Do you know that a device can support 65535 ports?
A port is a logical endpoint that the system uses for communication. Ports are usually operated by applications and processes that use the assigned port for listening for incoming information and sending messages to external devices and services.
Network ports have standard numeric IDs that let devices simultaneously respond to several network requests with a single IP address. Generally, firewalls control communication through ports on a system. System administrators can control access to ports by firewall rules.
Open ports are a security hazard and a critical challenge in this context is to discover which ports are open and accessible on your system.
This comprehensive tutorial will walk you through the process of searching for available listening ports on a Linux server using five commonly used networking tools.
Table Of Contents
What is a Listening Port on a Linux Server
Services and applications use listening ports to monitor incoming network requests. Each listening port has an interaction protocol (TCP or UDP) and an IP address.
Listening ports may be open or closed depending on the system and network configuration.
When an external connection uses the appropriate protocol, open ports on the system accept it.
Port numbers below 1000 are usually reserved for system services (for instance, port 80 for HTTP). Additional services initiated by other applications are assigned an available port number. In most cases, the system admin needs to alter the firewall rules to allow traffic to open ports.
Five Tools to Check Linux Open Ports
Checking ports in a Linux system is such a critical aspect of system security that you can find several tools to check and monitor linux open ports.
Before diving into the details of using these tools, you should know that while they perform very similar functions, they differ in how they present the information in the terminal or their custom UI.
The Prerequisites
Before you try out the tools we will discuss in this guide, make sure you have the following:
- A system running a mainstream Linux distribution
- A user account with administrator or sudo privileges
Tool #1: lsof
Users can view a list of the applications that use daemons to keep active network connections and listening ports using the lsof command.
Show the List of Active Ports
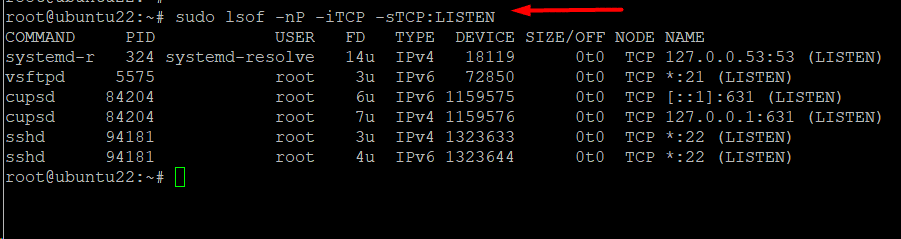
Consider the following command that generates a list of the connections that use the TCP protocol.
# sudi lsof -nP -iTCP -sTCP:LISTEN
Check if a Particular Port is in Use
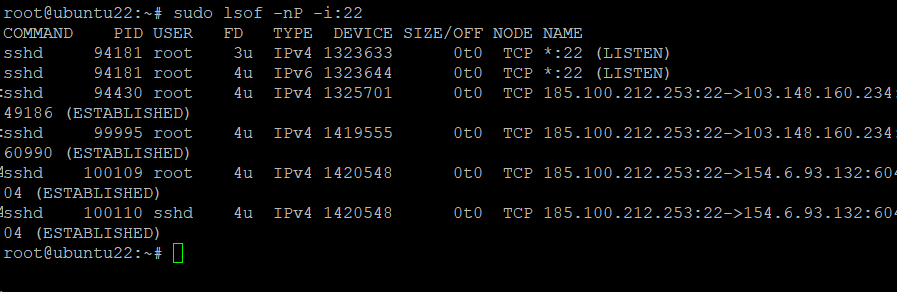
You can use the following syntax to see if a specific port is in use by a service or application.
# sudo lsof -nP -i:[port-number]
For example, run the following command to see if port 22 is in use:
# sudo lsof -nP -i:22
Note that this command doesn’t display anything if the target port is not in use. On the other hand, the command will display the application’s details if it is using the port.
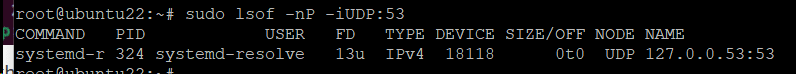
Add the Protocol to the Port Scan
You can add a protocol to the port scan to check if the port is mapped to an application that uses a specific protocol.
For example, you could run the following command to see if UDP port 53 is available:
# sudo lsof -nP -iUDP:53
Tool #2: netstat
netstat is a comprehensive tool that displays statistics about network activity, including network connections and routing tables.
