The healthcare industry was shaken by the notorious CommonSpirit cyber attack in 2022, a ransomware incident that captured widespread attention.
It sparked serious concerns regarding safeguarding sensitive patient data within healthcare service delivery operations.
In this article, we’ll discuss the intricacies of the attack, explore its aftermath, and then list down valuable insights and lessons you can apply to enhance cybersecurity measures for your business.
Table Of Contents
- An Overview of CommonSpirit Health
- The CommonSpirit Cyber Attack
- The CommonSpirit Health Cybersecurity Incident: A Timeline
- Affected Parties in the CommonSpirit Ransomware Attack
- Compromised Data During the CommonSpirit Health Ransomware Attack
- Prevention Methods: Lessons Learned from the CommonSpirit Health Cyber Attack
- Ransomware Attacks in the Healthcare Sector
- The Impact of Ransomware Attacks on Healthcare Providers
- Proactive Preventive Steps for Healthcare Organizations
- Conclusion
- FAQs
An Overview of CommonSpirit Health
CommonSpirit Health, formed in 2019 through the merger of Dignity Health and Catholic Health Initiatives (CHI), is a leading nonprofit healthcare system in the US.
Committed to compassionate care, they operate across 21 states, serving millions of patients annually. Their mission is to provide exceptional healthcare, address community needs, promote social justice, and improve well-being through various medical services, preventive care, and innovative collaborations.
The CommonSpirit Cyber Attack
In October 2022, CommonSpirit Health, the second-largest nonprofit hospital chain in the United States, experienced a severe ransomware attack.
The incident affected several hospitals and care sites, leading to disruptions in patient care and subsequent significant financial losses.
Let’s start the analysis of the CommonSpirit ransomware attack and how the impact of the incident affected the stakeholders.
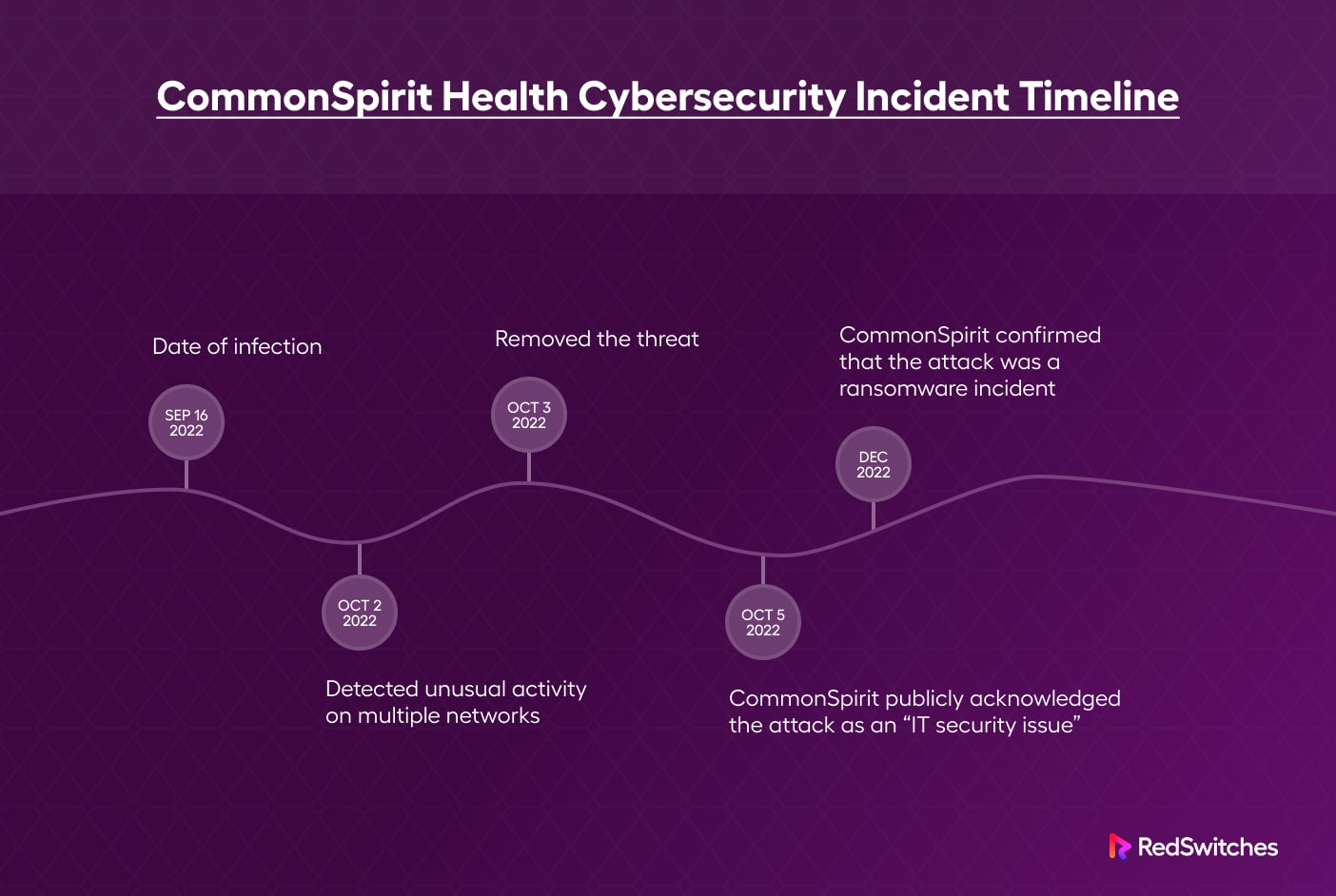
The CommonSpirit Health Cybersecurity Incident: A Timeline
Timeline analysis is the first step in understanding any cyberattack. Here’re the most significant incidents that unfolded during the attack.
- October 2, 2022: CommonSpirit’s security team detected unusual activity on multiple networks. In response, they enhanced network security measures, took systems offline to contain the threat, and brought in external cybersecurity experts to investigate the incident.
