Key Takeaways
- Implement cutting-edge security technologies and protocols to safeguard server-based staking from sophisticated cyber threats.
- Use artificial intelligence and machine learning for real-time anomaly detection and predictive threat modeling.
- Prepare for future technological challenges by adopting encryption methods that can withstand potential quantum computing threats.
- Enhance security and privacy by implementing decentralized identity solutions for user authentication.
- Develop and maintain enhanced governance models that ensure transparency and efficiency in response to security incidents.
- Deploy hardware security modules (HSMs) and trusted execution environments (TEEs) for robust physical and cryptographic security.
- Maintain high-security standards through rigorous compliance with international regulations and continuous security audits.
Server-based security for crypto staking operations is a requirement in the ever-changing world of cryptocurrencies. Staking cryptocurrency is growing in popularity, making it more vulnerable to advanced cyberattacks. The enormous stakes make strengthening these digital fortifications more critical than ever. This article covers in-depth security techniques that can protect your staking dedicated servers from even the most crafty opponents. We’ll examine how to respond to threats and stay one step ahead of them, covering everything from network security fundamentals to cutting-edge defensive solutions.
Come along as we discuss the intricate details of protecting your cryptocurrency holdings and ensuring the profitability of your investment.
Table Of Contents
- Key Takeaways
- What is Staking?
- Importance of Security in Staking
- Security Principles for Server-Based Staking
- Security For Crypto Staking: Principle of Least Privilege (PoLP)
- Security For Crypto Staking: Endurable Authorization and Authentication
- Security For Crypto Staking: Data Encryption
- Security For Crypto Staking: Thorough Auditing and Monitoring
- Security For Crypto Staking: Frequent Penetration Testing and Security Audits
- Advanced Security Measures
- Security For Crypto Staking: Behavioural Analytics and Anomaly Detection
- Security For Crypto Staking: End-to-End Encrypted Communication (E2EE)
- Security For Crypto Staking: Hardware Security Modules
- Security For Crypto Staking: Zero Trust Architecture
- Security For Crypto Staking: Secure Software Development Lifecycle (SSDLC)
- Security For Crypto Staking: Decentralized Identity Verification
- Decentralization and Security
- Security For Crypto Staking: Blockchain’s Decentralisation Concept
- Security For Crypto Staking: Enhanced Security via Redundancy
- Security For Crypto Staking: Resistance to Censorship and Tampering
- Security For Crypto Staking: Minimizing the Effect of Localized Attacks
- Security For Crypto Staking: Difficulties with Decentralization
- Mitigation Measures
- Real-Time Monitoring Tools and Techniques
- Future Trends in Staking Security
- Conclusion
- FAQs
What is Staking?
Credits: Freepik
A key idea in blockchain technology and cryptocurrencies is staking. It lets users profit from their investments while making the network more secure and stable. It is widespread in blockchain networks that employ Proof of Stake (PoS) or one of its variations as a consensus method.
Bitcoin and other networks use proof of work, which is energy-intensive. In contrast, Proof of Stake depends on the quantity of cryptocurrency that participants are willing to “stake” as collateral. It does not depend on computational work. Proof of stake uses the stake to create new blocks and maintain security. These users are called validators. They are chosen based on many criteria, including their stake size and investment duration. They use their position to build new blocks and validate transactions.
People are drawn to staking because it lets you earn passive income from cryptocurrency holdings. Transaction fees and extra cryptocurrency come from the network’s inflationary policy. They are given to validators as rewards. They get this pay in exchange for the resources they use to maintain network operations. This includes running dedicated servers and updating software. It also includes the opportunity cost of locking up their tokens.
Staking additionally enhances the blockchain’s security. Because they are paid to protect the network, they risk losing a lot of their own coin. Their staked and maybe earned tokens could drop dramatically if the network were compromised. This alignment keeps the network safe. It also makes it effective. It removes the need for heavy processing.
