Gone are the days when you used the traditional password authentication. Public key authentication with SSH has become the primary mode of securing access to remote servers.
This technique involves using a key pair for authentication to validate access to a remote server and run commands and applications. This approach is inherently better secure than passwords because of the security of the process of key-based authentication.
This tutorial will introduce SSH Public Key authentication and cover critical aspects such as how to create an SSH key pair and set up users to use SSH authentication.
Let’s start with an overview of how SSH authentication works.
Table Of Content
- How SSH Authentication Works?
- Benefits of Public Key Authentication in SSH
- How to Implement SSH Key Authentication
- Conclusion
- FAQs
How SSH Authentication Works?
The first step of the process is the generation of the SSH key pair. In Linux, you can use the popular ssh-keygen command.
A typical key pair consists of a private key and a public key. The user uploads the public key to the server and keeps the private key with the local application or system. During the initial authentication process, the server sends a message encrypted using the public key. The local system decrypts the message using the private key, verifying the user’s identity.
This key-based process (often protected by a secondary key password) offers more robust security than a regular password.
Benefits of Public Key Authentication in SSH
Utilizing public key authentication for SSH connections offers enhanced security. That’s why it’s often preferred over conventional password-based logins.
Enhanced Security of SSH Connections
SSh keys are typically 1024 bits long, making them significantly more secure than standard passwords. For even greater security, consider increasing the key length during generation.
Algorithmically Generated Complex Keys
The complexity of these keys, generated through sophisticated algorithms, makes them less predictable and more secure.
Restricted Access
In SSH authentication, access to the target server or services is limited to the device with the corresponding private key.
Server Privacy
The private key’s contents are never exposed to the server. Thus, the local machine remains secure even if a server is compromised.
Multi-Factor Authentication
Adding a passphrase to your private key introduces an additional layer of security.
How to Implement SSH Key Authentication
Now that you have a high-level view of SSH key-based authentication, let’s go into the details of setting up the SSH authentication process. Here are the prerequisites:
Prerequisites
Before diving into implementing and using SSH Public Key authentication, ensure you have the following:
- Access to a local computer and a remote server.
- You have an SSH client installed on your local machine.
- Basic familiarity with terminal or command-line interface.
The Process of SSH Authentication
SSH public key authentication involves the following straightforward four-step process:
Generate the Key Pair: Create a private and public key pair. The private key is stored securely on the local computer.
Upload the Public Key: Upload the public key to the server.
The Approval Step: The server then recognizes and approves the uploaded public key.
Access Verification: Access is granted only to users with the matching private key.
This method relies on the assumption that the private key is kept secure. Users can further enhance security by adding a passphrase. You can also use key management tools and follow the relevant best practices to automate the process and reduce the risks of the private key getting compromised.
Create an SSH Key Pair
Start by generating an SSH key pair on your local machine using OpenSSH.
For Linux and macOS Users
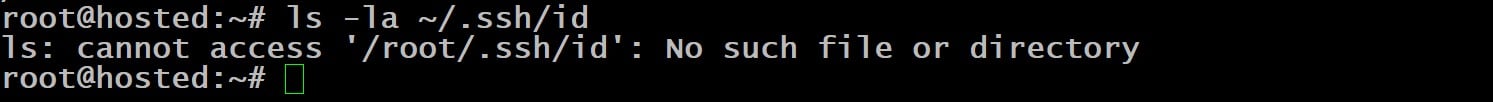
Open the terminal and confirm the presence of keys with the following command:
# ls -l ~/.ssh/id*
This command lists the directory’s contents if any keys are present. If no current keys are found, the output will suggest that the directory doesn’t exist.
This is an important step because creating new keys typically replaces existing ones by default. You can preserve the existing keys by specifying a unique name for the new keys to save them as new distinct files.
