Ask any business, and they’ll tell you that the data is the most prized asset in their inventory.
As such, businesses invest a lot of resources in keeping their databases safe and away from prying eyes.
Encryption has emerged as the most cost-effective method of guaranteeing the confidentiality and integrity of critical database data such as customer details, financial records, and intellectual property.
Encryption generally converts the database data (called plaintext) into unreadable text (called ciphertext). This process is applied to data at rest (stored on a medium) and data in transit to ensure that even if unauthorized parties intercept data in transit, they can’t benefit from the data.
The process of database encryption and managing encrypted databases involves working with robust encryption algorithms and multiple security-focused processes at all levels of database management.
This article will discuss why database encryption is a critical business requirement and how it can help you secure your data at all levels.
Table Of Content
- An Overview of Database Encryption
- Types of Database Encryption
- How Does Database Encryption Work?
- Database Encryption Methods
- Advantages of Database Encryption
- Disadvantages of Database Encryption
- Conclusion
- FAQs
An Overview of Database Encryption
Database encryption is critical to data security because it ensures the confidentiality and integrity of sensitive data contained in databases. The process converts plaintext data into an unreadable ciphertext, which can only be decoded with the correct encryption key.
Encryption Levels
Database encryption is applied at a variety of levels. At the storage (disk) level, encryption safeguards data when it is physically stored, preventing theft or illegal access to database files. Encrypting the whole database or particular tables is customary at this level of encryption.
Column-level encryption is another level that focuses on encrypting specific columns or fields inside the database. This method delivers a more granular data encryption process, in which sensitive data such as social security numbers or credit card information is protected while non-sensitive data remains unencrypted.
There is also the option of encrypting data in transit, ensuring that data stays secure as it’s transmitted between the database server and clients. This is accomplished by employing secure communication protocols such as SSL/TLS.
The Role of Keys in Database Encryption
Effective database encryption is as good as key management. Encryption keys must be securely kept, maintained, and cycled regularly to ensure the security of encrypted data. Software-based key management systems, or hardware security modules (HSMs), are often utilized to protect the integrity and secrecy of encryption keys.
Encryption and Performance Overheads
You should also consider the impact of encryption on system performance. Database encryption is all about maintaining a careful consideration of speed and overhead. The encryption and decryption operations add computational costs, primarily as time delays and additional resource consumption for decrypting and re-encrypting data.
When implementing database encryption at any level, you should understand the impact on database speed and its role in application performance. While encryption is essential, you should consider adding server resources to compensate for the additional processing load that encryption imposes on the system.
Types of Database Encryption
Database encryption is an umbrella term that includes several related and independent methods for safeguarding sensitive data contained in a database.
We’ll now discuss some examples of these methods.
Data-At-Rest Encryption
This encryption method safeguards data in the database’s persistent storage on disk or a similar physical medium.
When properly applied, Data-At-Rest Encryption ensures that critical information remains encrypted and unreadable even if an attacker acquires physical access to the database.
Full Disk Encryption (FDE) or Transparent Data Encryption (TDE) are two popular approaches used for data-at-rest encryption.
Both methods protect the database by prohibiting unauthorized users from directly accessing the data on the storage medium, ensuring data confidentiality and integrity at all times.
Disk Level Encryption
Full Disk Encryption (FDE), also known as disk-level database encryption, is a comprehensive data security approach that encrypts the entire database storage at the disk level.
The process guarantees that all data saved on the physical drive, including the operating system, database, and log files, is encrypted.
FDE secures data at rest, protecting it against unauthorized access, theft, and data breaches. The encryption doesn’t affect authorized applications and users since the encryption and decryption operations are transparent.
In the event of unauthorized physical storage access, encrypted data remains inaccessible since the hacker needs appropriate decryption keys to convert encrypted data into plaintext, ensuring data confidentiality and integrity.
Data-in-Transit Encryption
Data-in-Transit encryption is a database encryption method that protects data being transported between applications and the database server.
