Internet connectivity is critical to the operations of Linux servers, especially those hosting business or user-facing applications.
Linus offers several utilities to monitor and examine network and Internet connectivity so that admins and users can pick the best fit for their specific requirements.
netstat (Network Statistics) is a popular utility that admins use to examine and verify several aspects of your computer’s internet connection. It can provide information about the incoming connections, the communication channels in use, and even technical specifics like the quantity of data packets being delivered and received.
In this tutorial, we will start with an overview of the netstat utility and then illustrate with examples that show the capabilities of the utility in practical scenarios.
Table Of Contents
- An Overview of the netstat Command
- Examples of Using netstat for Network and Traffic Analysis
- Prerequisites
- Example #1: List Every Port and Connection
- Example #2: List Every TCP Port
- Example #3: List Every UDP Port
- Example #4: List Only the Listening Ports
- Example #5: Show Statistics For Each Protocol
- Example #6: List Transactions using Network Interfaces
- Example #7: Display the Extended Kernel Interface Table
- Example #8: Show Masqueraded Connections
- Example #9: Display PID/Application Mapped to Connections
- Example #10: List all Listening Programs
- Example #11: Display Kernel IP Routing Table
- Example #12: Show Membership in IPv4 and IPv6 Groups
- Example #13: Print the netstat Information Regularly
- Example #14: List Critical Details
- Example #15: Show User IDs, Port Numbers, Host Addresses, and Numerical Addresses
- Example #16: Locate a Process Using a Specific Port
- Example #17: List Every Option for Netstat
- Conclusion
- FAQs
An Overview of the netstat Command
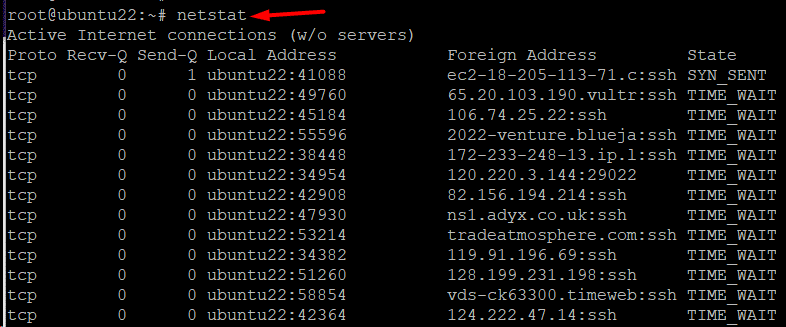
Initially introduced in 1983, netstat has been a popular choice for monitoring network traffic and connectivity. It is mainly used without any parameters in the following format:
# netstat
The output’s first list shows the computer’s active, established internet connections. The columns include the following information:
- Proto – The connection’s protocol (TCP or UDP).
- Recv-Q – Presents the queue of received or pending bytes.
- Send-Q – Presents the ready-to-be-sent bytes in a queue.
- Local address – Details on the local connection’s port and address. If a port hasn’t been set yet, an asterisk (*) in the host indicates that the server is listening.
- Foreign address—the port and address data for the connection’s remote server end. If a port is not yet established, you will see an asterisk (*).
- State – The local socket’s state, which is often blank, closed, listening, or established.
In addition, you can see a second list of the currently open sockets. This list provides the following information about the sockets:
- Proto – The socket’s protocol, which is always unix.
- RefCnt – The number of processes connected to this socket.
- Flags – Blank or ACC are typical values.
- Type – The socket type.
- State – The socket’s state can be blank, LISTENING, CONNECTED, or other.
- I-Node – This socket’s file system inode is the index node.
- Path – Systems path to the socket.
Examples of Using netstat for Network and Traffic Analysis
Now that you have a good idea of the fundamentals, let’s see the utility in action. But before that, let’s take a quick look at the prerequisites.
Prerequisites
- You have a system running a mainstream Linux distribution.
- A user account with root or sudo privileges.