You can run the following command to show the system’s listening ports:
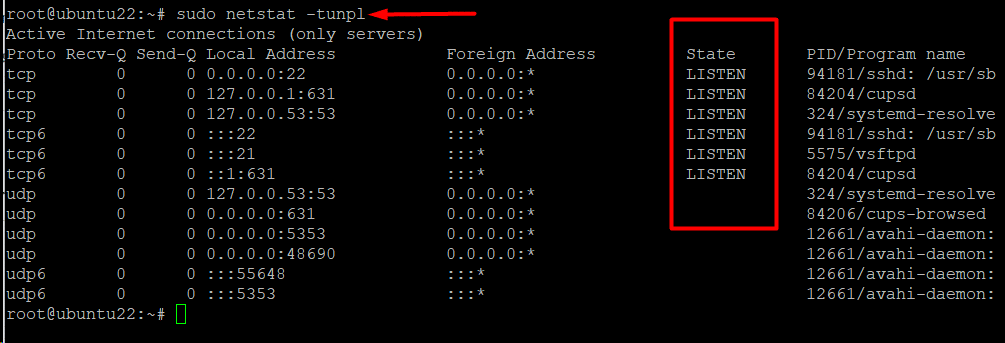
# sudo netstat -tunpl
This command syntax combines five command arguments to display the relevant information:
- -t: displays information about TCP ports
- -u: displays information about UDP ports
- -n: Doesn’t go into a detailed DNS lookup and displays IP addresses only.
- -p: Shows the application name and process ID mapped to the port.
- -l: Outputs the listening ports.
We recommend checking the State column and looking for the label LISTENING to determine which ports or sockets are open and listening.
Tool #3: ss
Note that the netstat utility we discussed in the previous section has been generally replaced by a much faster and more user-friendly ss command. The great thing about this utility is that it displays more statistics while using the same variables as netstat.
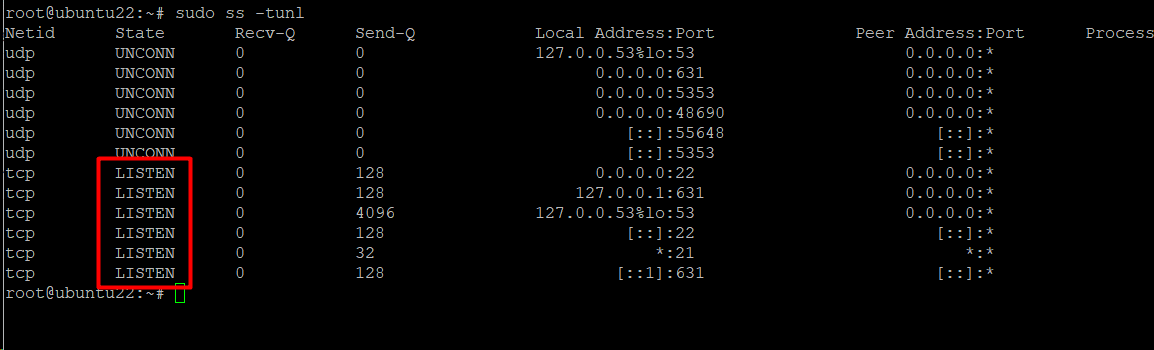
You can use the following command syntax to list the listening sockets on TCP and UDP ports:
# sudo ss -tunl
The listening ports/sockets in the State column are marked as LISTEN.
Tool #4: Nmap
The Nmap utility allows users to look for open ports on local and remote systems. We recommend the following command syntax to discover open TCP and UDP ports on the local system:
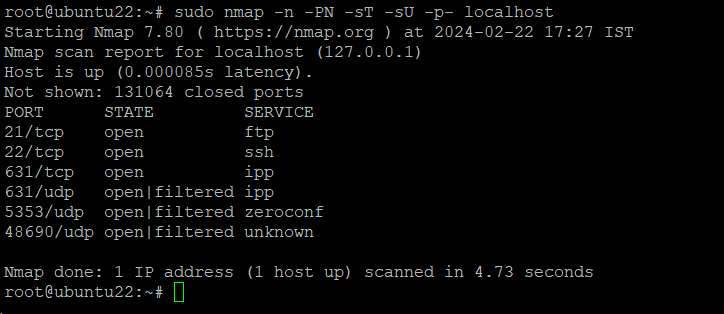
# sudo nmap -n -PN -sT -sU -p- localhost
Here’s a brief description of the options of this command:
- -n: Does not resolve DNS.
- -PN: Omits the discovery phase
- -sT and -sU: Tells Nmap to scan UDP and TCP ports.
- -p-: Examine every port.
The output includes a list of the services that are using the open ports.
