Key Takeaways:
- SSH (Secure Shell) enables secure remote access and command execution over insecure networks, using strong encryption and authentication.
- SFTP (Secure File Transfer Protocol), an extension of SSH, focuses specifically on secure file transfers, providing encryption and secure management of files.
- Both SSH and SFTP employ robust encryption methods and multiple authentication techniques, including public key and password-based authentication, to ensure secure communications and transfers.
- SSH offers a wide range of functionalities beyond secure communication, including port forwarding, session multiplexing, and X11 forwarding, whereas SFTP specializes in file transfer and management.
- Encryption and decryption in both protocols can impact performance, affecting speed and latency during file transfers and communications.
- SSH is ideal for secure system administration, remote access, and command execution, while SFTP is used for secure file transfers and management tasks.
- Both protocols typically use port 22 for secure connections, though SSH can be configured to use different ports for additional security measures.
- Use SSH for secure remote access and interactive sessions, and choose SFTP for encrypted file transfers and routine file management tasks.
In online security, SFTP and SSH are two terms you often hear. There are ways to keep data safe when sending it across the internet. But they do different jobs. This article will take a closer look at SFTP vs SSH. Think of SFTP as a secure way to move files from one place to another. SSH, however, lets you safely access a computer over the internet.
When we break through the mystery surrounding SFTP vs SSH, we discover ten significant distinctions that together reveal subtleties that influence the security environment of our globalized society.
So grab a virtual front-row seat and join us as we study the nuances of the SFTP vs SSH dispute and attempt to identify the various strategies of these two cyber guards.
Table of Contents
- Key Takeaways
- What is SSH?
- What is SFTP?
- SFTP vs SSH: Key Differences
- When to Use SSH or SFTP?
- Conclusion
- FAQs
What is SSH?
Credits: Freepik
SSH is a network protocol that allows users, especially system administrators, to securely access a computer across an unprotected network. It is often referred to as Secure Shell or Secure Socket Shell.
In addition, the group of programs that carry out the SSH protocol are referred to as SSH. Strong password and public key authentication, along with encrypted data transmissions between two computers connected via an open network, like the internet, are all made possible by Secure Shell.
Network administrators frequently use SSH to administer systems and programs and offer robust encryption remotely. It allows them to log in to another computer over a network, run commands, and transfer information between computers.
SSH is an acronym for the tools used to implement the cryptographic network protocol and the protocol itself. Using the client-server architecture, SSH links an SSH server—the endpoint where the session is executed—and a Secure Shell client application—the endpoint where the session is shown.
SSH uses strong encryption to ensure data security over the network. The support for application protocols used for file transfers or terminal emulation is frequently present in SSH implementations.
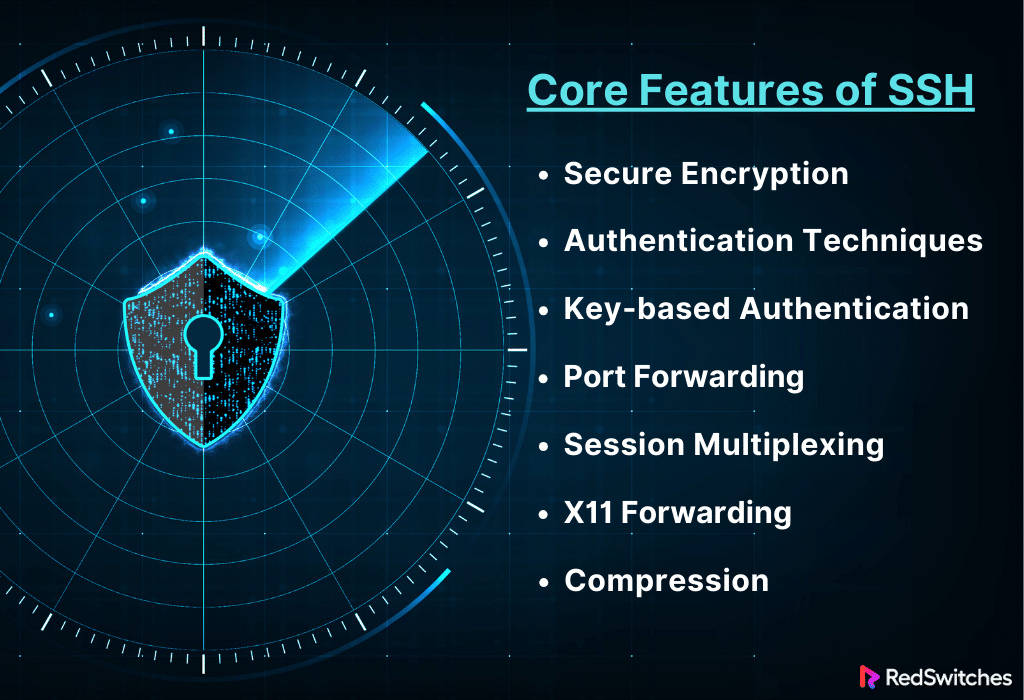
Core Features of SSH
Following the discussion of the definition, we will now learn about the key features of SSH.
Secure Encryption
SSH protects client-server communication by encrypting it using powerful algorithms. This ensures the confidentiality and integrity of information sent across the network is shielded from prying eyes and illegal access.