Example #1: List Every Port and Connection
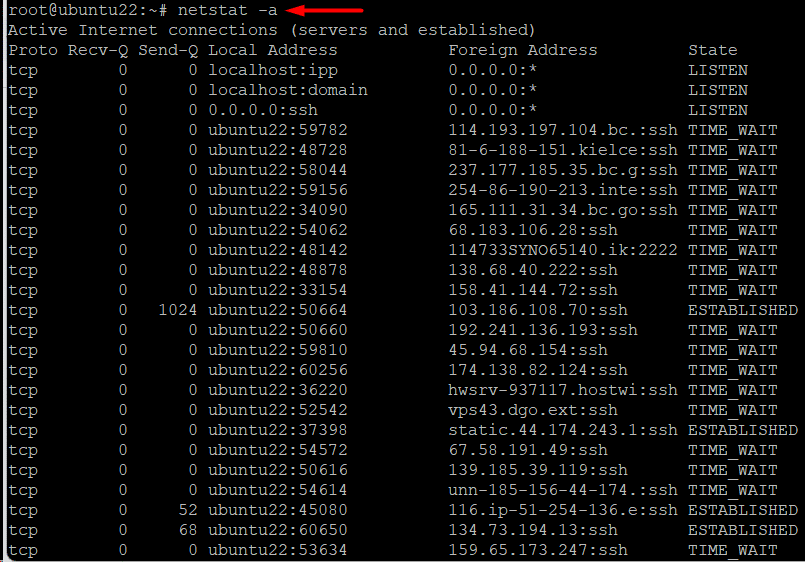
A common use case of the netstat command is to get a list of all ports and connections, separated by their protocol or state. For this, use the following command:
# netstat -a
The output shows the open or listening servers, along with the current connections.
Example #2: List Every TCP Port
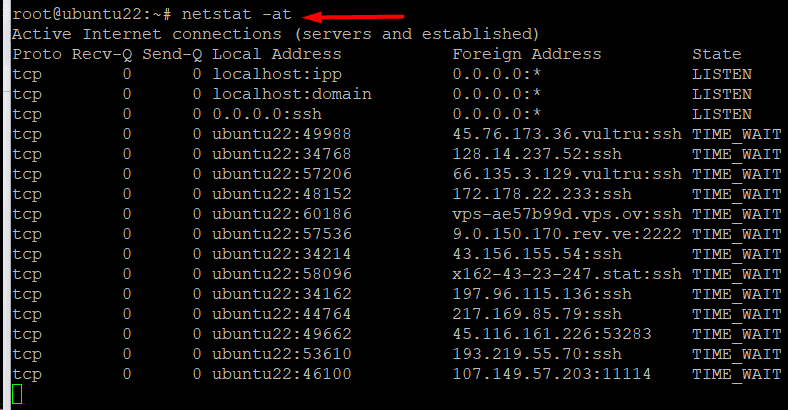
You can list only the TCP ports with the following command:
# netstat -at
Example #3: List Every UDP Port
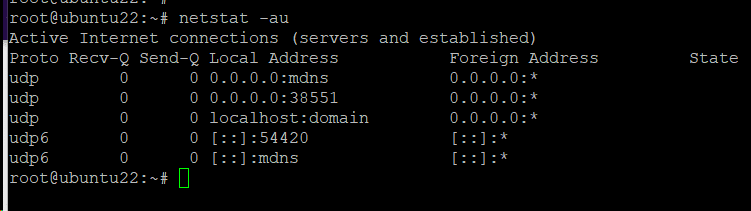
Alternatively, you can list every UDP port on the system with the following command:
# netstat -au
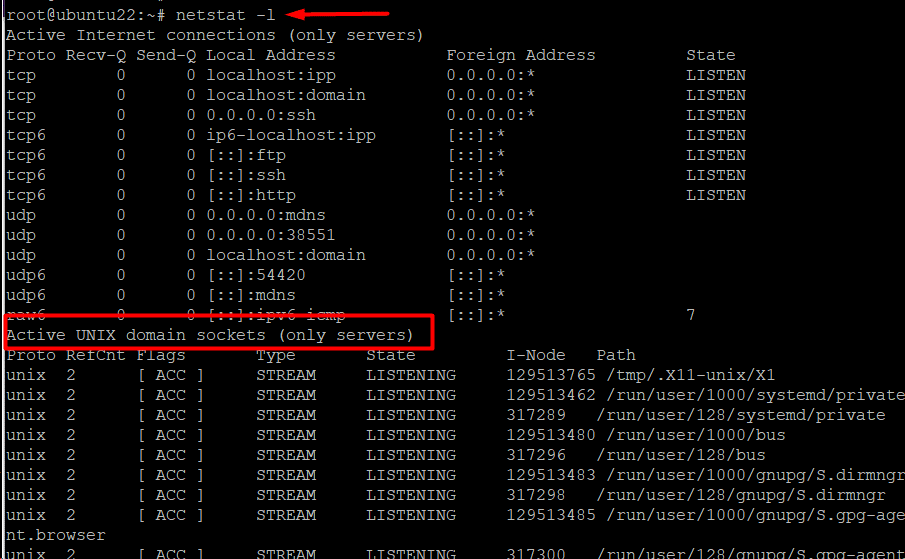
Example #4: List Only the Listening Ports
Use the following command to get a list of all protocols’ listening ports:
# netstat -l
Next, we will see how you can drill down to the listening ports mapped to specific protocols.
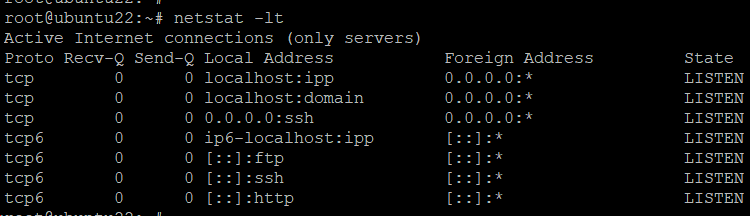
List TCP Listening Ports
You can list all system ports mapped to the TCP protocol with this command:
# netstat -lt
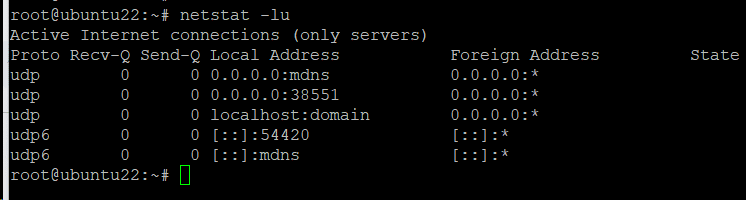
List UDP Listening Ports
Similarly, you can list only the UDP ports that are listening for incoming connections by running the following command in the terminal:
# netstat -lu
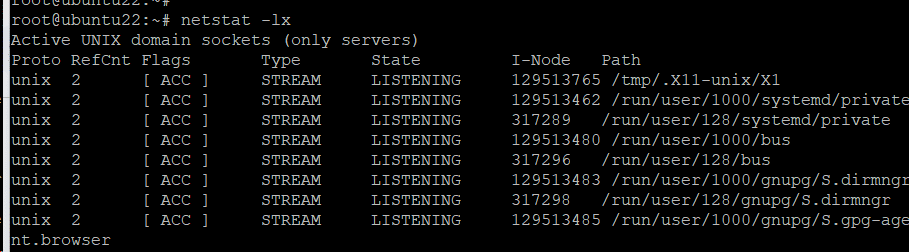
List the UNIX Listening Ports
Use the following command to get a list of UNIX listening ports:
# netstat -lx
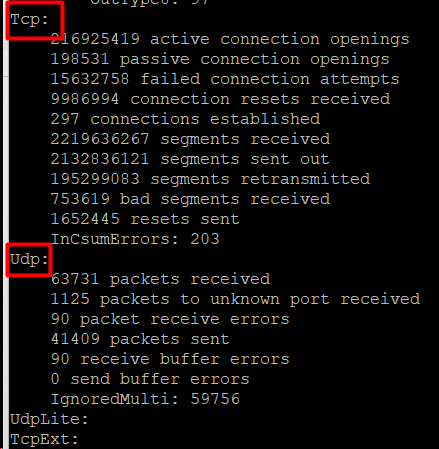
Example #5: Show Statistics For Each Protocol
You can format the output to show ports mapped to a specific protocol. This allows you to quickly view all the ports for a protocol.