Importance of Security in Staking
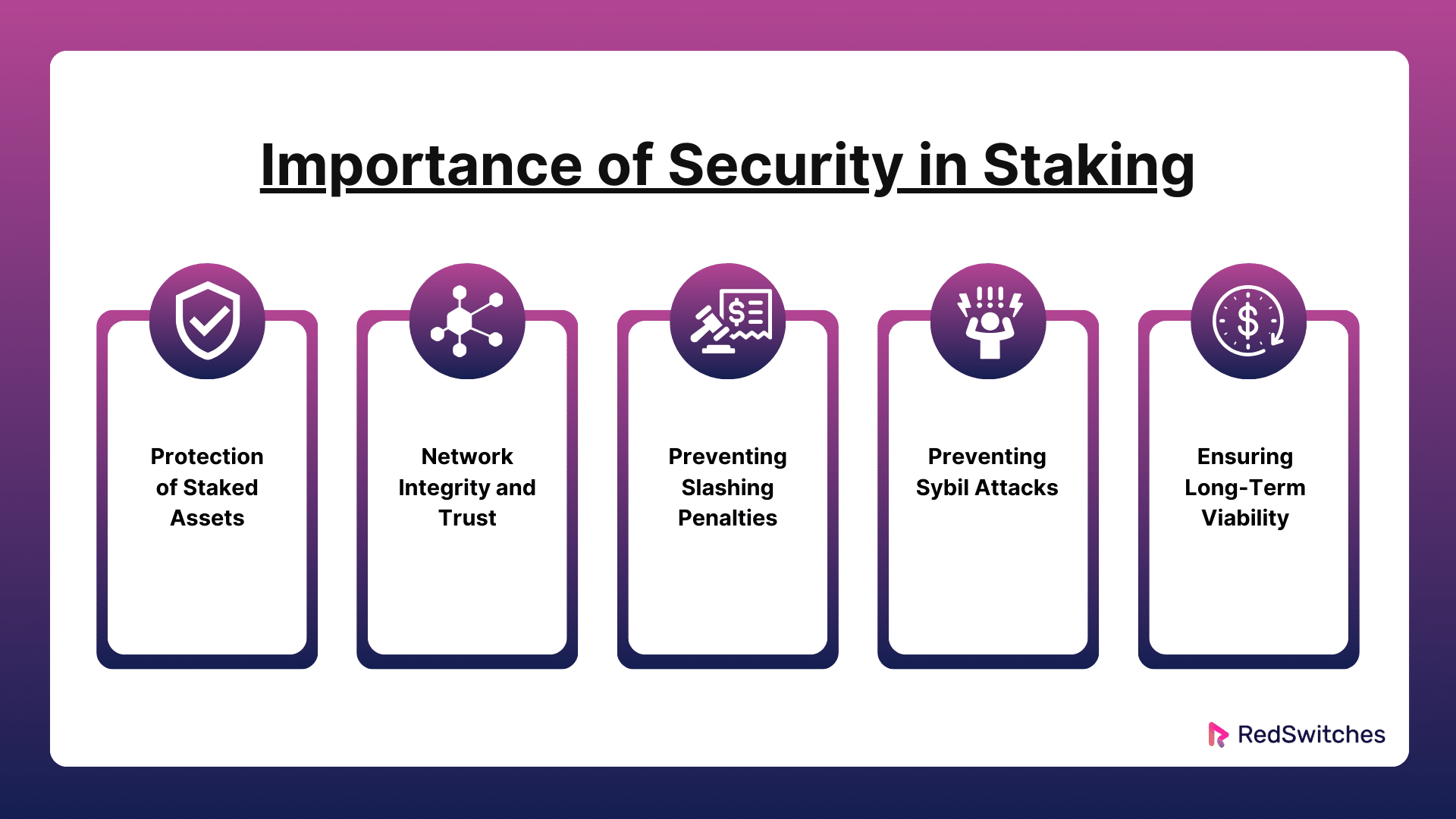
Blockchain networks rely on the efficiency of their staking processes. Their integrity and resilience depend on this. So, security in staking is critical. Security is essential for staking for the following principal reasons:
Security For Crypto Staking: Protection of Staked Assets
When users choose to stake their cryptocurrencies, many of their virtual assets are committed to the network. The assets are locked up and cannot be sold or exchanged while staking. Cyber risks include phishing scams, hacking, and other frauds. They aim to defraud people and could target these assets. Strong encryption, multi-factor authentication, and safe key storage protect these assets from illegal access. They also cut the risk of cyber theft. Also, continuous monitoring and quick response are critical. They help find and stop threats before they can harm the staked assets.
Security For Crypto Staking: Network Integrity and Trust
A blockchain crypto network’s decentralized structure and the immutability of its data form its fundamental basis. Validators are essential to a staking mechanism because they process transactions and create new blocks. The ramifications could be dire if the security of one or more validators was breached. Malevolent entities may modify transaction information, permit duplicate expenditure, or obstruct the generation of blocks, resulting in network outages or splits. These kinds of instances have the potential to seriously damage user confidence and trust, which could lead to significant disruptions in network activity and a decline in the market value of the cryptocurrency.
