Did you know that the most commonly used ports on a typical server are often below 1024?
These ports are often used for essential web traffic, email services, and secure connectivity via SSH. As a result, understanding port management is a critical sysadmin task for hosting websites, running email servers, and enabling networked services.
A service running on a system awaits incoming connections on a specific system or admin-assigned port. Similarly, external devices and services rely upon ports to interact with the services on a server.
That’s why opening a port in Linux is an essential operation in which you must configure the system’s firewall to allow traffic through that port.
So, how do you handle the situation when a specific service or application in Linux requires you to open a different port?
We will answer this and other related questions in this tutorial. We will discuss how to check for open ports, open specific ports on a Linux server, and test for open ports.
Let’s start with a brief overview of ports in a Linux system.
Table Of Contents
What is a Port?
In networking, a port serves as an endpoint for a service on a server. Each port, identifiable by a number ranging from 0 to 65,535, creates a unique communication socket when paired with an IP address.
Ports in a Linux Environment
Since we’ll be exploring how to check, open, and test a port in Linux, it is particularly important to understand the idea in that context. A port in Linux is like a virtual door through which your server sends and receives specific information from internal and external sources.
Why Is It Essential To Open a Port in Linux?
Opening a port is a crucial task for system administrators and users who manage network traffic for specific services. Most ports on Linux servers are closed by default because of security reasons. In almost all cases, the sysadmins have to open a port to allow traffic to the mapped service.
How Do You View and Open Ports in Linux?
Let’s now look into the technical aspects of opening and viewing ports in Linux.
The Prerequisites
Before we dive into how to check, open, or test ports in Linux, you should make sure that you have the following in place:
- A system running a mainstream Linux distribution.
- A user account with sudo or administrative privileges
- A working knowledge of Linux commands.
How to Check Open Ports in Linux
Before attempting to open a port on a system, we strongly recommend checking whether the desired port is already in use.
A simple way of checking that is to use grep to filter the output of the netstat utility. The syntax of the command in this case is as follows.
# netstat -na | grep :[port-number]
For instance, run the following command to evaluate the availability of port 8080:
# netstat -na | grep :8080
If there is no output of the command, port 8080 is closed on your system.
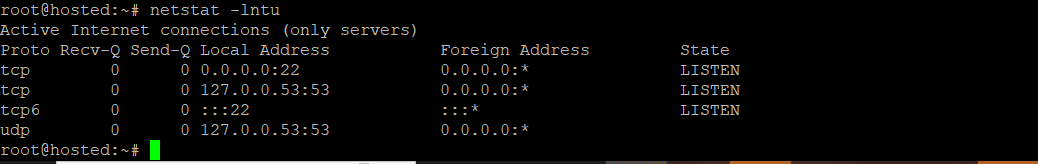
Alternatively, you can run the following netstat command to display a list of listening ports (open ports on the system):
# netstat -lntu
Here, -l looks for listening ports, -n shows numerical port values, and -t and -u represent TCP and UDP, respectively. The following screenshot shows the output of the command on our test system.
How to Open a Port in Linux
The actual steps in the process of opening a port in Linux vary from distribution to distribution, mainly because of the different firewalls and system management architecture.
Let’s discuss the process for the three popular categories of Linux distributions.
Case #1: Ubuntu and UFW-Based Distributions
The Uncomplicated Firewall (UFW) is the native firewall on Ubuntu and many other Debian-based distributions.
The following is the syntax of the UFW command to open a port on Ubuntu and related distributions:
# sudo ufw allow [port-number]
For instance, the following command will open port 8080 on our test system:
# sudo ufw allow 8080
The output will verify the addition of IPv4 and IPv6 rules for the specified port.
For a more service-specific approach, you can open the port associated with a particular service without explicitly mentioning the port number. The syntax of the command is as follows:
# sudo ufw allow [service-name]
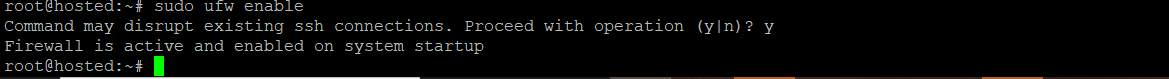
Important: After defining the rules, confirm that UFW is active on your system by executing the following command:
# sudo ufw enable
Case #2: CentOS and firewalld-Based Distributions
Many RHEL-based distributions, such as CentOS and Fedora, use firewalld as the default firewall. You can use the following command to open a port on the system:
# sudo firewall-cmd --zone=public --add-port=[port-number]/[protocol] --permanent
Note: We recommend including the optional –permanent flag to guarantee that the rule you add will persist after the system reboot.