# netstat -s
You can further filter down this data for specific protocols.
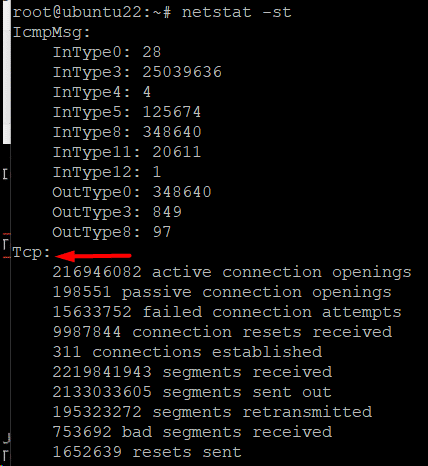
List Statistics for TCP Ports
You can list only the TCP port statistics with the following command:
# netstat -st
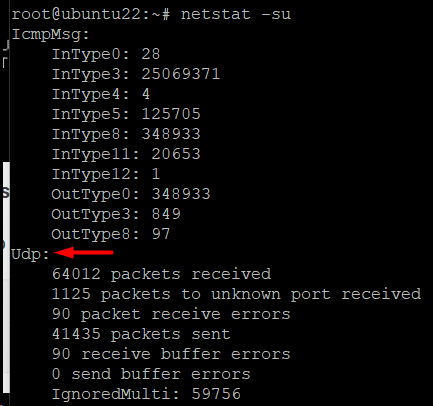
List UDP Port Statistics
Use the following command to display statistics for UDP ports:
# netstat -su
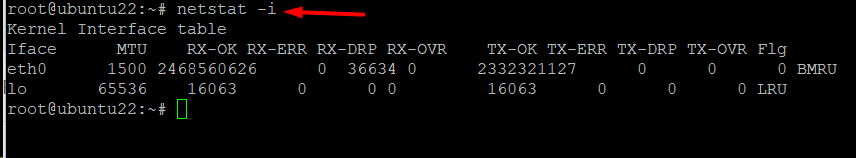
Example #6: List Transactions using Network Interfaces
Use the following command to view MTU transactions in the kernel interface table, including packet transfers and receipts:
netstat -i
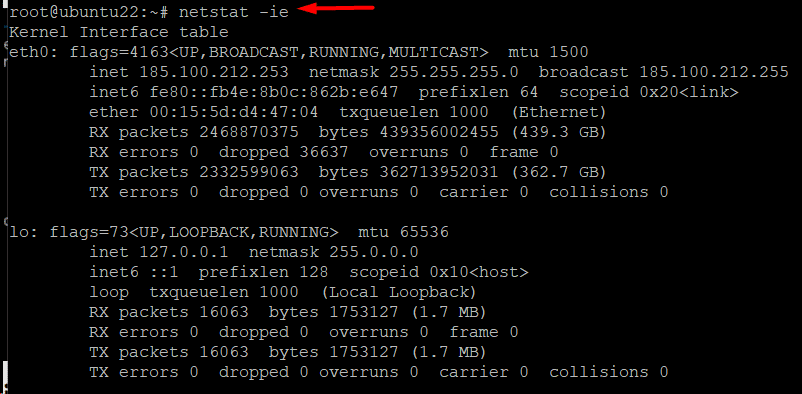
Example #7: Display the Extended Kernel Interface Table
You can list more details about the kernel interface table’s details by adding the -e option to the netstat -i command. The command, in this case, would be as follows:
# netstat -ie
Example #8: Show Masqueraded Connections
You can see the masquerade connections on your system by running the following command in the terminal:
# netstat -M
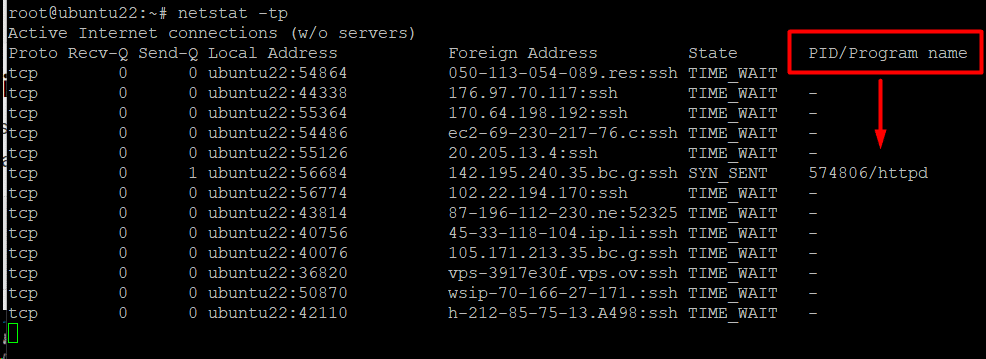
Example #9: Display PID/Application Mapped to Connections
You can see the process (process ID, to be precise) or the application connected to connections. This information can help you understand which application or process is using a specific connection.
