Do you know that automated scripts and bots scan for open ports during the initial surveillance before an attack?
Ports the entry and exit points from the information travels across your devices, servers, and networks. That’s why securing the ports is often the first action item on system security checklists.
But before doing that, you should know which ports are open and accessible on your system. This is a critical exercise because many system and user applications can open ports on your system without any prior indication.
In this tutorial, we’ll introduce Nmap, an excellent tool for scanning and identifying open ports. We’ll start with an introduction to the tool and then show you how to find open ports using Nmap. We’ll finish with an actionable list of tips for securing ports on your devices.
But first, let’s have a brief look at the idea of ports on a system.
Table Of Contents
- What Are Open Ports
- A Quick List of the Standard Server Ports
- Why Do You Need Nmap For Securing System Ports
- Applications of Nmap (Beyond Port Scanning)
- Nmap Scan Tips for Better Results
- Conclusion
- FAQs
What Are Open Ports
In networking, a port is a virtual point from where data comes in and goes out of a system. For example, almost all devices accessing the Internet use port 80 for HTTP connectivity and port 110 for email communication.
A port in a system acts as a pathway to a specific virtual or physical location. At a given time, a system can have several open ports to segregate the traffic from diverse sources and protocols.
That’s where the role of a firewall becomes critical in system security. A firewall acts as a security guard for the system’s ports. It uses pre-configured rules to decide which port should be open or closed. It also controls what information can go through specific ports.
A Quick List of the Standard Server Ports
In most cases, a typical server usually has the following available ports. Note that the firewall rules control which ports are accessible on a server.
- 21 – FTP (File Transfer Protocol): Used to transfer files between computers.
- 22 – SSH (Secure Shell): Securely connects to a server for command-line access.
- 25 – SMTP (Simple Mail Transfer Protocol): Sends emails.
- 53 – DNS (Domain Name Service): Resolves domain names to IP addresses.
- 80 – HTTP (Hypertext Transfer Protocol): Accesses websites.
- 110 – POP3 (Post Office Protocol 3): Retrieves emails from a server.
- 123 – NTP (Network Time Protocol): Synchronizes computer clocks.
- 143 – IMAP (Internet Message Access Protocol): Manages email on a server.
- 443 – HTTPS (Hypertext Transfer Protocol Secure): Secures web server connections.
- 465 – SMTPS (Secure SMTP): Sends secure emails.
- 631 – CUPS (Common Unix Printing System): Manages print jobs on a server.
- 993 – IMAPS (Secure IMAP): Securely manages email on a server.
- 995 – POP3S (Secure POP3): Securely retrieves emails from a server.
Why Do You Need Nmap For Securing System Portis Needed
Nmap, short for Network Mapper, is a powerful tool that scans and maps networks to find out what services are active on the connected devices. Since services interact with ports for sending and receiving data, Nmap also builds a list of open ports during the scan process.
You can use the information Nmap collects about your network to harden system security by properly managing the services and ports.
How to Find Open Ports Using Nmap
Nmap is a powerful tool for scanning and identifying open ports, providing insights crucial for understanding the network environment’s security.
We’ll now explore how to scan open ports on your computer using the Nmap’s easy-to-follow commands.
Important: Nmap is usually not available on many Linux distributions. If that’s the case with your system, you should first install it using your distribution package manager.
Prerequisites
Before diving into port scanning with Nmap, ensure you have the following:
- A system running a mainstream Linux distribution
- Access to a command line/terminal
- A user account with sudo/root privileges
Scan Your Network to Find Open Ports by Nmap
Launch the terminal and enter the following command in the terminal:
# sudo nmap 192.168.xx.xx
Remember to replace “192.168.xx.xx” with the actual IP address of the computer you want to check. This basic Nmap command gives you useful information about the status of ports on that specific system.
You can use the following Nmap commands to scan a website, a range of IP addresses, or more:
Scan a website/host:
# nmap www.hostname.com
Scan a range of IP addresses (e.g., .1 – .10):
# nmap 192.168.0.1-10
Scan a list of targets from a text file:
# nmap -iL examplefile.txt
Scan a whole subnet:
# nmap 192.168.0.1/13
These variations of the Nmap commands let you scan ports on your system based on your specific needs.
Examples of Nmap Port Scanning
Nmap is a very flexible utility, and you can use various flags and options to conveniently scan a single port, a range of ports, or even an entire series of IP addresses.