Authentication Techniques
SSH is compatible with several authentication techniques, such as public key and password-based authentication. Because of this flexibility, users can select the safest and most appropriate way to authenticate the server.
Also read Types of Database Encryption: Best Practices for Securing Your Data
Key-based Authentication
Support for key-based authentication is one of SSH’s most notable and powerful features. Users can create key pairs, where the public key is kept on the server, and the private key is safely kept on the client. This method improves and provides an extra layer of security compared to traditional passwords.
Port Forwarding
SSH makes secure port forwarding possible by enabling users to build encrypted tunnels through which other network traffic can be sent. This feature is useful and enables safely accessing services hosted on distant servers behind a firewall or on a private network.
Session Multiplexing
Multiplexing of sessions over a single encrypted connection is made possible via SSH’s multiplexing functionality. This feature maximizes available resources and boosts productivity when handling several jobs simultaneously.
X11 Forwarding
SSH can forward X11 sessions, enabling graphical programs to run remotely and see them displayed on their local display. This is useful for engaging with remote GUI apps as though they were local while running them on a distant server.
Compression
SSH allows the data stream to be compressed to maximize data transfer. This lowers the volume of data transferred across the network, particularly when bandwidth is constrained.
How SSH Works
Credits: Freepik
In this section of our blog, we will understand how SSH works. Let us understand the technical breakdown of SSH.
Key Exchange and Encryption
Before starting communication, SSH performs a secure key exchange between the client and server. The server provides its public key in response to a connection request made by the client. To establish a secure communication channel, the client generates a session key and sends it back encrypted with the server’s public key. The basis for encrypting the ensuing data transmission is this encrypted session key.
Authentication
An essential part of the SSH operation is authentication. Users can authenticate themselves using various techniques, including the more secure key-based authentication or the conventional username/password combo. In the latter case, users have two cryptographic keys: a matching public key shared with the server and a private key safely kept on their client computer.
Session Multiplexing
SSH allows multiplexing, which enables many communication channels to run over a single encrypted connection to maximize resource use and boost efficiency. As a result, users can handle multiple tasks at once inside a single SSH session.
Port Forwarding
Port forwarding takes the front stage in extending SSH’s reach. While remote port forwarding enables the server to forward a remote port to a different port on the client, local port forwarding provides secure access to services on a remote server. This fosters secure access to local services much easier.
X11 Forwarding Process
SSH shows off its graphical capabilities by enabling users to run and view local graphical apps on a remote server. This operation makes it possible to communicate with graphical interfaces without issues through a secure SSH connection.
Also, read How to Use SSH to Connect to a Remote Server in Linux And Windows
Compression
SSH uses compression methods in the background to maximize data transfer. This guarantees that the quantity of data traveling across the network is minimal, particularly when bandwidth is a valuable resource.
Closing the Connection
Once the user finishes their work on the remote server, a safe and classy disconnect occurs. An encrypted channel is closed, resources are released, and a safe and well-planned connection termination is left.
Security Aspects of SSH
Credits: Freepik
Security is paramount in SSH. From strong public key authentication to safe connection initiation, every component of SSH places a high priority on data security.
It uses robust encryption techniques like AES, 3DES, and Blowfish to protect data secrecy. Message Authentication Codes (MACs) are another tool SSH uses to confirm the authenticity and integrity of data.
SSH strengthens its defenses with several security elements in addition to encryption. Its focus on secure key management is one noteworthy feature where public-key cryptography enables users to create and maintain key pairs for authentication. This removes the need for potentially unsafe password-based logins in addition to providing a robust authentication mechanism.
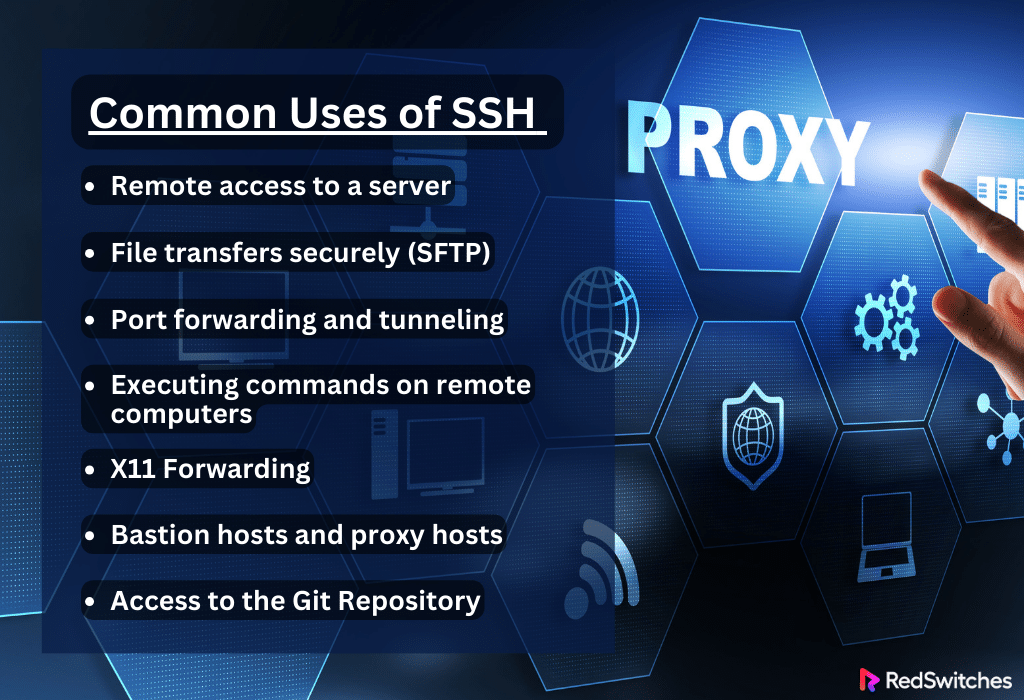
Common Uses of SSH
Now let’s briefly understand some common uses of SSH.
