Critical IT infrastructure is always under attack, and administrators need to find and patch security loopholes before cybercriminals can exploit them for their purposes.
That’s why, cybersecurity experts recommend sysadmins follow a systematic approach to finding vulnerabilities in their systems and fixing the issues. This approach is usually known as vulnerability assessment.
In this article, we’ll define the vulnerability assessment process and then go into the details of the process.
But before going into the specifics, here’s a bird’s eye view of this idea.
In technical terms, a vulnerability assessment methodically examines an information system’s security flaws. The process helps determine whether the system is vulnerable to known vulnerabilities, assigns classification (severity levels) to those vulnerabilities, and advises mitigation strategies and fixes, where necessary.
With this overview, let’s go into the details of the process.
Table Of Content
- What is a Vulnerability Assessment?
- The Importance of Vulnerability Analysis
- Types of Vulnerability Assessments
- A Template for Organization-wide Vulnerability Assessment Process
- Vulnerability Assessment Tools
- Conclusion
What is a Vulnerability Assessment?
The process of finding and analyzing security vulnerabilities in an ICT system, network, application, or organization’s IT assets is known as vulnerability assessment.
The evaluation often involves using several tools and techniques to discover “holes” and issues that attackers could exploit to jeopardize the confidentiality, integrity, or availability of the system’s or organization’s data or resources.
Examples of risks that vulnerability assessment can discover and avert include:
- SQL injection, XSS, and other code injection attacks.
- Privilege escalation in case of improper authentication techniques.
- Unsafe defaults – software with potentially unsafe settings, such as guessable administrator passwords.
- Unauthorized access that can result in data breaches and theft of sensitive information.
- Malicious software (malware) can infect the organization’s computer systems, servers, and other devices.
- Denial of Service (DoS) attacks can cause disruption of your online services.
The Importance of Vulnerability Analysis
Before understanding the steps and the importance of vulnerability analysis. Let’s see some technical challenges and user behaviors that can facilitate hackers in exploiting vulnerabilities in an organization’s ICT infrastructure:
- Breaches occur when organization members mistakenly reveal information or purposefully leak information to an external source (aka malevolent insiders).
- Unencrypted data on lost or stolen devices is an often-overlooked way cybercriminals use to intrude into a company’s network.
- Cybercriminals can install abusive malware on target computers to exfiltrate data or take control of computing systems.
Organizations can protect their assets by setting up vulnerability management that minimizes the opportunities for data leaks and breaches. However, these processes demand constant vigilance and entail completing periodic vulnerability assessments that overlap in assessment and execution cycles – once one is finished, another must begin.
Internal security teams can use vulnerability assessments to find, categorize, analyze, report, and repair security flaws in business applications, operating systems, endpoint devices, and browsers.
Since dozens of new vulnerabilities are discovered every year, businesses need to adopt a comprehensive vulnerability assessment protocol to safeguard their networks, apps, and operating systems.
This protocol is based on an organization-specific vulnerability management system. This system follows a multi-step process that prioritizes vulnerability fixes, ensuring that high-risk vulnerabilities are addressed first. These vulnerability management steps cover the methods and tools required to identify and address the most critical vulnerabilities regularly.
Types of Vulnerability Assessments
Now that you know the theory behind vulnerability assessment, let’s go in a little more depth into the types of vulnerability assessments:
Host Assessment
Evaluates crucial servers that may become targets if insufficiently tested (physical servers) or not produced from a tested and verified machine image (virtual servers).
Network and Wireless Assessment
Assess policies and procedures for preventing unauthorized access to personal or public networks and resources that can be accessed over networks.
Database Assessment
Examines databases or large data systems for flaws and incorrect setups, discovering “unsafe” databases and development and testing environments. The process also categorizes sensitive data throughout an organization’s infrastructure.
Application Scans
Helps find security flaws in web applications and their source code through automated frontend static/dynamic source code or scan analysis.