Also Read Blockchain Protocols and Proof of Stake (PoS) Mechanisms
Security For Crypto Staking: Preventing Slashing Penalties
Slashing penalties in Proof of Stake (PoS) networks act as a disincentive for validators to act carelessly or improperly, ensuring that validators have a stake in the network’s ongoing, proper operation. But even well-meaning validators may be penalized if their security protocols are compromised, resulting in actions that seem nasty, such as double-signing or the validator node going offline. Putting in place thorough security procedures helps prevent these situations, shielding validators from possible violations that can result in expensive fines. By doing this, the validator’s stake is protected, and their reputation is likewise guaranteed.
Security For Crypto Staking: Preventing Sybil Attacks
The fairness and decentralization of blockchain networks are seriously threatened by Sybil attacks, which include the attacker’s creation of multiple false identities in an attempt to obtain disproportionate control over the network. Effective staking security procedures enforce substantial financial obligations from validators, making it economically impossible for a single party to own enough stakes to carry out such assaults. Maintaining a decentralized and democratic validation process is crucial to prevent one member from exerting undue influence over the network. This safeguards the network against manipulation and guarantees that its decisions are based on the agreement of a wide range of stakeholders.
Security For Crypto Staking: Ensuring Long-Term Viability
Blockchain networks’ growth and sustainability mainly depend on their security. It is essential to ensure that these networks are safe from present and future dangers as they increasingly integrate into financial institutions. Investors and consumers will find a network with robust security protocols more appealing since they will feel more comfortable investing their money and faith in it. Additionally, a secure network is more likely to draw application developers, who enhance the ecology of the network and spur additional adoption.
Security Principles for Server-Based Staking
In blockchain tech, security is critical. It’s the cornerstone of a strong defense for server-based staking. The guidelines are meant to protect the network’s dependability and the security of members’ investments. They guard against threats to the network from both inside and outside. Here is a thorough examination of these fundamental security concepts:
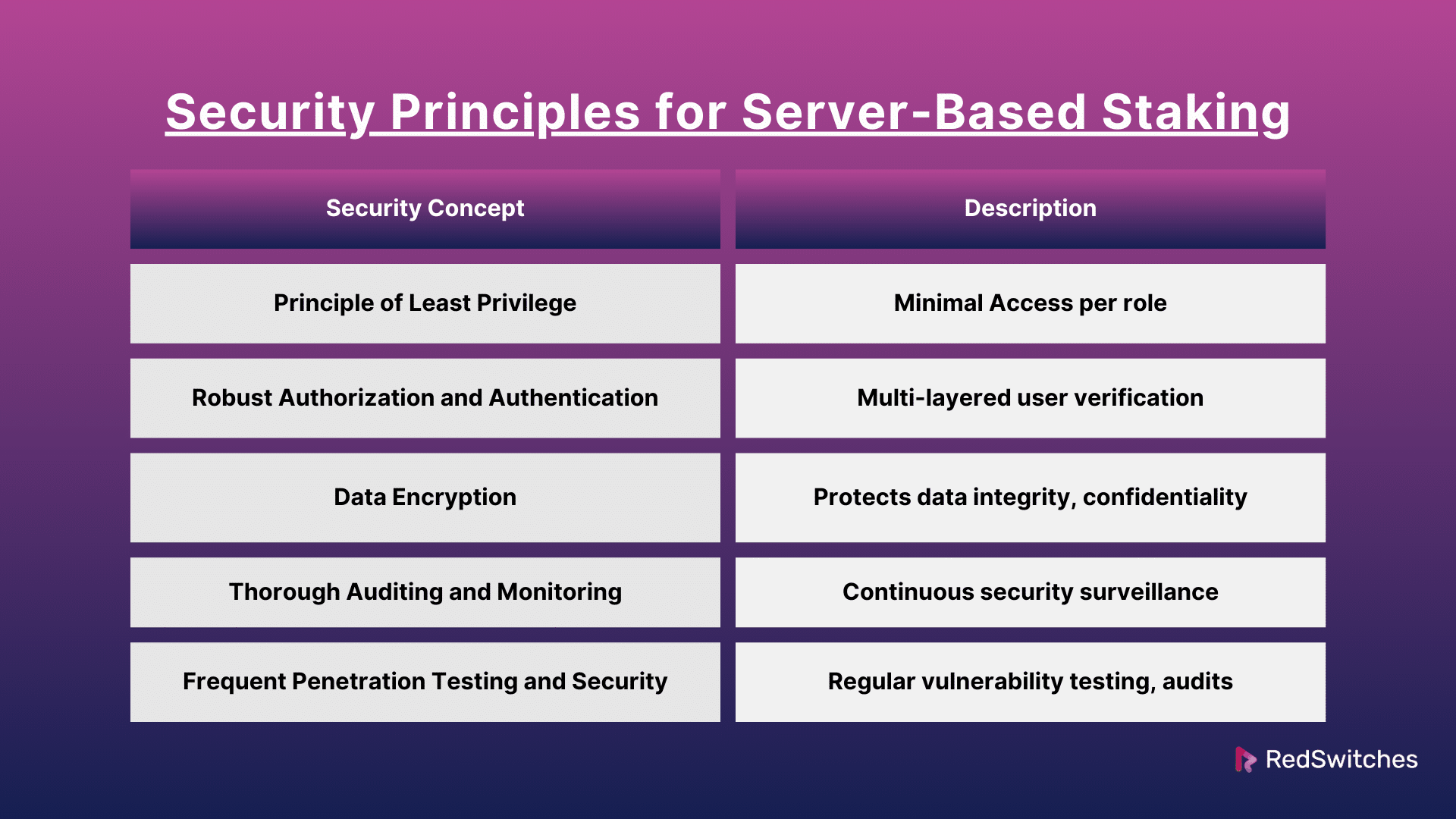
Security For Crypto Staking: Principle of Least Privilege (PoLP)
