Key Takeaways
- The predetermined configurations or settings known as firewall rules specify how a firewall is to handle both incoming and outgoing network traffic.
- Incoming and outgoing network packets are examined by firewall rules, which then compare them to established rules.
- Enforcing network security standards and defending against malware, illegal access, and other online threats require firewall rules.
- A firewall strategy delineates the methodology and tenets for configuring and overseeing firewall rules to safeguard a network efficiently.
- Firewalls offer vital security but are not impenetrable, and knowledgeable hackers can find ways around them or exploit flaws.
- Recognize the top 12 Windows firewall best practices.
Firewalls are increasingly important. They strengthen digital defenses in an era of cyber threats growing more clever. Firewall rules are our network’s first line of defense. They control what traffic may enter and leave. They provide a vital defense against attackers.
A firewall’s rules must be accurate and intelligent to be effective. It’s not enough to simply have a firewall. In this blog, we will explore the topic of firewall rules and reveal the complexities involved in creating and using them. Get ready as we discuss firewall rules’ best practices in detail.
Join us on a trip to learn the best practices. They can improve your firewall strategy and strengthen your digital infrastructure against the constant wave of cyber attacks. It does not matter your level of experience with cybersecurity.
Table of Contents
- Key Takeaways
- What Are Firewall Rules?
- How Do Firewall Rules Work?
- Why Are Firewall Rules Important?
- What Are The Main Types Of Firewall Rules?
- What Is A Firewall Strategy?
- Factors to Consider When Securing a Firewall
- Can Hackers Get Past Firewalls?
- Windows Firewall Configuration Best Practices
- Firewall Rules Best Practices # 1: Regularly Update the Firewall Rules
- Firewall Rules Best Practices # 2: Implementing the Principle of Least Privilege
- Firewall Rules Best Practices # 3: Utilizing Advanced Security Features
- Firewall Rules Best Practices # 4: Enabling Logging for Monitoring
- Firewall Rules Best Practices # 5: Implementing Default Deny Rules
- Firewall Rules Best Practices # 6: Using Private and Public Profile Domains
- Firewall Rules Best Practices # 7: Enabling Stealth Mode for Unnecessary Services
- Firewall Rules Best Practices # 8: Regularly Updating the OS
- Firewall Rules Best Practices # 9: Using Network Segmentation
- Firewall Rules Best Practices # 10: Educating Users About Firewall Alerts
- Firewall Rules Best Practices # 11: Encrypting Network Traffic Using VPN
- Firewall Rules Best Practices # 12: Implementing Two-Factor Authentication
- Conclusion
- FAQs
What Are Firewall Rules?
Credits: Freepik
The instructions govern a firewall device’s handling of incoming and outgoing traffic. They are called firewall rules. These access control systems use preset criteria. They allow or block communication to enforce network security. These requirements cover protocols, services, ports, source or destination IP addresses, and more.
The rules may also specify who can access which apps. They may also say where types of data can move across the network. This all depends on the kind of firewall. The rule needs to be precisely defined and enabled in the firewall setup for it to work.
Each firewall rule usually includes criteria. These may include source and destination IP addresses, ports, and protocols. The regulations specify whether to allow or prohibit traffic that meets specific requirements. Firewalls can be implemented at many layers. Network firewalls function at Layer 3, and application-layer firewalls operate at Layer 7.
Firewall rules are essential for improving network security. They do this by controlling data flow. They block unauthorized access and reduce dangers like malware, hacking, and other cyberattacks. You must configure firewall rules well. They must form a strong defense. The defense must fit an organization’s unique needs and network weaknesses.
Well-configured firewall rules benefit dedicated servers necessary for a robust network architecture. These guidelines provide a strong defense customized to a company’s network. They address the network’s specific requirements and weaknesses. This improves security against potential cyberattacks and unauthorized access.