We recommend the -p option for the netstat command to add this information to the output. For instance, the following command shows the PID and applications connected to the TCP connections:
# netstat -tp
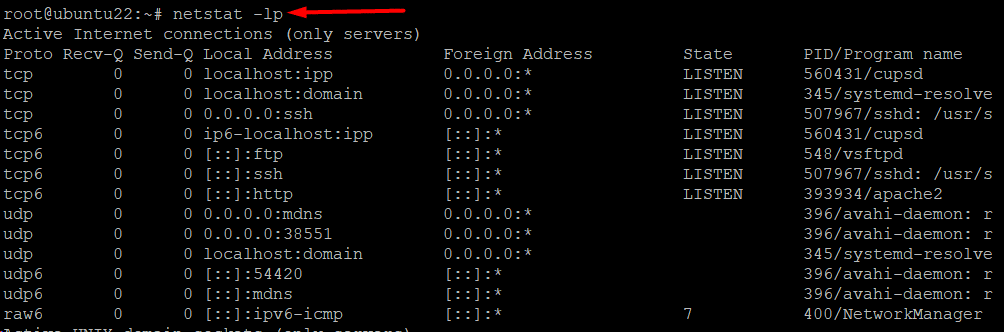
Example #10: List all Listening Programs
You can list all applications that are currently listening for incoming requests with the following command:
# netstat -lp
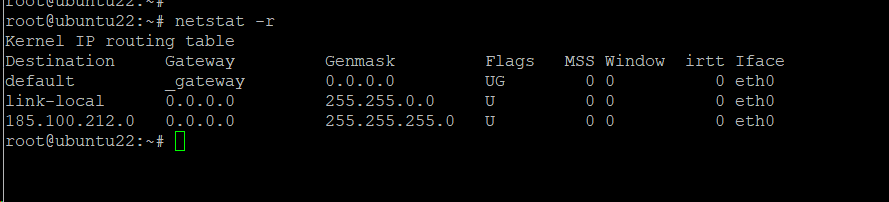
Example #11: Display Kernel IP Routing Table
The system uses the kernel IP routing table as an important factor in the packet forwarding process. You can list down the details in this table with the following command:
# netstat -r
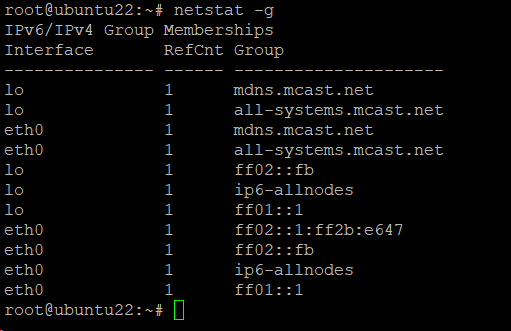
Example #12: Show Membership in IPv4 and IPv6 Groups
The following command shows the IPv6/IPv4 group membership:
# netstat -g
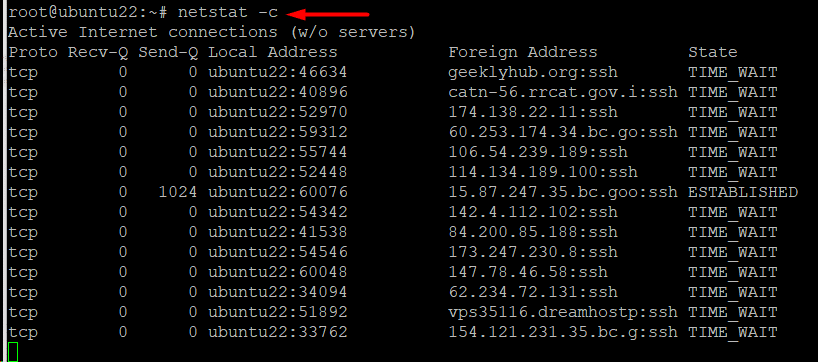