Remote Access to a Server
SSH is widely used for safe remote access to servers and networking equipment. System administrators can safely log in to distant servers for upkeep, repairs, and diagnostics.
File transfers securely (SFTP)
Secure file transfers between systems are made possible via SFTP, an SSH extension. It offers a safe substitute for conventional FTP when uploading, downloading, and handling files on distant servers.
Port forwarding and Tunneling
SSH enables users to forward ports and build safe tunnels between nearby and distant computers. This is useful for safely connecting to databases or accessing services on a distant server.
Executing Commands on Remote Computers
Secure command execution on remote machines is made possible by SSH. This is especially helpful for automation, scripting, and remote administration jobs.
X11 Forwarding Uses
X11 forwarding over SSH allows users to execute graphical apps on a distant server and view them locally. This is beneficial when working with GUI-based applications on remote servers.
Bastion hosts and Proxy hosts
Bastion hosts provide secure access to private networks, and SSH establishes secure proxy connections. They offer an extra layer of security by acting as the single point of entry from the public internet, protecting internal systems from direct exposure and unauthorized access. Proxy hosts and other technologies create secure proxy connections for specific applications. It utilizes a gateway to access internal systems and improves security.
Access to the Git Repository
SSH is supported by the distributed version control system Git, allowing for safe repository access. Developers can safely clone, pull, and push code through secure SSH connections.
Also read How to Install a Desktop (GUI) on an Ubuntu Server
What is SFTP?
Credits: Freepik
The Secure File Transfer Protocol, or SFTP, is a secure file transfer protocol that offers high security for file transfers, both sending and receiving. It is a secure alternative to traditional FTP due to its secure shell encryption.
Like FTPS, SFTP encrypts data while transferring between systems using AES and other techniques. Additionally, SFTP offers various methods to complete connection authentication, including SSH keys, user IDs and passwords, or combinations.
Businesses and individuals who need a secure way to transfer sensitive data often use SFTP which complies with file transfer regulations set forth by HIPAA, GDPR, and other laws. Because of its improved security features and versatility, it is frequently chosen over classic FTP.
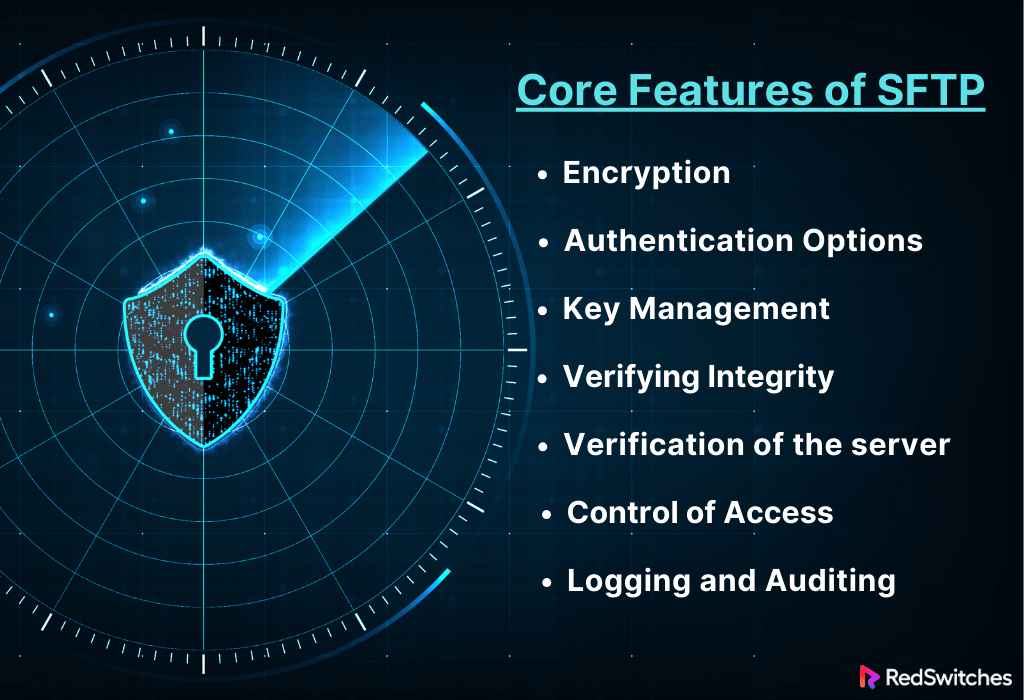
Core Features of SFTP
After discussing the definition, Let’s understand the core features of SFTP in detail.