- October 5, 2022: CommonSpirit publicly acknowledged the attack as an “IT security issue” without mentioning ransomware. The organization did not comment on whether the attackers accessed patient information or health data.
- December 2022: CommonSpirit confirmed that the attack was a ransomware incident, with threat actors infiltrating parts of the network between September 16 and October 3. During this period, the attackers accessed the confidential personal data of patients who received care at Franciscan Health, a 12-hospital affiliate of CommonSpirit Health.
As of March 2023, the healthcare provider has not identified the specific ransomware or the group responsible for the attack. Unsurprisingly, no criminal organization has claimed responsibility for the attack.
Affected Parties in the CommonSpirit Ransomware Attack
The CommonSpirit ransomware incident primarily impacted seven Franciscan Health hospitals in Washington state and the associated physician clinics. These facilities include:
- St. Anne Hospital (Burien)
- St. Michael Medical Center (Bremerton & Silverdale)
- St. Joseph Hospital (Tacoma)
- St. Francis Hospital (Federal Way)
- St. Anthony Hospital (Gig Harbor)
- St. Elizabeth Hospital (Enumclaw)
- St. Clare Hospital (Lakewood)
In addition, the following healthcare installations experienced indirect effects of the attack:
- Seattle-based Virginia Mason Franciscan Health providers
- MercyOne Des Moines Medical Center
- CHI Health facilities in Nebraska and Tennessee
- Houston-based St. Luke’s Health
- Michigan-based Trinity Health System
Compromised Data During the CommonSpirit Health Ransomware Attack
During the CommonSpirit Health cyber attack, hackers accessed the personal data of 623,774 patients and the information of their family members and caregivers.
In particular, the compromised data included the following:
- Names
- Addresses
- Phone numbers
- Dates of birth
- Unique internal IDs used by the organization (not Medical Record Numbers or insurance IDs)
Though CommonSpirit claims no evidence of data misuse, the exposed information is commonly used for identity theft. If attackers could get the data out, the effects of this breach might persist for years.
Prevention Methods: Lessons Learned from the CommonSpirit Health Cyber Attack
Organizations should learn from the CommonSpirit ransomware incident and implement preventive measures to avoid becoming victims of similar attacks.