Create a directory with the mkdir command to store the new key pair:
# mkdir ~/.ssh
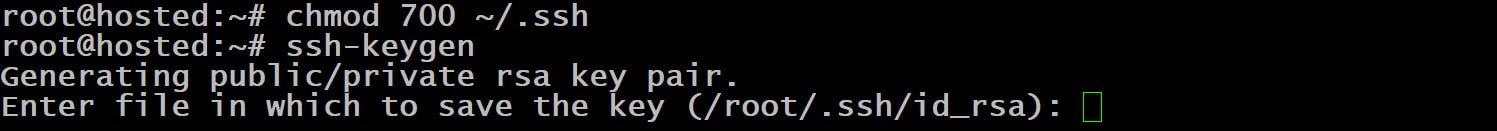
Set this directory permissions to 700:
# chmod 700 ~/.ssh
Now, start the key generation process with the following command:
# ssh-keygen
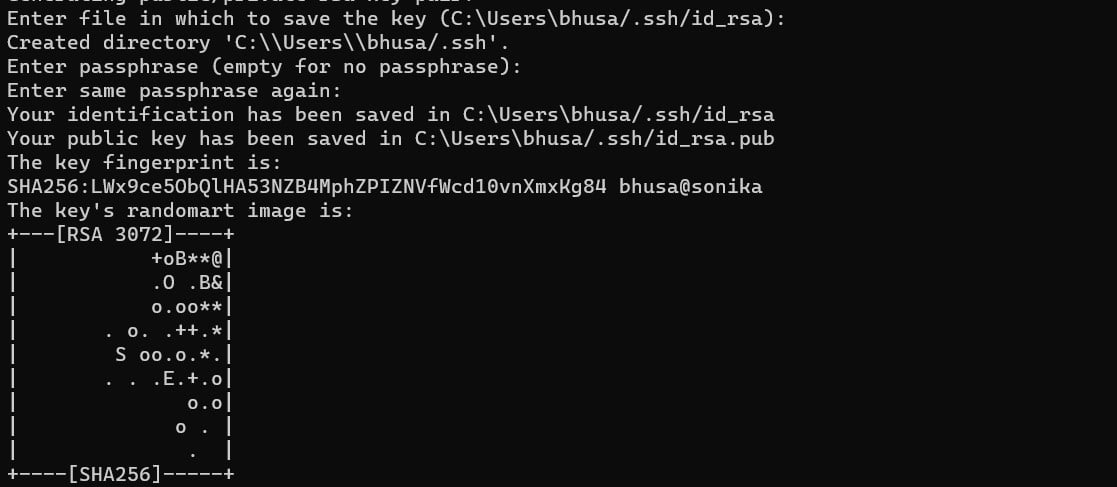
You’ll see a message confirming the command’s success. The system will then prompt you to choose a save location for the file.
The standard storage path for the key is /home/<username>/.ssh/id_rsa. If you wish to preserve existing keys, provide a different file name.
Alternatively, you can simply press Enter to use the default path. You should note that the process will overwrite existing key(s) in this location.
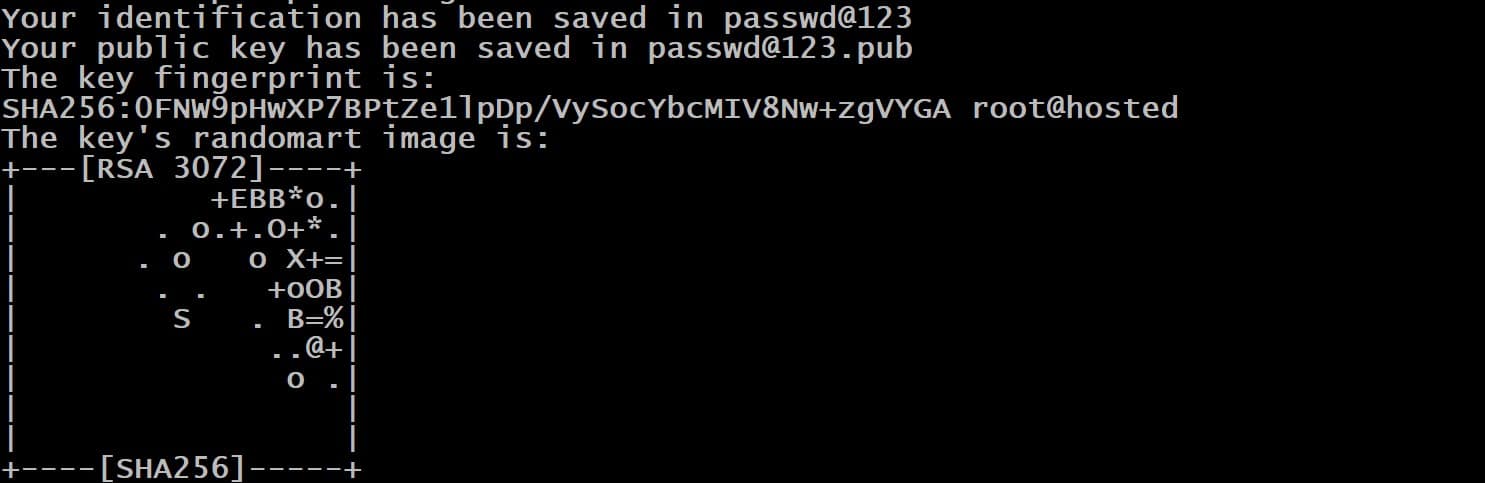
We strongly recommend securing the key by entering a passphrase. Hit Enter and re-enter the passphrase for confirmation. This passphrase is used whenever the key is used for authentication purposes.
The command displays details about the storage location. It also presents a digital and a graphical representation of the key in the console.
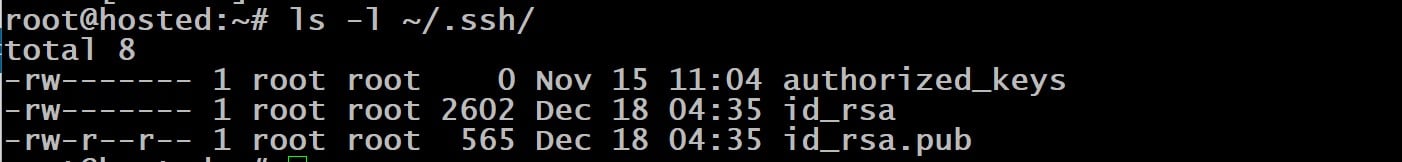
Finally, verify that the keys have been correctly placed in the directory by listing the contents with the following ls command:
# ls -l ~/.ssh/
The output will show two important files:
id_rsa: This is your private key.
id_rsa.pub: This file contains your public key.
For Windows Users
