Key Takeaways
- Dedicated servers provide unparalleled performance and reliability for high-demand applications.
- Enhanced security and privacy features protect sensitive data from cyber threats.
- Customization and control allow for tailored server environments to meet specific needs.
- Dedicated resources ensure smooth operation without the constraints of shared hosting.
- Regular updates and vigilant security measures are crucial for maintaining server integrity.
- Sustainable practices reduce environmental impact and promote energy efficiency.
- Continuous monitoring and maintenance optimize server performance and uptime.
Tired of slow loading times, website crashes, and limited resources? It’s time to ditch shared hosting and level up your online game with a dedicated server. This thorough guide will walk you through the complex world of setting up a server. Many find this task intimidating, but it has massive potential for those who take the time to learn. You’re in the perfect place if you want to run a successful online game, a booming e-commerce site, or the best security and performance for your web apps.
Use our clear instructions. They contain professional advice and best practices on setting up dedicated server. With them, you can use your dedicated server to raise the bar for what is possible on the Web. Together, let’s go on this journey to unlock a world of seemingly endless possibilities.
Table Of Contents
- Key Takeaways
- What are Dedicated Servers?
- How do Servers Work?
- When to Choose a Dedicated Server?
- Initial Setup Steps of Server
- Installing the Operating System
- Security and Maintenance of Dedicated Servers
- Troubleshooting Common Issues
- How to Enhance Your Dedicated Server?
- Environmental Considerations And Energy Efficiency
- Conclusion
- FAQs
What are Dedicated Servers?
Credits: Freepik
Dedicated servers give users unmatched power and resources. In contrast to shared hosting or virtual private servers (VPS), a server is used only by one customer. This shows that no hardware resources, like the CPU, RAM, and storage, are shared. Dedicated hosted Servers are only used to support the client’s website, application, or platform. Dedicated hosted Servers are unique. They are exclusive and provide enterprises and demanding applications with top performance and security.
One of its main features is the possibility to personalise servers. Clients can often customize a server’s exact hardware. This includes the type and speed of the processor, the amount of RAM, and the type and capacity of storage. This flexibility allows for a custom setup. It may fit a business’s or project’s needs. These needs may be hosting an extensive database, a high-traffic website, or a resource-intensive program. Also, clients can build servers with any OS and software they like. This gives them complete control over the environment for their apps.
Another essential benefit of servers is security. The Dedicated hosted server cannot share space with a malicious website or program because it is dedicated to a single user. Users have complete control over the security mechanisms. They include software updates and patches, firewall settings, and intrusion detection systems. Dedicated hosted Servers are the best option for managing sensitive transactions and personal data. They are also suitable for any other operation needing a high level of security. This is because they offer a high level of control.
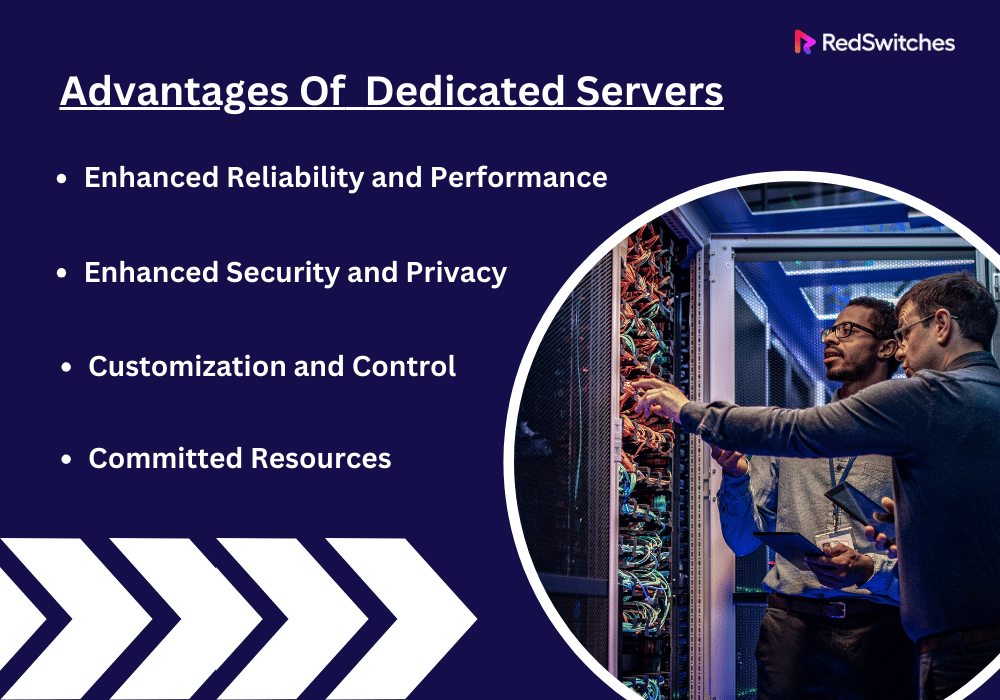
Advantages Of Dedicated Server
Dedicated hosted Servers are a reliable platform for hosting websites, apps, and databases. They have many benefits for companies and individuals with high-performance needs. Here is a thorough analysis of their advantages:
Enhanced Reliability and Performance
Servers are famous for their excellent reliability and performance. They set a high standard for hosting options. Thanks to the allocation of dedicated resources. The dedicated hosted server can easily handle high traffic and complex tasks. It does so without losing performance or availability. The “noisy neighbor” effect happens in shared hosting. It is eliminated in this dedicated environment. In it, one user’s activity affects the performance of other users on the same server. Dedicated Private servers offer many benefits. Firms that rely on their online presence use them. These businesses include high-traffic news portals. They also include social networks and substantial eCommerce sites.