This method protects sensitive information from eavesdropping or interception as data is sent over networks. The process involves using protocols such as SSL/TLS, which encrypt and decrypt data packets as they travel between the client and server.
Data-in-Transit encryption protects data during transmission by adding an extra layer of security against man-in-the-middle attacks, unauthorized access, and data modification. As a result, data stays unreadable and intact throughout its trip between the application and the database.
How Does Database Encryption Work?
As mentioned earlier, database encryption works by encrypting plain text data with cryptographic techniques and encryption keys.
The process includes the following moving parts:
Data Encryption
When sensitive data is kept in a database, it undergoes encryption.
This process converts plaintext data into ciphertext using an encryption method such as the Advanced Encryption Standard (AES). This encryption technique is very secure since it operates on fixed-size data blocks.
Encryption Keys
An encryption key is a file containing a very long character string that an encryption algorithm uses to execute encryption and decryption operations.
There are two kinds of encryption keys: symmetric keys and asymmetric keys. Asymmetric encryption employs a pair of separate keys (public and private) for encryption and decryption, whereas symmetric encryption uses the same key for both encryption and decryption.
Proper Key Management
Any database encryption is as good as the key management process it employs. Encryption keys must be generated, kept, and managed securely to prevent unauthorized use. We highly recommend using industry-standard key management platforms to ensure secure access and use of encryption keys.
Data Storage
The ciphertext is also kept in the same database as the plaintext. DBMS offers several ways of securely storing this data. For instance, column-level encryption encrypts selected columns holding sensitive data while leaving the rest unaltered.
Data Retrieval
When the DBMS receives a data retrieval request, it checks the request credentials to verify its validity. Once verified, the DBMS uses the appropriate decryption key to decrypt the ciphertext. This data is then transferred to the data transmission method to send the data using Data-in-Transit methods.
Data Access Control
In addition to encryption, access control techniques are critical for limiting access to encrypted data. These methods ensure that only authorized individuals can use the decryption keys to access encrypted information.
Database Encryption Methods
Database encryption methods preserve the confidentiality and integrity of data contained in a database. Over the years, various vendors have developed various methods to encrypt data in the database. Let’s discuss some popular methods of data encryption.
Transparent Data Encryption (TDE)
TDE is a database encryption mechanism that automatically encrypts data at rest, making the operation invisible to applications and users.
During the process, TDE encrypts the entire database, including backups and log files, to ensure strict data privacy in the event of illegal access or theft.
Data is automatically decrypted during a data retrieval request, allowing apps and users to access the data without needing manual decryption.
API-based Decryption Methods
API methods are internal DBMS services or third-party platforms (or encryption libraries) that allow users to interact with encrypted data.
These services cover encryption and decryption processes, key creation and management, and data integrity checks.
Applications and processes use these approaches to save and retrieve encrypted data from databases. The API methods make it easier for developers to implement encryption in applications to ensure data stays unreadable without the correct decryption keys.
The Encryption/Decryption Plugins
The plugin technique refers to a modular approach to database encryption that integrates encryption features as external components into the database management systems.
Database administrators can add or uninstall these encryption plugins without requiring changes to the underlying database platform.
The plugin mechanism allows users to select the encryption algorithms and key management techniques that best meet their security needs. As a result, administrators can use various encryption standards and smoothly update or replace encryption features as needed.
The plugin method protects sensitive data without affecting the integrity and performance of the core database system.
Column-level Database Encryption
Column-level database encryption protects specific columns in a database table. It enables granular data protection by encrypting sensitive data while leaving other columns unprotected. This guarantees that authorized users with decryption access can see the encrypted data.
Symmetric Database Encryption
Symmetric database encryption processes use the same secret key for data encryption and decryption. It’s a simple and effective solution with minimum overheads. However, the main challenge in adopting this method is securely keeping and disseminating the secret key among authorized users.