Here are the lessons we learned by going through the CommonSpirit ransomware incident.
Strengthen Network Security
Implement network segmentation, stricter access controls, intrusion detection systems, and zero-trust security measures to minimize the risk of security breaches.
Improve Incident Response and Disaster Recovery Plans
Efficiently restore operations by developing comprehensive plans for responding to cybersecurity incidents. Test the plans to ensure you can recover with minimum downtime.
Enhance Phishing Defenses
Invest in email security and employee security awareness training to identify and prevent phishing attempts. Remember that most ransomware attacks originate from successful phishing attacks.
Implement At-rest Encryption
Use encryption at rest to protect stored data, making it inaccessible to attackers even if they manage to exfiltrate it. The at-rest encryption might add a slight performance overhead as data needs to be decrypted when its state changes. However, it’s a small price to pay for enhanced security in the longer run.
Seeking Third-party Expert Support ASAP
Engage external cybersecurity specialists to supplement in-house expertise early during the attack. This becomes more important if your team lacks the necessary skills to prevent or mitigate ransomware attacks.
Ransomware Attacks in the Healthcare Sector
Ransomware attacks frequently target healthcare providers. Hospitals, in particular, remain a common target for cybercriminals due to their high-value data and often inadequate security measures.
Key statistics demonstrate that the threat of ransomware attacks in the healthcare industry is real.
- Approximately 66% of all US hospitals experienced a ransomware attack at some point in 2022.
- Two-thirds of healthcare IT professionals reported a significant cybersecurity incident within the past 12 months.
- The average recovery time for healthcare providers following a ransomware attack was one week in 2022, slightly lower than the 6.2 days reported in 2021.
The Impact of Ransomware Attacks on Healthcare Providers
CommonSpirit ransomware attack is just the latest in ransomware attacks on healthcare providers.
The results include operational disruptions, financial losses, reputational damage, and potential legal repercussions.
The CommonSpirit cyber attack, for example, resulted in an estimated $150 million in losses, including the cost of restoring IT systems and lost revenue from business interruption.
Additionally, CommonSpirit is facing a class-action lawsuit alleging negligence in the ransomware attack. A patient from Washington State filed the lawsuit, accusing the provider of failing to exercise reasonable care and increasing patients’ risk of identity theft.
Proactive Preventive Steps for Healthcare Organizations
CommonSpirit ransomware attack is a great learning opportunity, especially for healthcare organizations.
During this study, we extracted the following action items organizations should adopt to protect against ransomware attacks. As you’ll see, the list covers pre-attack preventive steps and post-attack recovery.
- Assess current cybersecurity posture and identify vulnerabilities that could help initiate ransomware attacks.
- Implement robust security measures, including network segmentation, intrusion detection systems, and at-rest encryption.
- Regularly update software and hardware to patch for known vulnerabilities
- Train employees on cybersecurity best practices and how to identify phishing attempts
- Develop and periodically update incident response and disaster recovery plans
- Collaborate with external cybersecurity experts to supplement in-house expertise
Conclusion
The CommonSpirit cyber attack is a stark reminder of the potential consequences of ransomware incidents in the healthcare sector. By analyzing the events surrounding the breach and the resulting fallout, organizations can learn valuable lessons and implement preventive measures to protect themselves from similar attacks in the future.
Strengthening cybersecurity measures, training employees, and developing comprehensive plans for incident response and disaster recovery are crucial steps in safeguarding against ransomware and other cyber threats.
FAQs
Q-1) When did the cyber attack on CommonSpirit occur?
According to the official announcements, the ransomware attackers accessed CommonSpirit Health’s network from September 16 until October 3, 2022.
Q-2) What type of cyber attack did CommonSpirit experience?
CommonSpirit confirmed that the incident was a ransomware attack.
Q-3) What data or information was compromised during the CommonSpirit cyber attack?
The attackers were able to get information that could identify patients and could be used in identity theft scenarios. Specifics include date of birth, full name, address, and phone number(s).