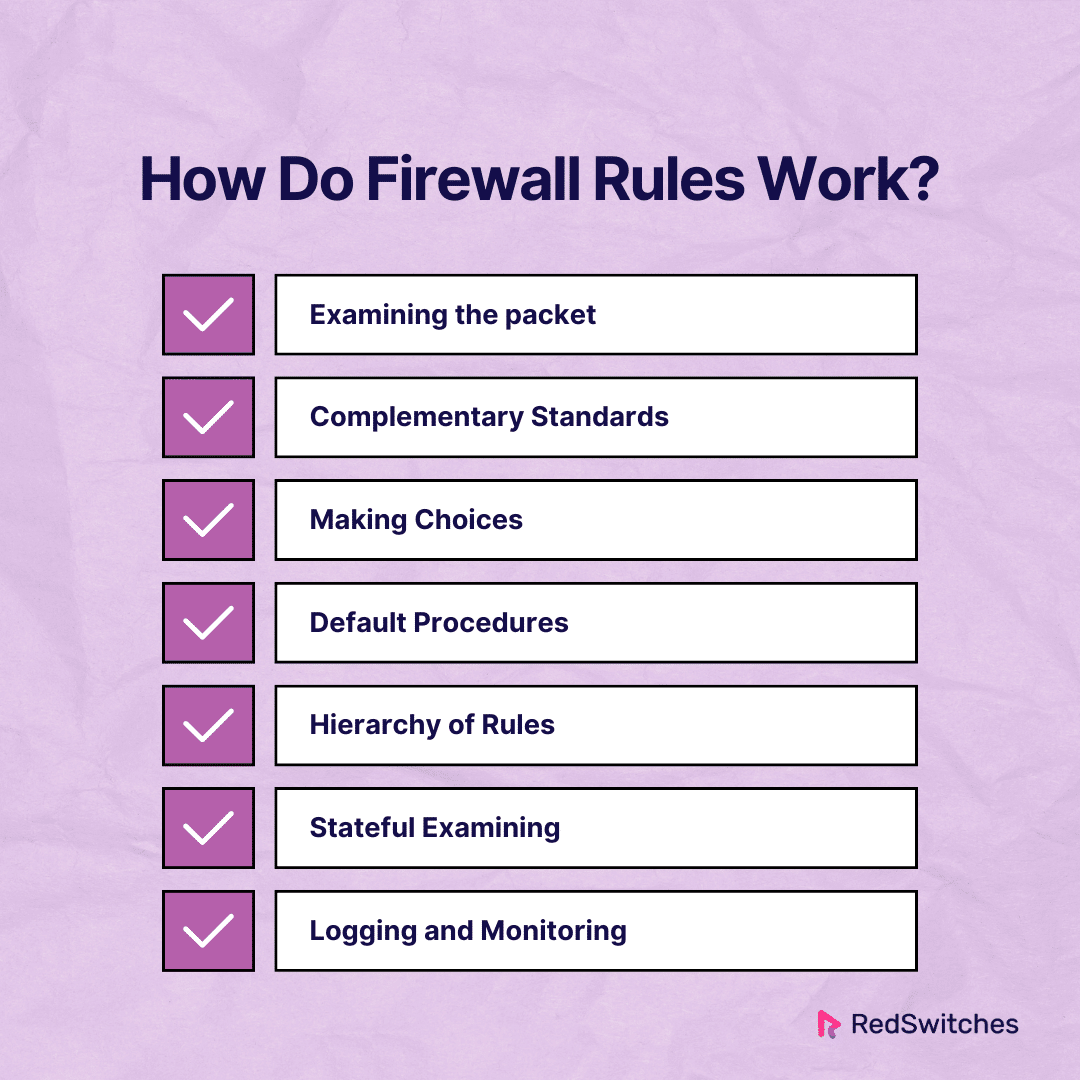
How Do Firewall Rules Work?
Firewall rules define criteria for treating incoming and outgoing network traffic. These rules are created based on variables. These variables include source and destination IP addresses, ports, and protocols. The firewall uses these standards to examine each data packet. It checks if the packet meets the rules. Then, it either allows or blocks it. Let’s examine each step in greater detail:
Examining the packet
Data packets go through the firewall on their way across a network.
The firewall examines each packet’s header information. This includes the protocol (TCP or UDP), port numbers, and source and destination IP addresses.
Complementary Standards
Firewall rules are conditions or requirements that packets must satisfy to be processed.
These requirements could include particular protocols, port ranges, and IP addresses. For instance, a rule may permit only data from a specific IP address.
Making Choices
The firewall decides how to handle a packet if it meets the requirements specified in one of the rules.
A packet can flow across the firewall if the rule permits the traffic. The packet is blocked if the rule rejects traffic.
Default Procedures
Firewalls frequently set default rules when a packet doesn’t fit expressly established rules. Default actions are usually configured to reject all communication unless authorized in advance.
Hierarchy of Rules
The hierarchy of firewall rules determines the order in which they are applied.
The first rule that satisfies the requirements of the packet is applied when rules are handled sequentially. Usually, after a match is discovered, more rules are not assessed.
Also read How To Use SSH Authorized Keys For End-to-End Security
Stateful Examining
Stateful inspection is a feature of many contemporary firewalls. It monitors the status of active connections.