Using the PoLP guarantees that no user or component in the staking environment has extra access. They only have the permissions needed to function. This lowers the danger of insider threats and limits possible damage in the event of a security breach. Roles and access permissions must be well-defined and strictly regulated for server-based staking. For example, the accounts in charge of software upgrades shouldn’t access transaction processing and wallet management features. Access credentials should also be reviewed and adjusted regularly to stay on top of any changes in responsibilities or operational requirements.
Security For Crypto Staking: Endurable Authorization and Authentication
A robust authentication system is your first line of protection against unwanted access. More authentication steps are needed. These steps include hardware security keys or biometric verification. They should be added to multi-factor authentication (MFA) in server-based staking. This is where people keep significant financial assets. It limits user actions by their responsibilities. Role-based access control (RBAC) also links actions to accounts, which improves accountability. Users need regular training and updates. These ensure that they know their duties and the value of security procedures.
Security For Crypto Staking: Data Encryption
Encryption vitally protects data integrity and confidentiality. In server-based staking, config files and logs hold sensitive data. They should be encrypted, as should wallets and backup keys. Robust encryption mechanisms, such as TLS 1.3, should be implemented for transit data. It is recommended that these protocols be updated regularly to address new cryptographic flaws. In addition, all network data transfers, including those between staking nodes and administrative interfaces, ought to require the usage of encrypted communication channels.
Security For Crypto Staking: Thorough Auditing and Monitoring
Having a system that can notice and react to events instantly is necessary. It is vital for efficient security monitoring. This should be part of using IDS and IPS. They can spot patterns that suggest a cyberattack. Every admin activity must be fully documented to prevent tampering. This requires time stamps, unchangeable integrity, and offsite storage. Security teams must regularly examine the records. They do this to find possible problems before they get worse.
Security For Crypto Staking: Frequent Penetration Testing and Security Audits
Keeping a solid security posture requires regular penetration testing and security audits. These tests look for weaknesses in the staking infrastructure. They do this by simulating actual attacks. It is advantageous to occasionally bring in different outside auditors to obtain diverse viewpoints on security issues. Following up on the results with prompt remediation and even retesting is crucial. Furthermore, the audits verify adherence to security guidelines and standards. They contribute to increased user and stakeholder trust.