Enhanced Security and Privacy
Dedicated hosted Servers offer unmatched security and privacy. They act as a haven in the turbulent seas of cyber threats. Cross-contamination is a possibility. It can happen in shared environments where one hacked website could harm others hosted on the same server. The risk is eliminated when a server is devoted to a single client. Customized security measures are used to strengthen the server. They include advanced firewalls, intrusion detection systems, and frequent security audits. They protect it from external and internal threats. The server has exclusive access, so this is possible. Businesses handle proprietary data. They hold private client information and do sensitive transactions. They must have this customized security.
Customization and Control
Servers give clients unmatched customization and control. They can tailor their hosting to meet their needs. This level of customization goes beyond just installing software. It also includes server setups, speed boosts, and security upgrades. The flexibility to choose the best operating system is essential. It ensures the server fits the business’s needs. This could mean going with a stable Linux distribution or a version of Windows Server for specific applications. This control also applies to the server’s hardware, enabling updates or changes to accommodate business needs. The ability to customize servers is beneficial for companies that use specialized software or bespoke applications that call for a particular set of resources.
Committed Resources
Dedicated hosted servers have a crucial feature. It is the provision of dedicated resources. This guarantees that customers can access the server’s processing and storage capacity. This exclusivity ensures that the server won’t experience the bottlenecks frequently present in shared environments when processing big datasets, supporting high-resolution media streaming, or hosting complicated web applications. Demanding computational activities can be completed effectively for sectors dependent on data-intensive processes, such as financial analysis firms, video production companies, and scientific research organizations, thanks to the availability of dedicated resources. Businesses can customize the server to meet their unique workload requirements by selecting various hardware configurations, including fast SSDs or high-capacity HDDs, high-performance CPUs, and plenty of RAM.
How do Servers Work?
Let’s understand the working procedure of servers.
A dedicated hosted server requires many essential parts and procedures. These range from setup to upkeep. Understanding a server’s function is vital for enterprises and people. They seek to use this powerful hosting option well.
First Setup and Configuration
The first step in the journey of a dedicated hosted server is choosing and setting it up. Clients choose servers based on their needs, including CPU speed, RAM size, storage, and network bandwidth. After choosing the dedicated hosted server, the hosting company or data center staff sets it up. They install the needed hardware components to match the client’s requirements.
The following steps are for installing the operating system (OS) and setting up the server software. Clients can select from various operating systems based on their needs. These include Windows Server and Linux distributions. Examples of Linux distributions are Ubuntu, CentOS, and Debian. There are also other specialized OS solutions. The OS selection determines the program environment. It also affects the administrative tools and security configurations available for the server.
Network Accessibility And Connectivity
After configuring, the server is linked to the data center’s network infrastructure. Thanks to this connection’s high-speed internet, the server can provide content to users and offer services over the Internet. The server is given a static IP address to identify it on the network and enable remote access.
Typically, clients use tools like Remote Desktop Protocol (RDP) for Windows servers. They use Secure Shell (SSH) for Linux servers. These tools let them remotely control their servers. With the help of these tools, administrators may access the server from any location with an internet connection, apply updates, adjust configurations, and diagnose problems.
Continuous Upkeep And Improvements
A dedicated hosted server must be regularly updated and monitored to guarantee peak performance and security. This entails updating the operating system and loaded applications with security patches, monitoring performance indicators and system health, and adjusting the system as necessary to accommodate variations in load or functionality.
Clients may also choose to upgrade the hardware components of their servers over time to meet increasing needs. Enhancements may include increasing RAM and storage space or swapping out the CPU for a more potent one. Since the hosting provider will modify the data center’s hardware, collaboration is usually necessary for these physical updates.