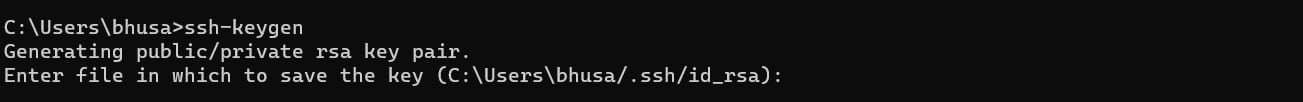
Launch the Command Prompt and enter the following command to initiate the key pair generation process:
# ssh-keygen
If you wish, specify a custom path for storing the keys. Otherwise, simply press Enter to save the keys at the default location.
If the location contains existing keys, a prompt will appear asking for confirmation to overwrite them. Select Y and hit Enter to continue the setup.
Enter a passphrase for additional security of the private key. Re-type the passphrase for confirmation and press Enter to finalize the process.
Set Up SSH/SFTP Users for Your Key
Once you have your key pair, the next step involves configuring SSH and SFTP users on the server to recognize the key. Generally, this process has the following four steps:
- Check the .ssh Directory on the Server
Run the following command in the terminal to see if the .ssh directory exists on the server:
# ls -l ~/.ssh/
If it doesn’t, create the directory using the following mkdir command:
# mkdir ~/.ssh
Then, set the proper permissions with chmod:
# chmod 700 ~/.ssh
- Create the authorized_keys File
In the .ssh directory, create a file named authorized_keys using the following command:
# touch authorized_keys
Then, adjust its permissions with
# chmod 600 ~/.ssh/authorized_keys
- Edit the authorized_keys File Using a Text Editor
Now, use a text editor to insert the contents of the public key into the file.