Encryption
SFTP protects files from illegal access or interception by encrypting data while it is transmitted. By doing this, the integrity and confidentiality of the sent data are guaranteed.
Authentication Options
Multiple authentication mechanisms, such as the more secure public key authentication and the conventional username/password combination, are supported by SFTP. Because of this flexibility, users can select the authentication method that best suits their security needs.
Key Management
Authentication security is improved by allowing users to create and manage public and private key pairs. Maintaining the integrity of the file transfer depends on using proper key management procedures.
Verifying Integrity
SFTP uses hashing methods to confirm the integrity of transferred data. Hashes are produced before and after the data transfer to detect unauthorized alterations.
Verification of the server
SFTP clients uses host key verification to confirm the server’s legitimacy before initiating a connection. This guarantees a secure connection and protects against potential man-in-the-middle attacks.
Control of Access
SFTP uses file system permissions to regulate user access. Users can improve security and reduce potential risks by restricting their ability to interact with files and directories.
Logging and Auditing
SFTP servers keep thorough records of user activity, which serve as audit trails for incident identification, security audits, and compliance monitoring. Having these logs helps maintain a strong security posture.
How SFTP Works: Technical Breakdown
Before moving toward the SFTP vs SSH debate, we will now understand the working procedure of SFTP in detail.
Establishing a connection and verifying identity
Initiating an SFTP connection involves a negotiation between the client and the server. During this process, the server requests the user’s authentication credentials to verify the identity.
Change of Encryption Keys
Following authentication, a key exchange is conducted between the client and server to create a secure communication channel. Encrypting the data during transmission requires creating a shared secret, also known as a session key.
Encryption of Data
Once the secure communication channel is established, SFTP ensures that the files being transferred are safe from prying eyes or illegal access by encrypting the data using the pre-established session key. This encryption safeguards the data by traveling through a secure tunnel.
File Operations and Command Execution
The client and server can exchange commands for different file actions once the secure channel has been created. Requests to upload, download, remove, or list files and directories on the server are examples of these commands.
Integrity Checking through Hashing
SFTP computes hash values for the transferred files using hashing methods before and after the data transfer. Through this method, the recipient can compare the hash values to confirm the integrity of the files they received.
Logging and Error Handling
SFTP keeps detailed logs of the file transfer procedure. Information concerning user actions, mistakes, and other pertinent occurrences may be included in these logs. These logs are also essential for auditing, debugging, and tracking file transfer activities.
Termination of Connection
The SFTP connection is safely closed after the file transfer is finished or the user chooses to disconnect. A smooth conclusion to the secure session is ensured by releasing resources and closing the encrypted channel.
Also, read Efficient Log Management in Linux Environment with Journalctl
Security Aspects of SFTP
Now, let’s throw light on the security aspects of SFTP.
The SSH backbone of SFTP is largely responsible for its security. The same authentication and encryption methods are used, guaranteeing the safe execution of commands for file management and transfers. Additionally, SFTP’s support for transport layer security adds another layer of security while data is transmitted.
Moreover, SFTP carries over the strong security characteristics of its SSH base, offering a complete barrier for private information while it is being transferred. End-to-end encryption is ensured by the SSH backbone, which reduces the possibility of interception and unauthorized access during file transfers.
In addition, the authentication mechanisms, which include password-based and public-key authentication, confirm the client and server’s identities and strengthen the security posture. By doing this, the communicating entities build a relationship of trust and avoid unwanted access.
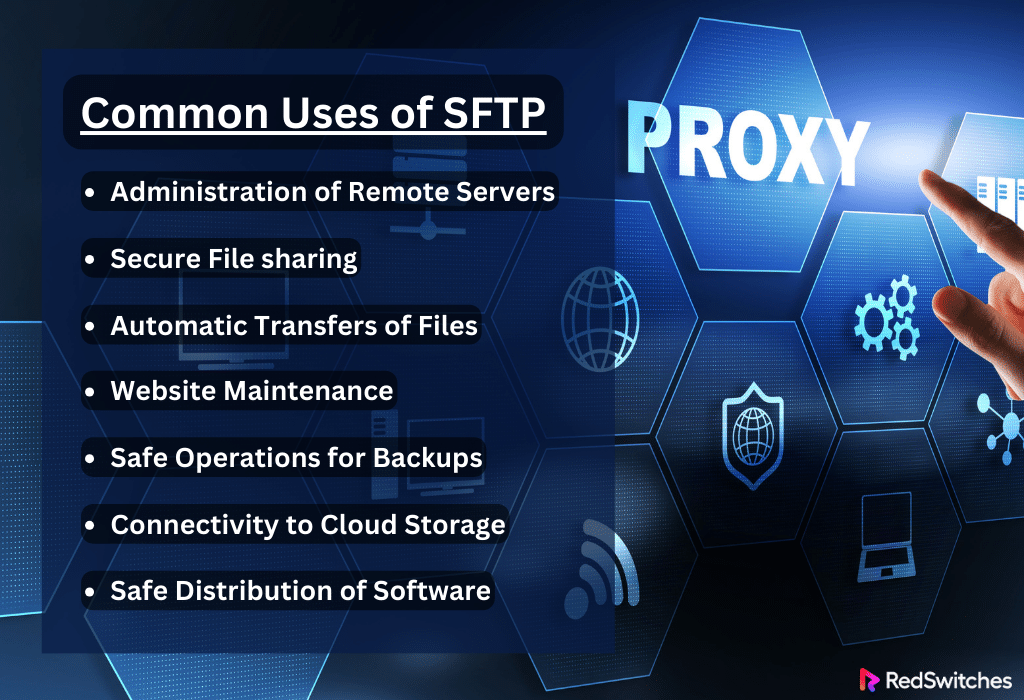
Common Uses of SFTP
Before moving towards our core topic of debate, the 10 key distinctions in the SFTP vs SSH debate, let’s understand the common uses of SFTP.