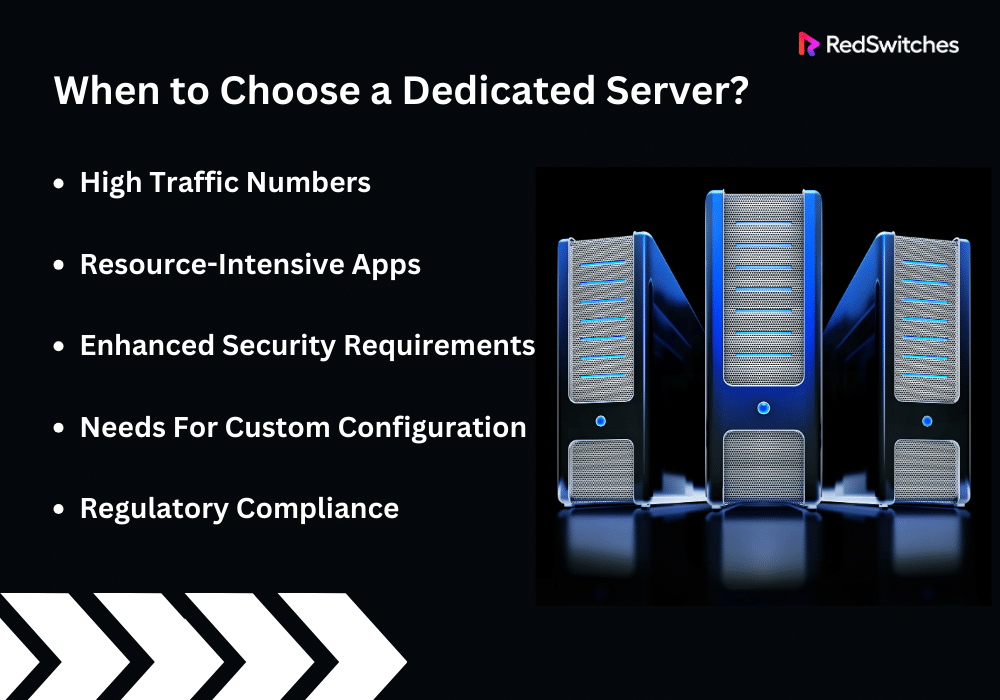
When to Choose a Dedicated Server?
Selecting a server is a strategic choice that depends on several critical variables that represent the demands of your project, its growth trajectory, and its particular security, control, and performance requirements. Despite providing unmatched resources and exclusivity, servers are more expensive than shared hosting or virtual private servers (VPS). Here’s a thorough explanation of when choosing a server is the best course of action:
High Traffic Numbers
A server can offer the capacity to manage the load when your website or online application encounters high traffic numbers or anticipates scaling up quickly. Servers have the bandwidth and processing capacity to operate normally, even under high loads, providing a dependable and constant user experience. This contrasts with shared hosting, where unexpected traffic surges may cause slower response times or outages.
Resource-Intensive Apps
Some apps demand much memory, processing power, or storage space for optimal operation. Examples include complex databases, expansive e-commerce sites, enterprise-level CRM programs, and real-time data processing apps. Shared resource constraints won’t limit your applications when you use a server because the hardware can be customized to suit these high resource demands.
Enhanced Security Requirements
Security becomes a top priority for projects managing sensitive data, such as financial transactions, health records, or personal information. Because you aren’t sharing resources with other users, servers provide a secure environment and remove the possibility of security flaws on nearby websites that could compromise your data. Furthermore, having complete control over the server environment makes it possible to install security measures specifically suited to your security rules, such as firewalls, encryption, and access controls.
Needs For Custom Configuration
Specific projects might have certain specifications that call for installing specific software, setting up specific servers, or using operating systems incompatible with shared or VPS hosting. With servers, you can easily customize the hardware and software environment to your specifications, guaranteeing your applications’ compatibility and best possible performance. This degree of control is especially crucial for companies that use specialized software that needs a specific configuration or software designed from scratch.
Regulatory Compliance
Businesses operating in sectors subject to legislation like the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA) may need to adhere to stringent privacy and data handling guidelines. Configuring servers to provide the data isolation, security mechanisms, and audit trails required to guarantee compliance can meet these regulatory requirements.