Advanced Security Measures
The reliability and resilience of server-based staking platforms depend on advanced security mechanisms. Here are six thorough explanations of these actions:
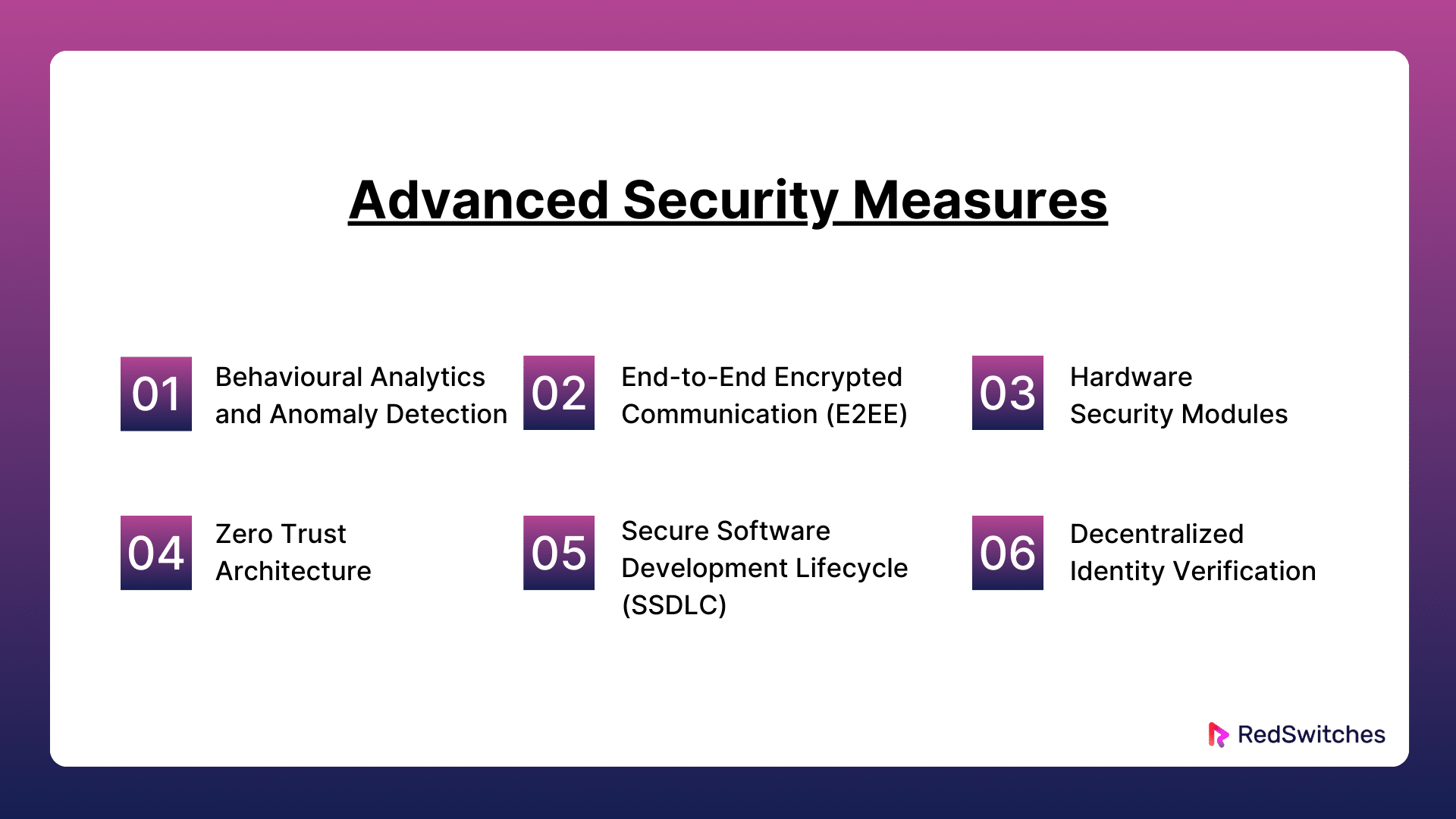
Security For Crypto Staking: Behavioural Analytics and Anomaly Detection
AI and machine learning enable behavioral analytics. It tracks and examines user and system behavior for abnormal activity. This activity might pose a security risk. With time, this technology learns what constitutes regular behavior. It may identify deviations from the norm, such as odd login timings, a sudden burst of transactions, or access from dubious IP addresses. This real-time analysis improves server-based staking system security. It does this by quickly detecting and stopping threats. It does so before it can cause serious harm.
Security For Crypto Staking: End-to-End Encrypted Communication (E2EE)
E2EE is a communication protocol that restricts message reading to the users involved. Implementing E2EE ensures that all data sent between clients and between dedicated servers is securely encrypted. Only the intended receiver can decrypt it. This prevents the sent data from being accessible to eavesdroppers, including telecom and internet providers. E2EE is vital. It keeps sensitive data secret in the staking infrastructure.