Note that Nmap is not usually installed on many Linux systems. If that’s the case with you, we recommend our quick tutorial on installing Nmap on Ubuntu and related distributions.
Tool #5: netcat
The netcat utility (often shortened to nc) is a popular choice for scanning ports on local and remote computers and finding out if they are open, closed, or filtered by a firewall rule.
Important: The netcat command is referred to as ncat on CentOS, RHEL, and Debian.
You can start with the following command that checks every port on the local system:
# nc -z -v localhost 1-65535
The -v option instructs netcat to generate detailed output, whereas the -z option activates the zero-I/O mode, which is helpful for port scanning.
When the command is executed, netcat attempts to connect to all ports, reporting the success or failure of the connection.
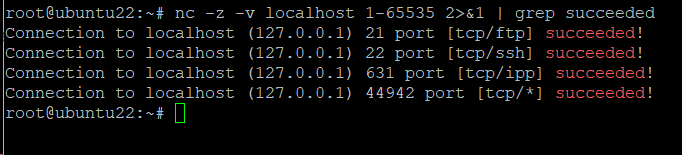
You will notice that the command produces several screenfuls of output. You can reduce this by adding the 2>$1 option and then further filtering the output with the grep utility:
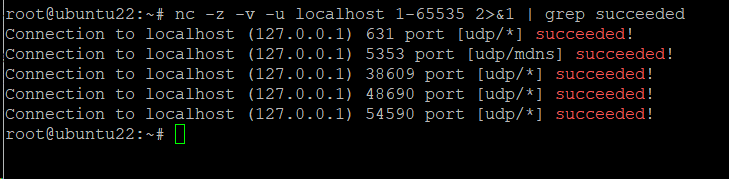
# nc -z -v localhost 1-65535 2>&1 | grep succeeded
By default, netcat only tests the system’s TCP ports. You can include the UDP ports with the -u option:
# nc -z -v -u localhost 1-65535 2>&1 | grep succeeded
netcat is a feature-rich utility that admins can use in several real-world applications. We have a comprehensive guide that explains how to use netcat to deal with 8 critical challenges.
Conclusion
Network files managers and users must understand how to verify Linux open ports.
By becoming proficient in these methods, users can improve their networks’ effectiveness and security by ensuring that only the required ports are open. One proactive way to protect against possible security attacks is to monitor and manage open ports. To establish a dependable and safe Linux environment, take charge of open port management.
Boost your online visibility with RedSwitches, the world’s leading dedicated hosting company. Whether you need a dedicated server, a traffic-friendly 10Gbps dedicated server, or a powerful bare metal server, we are your trusted hosting partner.
We ensure a reliable and safe hosting environment. So, see us today for a hosting solution that works everywhere. For flawless performance and dependable hosting anywhere in the world, go with RedSwitches!”
FAQs
Q. Why is it important to check Linux open ports?
To assist in detecting potential vulnerabilities and make sure that only necessary services are available, it is imperative for security risk to check open ports regularly.
Q. How can I use the ‘netstat’ command to check open ports?
Use the command ‘netstat -an | grep LISTEN’ to display open ports on your Linux system.
Q. What is the purpose of the ‘nmap’ tool in checking open ports?
Nmap is a powerful network port scanning tool that provides a comprehensive view of open ports on a system, aiding in network exploration and security risk auditing.
Q. Are there any GUI applications available for Linux port scanning?
Yes, tools like ‘Wireshark’ and ‘Gufw’ offer graphical interfaces for monitoring Linux open ports.
Q. How can I check which process uses a specific open port?
You can use the ‘lsof’ command to find out which process uses a certain open port. ‘lsof -i :’ is one example.
Q. Can I check open ports on remote Linux servers?
You can use tools like ‘nmap’ or ‘telnet’ to check open ports on remote Linux servers.
Q. What should I do if I find an unexpected open port on my Linux system?
Investigate the process using the port, and if it’s unexpected or unnecessary, consider disabling or securing the associated service.
Q. How can I use the ‘ss’ command to look for open ports?
Use the command ‘ss -tunlp’ to display open ports and associated processes.
Q. Are there specific ports I should always keep open on a Linux server?
It depends on the services your server requires. However, commonly used ports include 22 (SSH), 80 (HTTP), and 443 (HTTPS).
Q. How frequently should I check open ports on my Linux system?
Regular checks, especially after system updates or changes, are recommended. Incorporating it into routine security practices is advisable for a proactive approach.
These FAQs provide insights into various methods for checking open ports in Linux, promoting a secure and well-maintained system.