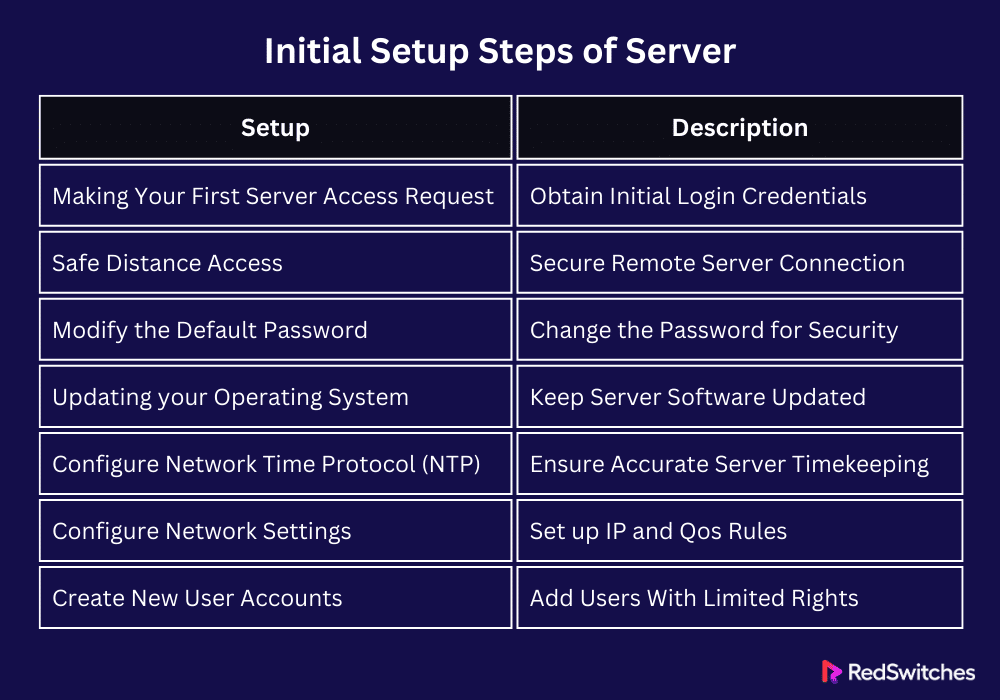
Initial Setup Steps of Server
Setting up a server is a crucial first step in building a solid web presence for your project or company. The initial setup has many crucial steps. You need to get access to the server, do a basic setup, and put in necessary security measures. Here’s a closer look at these preliminary actions:
Making Your First Server Access Request
Get Credentials from the Source You Choose: Once your server is provisioned, your hosting company will send you an email or secure message with the initial login credentials. This data usually includes the server’s IP address, a temporary password, and the default username (such as “root” for Linux or “Administrator” for Windows). Protecting this information and completing the initial login process as soon as possible is critical.
Safe Distance Access
Linux/macOS: Use an SSH client to create a secure connection. For first-time connections, you may receive an error message stating that the host’s authenticity has not been verified. Before accepting, compare the message’s fingerprint to your server’s expected fingerprint. Your host often supplies it. You must take this action to stop man-in-the-middle attacks.
Windows: RDP offers a graphical user interface for establishing a server connection. When using RDP for the first time, ensure your link is secure. Confirm the ID of the distant computer. Your RDP session can be secured using a VPN, particularly if connected over a public network.
Modify the Default Password: As soon as possible, replace the default password with a secure, one-of-a-kind one. Use a password manager to create and save this password for increased security. Ensure your new password has capital and lowercase letters, numbers, and symbols. It should follow recommended practices.
Basic Configuration
Updating your Operating System: Maintaining the server is essential to preserving its performance and security. For Linux systems, a cron job can automate these updates and keep the system up to date without human intervention. Windows users can set up Active Hours in Windows Update to avoid unplanned reboots during crucial times.
Configure Network Time Protocol (NTP): Timekeeping accuracy is essential for server functions, including scheduled tasks and security logs. Choose several NTP servers to provide redundancy. You can add more NTP servers on Linux by editing the /etc/ntp.conf file.
Configure Network Settings: If your server will handle various traffic types, you should consider implementing Quality of Service (QoS) rules in addition to the primary IP configuration. This will prioritize critical services and prevent lower-priority traffic (such as VoIP or streaming) from interfering with high-priority traffic.
Create New User Accounts: For more precise control over the commands that can be executed, set the sudoers file when you create a new user with administrative access. This procedure reduces the possibility of inadvertent or deliberate abuse of administrative rights.
Installing the Operating System
Credits: Freepik
A fundamental step that establishes the foundation for a server’s functioning and performance is installing the operating system (OS). To assure optimal operation, this process entails carefully choosing the most appropriate operating system (OS), installing it according to structured guidance, and setting up the system initially. A thorough explanation of each of these processes can be found here:
Selecting an Operating System
Evaluate Your Needs: The operating system you choose will depend on your project’s particular requirements, which include the programs you want to use, performance issues, security needs, and your team’s experience. Common choices include Windows Server versions and Linux distributions (such as Ubuntu, CentOS, and Debian).
Think About Compatibility: Make sure the operating system you’ve selected is compatible with both the software programs you want to use and your hardware. Specific programs, particularly proprietary ones, might only function with a limited number of operating systems or system libraries.
Examine Community and help: The availability of community resources, forums, and expert help might be critical when troubleshooting or optimizing server performance.
Costs associated with licensing: A license must be purchased for Windows Server, but many Linux variants are free. Examine the financial effects of your OS selection, considering both one-time and recurring costs.
Step By Step Guide
Let’s dive into the step-by-step guide for setting up your dedicated private server.
Regarding Linux Server
We’ll explore these step-by-step dedicated private server setup guides in the context of Linux (using Ubuntu as an example).
Visit the official website to download the most recent Ubuntu Server ISO version.
Make Bootable Media: If installing physically, use an application such as Rufus to generate a bootable USB drive. Your hosting provider might supply IPMI (Intelligent Platform Management Interface) tools or a web interface to mount the ISO for remote installations.