Stateful firewalls can understand a connection’s status. This helps them make more informed decisions. They base their decisions not only on individual packets but also on the context of the entire communication.
Logging and Monitoring
Firewalls frequently include logging features to record information about permitted and prohibited traffic.
Monitoring firewall logs to spot possible security breaches, examining network behavior, and modifying firewall rules is imperative.
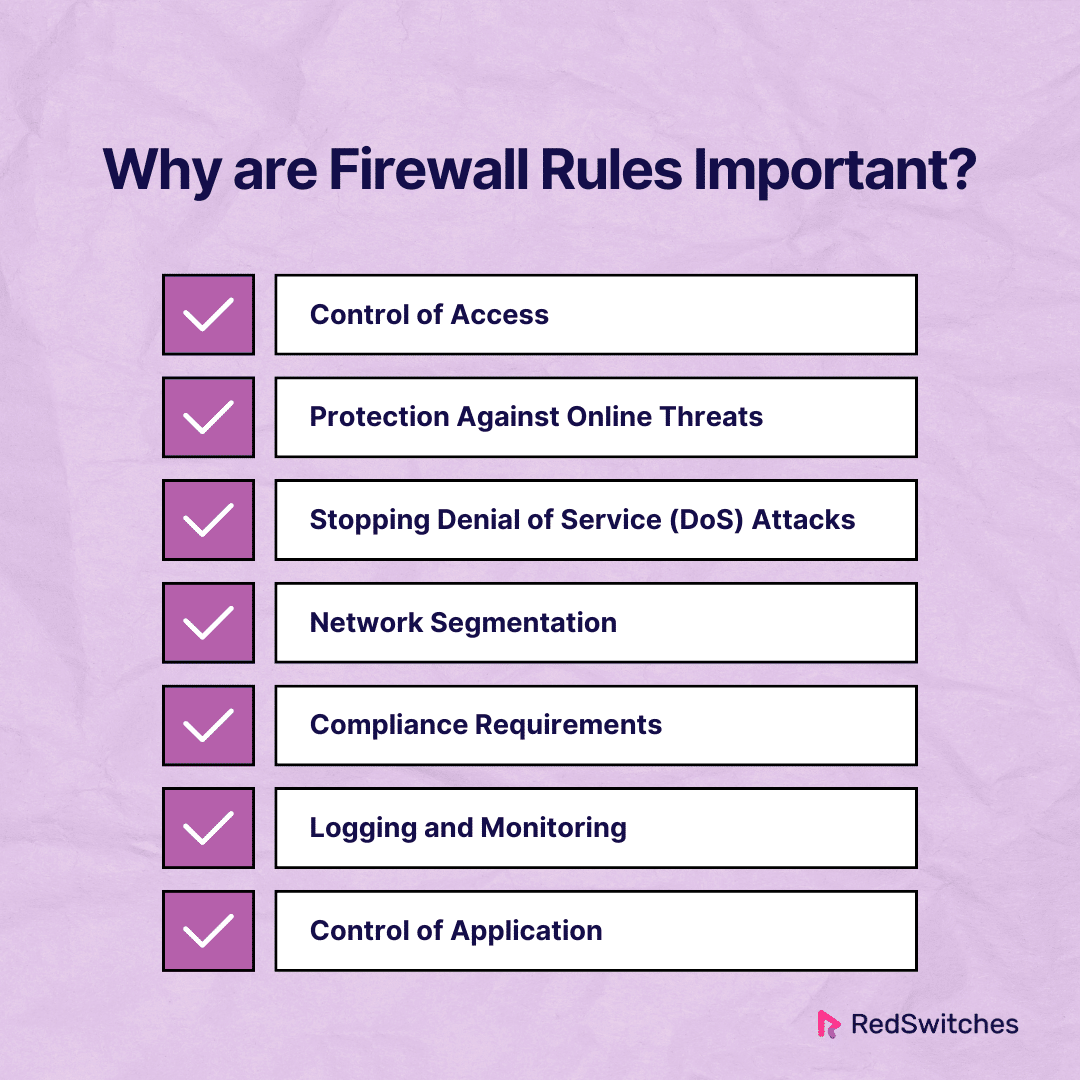
Why Are Firewall Rules Important?
We discussed how Firewall rules work. Now, we will learn why they are essential.
Control of Access
Firewall rules act as a barrier to control network traffic. They let businesses say exactly who and what can access their networks and resources. Firewall rules are paramount in maintaining the security and integrity of networks, particularly in the realm of dedicated server management.
Firewall rules prevent unwanted access. They safeguard data by saying which IP addresses, ports, and protocols are allowed or banned.