Security For Crypto Staking: Hardware Security Modules
Hardware Security Modules (HSMs) are physical devices. They manage digital keys for strong authentication and help with cryptoprocessing. The devices can generate, store, and manage the keys. They do so securely. This ensures that the keys are never lost. HSMs are used in server-based staking to improve security by protecting and managing digital keys and carrying out all necessary critical operations in a physically tamper-resistant device. Even if the dedicated server environment is compromised, HSMs assist in reducing the risk of exposure or critical theft.
Security For Crypto Staking: Zero Trust Architecture
Zero Trust is a security concept. It is based on the idea that businesses shouldn’t blindly trust anything seeking to connect to their systems. This includes things from within or beyond their boundaries. Instead, they should make sure that everything is legitimate before allowing access. Implementing a zero-trust architecture in server-based staking requires strict identity checks. It also needs micro-segmentation to limit user access to the minimum. And it needs layered security to protect network segments. Using this strategy decreases the attack surface and lessens the possible impact of internal threats and breaches.
Security For Crypto Staking: Secure Software Development Lifecycle (SSDLC)
The Secure Software Development Lifecycle (SSDLC) is a set of procedures that guarantee security is given top priority across the entire software development lifecycle. When using SSDLC for server-based staking, security precautions must be incorporated into the software development process, including threat modeling, security-focused code reviews, and frequent security testing. By taking a proactive stance, security vulnerabilities are found and fixed early on, significantly reducing the risks related to software defects. Additionally, it makes it easier to create staking platforms and applications that are safer and more resistant to cyberattacks.
Security For Crypto Staking: Decentralized Identity Verification
Utilizing blockchain technology, these systems enable users to validate their identities independently of central authority. By giving users control over the security and privacy of their personal data, decentralized identity verification can improve security in server-based staking. This technology lowers the danger of identity theft and fraud by storing identifying data on a blockchain rather than centrally, which makes it tamper-resistant and gives individuals complete control over who may access their information.
Decentralization and Security
Blockchain technology has a crucial idea: decentralization. It has significant security effects, especially in server-based staking. The idea emphasizes spreading control throughout a network. This is better for security but also brings unique challenges.
Security For Crypto Staking: Blockchain’s Decentralisation Concept
Decentralization divides authority, control, and operational capability away from a centralized body. In blockchain technology, the ledger is kept up to date across an extensive network of nodes. This is unlike a conventional centralized database with a single control point. Each node has a copy of the complete ledger. Transactions need confirmation by agreement among these nodes.
Security For Crypto Staking: Enhanced Security via Redundancy
Redundancy is one of the main ways that decentralization improves security. There is no single point of failure in a blockchain network since every node that is part of the network has a copy of the ledger. The design guards against various problems. These might impact centralized systems. For example, server outages, corrupted data, and deliberate assaults meant to bring a system offline. This means that in decentralized staking systems, the whole network keeps running. It ensures that staking and security continue, even if some nodes fail or are corrupted.
Security For Crypto Staking: Resistance to Censorship and Tampering
Decentralization is naturally resistant to censorship and tampering. Because blockchains are distributed, changes need consensus approval. This stops any one party from changing data. This is especially crucial regarding server-based staking because large stakes may be involved. It requires many unrelated parties to verify fraud. Fraud includes attempts to change stakes, reroute cash, or manipulate transactions.
Security For Crypto Staking: Minimizing the Effect of Localized Attacks
In a decentralized system, the integrity of the network is not jeopardized by assaulting one or more nodes. This resilience is critical to staking security. It raises the difficulty and resource needs of coordinated attacks on many nodes. To substantially impact the network, hackers must simultaneously infiltrate the majority of nodes, which is a far more challenging and possibly prohibitively expensive task than simply targeting one central server.
Security For Crypto Staking: Difficulties with Decentralization
On the other hand, decentralization has significant security issues. The lack of control may slow the spread of upgrades. It may also slow the reaction to threats. Also, the security and quality standards of staker nodes vary in decentralized staking systems. This difference could cause vulnerabilities unless there are strong governance and compliance processes.