Boot from ISO: After restarting the server, select whether to boot from the mounted ISO or the USB device.
Observe the installation prompts. Ubiquity installer Ubuntu will guide you through picking a timezone, partitioning drives, configuring network interfaces, and selecting your language.
Regarding Windows Server
Now, We’ll explore these step-by-step dedicated server setup guides in the context of window server.
Obtain Installation Media: Download the Windows Server ISO file from the Microsoft website or your supplier’s portal.
Make Media That Is Bootable or Mount ISO Remotely: You can mount the ISO using your server’s remote administration interface or tools like the Windows USB/DVD Download Tool for physical installations.
Installation Setup: Launch the installation by booting from your media. Choose the Windows Server version you want to install, then agree to the license conditions.
Select the Installation Type: To start from scratch, select the ‘Custom: Install Windows only (advanced)’ option.
Divide Your Hard Drive: If necessary, divide the hard drives on your server. A single partition is adequate in most situations.
Network Configuration
Setting up a server requires proper network configuration. This is key to ensuring that your server can be securely accessed. It is also essential for keeping network services running smoothly. This includes setting up DNS and IP addresses. It also involves creating firewall rules for security. Let’s examine each of these elements in greater detail:
Configuring IP addresses
Assign Static IP Addresses: Static IP addresses are usually necessary for reliable network connectivity on servers. Typically, your hosting provider assigns your server one or more static IP numbers. The network interface on your server has to be configured with this IP address, the subnet mask, the gateway, and any additional IPs you may have.
Linux: To add your static IP address, netmask, and gateway, edit the network configuration file (/etc/network/interfaces on Debian/Ubuntu or /etc/sysconfig/network-scripts/ifcfg-eth0 on CentOS/RHEL).
Windows Server: In Windows Server, enter your IP address, subnet mask, and default gateway by going to “Network and Sharing Center” > “Change adapter settings,” right-clicking your network connection, selecting “Properties,” and then “Internet Protocol Version 4 (TCP/IPv4).”
Setting up DNS
Domain Name System (DNS): DNS converts Human-readable domain names to IP addresses. Configuring DNS settings includes two tasks. You must set up DNS records for your domains and show which DNS servers your server should use to find domain names.
DNS Resolvers: You can specify the DNS resolvers by adding the IP addresses of your DNS servers—typically supplied by your hosting provider or a third-party DNS service—to the relevant configuration file (such as /etc/resolv.conf on Linux or via the network connection properties on Windows).
DNS Records: You must set up DNS records (A, AAAA for IPv6, MX for mail servers, etc.) with your domain registrar or DNS hosting provider for your domain to point to your server. Whereas an MX record captures direct email traffic, an A record should lead your domain to the IP address of your server.
Security and Firewall Configuration
Putting a Firewall in Place: A firewall uses security rules to regulate incoming and outgoing network traffic. It is necessary to safeguard your server from possible assaults and unauthorized access.
Linux: To configure firewall rules, use ufw (Ubuntu/Debian) or firewalld (CentOS/RHEL). For example, you can enable web servers to communicate on ports 80 and 443 while blocking all other unneeded ports.
Windows Server: Configure the Windows Firewall with Advanced Security to establish inbound and outbound rules. You can create rules based on IP addresses, port numbers, and apps to control access.
Security and Maintenance of Dedicated Servers
Credits: Freepik
Security and maintenance are key to managing servers. They keep a server dependable, secure, and efficient. These procedures combine advanced security protections, monitoring, backup plans, and frequent upgrades. Let’s explore each of these categories in detail:
Frequent Updates and Patches
Keeping the latest OS versions and installing apps on your server is vital. It is key to its performance and security. Hackers exploit most vulnerabilities in out-of-date software. Patches for known bugs are there, but they haven’t been installed. It is advisable to set up automatic updates whenever possible. For instance, Linux distributions often provide packages. These may be set up to install security updates automatically. For example, CentOS/RHEL has yum-cron, and Debian has unattended-upgrades. You need regular manual inspections for software not covered by these automatic processes. You also need them for big updates that may need a manual restart or specific changes.
Administrators should check servers for updates often. They should do this by hand. They should pay close attention to any vital running software and services. Furthermore, patch management technologies make the process easier. They help when handling many servers and ensure that all systems stay shielded from vulnerabilities.
Backup Plans
A strong backup policy must be implemented to protect your server against data loss due to various dangers, including hardware failure, software defects, human error, and cyberattacks. Following the 3-2-1 backup rule, which states that you should have at least three copies of your data overall—two on separate platforms or media and one off-site—can serve as a solid basis for data recovery plans. The frequent and constant execution of backups is ensured by automating the process with tools designed specifically for the needs of the server, such as database-specific utilities like mysqldump for MySQL or rsync for file backups. Cloud-based backup services can also provide secure off-site storage options that are scalable.