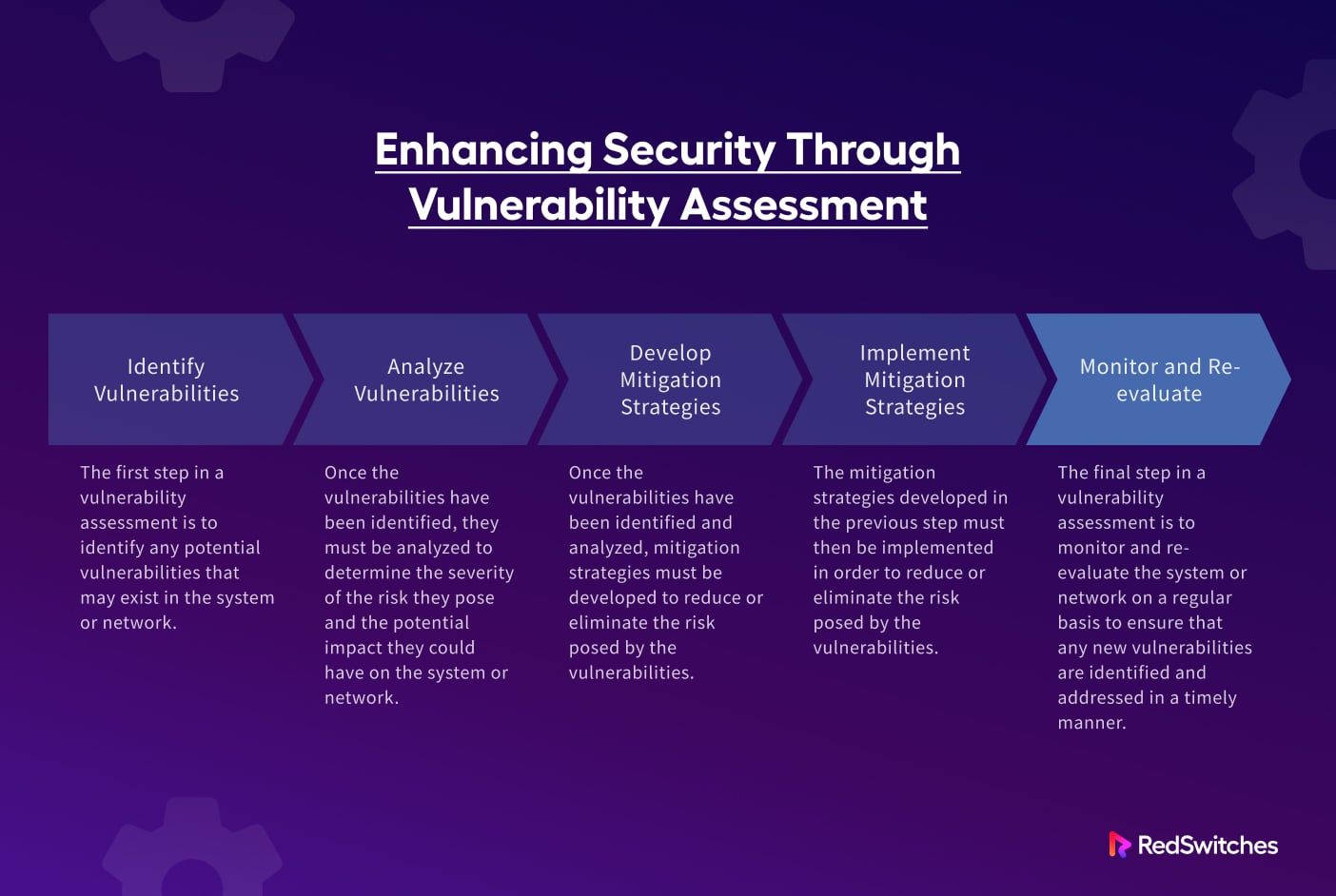
A Template for Organization-wide Vulnerability Assessment Process
Since every organization has a different set of ICT infrastructure and operational security requirements, there is no single process that applies to all organizations.
We strongly recommend that the organization’s IT security teams should come up with an internal vulnerability assessment process that covers all the unique use cases and known security loopholes to ensure complete protection for all organizations’s ICT assets.
A comprehensive vulnerability assessment process should include the following stages.
Initial Planning
This is the pre-process stage, where the team decides the goals and scope of vulnerability testing. Usually, the team covers the following points and requirements:
- Identification and mapping of all endpoints and protected assets.
- Determine the business worth of each asset, the consequences of an attack, and the potential cost of damage to the assets.
- Identify and document all system control access and other security requirements.
- Identify the system assets that store sensitive data and how this data is transmitted between system components.
- Create a baseline of protected assets, services, procedures, and open ports.
- Identify the operating systems and software installed on assets.
The outcome of this stage is a detailed report on the current state of the security of the organization’s ICT assets. The security teams have a clear understanding of the exposed attack surfaces, probable threat scenarios, and a starting point for the next stage.
Test for Vulnerabilities
Now that the team has mapped the organization’s ICT infrastructure, the next step is to test for vulnerabilities.