Administration of Remote Servers
System administrators securely manage files on distant servers using SSH File Transfer Protocol (SFTP). For jobs like configuration, updates, and troubleshooting, this is essential.
Secure File sharing
SFTP offers a secure framework for file exchange between users and systems. It guarantees the confidentiality of sensitive data while it is being transmitted.
Automatic Transfers of Files
Scripts and automated workflows facilitating planned or event-triggered file transfers can incorporate SFTP. Situations like data backups, log file transfers, and batch processing are typical examples.
Website Maintenance
SFTP is a secure file uploading and management tool used by web developers. This guarantees that website content is secured during upgrades and modifications.
Safe Operations for Backups
Sensitive data can be transferred and stored in a safe environment by organizations using SFTP for secure backup operations.
Connectivity to Cloud Storage
Secure file transfers to and from cloud-based repositories are made possible by frequently integrating SFTP with cloud storage solutions. This is a typical scenario when data needs to be transferred between on-premises servers and cloud platforms.
Safe Distribution of Software
Software updates and patches are distributed securely over SSH File Transfer Protocol. This guarantees that the software’s integrity is preserved throughout the distribution process.
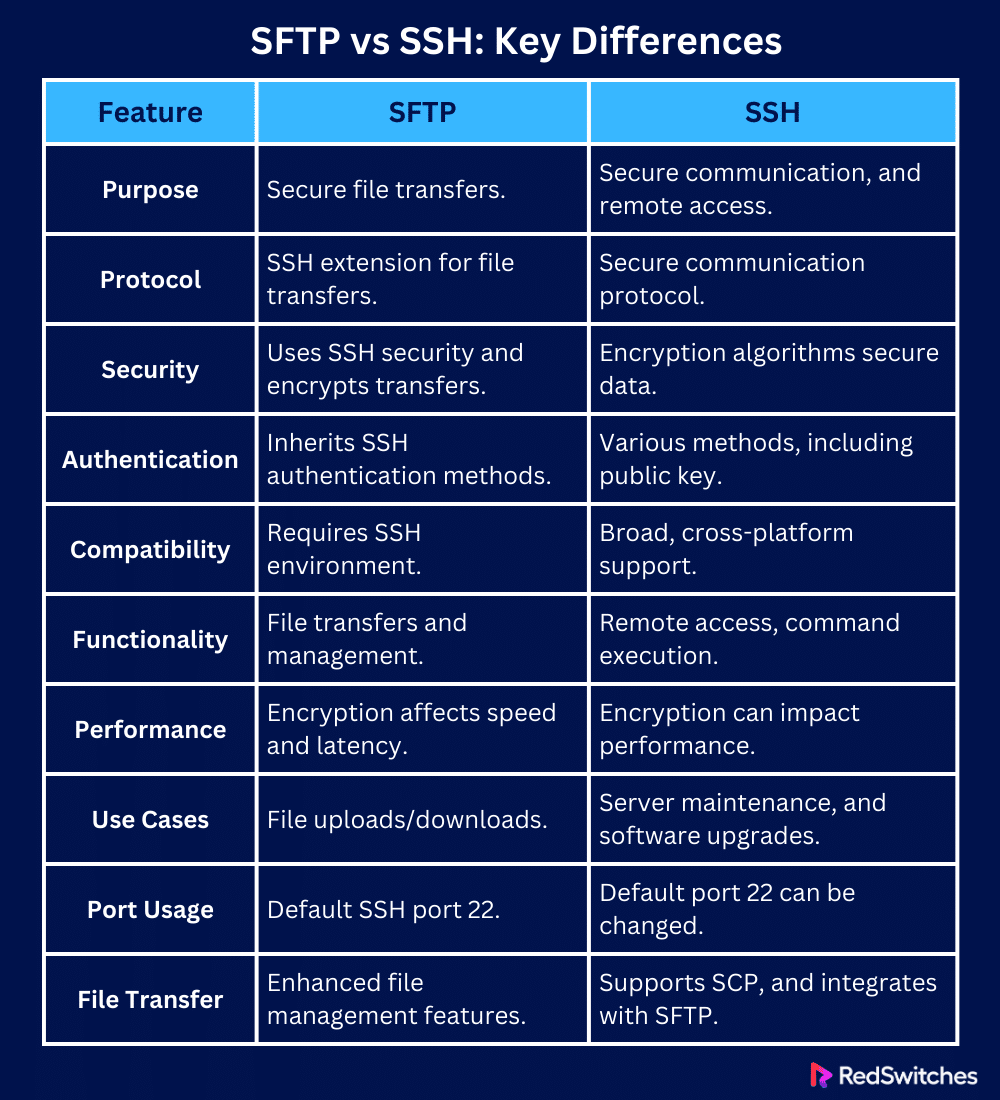
SFTP vs SSH: Key Differences
Credits: Freepik
We will now have a detailed analysis of the critical distinctions in the SFTP vs SSH debate. Let’s go.