Keeping an Eye On Your Server
Maintaining a server’s security and well-being requires regular monitoring. It lets us find problems early on, like system malfunctions, performance snags, and suspicious activity. This makes it easier to address possible concerns quickly. We will put in place monitoring systems. They will include performance metrics like CPU usage, memory consumption, disc activity, and network bandwidth. They can find and fix problems before they affect server performance or availability. Security monitoring is essential for identifying unusual activity pointing to a security breach. This is done by intrusion detection systems (IDS). It is also done by security information and event management (SIEM) solutions.
Furthermore, keeping and examining thorough logs of system and application activity can offer insightful information on the server’s security posture and functionality. Proactive security strategies require effective log management procedures backed by technologies that examine and notify users of significant or questionable log entries.
Advanced Security Practices
Adding advanced security practices goes beyond basic ones. It can greatly improve your server’s defense against sophisticated attacks. A well-designed firewall is one of the best defenses against unwanted access. It blocks harmful traffic based on pre-established security rules. Use data encryption to protect sensitive data sent to and from the server. Use SSL/TLS certificates while the data is in transit. By adding a second layer of security to server access, two-factor authentication (2FA) reduces the risk of password breaches. It will require regular security audits. You must use vulnerability scanning. The audits find and fix any potential security flaws in the installed software or server setup.
Access Control And Data Encryption
Ensuring the encrypted data on your server adds a vital degree of protection, shielding private data even in the case of illegal access. Encrypting the entire disc can protect data while at rest, rendering it illegible without the right encryption keys. Additional encryption at the file or database level guarantees that even if hackers circumvent other security measures, the encrypted data stays safe for databases and particular files that hold sensitive information, such as intellectual property or personal information. Implementing stringent access control procedures is crucial in addition to encryption. For each user or program, this entails limiting permissions and privileges to the absolute minimum required for their operation on files, directories, and services.
Troubleshooting Common Issues
Credits: Freepik
Let’s understand the troubleshooting common issues.
Boot Issues
To fix boot issues on a server, take a methodical approach. Find and fix the underlying problems that keep the server from starting. Hardware malfunctions are a common cause of boot problems. So are corrupted boot loaders, bad boot configurations, and damaged file systems. When a server doesn’t boot, the first step is to check its hardware. This includes the hard discs, memory, and power supply. Examining the bootloader is the next step after hardware problems have been ruled out. This is crucial for Linux servers. A bad GRUB can prevent them from booting.
One way to learn about the boot order is to find differences causing the boot failure. You can do this by accessing the BIOS or UEFI settings on the server. Fixing corrupt files or settings on servers that start to boot but stop midway may require entering recovery mode or using a rescue disc. These changes often cause boot problems. So, track recent ones. They may provide insight.
Network Problems
Slow connection speeds, sporadic connectivity, or total loss of network access are examples of network problems. They can affect servers and hinder their ability to communicate with the outside world. Basic tests come first. They involve making sure that network cables are securely connected. Also, the server’s network interface cards (NICs) are working; another crucial step is to check the server’s network configuration files for erroneous IP addresses, subnet masks, gateways, and DNS servers. Misconfigurations in these areas can result in connectivity problems. Firewall rules or security policies may accidentally block legal traffic in software. So, we need to review firewall configurations to find and fix any wrong rules.
The breakdown’s location is the issue. It may be in the local network or farther along the route. You can find the location using network diagnostic tools like ping, traceroute, or netstat. Complex networks can also have problems from outside sources, such as ISP troubles or upstream router malfunctions, which call for coordination with network providers or other outside parties to fix.
Performance Optimization
On servers, performance optimization is finding and removing bottlenecks that impair the responsiveness and efficiency of the server. Monitoring and evaluating server performance indicators to spot problem areas, including high CPU utilization, excessive memory usage, or disc I/O bottlenecks, is the first step in the optimization process. Ensuring the server’s hardware can handle the stress, increasing RAM and CPU, or switching to faster storage options like SSDs will boost performance. Performance can be greatly impacted by optimizing the settings of important software components, including web servers, database servers, and application runtime environments. This could entail modifying caching settings, thread counts, or connection limitations to better fit the workload and resources of the server.
Security Vulnerabilities and Patch Management
Upholding a server’s integrity and security depends on addressing security vulnerabilities and implementing a strong patch management procedure. If security flaws are not fixed, servers may become vulnerable to cyberattacks, illegal access, and data breaches. Regular vulnerability scanning with tools to find known security issues in the operating system and system applications is the first step in mitigating these vulnerabilities. These programs provide reports on potential exposures and compare installed software versions to databases of known vulnerabilities.
After vulnerabilities are found, they must be prioritized according to the danger they represent to the server and the applications it hosts.