The team uses both automated and manual tools to scan all devices and software components. In most cases, automated software in the initial pass flags potential vulnerabilities. The team uses manual tools and processes to check and verify these in the second pass.
During the process, the teams often rely on one or more vulnerability databases, threat Intelligence feeds, and vendor security advisories to better assess the threats to the system.
Depending on the size of the ICT infrastructure, and the intricacies of the scans, this stage can take anywhere from a few hours to a couple of days.
Catalog and Prioritize Vulnerabilities
The team now has a list of vulnerabilities that can compromise the assets. However, all vulnerabilities are not equal in their impact on the systems’ security, and the team now needs to prioritize them in order of impact.
An important task at the start of this stage is to identify and remove false positives to minimize the workload and reduce the efforts required to secure the assets.
While prioritizing the vulnerabilities, the team should evaluate all potential issues on the following questions:
- The severity rating in a database of vulnerabilities
- The financial impact of exploiting the vulnerability
- The impact of sensitive information leaking out
- The simplicity of using the weakness
- How long has the vulnerability existed?
- The accessibility to a patch and the time required to install it
Make a Vulnerability Assessment Report
At this point, the team prepares a comprehensive report outlining all vulnerabilities, a classification of the threat posed by a specific vulnerability, and a potential fix for the situation.
For high-risk and medium vulnerabilities, the report should include information on the vulnerability, when it was identified, which systems it affects, the potential impact if attackers exploit it, and a strategy to fix the situation before it can turn into a disaster.
In the case of critical vulnerabilities, the team should also give a proof of concept (PoC) illustrating how each critical vulnerability could be exploited.
Continuous Vulnerability Evaluation
ICT assets of an organization are evolving and changing to keep pace with the changes in business requirements, upgrades, and deprecations.
A vulnerability scan only uncovers vulnerabilities in an organization’s digital infrastructure at a specific point in time. New configuration changes, deployments, newly discovered vulnerabilities, and other factors can all result in the introduction of new vulnerabilities. As such, the organization’s vulnerability management process should be an ongoing activity to ensure that the security teams are well aware of the challenges in protecting the ICT infrastructure.
A good example of the requirement for continuous vulnerability scans is the security requirements for CD/CI pipelines.
As a simple precaution, these processes should include automated vulnerability assessment components. These components can flag vulnerabilities as they’re discovered. This allows the teams to correct processes to remove the security loopholes as early as possible.
An important outcome of this continuous activity is the reduction in the costs of distributing fixes for insecure code.
However, because this method can’t cover the detection of all vulnerabilities (especially those that might occur in legacy or third-party systems), it must be supplemented by continuous vulnerability scans of production systems.
Vulnerability Assessment Tools
A vulnerability scanning tool is the most important component of the vulnerability test process. This tool should be able to perform a variety of scans, including:
- External vulnerability assessments
- Internal vulnerability assessments
- Scans of the environment
Several popular Vulnerability Assessment tools include QualysGuard, OpenVAS, Microsoft Baseline Security Analyzer (MBSA), and Acunetix.
When selecting a vulnerability scanning tool, consider the following factors:
- Quantity and quality of vulnerabilities, including minimizing false positives and false negatives. Elimination of false positives
- Actionability of results
- Time between updates
- Integrations with the current IT security technologies (SIEM, patch management, etc.)
Conclusion
We reviewed the fundamentals of vulnerability assessment, the essential techniques for identifying vulnerabilities, and a 5-step procedure for managing vulnerability assessments in your organization.
The continuous vulnerability assessment process should be viewed as a roadmap for strengthening the organization’s security and reducing the chance of a security breach.
FAQ:
Q. Why is a vulnerability analysis crucial?
A vulnerability assessment is crucial because it enables organizations to find potential security flaws before attackers can exploit them. Organizations can overcome the risk of a security breach and safeguard their assets and data by addressing these vulnerabilities.
Q. What distinguishes a penetration test from a vulnerability assessment?
A penetration test aims to break into a system by simulating an attack and using known weaknesses. The security posture of a system is broadly assessed by a vulnerability assessment.
Q. Which tools are used in vulnerability assessments?
Vulnerability testing is assessed by deploying a varied toolkit that includes tools such as network scanners, vulnerability scanners, port scanners, and penetration testing frameworks.
Q: How frequently should a vulnerability assessment be performed?
A: The frequency of vulnerability assessments is determined by various criteria, including the size and complexity of the organization’s systems and the nature of the data to be secured. However, it is generally recommended that vulnerability assessments be performed at least once a year or more frequently if significant changes to the systems or network occur.