Case #3: Linux Distributions without UFW or Firewalld
Some Linux distributions prefer iptables over UFW or firewalld.
In this case, you set rules directly in the Linux kernel firewall to filter IP packets and control network traffic. While it’s a bit more complex to use than UFW or firewalld, many sysadmins prefer working with iptables because of minimal overheads and tighter integration, but still, a common way to manage network security.
Run the following command syntax to create an iptables rule for opening a port:
# sudo iptables -A INPUT -p [protocol] --dport [port] -j ACCEPT
In this syntax, you can specify the port number with the –dport, and the -p flag to define the protocol (TCP/UDP). For instance, the following command creates an IPv4 rule for TCP port 8080:
# sudo iptables -A INPUT -p tcp --dport 8080 -j ACCEPT
There is no need to restart the firewall after adding the rules, as they are applied immediately.
For IPv6 traffic management, we recommend the ip6tables command to set up filtering rules specific to IPv6 addresses.
# sudo ip6tables -A INPUT -p [protocol] --dport [port] -j ACCEPT
Persist iptables Rules Through Reboots on Debian-Based Distributions
By default, the iptables rules generated are not automatically retained after a system reboot. We recommend the following steps to make the rules persist on Debian-based distributions:
- Save the IPv4 rules you have configured with the following command:
# sudo iptables-save > /etc/iptables/rules.v4
- Similarly, save the IPv6 rules with the following command:
# sudo ip6tables-save > /etc/iptables/rules.v6
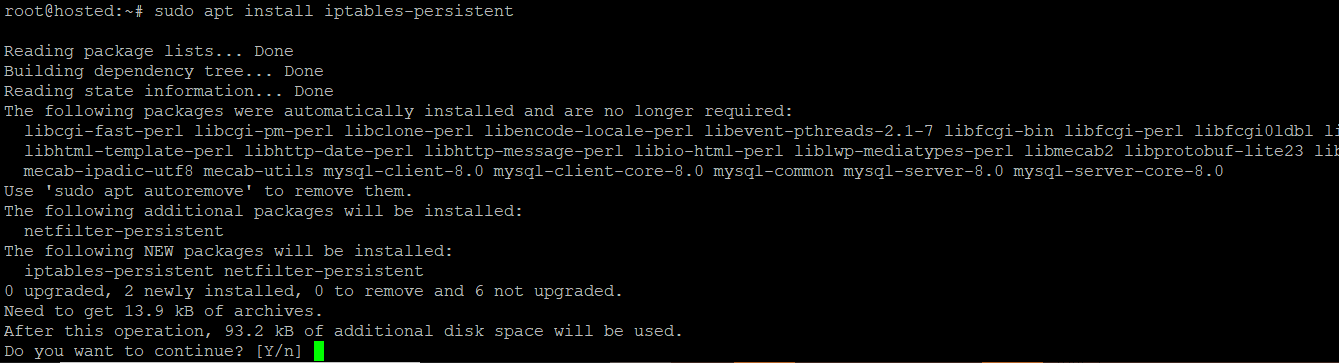
- Next, install the iptables-persistent package with the following command syntax:
# sudo apt install iptables-persistent
This package automatically reloads the contents of the rules.v4 and rules.v6 files upon system restart, maintaining the continuity of the iptables configuration.
Persist iptables Rules Through Reboots on RHEL-Based Distributions
Retaining iptables rules on RHEL-based distributions involves saving the configurations in a specific location. Here are the steps you need to follow:
- Save the IPv4 and IPv6 rules with the following commands:
# sudo iptables-save > /etc/sysconfig/iptables
# sudo ip6tables-save > /etc/sysconfig/ip6tables
- Install the iptables-services package with the following command:
# sudo dnf install iptables-services
- Next, start the service:
# sudo systemctl start iptables
- Enable the service:
# sudo systemctl enable iptables
- Save the iptables rule(s) with one of the following commands:
# sudo service iptables save
Or
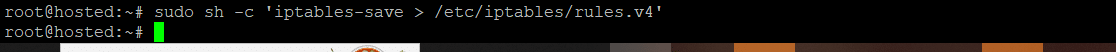
# sudo sh -c 'iptables-save > /etc/iptables/rules.v4'
- Remember to restart the service to apply the changes:
# sudo systemctl restart iptables
This process ensures that your iptables configurations persist across system reboots on RHEL-based systems.