This is largely possible due to firewall rules. They enforce the principle of least privilege. They ensure that devices and users have the right access for their jobs. This helps ensure that data privacy laws are followed while also improving security. Firewall rules help defend against unwanted access attempts. They do this by defining and enforcing access boundaries. They also safeguard sensitive data and expensive assets.
Protection Against Online Threats
A firewall is one of the first lines of defense against numerous cyber threats, such as malware, viruses, and hacking attempts. Moreover, firewall rules play a pivotal role in safeguarding against a myriad of online threats, including malware, viruses, and hacking attempts, thus fortifying the defenses of dedicated servers against potential breaches.
Firewall rules cut the chance of unwanted intrusions. They also shield systems from possible security breaches by blocking hostile traffic.
Stopping Denial of Service (DoS) Attacks
DoS attacks try to overload a network, system, or service so legitimate users cannot use it. Firewall rules intelligently manage incoming traffic, serving as a proactive defense. They can prevent DoS attacks by limiting rate. They also spot suspicious patterns. This keeps network resources accessible for authorized users. This keeps the service quality for users. They rely on these resources. It also protects the operations’ continuity.
Firewall rules limit traffic rates. They also identify suspicious patterns. This actively thwarts denial-of-service (DoS) assaults. By doing this, network resources are still available to authorized users. This preserves the operational continuity and service quality of dedicated servers.
Network Segmentation
Firewall rules make network segmentation possible. It is a calculated tactic to improve security by splitting a big network into smaller, more isolated sections. If a security event occurs, such as a breach or compromise in one segment, the effect is limited to that region. It stops threats from moving throughout the network. This limits harm and lowers the chance of a breach. This segmentation strategy is particularly pertinent in dedicated server environments
Also read Network Security in Cloud Computing: 7 Things To Know
Compliance Requirements
Many businesses and organizations cannot compromise. They must adhere to strict data security standards. This is true in the current regulatory environment. Firewall rules impose strict access controls. They are essential for meeting compliance obligations. It prevents unauthorized access to sensitive data. This helps organizations avoid the financial and legal fallout from data breaches. Well-designed firewall rules boost security. They also build trust by following regulations. In dedicated server management, adherence to compliance standards is imperative, and well-designed firewall rules are pivotal in ensuring regulatory compliance and fostering trust among stakeholders.
Logging and Monitoring
Firewall rules often include logging features. They let admins watch and examine network traffic.
Detailed logs are useful for finding security events. They also investigate questionable activity. They check that the firewall protects the network.
Control of Application
Firewalls can filter at the application layer. They can enforce rules based on specific applications or services.