Place each key on a separate line for configuring multiple users or keys. When done, save and close the file.
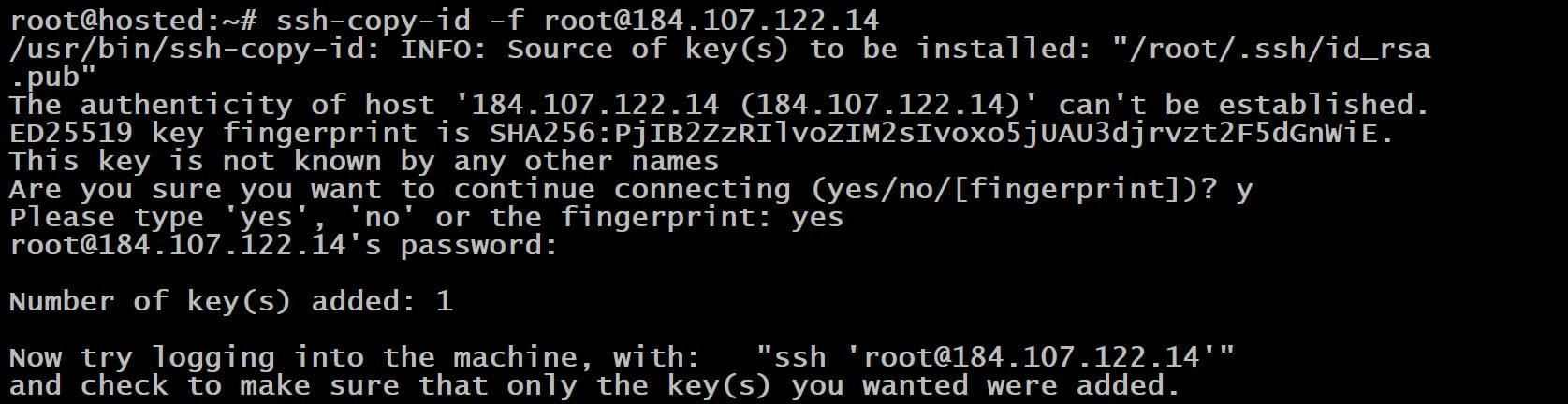
On Linux systems, streamline this process using:
# ssh-copy-id <username>@<host>
Once you type this command, it automatically copies the key.
The process displays the count of keys transferred to the server and additional guidance for the next steps.
Now, you need to move this file to the target server. For this, you can opt for one of the following options:
- Employ SSHFS for Linux, macOS, or Windows systems.
- Opt for RSync as an alternative on Linux platforms.
- Log In
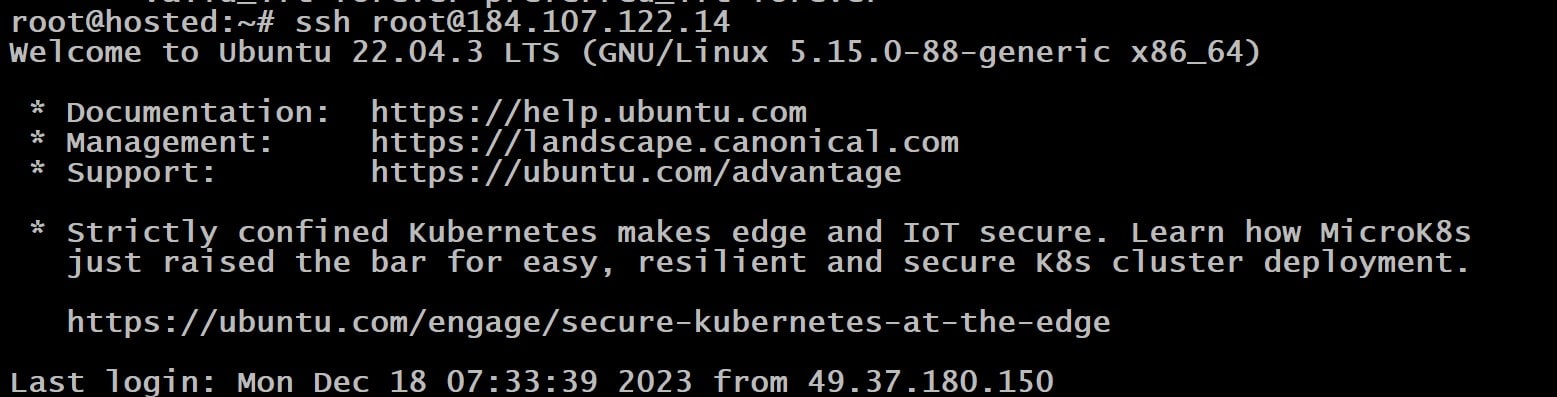
Once you’ve created and transferred the keys, access the server from the local machine with this command:
# ssh <username>@<host>
The command initiates a prompt requesting the password for the private key.