Example #13: Print the netstat Information Regularly
You can print the netstat data every second by adding the -c option to the command. The syntax in this case would be as follows:
# netstat -c
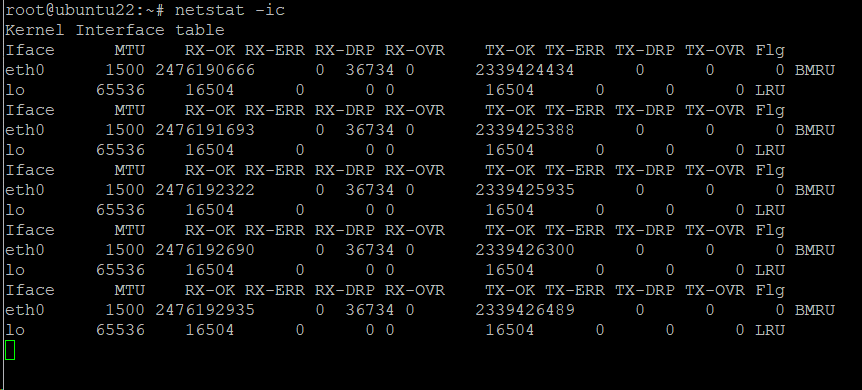
You can further combine other options to print other relevant information. For instance, the following simple command prints the kernel interface table continually.
# netstat -ic
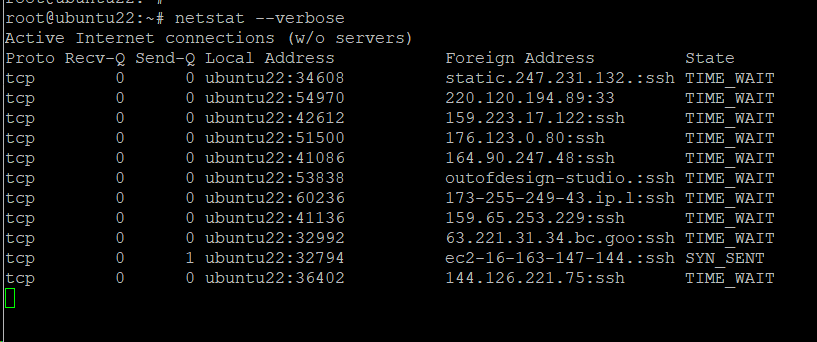
Example #14: List Critical Details
You can list more information by running the following command in the terminal:
# netstat --verbose
Example #15: Show User IDs, Port Numbers, Host Addresses, and Numerical Addresses
When possible, the utility converts addresses, port numbers, and user IDs into human-readable names by default. We will now discuss several scenarios where you can use the netstat utility to print specific information.