This lowers the risk of using unauthorized or insecure apps. It lets organizations manage general traffic flow and specific apps’ usage.
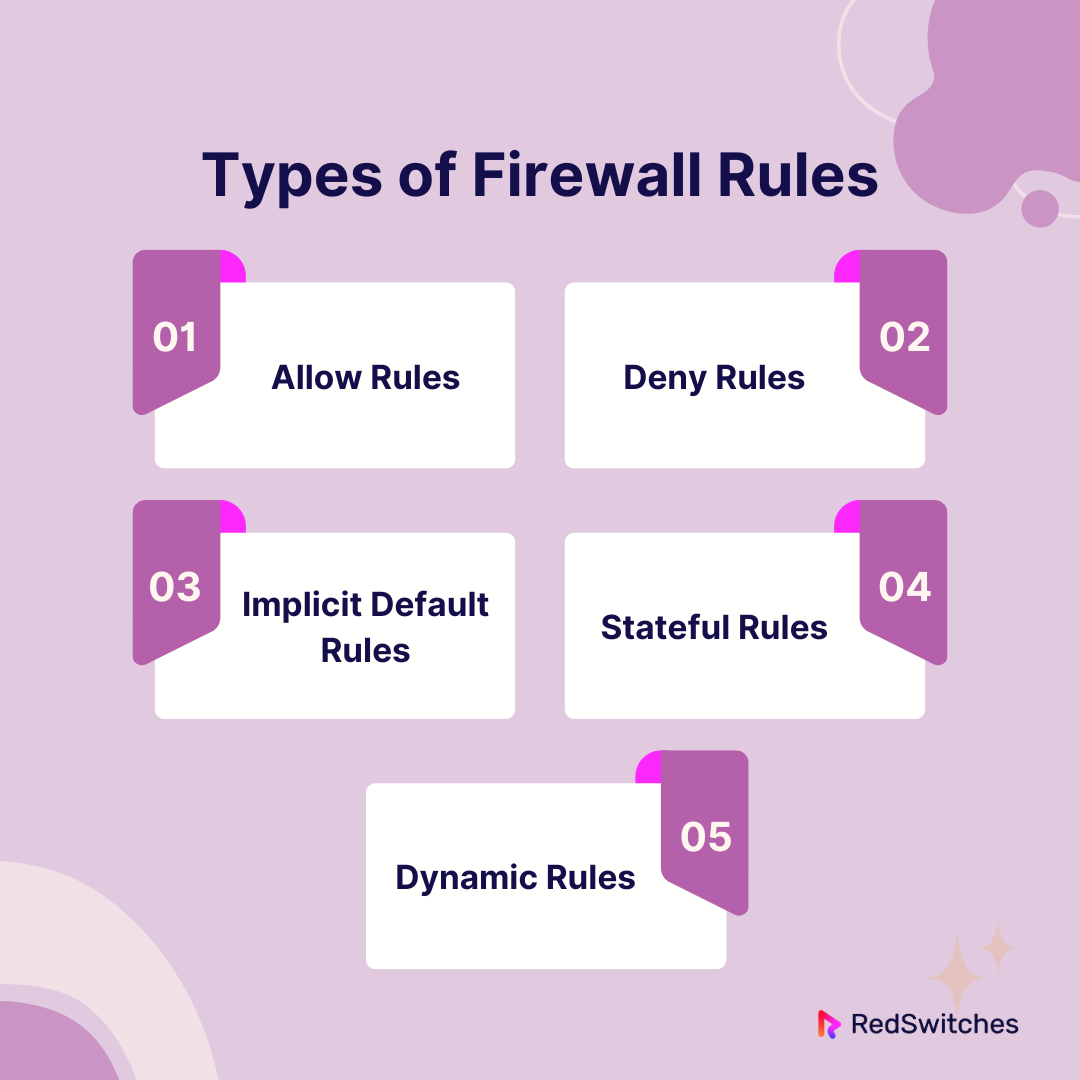
What Are The Main Types Of Firewall Rules?
Let’s understand the main types of Firewall rules.
Allow Rules
Allow rules to define when communication is allowed. They also allow particular kinds of traffic. These restrictions are usually for reliable sources, services, or programs. For example, an accept rule could permit inbound traffic on a port to help a web server run properly. These rules are key. They define the allowed paths through the firewall. They ensure that valid traffic can reach its destination across the firewall.
Deny Rules
Based on predetermined standards, deny rules serve as a first line of defense by preventing particular traffic. Denying rules improves security. They limit or stop traffic from risky sources, services, or apps. For instance, a deny rule can stop data coming from IP addresses known to be malicious or that target susceptible services.
Implicit Default Rules
Incoming or departing data that doesn’t fit accept or deny rules triggers default rules. These implicit rules are a baseline for processing traffic. These default rules are usually set to reject all traffic unless explicitly permitted. They serve as a safeguard by default, prohibiting unauthorized or unauthenticated communication. This lowers the network’s attack surface. It ensures that any unallowed traffic is automatically refused.
Stateful Rules
Stateful rules make decisions based on the current status of active connections. They consider the context of the entire conversation. The rules track connection states. They block unwanted access by checking if a connection is formed or related.
Dynamic Rules
Dynamic rules provide flexibility by adjusting to the conditions of the network as they change. Companies can use dynamic rules to react quickly and adaptably to certain situations or events. For example, dynamic rules can adjust firewall settings. They limit the rate of incoming traffic during a DDoS assault. This flexibility improves the firewall’s capacity to address new threats. It also helps with changing network conditions proactively.
What Is A Firewall Strategy?
Credits: Freepik
An organization’s firewall strategy outlines how it deploys, configures, and manages its firewall(s). It does this to safeguard its network and digital assets. It is a thorough and proactive plan. This strategy outlines the values, guidelines, and procedures that direct the use of firewalls. It reduces security risks and guarantees data confidentiality, integrity, and availability. It is a crucial part of the overall cybersecurity posture.
Also read CMS Security: 4 Types of Threats and 9 Tips To Prevent It
Key elements of Firewall strategy
Let’s discuss the key elements of Firewall strategy.
Evaluation of Risk
Determine and evaluate the organization’s exposure to potential security threats and risks. This entails being aware of the kind of data handled, the business’s nature, and the possible consequences of security lapses.
Business prerequisites
Ensure the firewall strategy aligns with the organization’s goals and needs. This means being aware of the organization’s workings. It also means being aware of the vital resources it must safeguard. And it means being aware of any legal or regulatory obligations it has to fulfill.
