Key Takeaways
- Dedicated server virtualization enhances resource utilization and performance.
- Virtualization on dedicated servers significantly reduces costs and increases IT efficiency.
- It provides enhanced security and isolation for virtual machines in a multi-tenant environment.
- Offers unmatched flexibility and scalability, facilitating rapid adaptation to changing business needs.
- Improves disaster recovery and high availability, minimizing downtime and ensuring business continuity.
- Requires careful consideration of hypervisor security, VM isolation, and secure virtual networking to protect against threats.
- Scalability, reliability, security features, support, and data center location are critical in choosing the right server for virtualization.
IT infrastructures need to be efficient, flexible, and scalable. This need is greater than ever in today’s changing digital landscape. Virtualization and servers are a powerful mix. Server virtualization revolutionizes how businesses allocate and oversee their computer resources.
This blog delves deeply into server virtualization. It exposes its many facets and highlights its big influence on computing today. We’ll look at how this integration optimizes resource use. It opens the door for innovation and growth. It does this by smoothly dividing real servers into virtual machines. And it gives unmatched performance and security benefits.
Prepare for a journey. It will demonstrate virtualization’s depths and highlight its strategic benefits in a server environment. This applies to all, regardless of your IT experience or if you are just a tech enthusiast.
Table of Contents
- Key Takeaways
- What is a Dedicated Server?
- What is Dedicated Server Virtualization?
- Types of Virtualization
- Advantages of Using Servers for Virtualization
- Key Considerations When Choosing a Server for Virtualization
- How Virtualization Works on Dedicated Servers
- Security Considerations in a Virtualized Environment
- Conclusion
- FAQs
What is a Dedicated Server?
Credits: Freepik
A dedicated server is fully devoted to a person, group, or program. This kind of server gives all its resources to one client. Shared hosting, in contrast, divides resources among many users. Under this agreement, the customer has complete control over the server. They can select the hardware, operating system, and customizations. From web hosting to complex data processing, a server is essential. It guarantees that the server’s resources are available to just one customer. This provides a customized, high-performance computing solution.
Moreover, servers provide more control and customization options. Customers can set up the server environment to meet their needs. This is especially useful for companies that run special or resource-hungry applications. This flexibility includes installing custom apps. You can change server settings as needed and pick the OS. Also, dedicated hosting often includes strong support from the hosting company. This support includes technical help, software upgrades, and hardware upkeep. They are to ensure the server runs well.
What is Dedicated Server Virtualization?
Splitting a single physical dedicated hosting server into several separate virtual servers, each operating as a distinct, independent server, is known as dedicated server virtualization. A hypervisor, another name for virtualization software, is used to accomplish this.
The real server has hardware, but the hypervisor tops it. The hypervisor enables virtual machines (VMs) and their development and administration. VMs replicate standalone servers and use a subset of the server’s resources, including memory, CPU, and storage.
Suppose you only utilize a small portion of the available space (server resources) for your everyday requirements despite owning a large, powerful apartment (your reliable dedicated server). A creative workaround is dedicated server virtualization, which lets you build several virtual apartments (virtual machines) on top of your current dedicated hosting server.
Each virtual computer has its own operating system, memory, and storage capacity, and it operates independently. This maximizes resource use and efficiency by allowing you to operate numerous apps or websites on a single physical server.