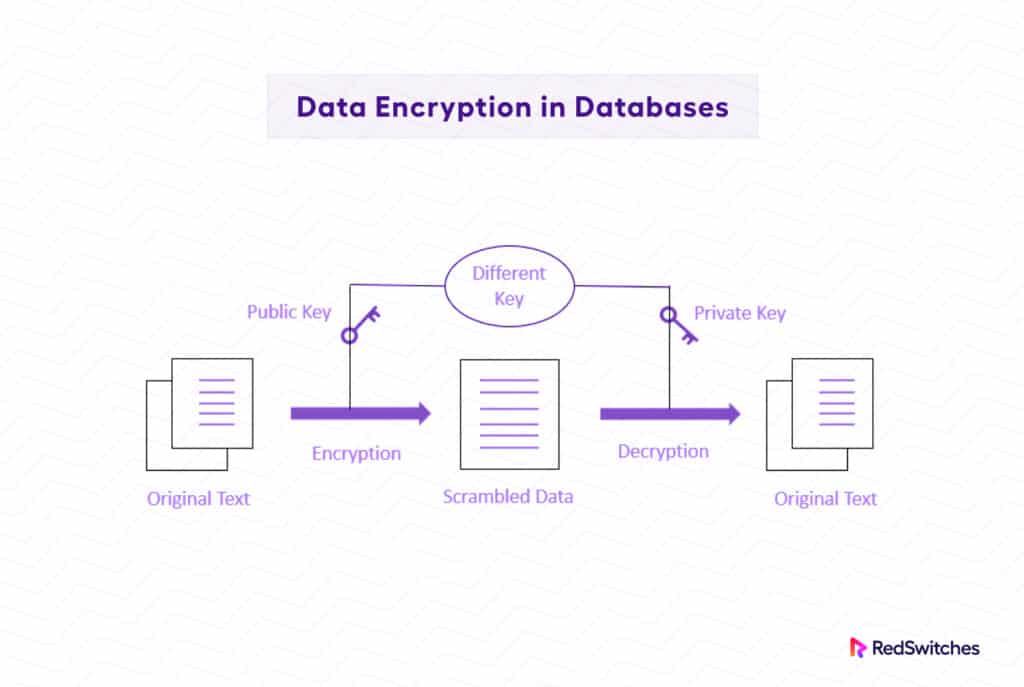
Asymmetric Database Encryption
Asymmetric database encryption, commonly known as public-key encryption, encrypts and decrypts data using a pair of public and private keys.
Data encrypted with the public key can only be decrypted with the associated private key, offering a more secure method of protecting sensitive data.
Asymmetric database encryption also solves the problem of managing key distribution by separating public and private keys.
Advantages and Disadvantages of Database Encryption
Now that you understand how database encryption works and how to set up and manage encrypted databases, let’s take a closer look at the benefits and drawbacks of the encryption process.
Advantages of Database Encryption
Database encryption brings a range of benefits to database operations, such as:
Robust Data Security
Encryption adds extra security to sensitive data stored in a database. It assures that even if unauthorized users access the database, the encrypted data remains unreadable and unusable without encryption keys.
Compliance with Data Privacy Regulations
Encryption is often the core requirement of data privacy and security standards compliance. Setting up and maintaining encrypted databases indicates a proactive attitude toward data protection as laid down in standards such as HIPAA, PCI DSS, and GDPR.
Defense Against Insider Threats
Encryption is a great way of protecting sensitive data from insider threats, where authorized personnel abuse their access privileges and leak sensitive data. Even if someone with access tries to view or copy encrypted data without sufficient authorization, the operation will fail, and the system administrators will be notified of the incident.
Secure Data at Rest and in Transit
Database encryption safeguards data at rest (while it is kept on storage media) and in transit (when it is transmitted). It protects sensitive data from one end to the other so that it remains protected during security incidents.
Increased Trust and Customer Confidence
Encryption displays a dedication to data security and privacy. It fosters trust and confidence among consumers, partners, and stakeholders by assuring them that their sensitive information is secure within the organization’s database.
Disadvantages of Database Encryption
Despite all the above advantages, encrypting databases can introduce challenges to business operations. Let’s discuss some critical challenges of encrypting databases.
Impact on Performance
The encryption and decryption operations might add overhead and thus impact database performance.