Network Structure
Think about the topology and architecture of the network within the company. Knowing how external connections, internal networks, and traffic flow are organized entails. The current network infrastructure should be improved and complemented by the firewall strategy.
Factors to Consider When Securing a Firewall
Now, let us understand the factors to be considered when securing a firewall.
Location of Firewall
Identify the best location for the firewall for the network architecture. This can mean firewalls inside cloud environments. They can also be between network segments or at the network’s edge. Appropriate positioning guarantees efficient traffic management and filtration.
Policies for Access Control
Create and implement strong access control policies. Use clear firewall rules. This involves defining the allowed and banned IP addresses, ports, and protocols. The rules come from the company’s security specs and operational needs.
Configuration of the Default Rule
Set up your firewall’s default rules to automatically block all traffic. Limiting the attack surface and blocking unauthorized access is key. It guarantees that only authorized traffic is allowed.
Hierarchy of Rules
Create a clear rule hierarchy. Rank rules by their importance and level of detail. This ensures that narrow rules come before broad ones. It makes traffic processing efficient.
Prioritize firewall rules according to their significance and level of detail. Arrange them in an obvious hierarchy. This tactical configuration guarantees the primacy of particular rules over more general ones. It optimizes the defense mechanism for dedicated servers and expedites traffic processing.
Stateful Examining
Many contemporary firewalls have a feature called stateful inspection. It monitors the status of active connections.
Stateful firewalls can understand the connection status and make better decisions. They base their decisions not only on individual packets. They also consider the context of the entire communication.
Logging and Monitoring
Firewalls frequently include logging features to record information about permitted and prohibited traffic.
It is imperative to monitor firewall logs for possible security breaches. It’s also necessary to examine network behavior and modify firewall rules.
Frequent Evaluations and Audits
Perform routine security audits and assessments to gauge how well firewall setups work. Finding and fixing flaws may need vulnerability scanning. It may also need penetration testing and rule set reviews.
Can Hackers Get Past Firewalls?
Credits: Freepik
Firewalls help stop and lessen the impact of many cyberattacks. Still, it’s important to recognize that no security solution is 100% reliable, and skilled hackers may be able to get past or breach firewalls.
Exploiting weaknesses in the firewall’s hardware or software is one technique hackers may use to get around firewalls. The firewall may have known flaws. Hackers could use them to get unauthorized access. However, applying security patches regularly can prevent this. So, keeping the firewall resilient requires applying updates and patches on time.
In conclusion, firewalls are an essential first line of defense against online attacks. However, their effectiveness depends on how well they are configured, how often they are updated, and how closely they are watched.
Hackers can bypass firewalls using many techniques. This highlights the need for a thorough cybersecurity plan. The plan should include proactive threat intelligence, user education, and multiple defenses.
Dedicated servers are a key security component. They work with firewalls to make a strong barrier against online attacks. These servers are often used for important websites, databases, and applications. They rely on firewalls to control and filter traffic. Data confidentiality and integrity depend on dedicated servers and firewalls working together harmoniously.
We will discuss Windows firewall best practices in the next section.
Also read Does Your Organization Needs An Intrusion Detection System?
Windows Firewall Configuration Best Practices
Now we will understand the core part of our blog, i.e. windows firewall rules best practices, in detail.
Firewall Rules Best Practices # 1: Regularly Update the Firewall Rules
You must regularly reevaluate and update firewall rules. This is key to keeping strong and adaptable security. This technique involves limiting the attack surface. It does this by removing unneeded restrictions and allowing only necessary traffic.
The firewall adapts to new threats and changing business needs. It does this by managing rule sets. This guarantees that it will always be strong.
Updates are frequent. They include rules to fine-tune for network changes. And to change configurations in response to business needs.
This plan improves the firewall’s ability to stop threats. It also ensures that security policies stay current. This is important because the cybersecurity environment is always changing.
Firewall Rules Best Practices # 2: Implementing the Principle of Least Privilege
Security has a main tenet. It is to use the least privilege principle in making firewall rules. Organizations reduce potential vulnerabilities by allowing only necessary traffic and services. They limit access based on predetermined standards.
This method improves security by cutting exposure to potential attacks. It ensures that the firewall only allows necessary traffic for authorized processes.
After making rules, the principle of least privilege requires ongoing audits. These audits reevaluate and improve rules. They adjust rules to changes in business processes. This reduces the risk of unauthorized access. This improvement strengthens the firewall’s position as a proactive guardian against security threats.