Display addresses in numbers using:
# netstat -n
Run the following command to display host addresses as numbers:
# netstat --numeric-hosts
Run the following command to display ports as numbers:
# netstat --numeric-ports
You can use the following command to see user IDs as numbers:
# netstat --numeric-users
Example #16: Locate a Process Using a Specific Port
We recommend using the grep utility to filter the data presented by netstat. For instance, run the following command syntax to locate a process using a specific port number:
# netstat -an | grep ':[port number]'
For instance, consider the following command that extracts data about port 80:
# netstat -an | grep ':80'
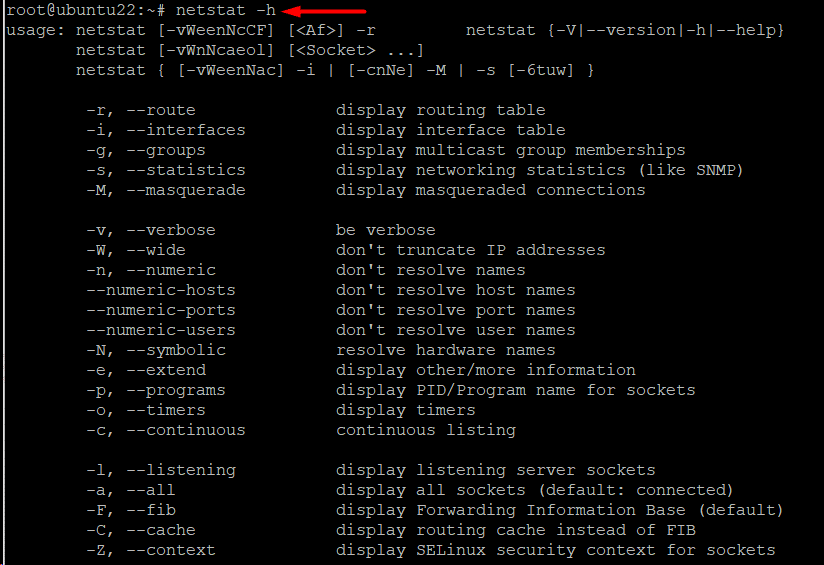
Example #17: List Every Option for Netstat
netstat is a very versatile utility, mainly because it supports a huge range of options. We recommend the following command to list all supported commands:
# netstat -h
Also Read: lsof Command in Linux with Examples
Conclusion
The Linux netstat command is an effective tool for network monitoring and troubleshooting, providing a large range of options and commands to collect comprehensive data about interface statistics, routing tables, network connections, and other topics.
Users can get insights into the network activity of their system, diagnose connectivity problems, spot potential security risks, and improve network performance. Linux administrators can ensure seamless and successful system operation and effective network infrastructure management by becoming proficient with the Netstat tool.
Experience the power of seamless hosting with RedSwitches, your dedicated hosting provider globally. We empower your online presence with unparalleled reliability, security, and performance. If you’re looking for a robust server for your Linux projects, we offer the best dedicated server pricing and deliver instant dedicated servers, usually on the same day the order gets approved. Whether you need a dedicated servers, a traffic-friendly 10Gbps dedicated server, or a powerful bare metal server, we are your trusted hosting partner.
FAQs
Q. What is the Netstat command used for in Linux?
The Netstat command displays network-related information in Linux, such as active network connections, routing tables, interface statistics, and more.
Q. How do I display all active network connections using Netstat?
The command netstat—tuln displays all active TCP and UDP network connections, along with their associated port numbers and states.
Q. Can Netstat show listening ports on my Linux system?
Yes, you can use the command netstat -tuln to show all listening ports on your Linux system.
Q. How do I filter Netstat output to display TCP connections only?
You can use the command netstat -at to display TCP connections only.
Q. Is it possible to view UDP connections with Netstat?
Yes, you can use the command netstat -au to view UDP connections.
Q. How can I determine which process uses a specific port with Netstat?
You can use the command netstat -tulpn to display active TCP and UDP connections along with the process ID (PID) and program name.
Q. Can Netstat display the routing table information?
You can use the command netstat -r to display the routing table information.
Q. How do I continuously monitor network connections with Netstat?
You can use the command netstat -c to monitor network connections, continuously displaying updates every second.
Q. Can I use Netstat to detect network performance issues?
Yes, Netstat can help identify network performance issues by displaying network statistics such as packet counts, errors, and collisions.
Q. What are some advanced options and parameters available with the Netstat command?
Some advanced options include -s option for summary statistics, -p to show the PID and program name, and -i to display interface statistics.