SFTP vs SSH: Purpose
The first distinction in our SFTP vs SSH debate is the Purpose.
SFTP
An SSH extension, SFTP (Secure File Transfer Protocol), has a unique function for safe file transfers. The secret and integrity of file transfers between local and remote systems are the main concerns of SFTP, even when it operates via the secure channel created by SSH.
In contrast to SSH, SFTP is best suited for safe file management, uploads, and downloads rather than interactive command-line connections. Its goal is to offer a safe substitute for conventional FTP by ensuring that files move across the network in an encrypted manner, protecting private information from prying eyes.
SSH
A fundamental protocol called SSH (Secure Shell) is intended to provide encrypted and secure communication over networks that may be insecure. Its main objective is to enable safe communication and access to distant systems.
SSH enables users to instantly execute commands on a remote computer by creating an encrypted channel between a client and a server. As a result, SSH is a very useful tool for developers and system administrators who need secure, interactive command-line access for things like configuration, debugging, and server administration.
SFTP vs SSH: Protocol Type
This distinctions section will differentiate between SFTP and SSH concerning the protocol type.
SFTP
SFTP (Secure File Transfer Protocol) is a specialized protocol operating within the SSH framework. It can be viewed as an SSH subsystem created especially for safe file transfers. SFTP is a file transfer protocol that ensures that files are securely exchanged between a local and distant system.
SFTP uses SSH’s security capabilities to offer a dependable and encrypted channel for file uploading, downloading, and management.
SSH
A complete protocol for secure communication is SSH (Secure Shell), a subset of network protocols. Its main purpose is establishing a safe and encrypted connection between two networked devices—typically a client and a server.
SSH ensures data confidentiality, integrity, and authenticity while being transmitted, making it a secure substitute for more conventional communication protocols like Telnet. It functions at the application layer of the OSI model.
This protocol is essential for safe remote access and command execution since it is flexible and supports many authentication techniques and encryption schemes.
SFTP vs SSH: Security
Security is the most critical aspect of the SFTP vs SSH argument. Let’s delve deep into it.
SFTP
As an SSH extension, SFTP (Secure File Transfer Protocol) builds on the security features of its parent protocol to enable safe file transfers. Encrypting data while it is being transmitted is a key component of SFTP security.
SFTP guarantees that data are sent securely using SSH’s encryption to prevent eavesdropping and unauthorized access. SFTP and SSH share similar authentication techniques, giving users public key and username/password authentication choices.
Key management procedures are essential for SFTP to provide safe authentication. They enable users to create and maintain key pairs. SFTP also uses hashing methods for integrity checking to confirm the integrity of received files. Here hash values are computed both before and after data transfer.
SSH
A mainstay of network security, SSH (Secure Shell) offers a strong foundation for safe communication. SSH uses sophisticated encryption algorithms like AES, 3DES, and Blowfish to protect data in transit, making encryption one of its core tenets.
This encryption ensures that data transferred between the client and server stays private by avoiding unauthorized interception.
Moreover, SSH offers a variety of authentication methods, giving users the option to select between public-key authentication, which is more secure, and password-based authentication.
SFTP vs SSH: Authentication
Which has strong authentication potential? Let us understand this in the SFTP vs SSH debate.
SFTP
As an extension of SSH, SFTP (Secure File Transfer Protocol) mirrors and inherits the strong authentication procedures of its parent protocol. Because the authentication techniques offered by SFTP are compatible with SSH, file transfers can be conducted reliably and securely.
With the help of SFTP, customers can access secure file transfer services with well-known login credentials because it supports standard username/password authentication. However, public-key authentication is a more popular and secure choice for SFTP.
SSH
SSH (Secure Shell) uses a flexible and safe authentication mechanism that prioritizes users’ identity verification to grant them safe access to remote systems. Its main strength is its support for various authentication methods, which gives users choices based on their security preferences and organizational norms.
While strong passwords are advised to reduce security risks, the standard username/password combination is still popular. A more secure option is public-key authentication, which requires users to create a key pair consisting of a private key on the user’s device and a public key on the server.
SFTP vs SSH: Compatibility
Let’s differentiate the compatibility factor concerning the SFTP vs SSH debate.
SFTP
SSH (Secure Shell) uses a flexible and safe authentication mechanism that prioritizes users’ identity verification to grant them safe access to remote systems. Its main strength is its support for various authentication methods, which gives users choices based on their security preferences and organizational norms.
While strong passwords are advised to reduce security risks, the standard username/password combination is still popular.
A more secure option is public-key authentication, which requires users to create a key pair consisting of a private key on the user’s device and a public key on the server.
SSH
One prominently compatible and extensively used protocol that guarantees safe communication in a variety of computing contexts is SSH. It displays cross-platform compatibility and native support on Unix-like systems, such as Linux and macOS.
Third-party programs such as PuTTY or OpenSSH for Windows can be used to access SSH on Windows systems. The protocol supports TCP/IP and may be easily navigated through firewalls and network address translation (NAT) settings on various network topologies.