Firewall Rules Best Practices # 3: Utilizing Advanced Security Features
Using advanced security features improves the firewall. They include authenticated bypass and connection security rules. These traits offer a sophisticated defense. They add extra protection against specific threats.
For example, network security rules allow the firewall to enforce secure connections. They also enforce encryption. This gives data in transit an added layer of confidentiality. Bypass rules let you safely access specific services. They do this by increasing the firewall’s flexibility.
Organizations can customize their defenses to specific threats. They can do this by including these new technologies in their firewall strategy. This ensures better security. It can withstand complex cyber-attacks and changing attack vectors.
Firewall Rules Best Practices # 4: Enabling Logging for Monitoring
To perform proactive monitoring and analysis, you must enable firewall logging. An in-depth analysis of permitted and prohibited traffic offers insight into network activity. Reviewing the logs, you can spot risky trends, setup errors, or suspicious behaviors.
Logging helps with forensic investigation. It also improves network security management. This makes security stronger.
It provides quick anomaly detection and reaction. It also shows the features and origins of threats. Also, logging is crucial for meeting audit and compliance needs. It does so by providing a record of all firewall activity.
Organizations can improve. They can do this by using logs to make decisions. This will help them stop new threats and keep strong security.
Firewall Rules Best Practices # 5: Implementing Default Deny Rules
Setting up default refuse rules is a preventative security precaution. Organizations greatly reduce the danger of exploitation. They do this by allowing only necessary communication and blocking all other communication.
This method guarantees that any unauthorized or unexpected traffic is immediately rejected. It acts as a strict first line of defense against possible attacks.
A zero-trust security architecture assumes all traffic is untrusted until authorized. It is enabled by default to deny rules. This strategy reduces the attack surface. It makes it harder for adversaries to exploit weaknesses.
Organizations can stay ahead of new threats by reviewing the rejected rules. They can also improve the rules. This helps ensure the firewall stays effective. It also helps it adapt to changing cybersecurity risks.
Firewall Rules Best Practices # 6: Using Private and Public Profile Domains
You can make custom rule sets using Windows Firewall profiles. You can make them for each network location. Security rules will adjust to trust levels in different network settings. This happens because separate rule sets are used.
This offers fine-grained control over traffic. Enterprises can impose setups based on if a device is linked to a public, private, or trusted network.
For example, the public profile can have stronger restrictions. This will improve security when connecting to untrusted networks. In contrast, the domain profile can have more relaxed rules. They support trusted internal interactions.
Firewall Rules Best Practices # 7: Enabling Stealth Mode for Unnecessary Services
Stealth mode increases system security. It does this by making extra services less visible to attackers. This proactive solution prevents the system from responding to certain network probes. It also stops it from responding to unsolicited requests. This reduces the chance of reconnaissance and possible exploitation.
Organizations can improve their security and reduce the risk of targeted attacks. They can do this by making the system harder to detect. Stealth mode adds an extra layer of obscurity. It makes it harder for attackers to find entry points. Therefore, it is especially important to prioritize services that do not require exposure.
Firewall Rules Best Practices # 8: Regularly Updating the OS
Updating Windows is essential. It fixes security holes. They could be used to get over firewalls. Patches and upgrades come often. They make the system more secure and better at defending against new threats.
Updates happen often. They fix known vulnerabilities. This lowers the chance of exploitation and increases the firewall’s efficacy. Upgrades to the operating system make it more stable and fast. They fix security flaws and add new features and improvements.
Firewall Rules Best Practices # 9: Using Network Segmentation
Using firewall rules with network segmentation is a smart move. It will improve security. This technique entails splitting the network. It involves configuring firewall rules to control traffic. The rules apply to isolated network segments.
It stops threats from moving through the network. This helps contain security issues. Organizations can improve network resilience. They can also lessen the effect of breaches by dividing the network.
This strategy is especially good at reducing the effects of a security issue. It confines the hacked area and stops risks from spreading.
Firewall Rules Best Practices # 10: Educating Users About Firewall Alerts
Teaching end-users about firewall warnings is essential. It’s part of a good cybersecurity plan. Encouraging users to submit abnormalities or unexpected notifications helps the group. It improves their knowledge of possible security incidents.
User education emphasizes a team approach to security. It makes people essential for defense against cyberattacks. Users can actively improve network security. They can do this when organizations have a culture of awareness and responsiveness.
Firewall Rules Best Practices # 11: Encrypting Network Traffic Using VPN
Communications are further secured when Virtual Private Networks (VPNs) encrypt network traffic. VPNs create safe, encrypted connections. They span networks you might not trust. They prevent the interception of confidential information.