Single Port Scan (i): Use the following command to scan port 80 on the target system:
# nmap -p 80 192.168.xx.xx
Single Port Scan (ii): Use the following command to scan a range of ports 1 through 200 on the target system:
# nmap -p 1-200 192.168.0.1
Port Series Scan: You can carry out a fast scan of the most common ports directly in the terminal with this command:
# nmap -F 192.168.xx.xx
Scan All Ports: You can initiate a detailed scan of all ports (1 – 65535) on the system with the following command:
# nmap -p- 192.168.0.1
Nmap Port Scanning: Special Cases
Beyond the basic port scanning, Nmap offers various specialized scan options that cover specific scenarios. Let’s discuss some of these scenarios:
TCP Connect Scan: The TCP Connect scan takes longer, but it has more chances of establishing the connection:
# nmap -sT 192.168.0.1
SYN Port Scan: The default SYN (synchronize) scan tests ports by establishing only half of the connection, similar to a TCP handshake.
# nmap -sS 192.168.0.1
UDP Port Scan: You can instruct Nmap to scan UDP ports instead of TCP ports. This is a critical security check because malware can use UDP ports to communicate:
# nmap -sU -p 80,130,255 192.168.0.1
Fast Port Scan: You can run a fast scan on the target system, bypassing host discovery (This is useful for firewalls that do not respond to ping requests):
# nmap -Pn -F 192.168.0.1
Applications of Nmap (Beyond Port Scanning)
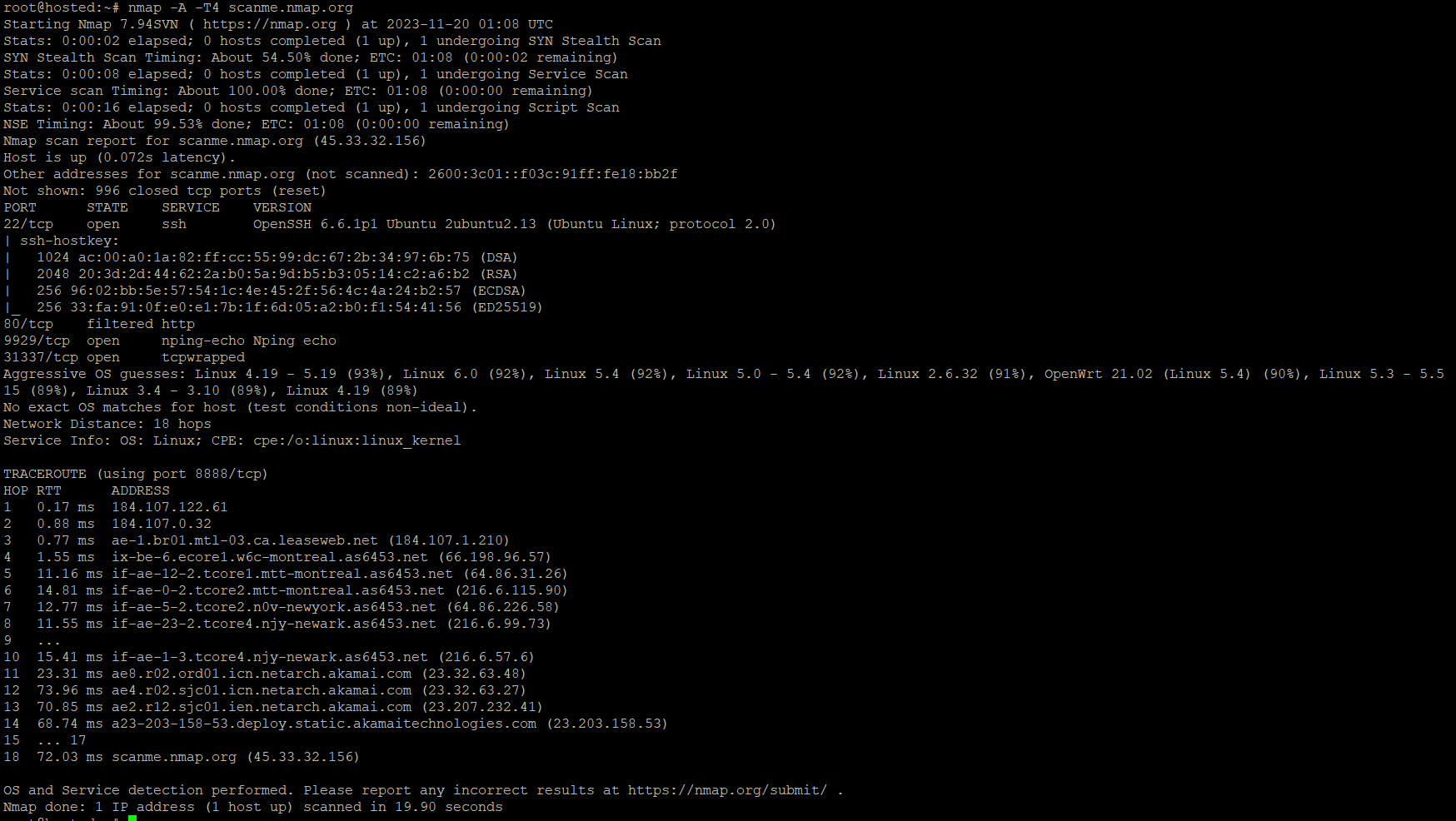
Nmap is versatile enough to be applied beyond simple port scanning. For instance, you can detect the OS on the target system with the -A flag:
# nmap -A 192.168.0.1
Furthermore, it can map out the services using different ports:
# nmap -sV 192.168.0.1
You can check the Nmap manual to see more options for applying the utility for advanced system security scenarios.