Also read CMS Security: 4 Types of Threats and 9 Tips To Prevent It
Mitigation Measures
Decentralized networks often use many measures to solve these issues. These measures include strict node admission, staking requirements that reward good behavior, and security protocols that work across nodes. Furthermore, developments in decentralized governance models keep improving how choices are made among distributed stakeholders, striking a balance between adaptability and coordinated response in the event of a threat.
Real-Time Monitoring Tools and Techniques
Effective management of server-based staking setups requires real-time monitoring. It improves security, aids in maintaining operational integrity, and offers performance insights into the system. I’ll review a few essential tools and methods that may be used in these setups to achieve efficient real-time monitoring below.
System Performance Monitoring
To keep dedicated servers running well, we need monitoring tools. These include Nagios, Zabbix, and Prometheus. They can monitor most of the server’s health. This includes power supply and temperature. These are vital for preventing hardware failure. This tech can do more than just alert. They can also interact with other systems to automate responses. For example, they can scale resources or start failover procedures to guarantee ongoing uptime. They also offer historical data. It may be used to forecast system behavior and resource needs. This lets you optimize dedicated server management proactively.
Network traffic analysis
The ability to analyze packets at a finer level is made possible by programs such as Wireshark and tcpdump. This is crucial for identifying problems such as network congestion or malformed packets that may point to an attack vector. Meanwhile, NetFlow/sFlow collectors like Plixer Scrutinizer and SolarWinds expand their capabilities. They offer a full view of network traffic patterns over time. This makes spotting patterns or repeat attacks easier. It is vital for fortifying network defenses. They can monitor data movement across networks. This makes them essential for meeting data protection rules.
Log Management and Analysis
More than just gathering and displaying data, sophisticated log management systems like Splunk and the ELK Stack do more. They can automatically find anomalies in big datasets. They shorten the time to uncover security problems. They do this with real-time data processing and machine learning insights. To show the health of the infrastructure, these systems can also work with other IT tools. This speeds up troubleshooting. It helps the IT team address alerts before harming system security or performance.
Application Performance Management (APM)
In addition to monitoring application performance, APM platforms like AppDynamics, New Relic, and Dynatrace also offer deep diagnostic features, including code-level analysis. This can help find flaws in staking algorithms. They are not always visible through regular monitoring. These tools may also evaluate how an application behaves in various scenarios by simulating user interactions. The tools offer insightful data. It is on system dependability and user experience. They can help prioritize development and maintenance tasks.
Security Information and Event Management (SIEM)
SIEM solutions, such as IBM QRadar, Splunk Enterprise Security, and LogRhythm, can secure dedicated servers well. They can provide advanced incident response capabilities, like automated threat containment, and detect complex attacks by correlating seemingly unrelated events across systems. These technologies, which provide thorough audit trails and compliance reports to help satisfy regulatory requirements and shield the company from possible legal and financial fines, are also essential for building a sound security governance framework.
Blockchain-specific Monitoring Tools
These tools, such as Alethio, Tenderly, and Blocknative, are essential for staking operations that rely on smart contracts to automate tasks like reward distribution. These tools can notify administrators of unsuccessful transactions or odd innovative contract executions, which could be signs of malware or defects. They can also give validators performance information to help them maximize their staking plans and increase their return on stake, improving network health and participation overall.
Also Read What Is the Meaning of Crypto Staking Apy?
Future Trends in Staking Security
Staking security is changing quickly, particularly concerning blockchain and cryptocurrency networks. It is anticipated that staking security trends in the future will adjust to the growing complexity of blockchain technologies and the growing sophistication of cyber attacks. Staking security is expected to be shaped by the following major themes in the future:
Integration of Machine Learning and Artificial Intelligence
Security systems must now use machine learning and artificial intelligence (ML). Cyber threats are getting more complex and nuanced. These technologies may quickly analyze lots of data. The data can be used to find anomalies and security risks that humans could miss. AI and ML can monitor and predict dangerous trends in node behavior, transactions, or smart contracts. They do this in the context of staking. This allows for proactive defense against potential attacks or system malfunctions.
Quantum-Resistant Cryptography
The current cryptographic techniques secure blockchains and staking protocols. But, they may potentially become vulnerable to quantum computing. Quantum-resistant cryptography aims to create new algorithms. They will be impervious to attacks by quantum computers. This is key for staking. The power of cryptographic algorithms directly affects digital asset security. We will pay a lot of attention to developing and applying quantum-resistant algorithms. This is to keep staked assets safe for the long term. Quantum-resistant algorithms are still under development, and it’s unclear when they will be widely implemented.
