modifies the boot image to achieve root access without altering the system partition, allowing for easier system updates and potentially better security. Traditional root modifies the system partition directly.
Q. What is a custom ROM, and how does it relate to rooting?
A custom ROM is a modified version of the Android operating system. Rooting may be required to install a custom ROM, as it often involves changing the device’s system files and settings.
Q. What precautions should I take before rooting my Android device?
It’s important to research and understand the specific rooting process for your device, back up important data, and consider the potential consequences, such as voiding the warranty, before rooting.
Q. How does rooting an Android device affect app compatibility?
Rooting can enable installing apps that require root access, but it can also potentially make certain apps that rely on strict security measures, such as mobile banking apps, incompatible or less secure.
Q. What is the role of root access in server management?
Root access on a server allows system administrators to have full control over the system, enabling them to perform administrative tasks, install software, and make configuration changes that are impossible with standard user permissions.
Q. How to root Android devices?
Use particular tools or techniques to obtain privileged access and enable customization beyond manufacturer limitations. Observe the procedure’s device-specific instructions.
Q. Rooting your Samsung Phone: How to Do it?
Turn on Developer Options, unlock the OEM, make a backup of your data, download rooting tools, unlock the bootloader if necessary, run the process on a computer, and use an app to confirm that you have root access.
Q. Is Android Root Important?
Essential for knowledgeable users who want deep personalization, setting up unique ROMs, and utilizing root-dependent applications; nonetheless, it has hazards such as voiding warranties.
Q. What happens when you root your device?
Provides elevated authority, permitting sophisticated personalization and application installation; but, it has hazards such as nullified warranties and possible security weaknesses. Throughout the procedure, proceed with caution.