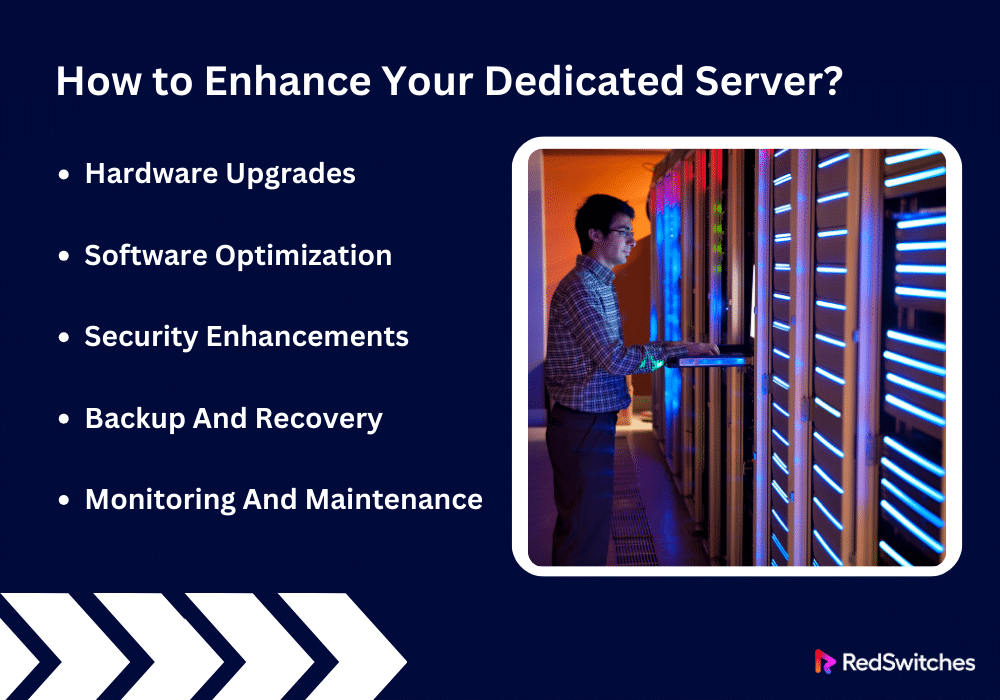
How to Enhance Your Dedicated Server?
Improving a server involves many tactics. These include software and hardware improvements, and security upgrades. To elaborate on your points:
Hardware Upgrades
You can greatly improve your server’s performance and efficiency. Just invest in hardware upgrades. Adding more RAM to the server makes it better at managing databases, virtual machines, and heavy-load applications. This ensures steady performance even when there is high demand. The responsiveness of hosted apps can be greatly increased by upgrading the CPU to a newer, faster model with more cores and threads. This will also make the server faster. It will help it complete many things at once. Swap out your old HDDs for SSDs. Or, add more SSD storage to increase the performance of data-heavy apps and get faster boot times and data retrieval. Network congestion can be greatly decreased by improving the server’s networking parts. This can be done by switching to higher-capacity network interfaces. Or by adding modern networking technologies like 10GbE or fiber optics.
Software Optimization
To keep an operating environment secure and stable, software optimization is essential. Regularly updating the operating system improves performance. It also reduces security flaws and ensures compatibility with the newest applications. Optimizing resource use and response times is key. You can greatly improve this by tweaking your web server settings. Do this based on traffic patterns. These adjustments can include worker processes, memory use limitations, and connection timeouts. Adding indexes and optimizing queries helps. Routine maintenance, like defragmentation, also helps. It can cut latency and improve database operations. Advanced caching techniques can greatly speed up dynamic websites and apps. They include object, page, and opcode caching. These techniques lower load times and improve server response times. This provides a better user experience.
Security Enhancements
A server’s security must be strengthened to defend against cyberattacks and unwanted access. Tailoring firewall policies to fit operational needs greatly improves security. It also blocks undesired traffic. You can achieve a strong defense against many attacks using layered security. It includes intrusion detection systems, web application firewalls, and routine vulnerability scanning. Automated methods manage and upgrade apps. They reduce vulnerabilities and add security fixes on time. We ensure data integrity and confidentiality. We do this by using strong encryption. We use protocols like TLS for web traffic, SSH keys for server access, and VPNs for remote connections. This protects sensitive information from interception and unauthorized access.
Backup And Recovery
A thorough backup and recovery plan must be implemented to ensure data integrity and company continuity. Automating backups must cover databases, servers, and data, ensuring many recovery options for data loss. Regular, scheduled disaster recovery drills are crucial to finding weaknesses in the backup plan and ensuring that recovery operations are efficient and fulfill organizational recovery time targets. By being proactive, we can reduce downtime and ensure that vital systems may be promptly returned to operational status during a crisis.
Monitoring And Maintenance
Ongoing monitoring and maintenance are essential to guarantee server health and peak performance. Advanced monitoring solutions offer real-time insights into the performance of applications, hardware, and user experience, making proactive optimizations to preserve service quality possible. Log rotation, cache cleaning, and performance benchmarking are regular maintenance operations that can be automated to keep the server operating smoothly and effectively. Frequent maintenance lowers the risk of system breakdowns and performance bottlenecks by maintaining a clean, orderly, and performance-optimized server environment.