Nmap Scan Tips for Better Results
Now that you know how to use Nmap, let’s explore some tips for making the most of using Nmap to find open ports on your system.
Permission Matters: Always scan servers you own or have explicit permission to scan. Using Nmap on servers for which you don’t have permission can constitute a legal issue.
Mindful Rescanning: Repeatedly scanning the same target can overload the server and cause performance issues. Always ensure suitable gaps between scans to avoid server overload.
Stay Vigilant: Watch out for unusual results during scanning, especially for services active on non-standard port numbers. These results can indicate misconfigured/mismapped services or, worse, unauthorized applications/processes exchanging data without permission.
Opt for Targeted Scanning: Use OS and Service scanning options to examine specific ports or services.
Know Your Ports: Understanding your system’s port assignment and usage is critical for identifying deviations. For instance, any port below 1000 assigned to a non-system application or process can signal security concerns.
Conclusion
Nmap is an invaluable tool for network administrators and security professionals. Following the steps outlined in this guide, you can effectively scan and identify open ports, enhancing your network’s security.
For those requiring robust hosting solutions, consider RedSwitches, known for its high-performance and secure infrastructure, ideal for intensive applications and services. Check out our dedicated servers, a traffic-friendly 10Gbps dedicated servers, or a powerful bare metal server; we are your trusted hosting partner.
FAQs
Q. Is the use of Nmap legal?
Nmap is legal when employed for legitimate network administration and security purposes. Nevertheless, scanning networks without proper authorization is illegal and unethical.
Q. Can firewalls or intrusion detection systems detect Nmap scans?
Yes, if you use Nmap in a way that’s too forceful or obvious, firewalls or detection systems might notice and react.
Q. Is Nmap suitable for beginners?
Nmap is designed to be user-friendly and is suitable for beginners. However, a foundational understanding of basic network concepts is beneficial for effective utilization.
Q. How does Nmap contribute to enhancing security?
Nmap helps improve security by identifying open ports and enabling the detection of potential vulnerabilities that attackers may exploit.
Q. What is Nmap’s role as a network mapper?
Nmap is a powerful network mapper, allowing users to explore and map network configurations efficiently.
Q. Can Nmap perform version detection during scans?
Nmap can perform version detection, providing valuable information about the software versions running on target systems.
Q. What is a client port, and how does Nmap handle it?
A client port is a port on the user’s machine used for communication. Nmap, during scans, interacts with client ports to establish connections and gather information.
Q. Does Nmap target popular ports during scans?
Nmap can target popular ports during scans, offering insights into commonly used services and potential security risks.
Q. How does Nmap handle unfiltered ports during a scan?
Nmap can identify unfiltered ports, providing information about ports that are neither open nor closed and contributing to a comprehensive network assessment.
Q. Can Nmap handle scanning a network range or IP range efficiently?
Certainly, Nmap is great for scanning a range of networks or specific IP addresses, giving you the flexibility to explore and assess a wide variety of systems.
Q. What are raw packets, and how are they utilized in Nmap scans?
Raw packets are unaltered data packets transmitted over a network. Nmap employs them to gather information during scans, allowing for efficient and precise data collection.
Q. What scan types does Nmap offer, and how do they differ?
Nmap provides various scan types, each tailored for specific purposes. Understanding the nuances of scan types is crucial for optimizing the scanning process.
Q. What is an open port, and why is it important to scan for them?
An open port is a communication endpoint on a computer that allows external devices to connect and communicate with the services running on the host. Scanning for open ports to identify potential security vulnerabilities and assess the overall network security posture is important.
Q. What are the different types of scans that can be performed using Nmap?
Nmap offers various scan techniques, including TCP connect scan, SYN stealth scan, UDP scan, and many more. Each scan type has its advantages and use cases depending on the specific requirements of the network scanning task.