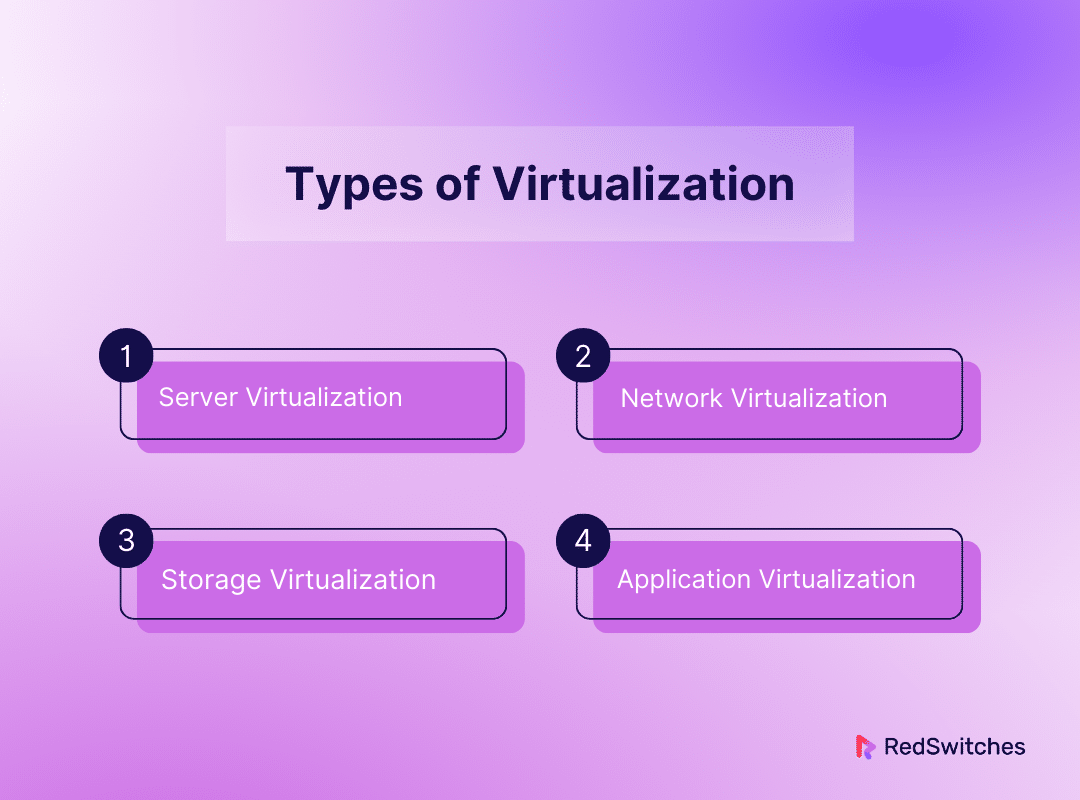
Types of Virtualization
Virtualization technology has changed how IT resources are deployed, managed, and scaled. It offers unmatched flexibility and efficiency. It imitates physical resources. These include networks, servers, storage devices, and whole desktops. They are imitated in a virtual form. This abstraction allows several virtual instances to run on a single physical hardware base. It makes the most of resources and makes IT operations more dynamic and cheaper. Here’s a thorough examination of the main varieties of virtualization:
Server Virtualization
It uses a hypervisor, a key software layer. The hypervisor splits one server into many virtual servers, each operating separately. This is how server virtualization transforms IT infrastructure. This new method makes computing better. It is more dynamic and cheaper. It also makes better use of hardware. Each virtual server is independent. So, one piece of hardware can support a diverse and flexible server environment. Each server can run its operating system and applications. This will lower hardware costs. It will also improve resource allocation. It will speed up server buying and setup. And it will create a strong disaster recovery framework.
Server virtualization enables quick replication and redeployment of server configurations. This greatly reduces downtime for maintenance and disaster recovery. Server virtualization also improves operational resilience and flexibility, doing so with agility and efficiency.
Network Virtualization
This technique creates a scalable and agile virtual network. It does this by hiding the complexity of the real network. This kind of virtualization combines hardware and software. It allows for more flexibility in allocating and managing network resources. It goes beyond the limits of physical virtualization. Virtual networks function without real hardware. This makes creating complex network setups, like VPNs, VLANs, and SDNs easy. This technology helps companies design new networking strategies. It also helps them optimize traffic flow and increase security through segmentation. And they can do this all without needing big changes to their network. Network virtualization is the foundation for creating safe, flexible, and resilient IT infrastructures.
Storage Virtualization
It combines resources from many devices into one entity. This entity is easily controlled. Storage virtualization is a big advance in data storage management. This layer of abstraction improves data management. It does this by streamlining backup, archiving, and recovery. It also simplifies the storage setup. Central storage management makes it easy for administrators to assign storage and move data. They can also build recovery solutions. They can do this without the headaches of managing many storage platforms. Also, storage virtualization is redundant and fault-tolerant. It ensures data is available and intact. It provides a strong foundation for data-driven enterprises.