Environmental Considerations And Energy Efficiency
Credits: Freepik
The environmental impact of data centers and servers has grown in importance in the digital age. We need strategies to reduce the servers’ environmental impact. They are needed because their energy use greatly adds to carbon emissions. Choosing energy-efficient hardware is needed. So is fine-tuning software settings and following sustainable operation best practices.
Techniques For Minimizing Environmental Impact
Choosing energy-efficient hardware is the first step. It minimizes the environmental impact of servers. Many manufacturers are focusing on developing components. The goal is to provide great performance while using little electricity. For example, choosing servers with CPUs built for low power use can greatly cut energy consumption. And they do not sacrifice computing capacity. Also, think about the energy efficiency of storage options. For example, SSDs are more efficient than HDDs. They minimize power use because they quickly access data and make less heat.
Integrating renewable energy sources into data center operations can also reduce environmental effects. These days, many hosting companies use solar or wind energy to produce all or most of the energy their data centers need. Thus, picking a hosting company that uses renewable energy can greatly help. It will enhance the sustainability of server operations.
Hardware and Software Options That Save Energy
Software optimization is just as important in improving energy efficiency as hardware selection. Applications and operating systems can be set up to use as little processing power and resources as possible. One way to save energy is to use power management settings that let servers go into low-power modes when not in use. Virtualization technologies allow the combining of several virtual servers into one physical one. This maximizes resource use and lowers the need for more physical servers.
Increasing software programs’ efficiency can also help reduce energy usage. This means optimizing code to use less computation and using effective algorithms to solve issues with little CPU or memory use.
Best Practices for Sustainable Server Operation
Using sustainable server operation best practices entails routine resource utilization optimization and monitoring. Server monitoring can help adjust unused resources, improving efficiency. For example, unused servers can be repurposed or decommissioned to reduce unnecessary energy use.
Another method is to improve the energy efficiency of data centers. This can be done through layout and cooling system improvements. Modern cooling techniques, like liquid cooling or hot aisle/cold aisle layouts, can greatly cut the energy needed for cooling. Cooling uses much of the energy in data centers.
Promoting sustainability in businesses and hosts can also speed up adopting eco-friendly activities and technologies. This means choosing hardware with fewer bad environmental effects, recycling old hardware ethically, and considering the whole life of server parts, from making to throwing away.
Conclusion
This long tutorial covered every part of setting up a dedicated server. It covered picking the hardware and software. It also covered configuring the complex network and security measures. We’ve examined how businesses with particular hosting needs can benefit greatly from servers. They provide unmatched performance, security, and customization choices. We also discussed the importance of energy efficiency and the environment in today’s servers. We stressed the need for sustainable practices in the digital world.
Apply these insights to RedSwitches. It’s clear that choosing them for your server needs means working with a business. They have vast server management knowledge. In addition to providing the strength and adaptability associated with servers, we are a forward-thinking company that integrates environmental responsibility and energy efficiency into its hosting solutions. Businesses can benefit from servers and contribute to a sustainable digital future by using RedSwitches.
FAQs
Q. What is server configuration?
A server configuration allows complete control and customization. It configures a server with all of its resources assigned to a single person or group.
Q. Can I make my PC a server?
Indeed, you can install server software on your PC and configure it appropriately for the services you want to host to turn it into a server.
Q. Why use a server?
Because servers can handle large volumes of traffic and offer dependable, high-performance hosting, they maximize website or application uptime and security.
Q. What is a dedicated server setup?
A Server setup involves configuring a server to exclusively host specific services or applications, such as a website, game server, or database server.
Q. How do I set up a dedicated server for ARK: Survival Evolved?
To set up a server for ARK: Survival Evolved, you will need to download the server files, configure the server settings, and launch the server using the appropriate command line parameters.
Q. What are the steps to install a server on a Linux system?
To install a server on a Linux system, you need to download the server files, set up the required configurations, and run the server setup process using terminal commands.
Q. Can I use a web server to host my website?
Yes, you can use a server to host your website. You need to install a web server software like Apache or Nginx on your server to serve web pages.
Q. How do I configure an FTP server on my server?
To configure an FTP server on your server, you need to install an FTP server software like vsftpd or FileZilla Server and set up the necessary permissions and user accounts.
Q. What should I do if my server crashes frequently?
If your server crashes frequently, you should check the server logs for errors, update your server software, ensure sufficient hardware resources, and troubleshoot any conflicting configurations.
Q. How do I ensure that my server runs smoothly when the system boots?
To ensure that your server runs automatically when the system boots, you can configure it as a startup service or set up a cron job to launch the server on system startup.
Q. Can I configure my dedicated server to run multiple game servers simultaneously?
Yes, you can configure your server to run multiple game servers simultaneously by setting up separate instances of the game server software for each game you want to host.
Q. How can I install a new server installation for hosting my game server?
To install a new server for hosting your game server, you need to download the server files for the specific game, configure the server settings, and launch the server using the appropriate commands.