How to Test Open Ports
After opening ports on your Linux server, it is always important that you test and verify the outcome of the process.
We recommend that you use the netstat utility for this purpose. Run the following command in the terminal:
# netstat -lntu
The output will show the open ports on the system.
Alternatively, you can list open sockets using the ss command and observe the port(s) listed within the socket details:
# ss -lntu
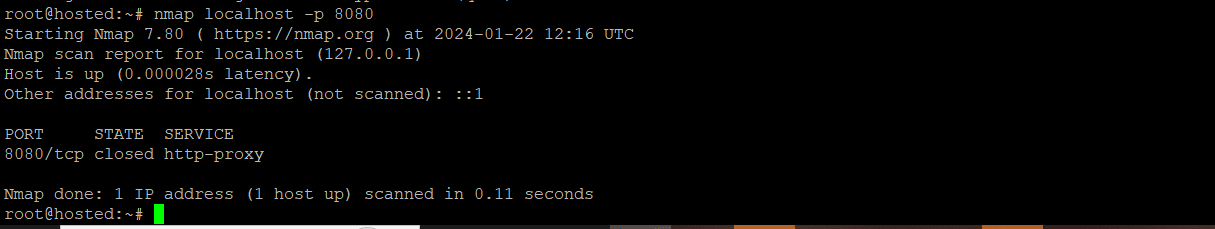
Finally, you can check a port’s status with the nmap utility, which displays its status as open or closed based on the connected service.
# nmap localhost -p 8080
Test the Port with the netcat Utility
The netcat utility allows you to test an open port. Here’s how:
Use echo to send output to netcat, specifying the port to listen to. The example below sends a message to test port 8080:
# echo "Testing port 8080" | nc -l -p 8080
Keep the command running and open another terminal window. Then, use telnet to check the local socket.
# telnet localhost 8080
If the port is open, the telnet command’s output will show the message sent through netcat. On our test server, the message will be Testing port 8080.
Conclusion
This guide has simplified instructions on listing, opening, and testing ports in Linux. Opening ports is essential for various purposes, enabling incoming traffic to access specific services or applications on your system efficiently.
Building on this, learning these methods enhances your understanding of network traffic management and ensures that you can handle various scenarios, from basic port opening to ensuring robust security. This knowledge is crucial for maintaining the smooth operation and protection of your Linux system’s network activities.
RedSwitches offers the best dedicated server pricing and delivers instant dedicated servers, usually on the same day the order gets approved. Whether you need a dedicated server, a traffic-friendly 10Gbps dedicated server, or a powerful bare metal server, we are your trusted hosting partner.
FAQs
Q. Why do I need to open a port in Linux?
Opening a port in Linux is crucial for facilitating communication between various network services or applications, allowing incoming connections and traffic on specific ports on your system.
Q. How can I verify if a port is currently accessible on my Linux system?
Utilize the netstat command to examine listening ports. For example, use # netstat -lntu to showcase open ports and their respective statuses, ensuring network ports are operational.
Q. What are the common approaches for enabling a port in Linux?
Depending on your Linux distribution, tools like UFW, firewalld, or iptables can be employed to set up port rules. Each method has its unique syntax, so consult distribution-specific guides for accurate instructions on managing network interfaces.
Q. Is it possible to open ports for TCP and UDP protocols simultaneously?
Indeed, numerous firewall tools, including iptables and firewalld, allow you to open ports for both TCP and UDP, ensuring flexibility for handling a range of ports. Specify the protocol when configuring the rules in the input chain.
Q. How can I ensure the persistence of my iptables rules following a system reboot?
To save iptables rules, save them using iptables-save or ip6tables-save and store the configuration in a file. On Debian-based systems, installing iptables-persistent ensures automatic rule reloading through the package manager at boot.
Q. Are there alternative methods for testing the accessibility of a port on my Linux system?
Indeed, tools like nmap and netcat offer additional avenues for assessing open ports. For example, you can execute simple commands such as # nmap localhost -p [port] or # echo “Test” | nc -l -p [port] to check UDP port connectivity.
Q. Can leaving ports open pose security risks?
Maintaining unnecessary open ports can pose security risks, potentially exposing your system to unauthorized TCP connections. Always open only the ports required for specific services and regularly audit your firewall rules.
Q. How can I troubleshoot issues encountered while attempting to open a port?
Check for typos in your commands, verify that the required service is running, and review firewall logs for relevant information. Additionally, ensure that an external firewall does not block the chosen port destination port, securing your operating system from potential security threats.