Desktop Virtualization
Desktop virtualization separates the user’s desktop from the physical device. It offers a paradigm change in end-user computing. It lets users access personal computing resources on any device and anywhere. This method greatly improves IT security and management. It meets the rising demand for flexible and remote work. Sensitive data is kept in safe data centers, not on flimsy end-user devices. So, centralized desktop management reduces the danger of data breaches. Furthermore, desktop virtualization streamlines IT operations. It lowers the cost of PC ownership by making software updates, patches, and compliance easier. The flexibility and security offered by desktop virtualization make it an invaluable strategy for modern businesses aiming to empower their workforce while safeguarding their digital assets.
Application Virtualization
Application virtualization transforms program deployment and administration by separating apps from the underlying hardware and operating system. This isolation allows applications to be distributed and run in a self-contained environment on any suitable device without conventional installation procedures. Centralizing program management offers a consistent and safe user experience across all devices, reducing the strain of software upkeep, updates, and security patching. Additionally, application virtualization lessens software conflicts and makes operating systems more compatible, which improves operational efficiency. Application virtualization helps businesses stay competitive, adaptable, and agile by optimizing application deployment and access in a quickly changing technology landscape.
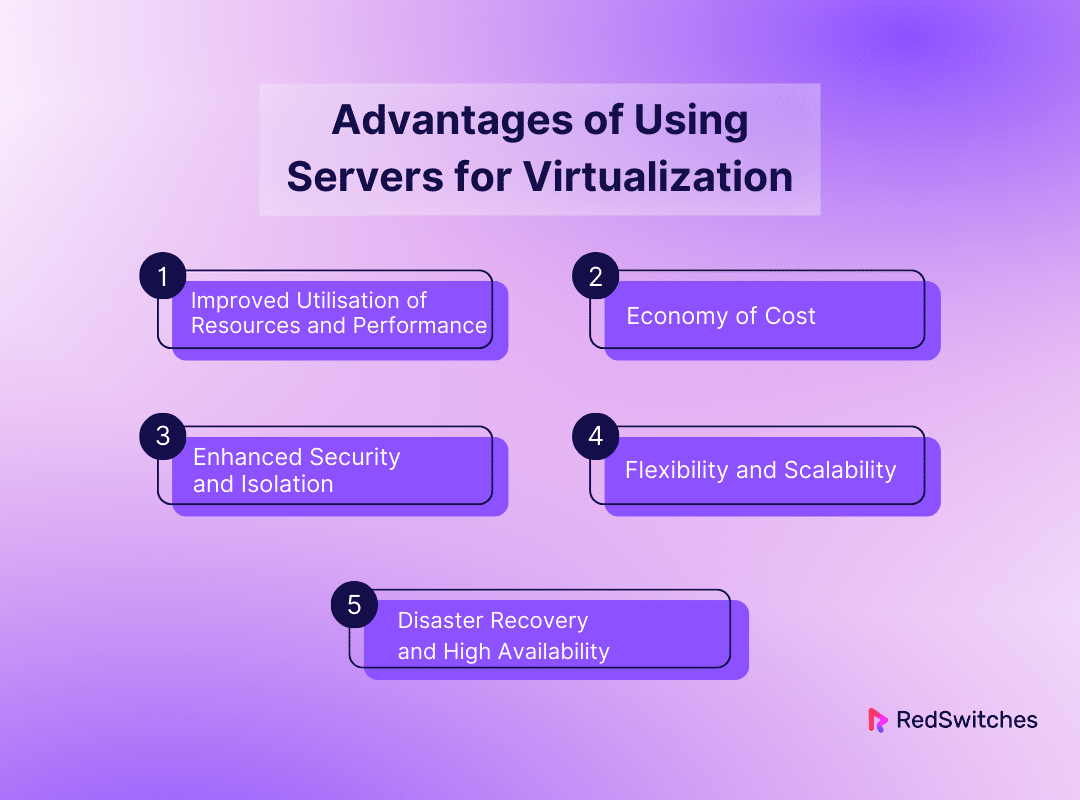
Advantages of Using Servers for Virtualization
Dedicated servers have many benefits for virtualization. They meet the growing needs of IT for efficiency, scalability, and security. These servers allow enterprises to host several virtual machines (VMs) on a single physical server by providing an ideal environment for virtualization technologies. Below, we discuss the main advantages of using servers for virtualization.