SFTP vs SSH: Functionality
Now, we will compare the functionality concerning the SFTP vs SSH argument.
SFTP
The Secure File Transfer Protocol, or SFTP for short, is an SSH extension that specializes in file transfers securely and offers unique features designed to make file management safe and effective. Its main purpose is to offer an encrypted, safe environment for file transfers between local and remote systems.
Using the encryption powers inherited from the underlying SSH protocol, SFTP encrypts data while transferring files. In addition to transferring files, SFTP enables users to perform file management operations safely, see file structures on remote computers, and list directories. Users can also maintain the confidentiality of the transmitted files by uploading files from local computers to distant servers and downloading them in another way.
SSH
SSH (Secure Shell) is a robust and flexible protocol with several features to guarantee remote access and secure communication. Fundamentally, SSH gives users a safe way to connect to and communicate with remote systems, which is why it’s a crucial tool for managing, configuring, and debugging servers.
The protocol performs exceptionally well in creating encrypted communication channels across networks that may not be entirely secure, guaranteeing data privacy, accuracy, and legitimacy while it is being transmitted.
Beyond just remote access, SSH also provides features including command execution, file transfers via secure copy (SCP), secure service access via port forwarding, graphical interface display via X11 forwarding, and secure channel creation for several data kinds via tunneling.
SFTP vs SSH: Performance
The most important feature is the performance. Let’s compare it in the SFTP vs SSH debate.
SFTP
While SFTP encrypts data to protect your transfers, the computational overhead for encryption and decryption that results from encrypting affects the overall speed of file transfers. Like SSH, SFTP can cause latency, especially when communication with minimal latency is essential. It is also necessary to consider the bandwidth for encryption since safe file transfers require sending additional encrypted data.
SSH
Prominent for its strong security features, SSH (Secure Shell) brings certain performance problems. The computational overhead caused by the encryption and decryption procedures built into SSH slows down data transfer.
This encryption overhead could be especially apparent on systems with low computing power and cause data transfer delays. Furthermore, the latency caused by the cryptographic procedures may impact the nature of real-time interactive encounters.
SFTP vs SSH: Common Use Cases
Now, we will compare the Common use cases concerning the SFTP vs SSH argument.
SFTP
Due to its many popular applications, SSH (Secure Shell) is an essential protocol for remote access and secure communication. One of its main uses is remote server access, where administrators can use a command-line interface to administer and configure systems from a distance safely.
SSH allows it to execute commands on distant servers in real time, facilitating operations like system maintenance, software upgrades, and installation. Its flexibility is demonstrated by its support for port forwarding, which improves the security of gaining access to services on distant servers, and tunneling, which makes it possible to create secure channels for transmitting various network traffic types.
SSH
Due to its diverse popular applications, SSH (Secure Shell) is an essential protocol for remote access and secure communication. One of its main uses is remote server access, where administrators can use a command-line interface to administer and configure systems from a distance safely.
SSH allows it to execute commands on distant servers in real-time, facilitating operations like system maintenance, software upgrades, and installation.
SFTP vs SSH: Port usage
Let’s compare Port usage in the SFTP vs SSH debate.
SFTP
Using SSH’s encryption and security characteristics, SFTP (Secure File Transfer Protocol) functions as a subsystem of SSH. As a result, by default, SFTP uses port 22, used by SSH. By using this default port, SSH-established secure connectivity is maintained for SFTP transactions.
SSH
Port 22 is the primary communication port for SSH (Secure Shell). SSH can create encrypted connections using this default port to provide secure remote access, command execution, and other features.
Even though port 22 is the default port for SSH, administrators can set SSH to run on other ports to comply with certain network setups or for security concerns. Users must include the port number in their connection parameters when utilizing an alternate port.
SFTP vs SSH: File Transfer
Now, Let’s compare File Transfer in the SFTP vs SSH debate.
SFTP
As a crucial component of SSH, SFTP (Secure File Transfer Protocol) is devoted to safe and effective file transfers. In contrast to SCP (Secure Copy), SFTP offers several interactive file management tools in addition to basic copying. It uses SSH’s security capabilities to encrypt data as it is being transferred, guaranteeing the integrity and confidentiality of the contents.
SSH
SCP (Secure Copy) and SFTP (Secure File Transfer Protocol) are two prominent examples of the protocols that SSH (Secure Shell) integrates with to provide secure file transfers. SCP is an easy-to-use command-line technique that simplifies file transfers between local and remote systems using SSH.