Organizations ensure the integrity and privacy of data. They do this by encrypting it as it travels between networked systems. This is crucial when sending sensitive data over public networks. It’s also key when connecting to distant networks.
Firewall Rules Best Practices # 12: Implementing Two-Factor Authentication
Multi-factor authentication (MFA) protects network security against unwanted access. With MFA, users must verify their identity. They do so with various techniques, including security tokens, biometrics, and passwords.
This procedure greatly reduces the chance of unwanted access. Even if someone steals login credentials, this remains true. Organizations can improve access restrictions. They can make sure that only authorized users can interact with network resources. They can do this by combining MFA with firewall policies.
Conclusion
In summary, putting strong firewall rules in place is essential. Following best practices ensures network security. Every recommended practice is essential to constructing a solid defense. It protects against changing cyber threats. Organizations can strengthen their networks completely by employing complex security technologies. These include VPNs and Multi-Factor Authentication. They can also turn on the Windows Firewall as an essential precaution. We learned firewall rules best practices in detail.
Additional factors that support a proactive security approach include user education. They also include dynamic rule administration and routine updates. Taken together, these procedures create a strong architecture. It can stop unwanted access and adapt to cybersecurity changes.
Organizations may strengthen their cybersecurity strategy with a reliable partner. They can coordinate these firewall best practices with RedSwitches. Turning on the Windows Firewall provides a basis for a secure network. Establishing centralized management via Group Policy also helps. Our dedication to reliable infrastructure reinforces this foundation.
FAQs
Q. Firewall Rules Best Practices: What are the best practices for firewall implementation?
For the best protection, use network segmentation. Enforce default refuse rules and update firewall setups frequently.
Q. What are the best firewall settings?
Using VPNs for encryption will improve firewall defenses against online attacks. Configuring default refuse rules and turning on logging are also effective.
Q. What is a strong firewall?
Strong firewalls enforce the least privilege principle. They also maintain an updated defense against cyber threats. They do this by using features like VPN encryption. They also use authenticated bypass rules and connection security rules.
Q. Firewall Rules Best Practices: What are the best practices for ensuring security through firewall rule configuration?
Updating and optimizing the firewall rules regularly is essential to ensure security through firewall rule configuration. Additionally, it’s important to configure the firewall to allow only necessary outbound and inbound traffic by default.
Q. How can I configure firewall rules to enhance security?
You can enhance security by ensuring that your firewall rules restrict access to your network based on source and destination IP addresses. Implementing a policy to allow only approved traffic can also help in configuring firewall rules for improved security.
Q. What steps should be taken to update firewall rules regularly?
Regular update of firewall rules involves reviewing the rule base to identify outdated or redundant rules and removing or modifying them accordingly. It’s important to also stay informed about the latest security threats and adjust the rules to mitigate potential risks.
Q. Firewall Rules Best Practices: Why is change management crucial in firewall rule configuration?
Change management is crucial in firewall rule configuration to ensure that any changes made to the rules are properly documented, reviewed, and approved. This helps in maintaining the security posture and avoiding unintended security gaps.
Q. What are the key considerations for configuring regular firewall rules?
When configuring regular firewall rules, it’s important to understand your network’s traffic patterns clearly and implement rules that align with the organization’s access control policies and security best practices.
Q. Firewall Rules Best Practices: How can firewall rule configuration be optimized for improved performance?
Firewall rule configuration can be optimized for improved performance by organizing the rules logically, minimizing overly broad rules, and leveraging next-generation firewall features where applicable.
Q. Firewall Rules Best Practices: What are the essential aspects of firewall security best practices?
Firewall security best practices include implementing a comprehensive set of rules, regularly reviewing and updating the rules, and ensuring that the firewall management solution or tool provides detailed logs for monitoring and analysis.
Q. What is the significance of outbound traffic in firewall rule configuration?
Outbound traffic plays a significant role in firewall rule configuration as it determines which traffic originating from within the network can pass through the firewall. Properly configuring outbound rules is crucial for preventing unauthorized data exfiltration.
Q. Firewall Rules Best Practices: How can I ensure that my firewall rule configuration aligns with security policies and access control lists?
You can ensure alignment with security policies and access control lists by regularly reviewing and updating the firewall rules based on the latest security posture, and conducting periodic audits to verify compliance with the defined policies and lists.
Q. Firewall Rules Best Practices: What are the recommendations for configuring firewall rules to manage network security effectively?
Recommendations for effectively managing network security through firewall rule configuration include setting up a robust change management process, leveraging a new firewall with advanced features, and establishing a security team responsible for maintaining the rule base and policy rules.