Improved Utilization of Resources and Performance
The notable performance and resource use increase is a main benefit of virtualization. It happens with servers. Each virtual machine can use all the underlying hardware. The server’s resources (CPU, RAM, and storage) are not shared with other users, as in shared hosting. Because of this exclusivity, there is no chance of resource contention. Other tenants’ activities can’t cause performance degradation. This ensures that applications on these virtual machines (VMs) operate at their best. Virtualization also enables better resource allocation. Resources can be assigned or changed in response to individual virtual machines (VMs) needs. This allows for better use of the server’s capabilities.
Economy of Cost
Using servers for virtualization is a huge leap. It makes IT operations much more cost-effective. It uses several virtual servers on a single server. This choice lets firms reduce the number of physical servers they need. Combining servers saves a lot on hardware costs. It stops the need to buy and maintain many physical servers. The method dramatically cuts energy usage and cooling needs. These are big costs in running a data center, in addition to the initial hardware savings. Cutting server size also cuts facility costs. This is because space is scarce in many data centers.
The scalability of virtual machines adds another level of cost-effectiveness. Organizations may cut costs by adding resources at peak times and removing them during low usage. This way, they avoid paying for unused capacity by assigning resources based on demand. An important part of cost-effective IT is flexible resource management. It lets companies better match IT spending to their real needs.
Enhanced Security and Isolation
Credits: Freepik
In the current cybersecurity environment, virtualization on servers introduces a strengthened layer of security and isolation. Isolating each virtual machine into its isolated environment significantly reduces the possibility of one hacked virtual machine affecting others. In containment tactics, this isolation is essential so that a breach in one instance does not destroy the entire server ecosystem. Moreover, completely controlling servers allows businesses to customize their security protocols. This feature enables deploying cutting-edge security protocols, bespoke firewall rules, and anti-malware programs tailored to the company’s security requirements.
Flexibility and Scalability
The flexibility and scalability of virtualization on servers are essential when business needs change at a never-before-seen rate. With exceptional speed and ease, this technology enables enterprises to scale resources, deploy new virtual machines, and clone entire environments. This agility makes fast development and deployment cycles possible, which helps companies react quickly to internal or external needs. Startups and expanding businesses that must swiftly expand their IT infrastructure due to erratic workloads will find this feature especially helpful. Because there are no physical hardware limitations, it can scale up or down quickly to meet demand or control expenses without requiring a substantial upfront investment.
Disaster Recovery and High Availability
Virtualization on servers drastically changes an organization’s approach to disaster recovery and high availability. Virtual machines facilitate easy replication and backup, allowing for a strong data protection and recovery plan. These backups or replicas can be swiftly activated on a different server in the case of a server failure or other catastrophic event, minimizing downtime and guaranteeing business continuity. This skill is essential for preventing data loss and running operations during unscheduled disruptions. Furthermore, virtual machines’ mobility—the ability to move them between servers without experiencing any downtime—improves services’ overall availability. Because of its fluid movement capacity, operational continuity is minimized even during unanticipated hardware breakdowns or maintenance.
Also Read, The Advantages of Virtualization in Server Environments.