Decentralized Identity Verification
The demand for private and safe verification will increase. This will happen as blockchain networks expand. Participants can be authenticated using decentralized identity technologies without disclosing private information. It can be a weak point to ensure all players are authentic and reliable without relying on centralized authority. But, this strategy helps improve stake security.
Enhanced Governance Models
The governance model runs decentralized networks. It often determines their security level. Staking processes are getting more complicated. They need better governance. It must work transparently and effectively. It must adjust to new challenges. These models will likely use automated governance through smart contracts. The contracts can do tasks like adding patches and upgrades without humans. This lowers the possibility of human error or manipulation.
Multi-Party Computation
MPC is a cryptographic system. It lets many parties compute a function over their inputs together. They do this while keeping their inputs private. MPC may be utilized in staking to process transactions and build new blocks so that no single party is privy to all the transaction information. Spreading trust and ensuring no one node can endanger the process’s integrity might greatly improve staking security.
Enhanced Regulatory Compliance
As staking becomes more widely accepted, more regulatory oversight is anticipated. It is probable that in the future, staking security will focus more on adhering to international security norms and laws. This will require stricter audits, disclosure of security problems, and integration of compliance into staking platforms to ensure that staking follows ethical and legal standards.
Usage of Hardware-based Security
There is an increasing trend towards using hardware-based security solutions, such as trusted execution environments (TEEs) and hardware security modules (HSMs), to counteract the weaknesses associated with software-based security. These tamper-resistant, isolated devices that are not connected to the rest of the system can generate, store, and manage stake-related encryption keys. Their application in safeguarding staking activities adds a physical security layer to software solutions.
Conclusion
In summary, the security of cryptocurrency staking is complex. It is also dynamic. It needs ongoing innovation and attention to detail. As we’ve seen, staking’s integrity and assets’ safety depend on using top security and best practices. These tactics are crucial. They reduce hazards early in the fast-growing field of blockchain. They include using quantum-safe cryptography. They also involve adding AI and machine learning to improve anomaly detection.
Working with a company like RedSwitches can be pretty beneficial for stakeholders who want to deploy staking solutions that are dependable and strong. We offer the required infrastructure and assistance, utilizing state-of-the-art security technology and procedures to guarantee the safety and effectiveness of your staking activities. We are a helpful ally in navigating the intricate security landscape of cryptocurrency staking, offering dedicated servers and knowledgeable support to help you safeguard your investments and optimize your returns in this ever-changing market.
FAQs
Q. Is staking my crypto safe?
Staking cryptocurrency can be risk-free. You just need to use trustworthy, safe platforms and follow recommended security steps. These include two-factor authentication and secure wallets.
Q. How to safely stake crypto?
To stake cryptocurrency safely, use reliable staking platforms. Also, turn on multi-factor authentication and update your software.
Q. Can staked crypto be stolen?
Choosing trustworthy and safe staking services is crucial. This is because staked cryptocurrency may be taken in a security breach.
Q. What is crypto staking, and how does it work?
Crypto staking is a process where users can stake their crypto assets to support the security and efficiency of a blockchain network. By staking your crypto, you can earn rewards in the form of staking rewards.
Q. What are the security measures for servers?
Key security measures for servers include using firewalls to control incoming and outgoing network traffic, installing antivirus and anti-malware software, implementing regular patch management to update software and operating systems, and using robust authentication methods such as multi-factor authentication (MFA).
Q. What are the risks of staking crypto?
Staking crypto has risks. These include security holes, intelligent contract risks, and the chance of losing your assets to network issues or attacks.
Q. What are some popular crypto staking platforms?
Popular crypto staking platforms include Ethereum. They also include staking pools and some crypto exchanges. These exchanges offer their users staking services.
Q. What is liquid staking, and how does it differ from traditional staking?
Liquid staking is a type of staking in which users can stake their crypto assets while maintaining liquidity. This differs from traditional staking, where assets are locked up for a specific period.
Q. What is the role of securities law in crypto staking?
Securities law is crucial. It regulates staking and ensures compliance with rules. It also protects investors.
Q. How can one participate in staking and start earning staking rewards?
To stake users can stake their crypto on staking platforms or exchanges. By doing so, they can earn staking rewards for supporting the network.
Q. What are the security strategies one should consider when involved in staking?
When staking, use secure wallets. Follow best security practices for your assets. Stay informed about the staking process and its risks.