Also Read How to Use SSH Public Key Authentication
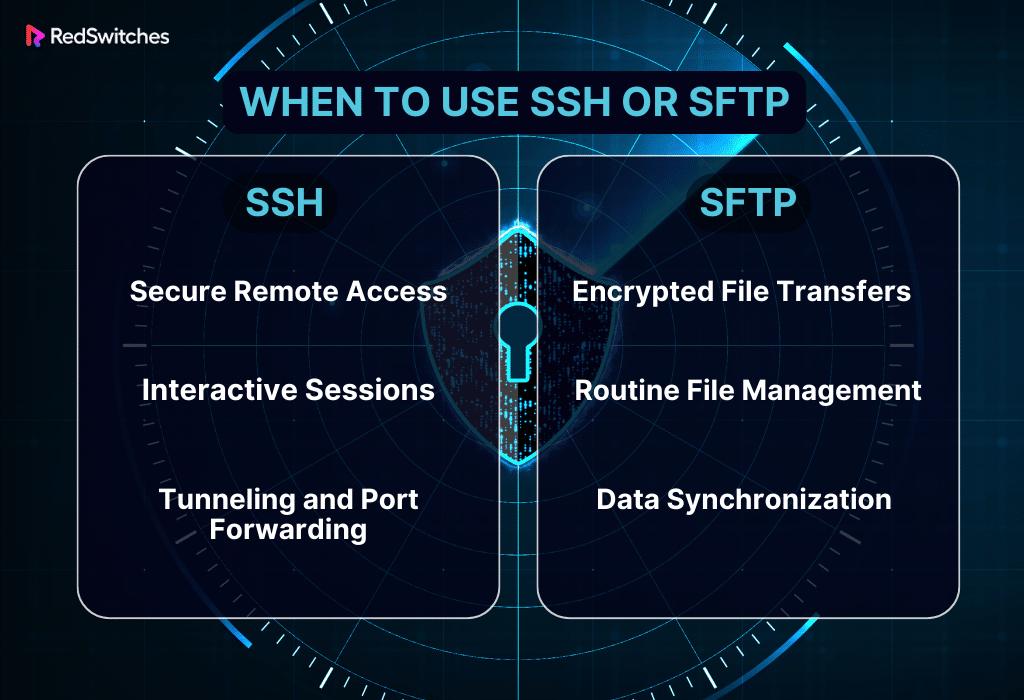
When to Use SSH or SFTP?
After discussing the ten key differences in the SFTP vs SSH debate, we will understand which is required and when.
Choose SSH if
Secure Remote Access: If using a server for real-time command execution, system administration, and command-line interaction is your main objective, then secure remote access is what you need.
Interactive Sessions: For safely performing commands on a remote server, you may require an interactive shell.
Tunneling and Port Forwarding: To securely access services on distant servers and create secure pathways for transmitting network traffic, use port forwarding and tunneling.
Choose SFTP If
Encrypted File Transfers: If transferring files securely between local and remote computers is your paramount need.
Routine File Management: When you require a complete solution for managing files regularly, such as integrity checks, uploads, downloads, and directory listings.
Data synchronization: To handle data synchronization duties between local and remote systems automatically and securely.
Conclusion
To summarize, studying the SFTP vs SSH debate has highlighted two crucial file management protocols and secure communication protocols. To help with decision-making, we examined their fundamental characteristics, figured out how they function, and revealed ten significant distinctions.
Knowing when to use SFTP for thorough and safe file transfers and SSH for strong command-line interactions becomes crucial as enterprises traverse the terrain of secure data transmission and remote access.
RedSwitches is a leader in customized hosting solutions, offering robust security and flawless operation in the dynamic digital world. Selecting a hosting partner such as RedSwitches guarantees a dependable infrastructure reinforced by state-of-the-art technology and a steadfast dedication to data protection, regardless of the choice between SSH and SFTP.
FAQs
Q. SFTP vs SSH: Which is better?
SFTP and SSH serve different purposes; SSH is a protocol for secure remote access and command execution, while SFTP is specifically designed for secure file transfers.
Q. SFTP vs SSh: What is the difference between SSH and FTP?
While both provide secure file transfers, SSH (Secure Shell) is a comprehensive protocol for secure remote access, including command execution. At the same time, FTP (File Transfer Protocol) is a standard protocol solely for file transfers.
Q. SFTP vs SSH: Is SSH and SFTP connected to the same port?
Yes, SFTP typically operates on the same port as SSH, port 22 by default. Both protocols leverage the security features of SSH, ensuring encrypted communication during file transfers and remote access.
Q. Is SFTP passive or active?
SFTP operates over the SSH protocol, and unlike traditional FTP, it does not use separate passive or active modes. Instead, SFTP establishes a single secure connection, simplifying configuration and providing inherent security during file transfers.
Q. What is the difference between SFTP and SSH?
SSH (Secure Shell) is a secure protocol used to access a remote server, while SFTP (SSH File Transfer Protocol) is a specialized protocol for securely transferring files over an SSH connection.
Q. How does SFTP provide secure file transfer?
SFTP provides a secure means of transferring files by encrypting both the data being transmitted and the commands used for file operations.
Q. Why is SFTP often preferred over other file transfer protocols?
SFTP is often preferred for file transfers because it provides a secure channel for data transfer and offers authentication options for added security.
Q. How is SFTP different from FTPS?
An SFTP is based on SSH, while FTPS (FTP over SSL) uses SSL/TLS for encryption. SFTP is often favored for its ease of use and strong security features.
Q. What are the advantages of using SFTP for file transfer?
SFTP offers secure and encrypted file transfers, supports various authentication methods, and can be used to automate file transfer processes.
Q. SSH vs SFTP: Can SFTP be used with a standard SSH server?
Yes, SFTP is typically built into SSH servers, allowing users to securely transfer files over a secure shell connection.
Q. How does SFTP compare to SCP for transferring files?
SFTP and SCP (Secure Copy Protocol) both utilize SSH for secure file transfer, but SFTP provides additional file management capabilities beyond simple file transfer.