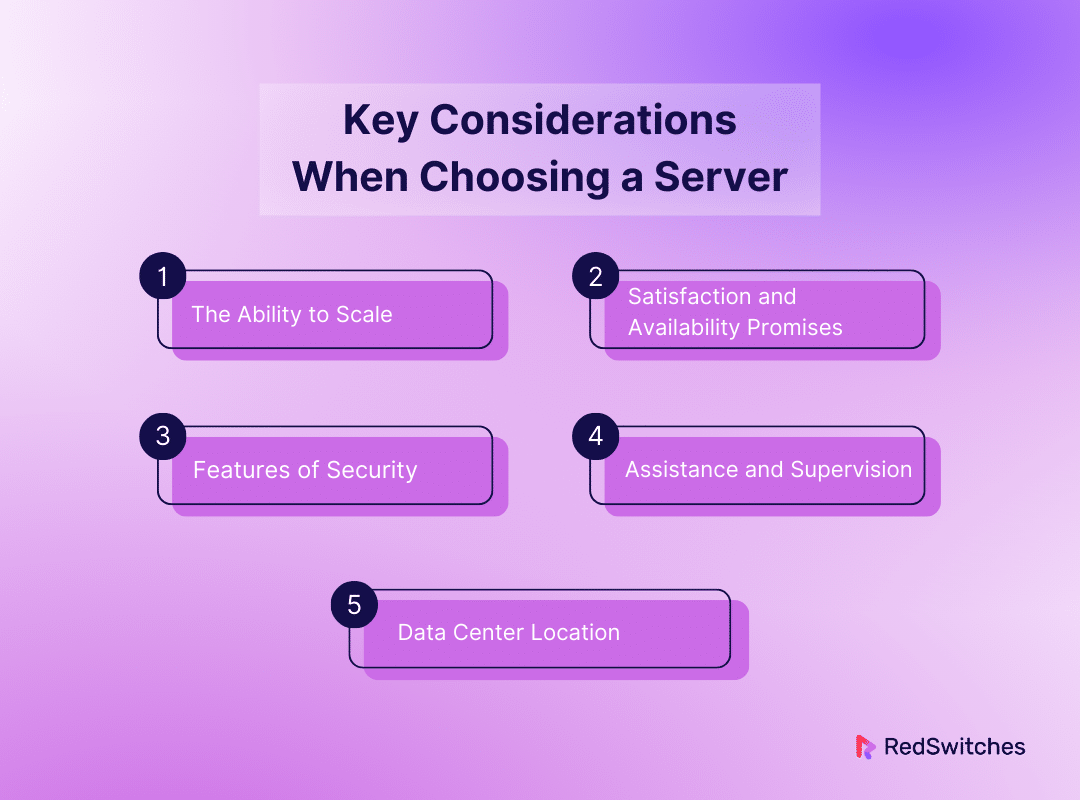
Key Considerations When Choosing a Server for Virtualization
You must consider several key factors when choosing the best server for your virtualization needs. These factors ensure the server meets your current needs. It is also expandable and flexible enough to handle growing demand. The following are important factors to consider while selecting a server:
The Ability to Scale
As demands in today’s dynamic corporate climate might change suddenly, scalability is not only a feature but a must. A scalable server ensures that your infrastructure can quickly adjust. It can handle organizational changes, like long-term growth or sudden traffic surges. Maintaining performance standards and guaranteeing client satisfaction depends heavily on this flexibility. Scalable solutions make sure that your server can change to meet your needs. They do this by letting you add virtual machines or resources as needed. Also, consider if the server is good for hybrid and cloud environments. They may offer more options for scaling and flexibility.
Satisfaction and Availability Promises
The foundation of any online service is reliability. Downtime is often tied to lost income and eroded trust. Looking beyond uptime guarantees is critical when searching for a server provider. You must grasp the procedures and architecture behind these claims. This includes redundancy in power supplies and network connections. It also includes entire redundant data centers. They guarantee continued operation. Their investment in cutting-edge technologies and maintenance procedures shows the provider’s dedication. It shows their dedication to dependability. Furthermore, the provider’s reaction during outages is essential. The speed at which they identify and resolve problems impacts total uptime. As a result, evaluating the provider’s reaction and disaster recovery plans is as crucial as checking their uptime.
Features of Security
Credits: Freepik
The security of a server is crucial. Data breaches are common now. They can have catastrophic consequences. The breadth and depth of the security mechanisms offered must be considered when assessing a server’s security. This means knowing how these safeguards are in a full security plan. It also means examining the tools and procedures in place. For example, what is the frequency and method of the provider’s vulnerability screening? What is their patch management protocol? Adding tools like SSL certificates, dedicated IPs, and secure VPNs can improve your server’s security. You should use these in addition to normal precautions. Also, for companies in regulated industries, following industry laws like GDPR, HIPAA, or PCI DSS is essential. This compliance shows a provider’s dedication to strict security guidelines. It also guarantees that your server follows the law.