Enter the passphrase to unlock the key:
You will be granted access to the server through SSH upon successful verification.
Conclusion
Utilizing Public Key Authentication with SSH offers a robust and secure method for accessing remote server systems. By setting up a public-private key pair using the ssh-keygen command, users can significantly enhance the security of their remote host connections.
This method surpasses the traditional password-based authentication by integrating SSH key-pair authentication, which not only secures file permissions but also verifies the authenticity of the host.
RedSwitches helps customers by offering customizable bare metal servers.
If you’re searching for a reliable server infrastructure for your projects, we provide competitive, dedicated server pricing and ensure swift delivery, typically on the same day of order approval. Whether you require a dedicated server, a traffic-friendly 10Gbps dedicated server, or a high-performance instant dedicated server, we are your trusted hosting partner!
FAQs
Q. Can you explain SSH public key authentication?
SSH public key authentication refers to a secure login technique for servers, where a pair of cryptographic keys, rather than a traditional password, is used for authentication.
Q. How does SSH public key authentication differ from password authentication?
With SSH public key authentication, the user logs in with a private key corresponding . to a public key stored on the server, whereas with password authentication, the user logs in with a password.
Q. What are the steps to configure SSH public key authentication?
First, create an SSH key pair using the ssh-keygen command to configure SSH public key authentication. Following this, transfer your public key to the server’s ~/.ssh/authorized_keys file to complete the setup.
Q. What are the benefits of using SSH public key authentication?
SSH public key authentication offers enhanced security by using cryptographic keys, eliminating the risk of brute force attacks and providing additional security compared to password authentication.
Q. Can I disable password authentication and only allow SSH public key authentication on my server?
Yes, you can disable password authentication and only allow SSH public key authentication by modifying the sshd_config file on your server and setting the PasswordAuthentication option to no.
Q. What is the procedure for establishing a connection with a remote server using SSH and public key authentication?
When you want to establish a connection to a remote server using SSH public key authentication, you should use the private key file in your command. This is done by incorporating the -i option in the SSH command, formatted as follows: ssh -i [location_of_private_key_file] [username]@[remote_server_address].
Q. What is the process for adding my public key to a remote server for SSH public key authentication?
To add your public key to a remote server for SSH public key authentication, you can use the ssh-copy-id command, which automatically installs the public key in the appropriate location on the server.
Q. What should I do if I need to manage multiple SSH keys for different servers?
You can use the ssh-agent and ssh-add commands to manage multiple SSH keys and enable key-based authentication for connecting to different servers without re-entering the passphrase for each key.
Q. How do I ensure the file permissions of my SSH key pair are secure?
To ensure the file permissions of your SSH key pair are secure, you should set the correct permissions for the private key file (id_rsa) to 600 and for the ~/.ssh directory to 700.
Q. What is the recommended approach for key management and maintaining the security of SSH keys?
The recommended approach for key management and maintaining the security of SSH keys involves regularly rotating your key pairs, using strong passphrases for added security, and monitoring the access and usage of SSH keys.