In most cases, encryption and decryption procedures require additional resources and time. This slows down the query response times and eventually affects user experience.
Complexity and Key Management
Encryption key management is complex, especially with huge databases supporting multiple remote users and processes.
Secure key storage, distribution, rotation, and access controls are all part of the key management process, and any lapse in this process significantly reduces encryption’s efficacy.
Limited Search and Analysis Capabilities
Without decryption, encrypted data is illegible, limiting the ability to execute searches, data analysis, and other database functions that access data.
Administrators must add multiple steps and dedicate additional resources to decrypt data to support data search and analysis processes.
Potential Vulnerabilities
Encryption is not infallible. Implementation problems, poor key management, corrupted systems, or side-channel assaults can introduce vulnerabilities that attackers can exploit. We highly recommend regular security audits, key rotation, and reassignment to address any possible vulnerabilities.
Increased Operational Costs
Implementing and maintaining a strong encryption solution may incur additional expenditures, such as purchasing encryption software and hardware, staff training, and managing encryption keys. Database administrators should carefully weigh the expense of encryption against the benefits of the secured data.
Before deploying database encryption, assessing your organization’s particular requirements and issues is critical. A thorough risk assessment and an awareness of the possible advantages and limits of encryption aid in determining the best way to safeguard your database.
Conclusion
Adopting database encryption is an important step in maintaining the security and integrity of sensitive data. Encryption adds an extra layer of security and protects against data breaches, illegal access, and insider threats.
Organizations may satisfy regulatory requirements, increase consumer confidence, and decrease the risks associated with data breaches by encrypting data at rest and in transit.
While some issues, such as performance impact and key management, may exist, the benefits of data confidentiality, regulatory adherence, and risk minimization exceed these problems. When paired with additional security measures, database encryption forms a holistic security strategy that strengthens the protection of valuable information.
RedSwitches, as a provider of secure and reliable bare metal hosting solutions, understands and prioritizes data encryption to maximize data security. By choosing RedSwitches, you opt for a secure infrastructure that values data security as strongly as you do.
FAQ’s
Q: What is data encryption?
A: Data encryption is a process that converts plain text, or unencrypted data, into cipher text, or encrypted data, to protect its confidentiality. Encryption ensures that only authorized individuals can access and read the data.
Q: Why is data encryption important?
A: Data encryption is important because it provides a secure mechanism for protecting sensitive information from unauthorized access. It helps prevent data breaches and ensures that even if data is intercepted, it cannot be read without the decryption key.
Q: What are the common types of data encryption methods?
A: The common types of data encryption methods include symmetric encryption, asymmetric encryption, column-level encryption, and application-level encryption.
Q: What is symmetric encryption?
A: Symmetric encryption is a type of encryption method where the same key is used for both encryption and decryption. It is faster than asymmetric encryption but requires secure key distribution.
Q: What is asymmetric encryption?
A: Asymmetric encryption, also known as public-key encryption, uses two different keys – a public key for encryption and a private key for decryption. It provides a more secure solution for key exchange between parties.
Q: What is column-level encryption?
A: Column-level encryption is a form of database encryption where specific columns within a database are encrypted. It allows for more granular control over data protection and is often used for protecting sensitive or personally identifiable information.
Q: What is application-level encryption?
A: Application-level encryption refers to encrypting data at the application layer before storing it in the database. It provides an additional layer of security and allows for greater customization in how data is encrypted and accessed.
Q: What are the advantages of data encryption?
A: The advantages of data encryption include protecting sensitive information, ensuring data confidentiality, compliance with data protection regulations, and safeguarding against data breaches.
Q: What are the disadvantages of data encryption?
A: Some disadvantages of data encryption can include increased overhead and processing time, dependency on secure key management, potential loss of data if encryption keys are lost, and the complexity of implementation and maintenance.
Q: Where is data encrypted within a database?
A: Data can be encrypted at different levels within a database, including at the column level, application level, or even at the file level. The specific encryption approach depends on the requirements and best practices followed by the organization.