Assistance and Supervision
The key to efficient operations may lie in the caliber of management and support services offered and a server. This includes the depth of knowledge available to handle potential problems. They range from hardware malfunctions to sophisticated cybersecurity attacks. It goes beyond just having access to round-the-clock technical help. Proactive management involves monitoring your server. It means foreseeing possible issues and acting before they worsen. It can be quite helpful for the provider. Also, managed services can greatly reduce your IT staff’s workload. This frees them to focus on strategic projects, not routine server maintenance. Consider the available contact channels. Also, consider the average response times and the degree of customization in the service agreements. These factors help when evaluating a provider’s assistance.
Data Center Location
Selecting the ideal data center location for your server is a complex choice that impacts server uptime, latency, and general dependability; therefore, it requires a thorough analysis beyond simple geographic factors. The ideal distance from your main user base directly impacts latency, which improves user experience by guaranteeing quicker load times and more seamless interactions. This is especially important for apps that require real-time responsiveness. Beyond its physical location, a data center’s ability to withstand environmental threats is crucial. To guarantee continuous operation, locations in areas vulnerable to natural catastrophes must exhibit strong disaster recovery plans and infrastructure safeguards. Another important consideration is connectivity to major internet backbones. High-traffic services require reliable and efficient data transmission, ensured by direct connection to these networks.
How Virtualization Works on Dedicated Servers
Credits: Freepik
It’s a game-changing technology. It lets you create many virtualized environments or dedicated resources. You make them from a single physical system. This is virtualization on servers. To build virtual machines (VMs), you must make environments. They can run their operating systems and applications as if they were on separate physical servers. This involves abstracting and splitting the hardware of the physical server. A hypervisor is a software layer. It is essential for controlling virtualized environments. It makes this procedure easier. This is a thorough explanation of how virtualization functions on servers:
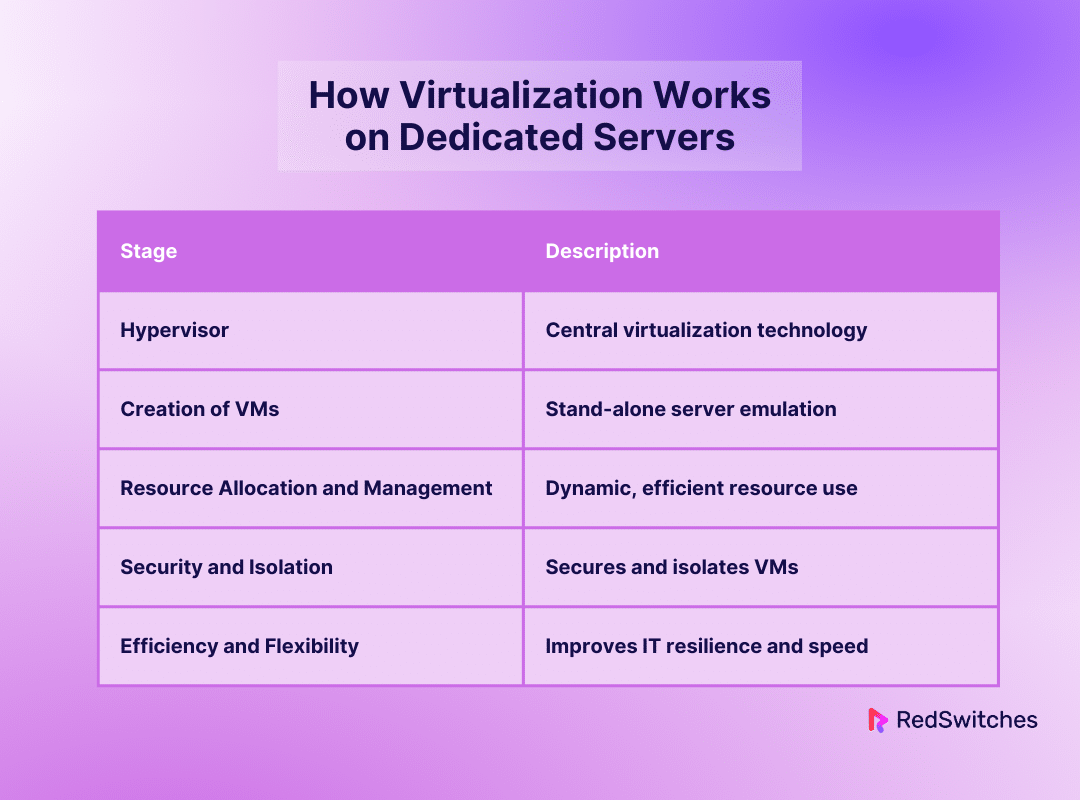
Hypervisor: The Central Element of Virtualization
The hypervisor is the key technology for server virtualization. It is a tactical bridge between the real server resources and the virtual environments it supports. There are two main types of hypervisors: Type 1 (bare-metal) hypervisors provide direct hardware access. They offer better security and performance by removing the need for a host operating system. Type 2 (hosted) hypervisors run on top of a host operating system. They offer more flexibility and user-friendliness for specific applications. The hypervisor can divide and manage a server’s hardware. This lets many virtual machines operate in total isolation on one server.
Creation of Virtual Machines
Using and managing computing resources have changed the paradigm. They did so by introducing virtual machines (VMs) via the hypervisor. Each virtual machine (VM) can work as a stand-alone server. The server’s physical properties are abstracted, and the VMs see virtualized hardware. In addition to the basic parts like CPUs and RAM, this emulation also covers storage controllers, network interfaces, and, in more complex configurations, graphics processing units (GPUs). A single physical platform may support several application environments thanks to this thorough virtualization, which significantly lowers the requirement for physical hardware and permits workload consolidation never before possible.
Resource Allocation and Management
Virtualization’s core value is resource allocation and management. It allows for the efficient use of physical resources. It creates a dynamic environment that can adjust in real time to workload changes. It does more than simple partitioning. The hypervisor’s resource management includes advanced scheduling and balancing. They ensure every virtual machine (VM) has the resources to operate at peak efficiency. They do this without hurting the performance of other virtual machines. This dynamic resource management is crucial. It lets us keep up service levels for many applications. It also allows resource-intensive processes without needing over-provisioning.
Security and Isolation
In a virtualized system, the hypervisor attains security and isolation. It carefully controls how virtual machines (VMs) access and use physical resources. This control ensures that no virtual machine is aware of or impacted by any other VM. So, even inside a single physical server, a safe multi-tenant environment can be created. This isolation is essential for security. It offers a strong barrier against malware and privilege escalation. It also ensures operational integrity. This integrity stops a hacked or broken VM from affecting others. Modern hypervisors also improve the security of virtualized servers. They provide features like secure boot and encrypted virtual machines (VMs).
Efficiency and Flexibility
Virtualization on servers is very efficient and flexible. It revolutionizes IT. It makes infrastructures more resilient, responsive, and cheap. Virtualization speeds up server installation. It takes minutes instead of weeks or days. It also allows quick provisioning of identical duplicates of current systems. This is for testing, development, or disaster recovery. Organizations can dynamically optimize their IT operations with the flexibility to scale resources up or down on demand and relocate virtual machines (VMs) between physical servers for maintenance or load balancing. Moreover, consolidating workloads onto fewer physical servers through virtualization reduces hardware, energy, and space costs, simplifies management, and enhances disaster recovery capabilities, making it a keystone of modern IT strategy.
Let’s summarize it in a tabular format.
Security Considerations in a Virtualized Environment
Security in virtualized environments has different issues. They are distinct from those in physical infrastructures. Virtualization requires reevaluating security measures to protect data, programs, and virtual resources properly. It must adapt due to the extra abstraction and complexity it adds. Here are thorough explanations of the main security factors to take into account in a virtualized environment:
Security of the Hypervisor
The hypervisor is a prime target for assaults since it forms the basis of any virtualized environment. Attackers may be able to take control of all hosted VMs. They’ll gain access to shared resources if they compromise the hypervisor. To secure a hypervisor, apply patches and updates often to fix known flaws. Also, configure the hypervisor minimally to limit attack surfaces. And use hardware-assisted virtualization meant to boost security. It is essential to stop unwanted access. This requires monitoring and controlling hypervisor access using strict authentication and authorization procedures.
VM Isolation
To stop one hacked VM from influencing others or accessing their data, rigorous isolation between VMs must be maintained. This calls for careful management of shared resources like networks and storage. It also requires logical isolation. You can use network segmentation strategies. These include firewall rules and VLANs. They can help enforce isolation policies. Also, setting storage access permissions correctly shields virtual machines (VMs) from unwanted access to other people’s data.
Also read Firewall Rules: Best Practices for Long-Term Security in 2024
Safe Virtual Networking
Credits: Freepik
Virtual networks connect virtual machines (VMs). They have security flaws. These flaws are the same and as complex as those in physical networks. You must use conventional network security techniques in a virtualized environment. These techniques include network segmentation. They include intrusion detection and prevention systems (IDS/IPS) and virtual firewalls. They protect these networks. Protecting the virtualized network needs setting up secure virtual switches and routers. It also needs to encrypt data in transit within the virtual network.
Management and Configuration Hardening
The virtualized environment’s management interfaces and configuration settings are important weak areas. We must enforce strong authentication. Access to these must be restricted to key workers using role-based access controls (RBAC). Also, communication with management interfaces must be encrypted. Risks come from wrong configurations or unauthorized changes. You can reduce them by routinely checking configurations and following the best security practices.
Compliance and Data Protection
Encrypted data should be used in virtualized environments, both while it is in transit and at rest. This prevents unwanted access to sensitive data. Backup and recovery are also crucial. They ensure data is available and intact. Virtualized environments must follow data protection laws and guidelines, which require careful preparation and implementation of compliance plans.
Observation and Reaction to Incidents
Detecting security incidents early requires constantly monitoring virtualized environments for anomalies or breaches. Integrating SIEM systems can help combine and analyze logs from virtualized infrastructure. Thanks to a clear incident response strategy made for virtualized environments, breaches can be quickly fixed.
Conclusion
Dedicated server virtualization is a revolutionary technology that provides businesses with incomparable efficiency, scalability, and flexibility. As we’ve covered in this blog, organizations can maximize resource utilization, improve security, and cut expenses by setting up distinct virtual environments on a single physical server. Server virtualization offers a strategic advantage in today’s fast-paced digital environment by dynamically allocating resources and adapting swiftly to changing demands.
RedSwitches is a top option for businesses wishing to use server virtualization. We offer the ideal platform for virtualization with our reliable dedicated server solutions, guaranteeing that companies can achieve high performance, scalability, and stability customized to match their unique requirements. Choosing us is like taking a step into a future where innovation and growth are effortlessly driven by IT infrastructure.
Learn more about the potential of server virtualization with RedSwitches. For additional information and resources, visit our website or get in touch with us to learn how our solutions can revolutionize your IT environment.
FAQs
Q. How is virtualization used in servers?
Server virtualization improves efficiency and flexibility. It allows a single physical server to run many operating systems and applications.
Q. What is the difference between a VM and a dedicated server?
A dedicated hosting server offers all its resources to a single user or application. In contrast, virtual machines (VMs) share resources with other VMs on the same host.
Q. Is VPS faster than a cloud?
The workload and resources allotted determine how well a virtual private server (VPS) performs. But cloud services can be faster. They can also scale more dynamically. This is due to their distributed resources.
Q. What is server virtualization?
Server virtualization divides a physical server into multiple virtual servers. They can run different operating systems and applications on their own.
Q. How does server virtualization work on servers?
Server virtualization uses virtualization software. It creates many virtual machines on one physical server. This optimizes hardware resources and improves efficiency.
Q. What are the advantages of server virtualization for businesses?
Server virtualization offers advantages. These include increased flexibility, scalability, cost savings, and better resource use. It also improves disaster recovery for businesses.
Q. What is the difference between virtual private servers and dedicated servers?
VPSs share a physical server with other virtual instances. Servers have the whole server dedicated to one customer. They offer greater control and performance.
Q. What is a bare metal server, and how does it relate to server virtualization?
A bare metal server is a physical server without a pre-installed operating system. It is ideal for hosting virtualization software. This software creates virtual machines for various applications and workloads.
Q. Which virtualization solutions are commonly used for server virtualization?
People commonly use popular virtualization software, like VMware, Hyper-V, and KVM. They use it for server virtualization to make virtual environments and save resources.
Q. How does server virtualization enhance performance and security for businesses?
Server virtualization improves performance by allocating resources based on demand. It also improves security. It does this by isolating virtual environments and offering better disaster recovery options.