Key Takeaways
- Dedicated servers enhance staking efficiency with improved security, performance, and control.
- Physical and digital security measures on dedicated hosted servers protect against potential threats and attacks.
- Optimizing server hardware and configurations can significantly boost staking rewards.
- Scalability and customization of dedicated hosted servers support growing staking demands.
- Reduced latency from strategic server placement enhances the chances of validating blocks.
- RedSwitches offers robust dedicated hosted server solutions ideal for optimizing and securing staking operations.
Welcome to staking, the state-of-the-art in Bitcoin investing! As digital currencies keep changing how we do business, astute investors always look for new methods to increase their profits. One frequently disregarded method is using dedicated servers to increase crypto staking rewards. This post details how staking may be turned from a passive source of income to a reliable source of income with dedicated hosted servers.
We will cover everything from the fundamentals of configuring your own server to sophisticated optimization strategies that can significantly boost your profits. We will also learn crypto staking rewards using dedicated hosted servers.
Prepare to unleash the power of specialized hardware to maximize the return on your investments, regardless of experience level in cryptocurrency. Now, let’s get going!
Table of Contents
- Key Takeaways
- What is Staking?
- What are Dedicated Servers?
- Benefits of Using Dedicated Servers For Staking
- How Dedicated Server Enhances Staking Efficiency
- Crypto Staking Rewards: Optimal Performance Stability
- Crypto Staking Rewards: Strengthened Security for Staked Assets
- Crypto Staking Rewards: Enhanced Reliability and Uptime
- Crypto Staking Rewards: Updates to the Configuration More Quickly and Easily
- Crypto Staking Rewards: Customization to Maximize Rewards
- Crypto Staking Rewards: Geographical Advantages
- Setting up a Dedicated Server For Staking
- Security Measures To Protect Your Staking Assets
- Optimization Strategies For Maximizing Crypto Staking Rewards via Dedicated Servers
- Risks Involved with Crypto Staking Rewards and How Dedicated Servers Can Mitigate it
- Future Trends in Staking and Server Technology
- Conclusion
- FAQs
What is Staking?
Credits: Freepik
In the world of cryptocurrencies, staking is critical. This is especially true in blockchain networks that use Proof of Stake (PoS) as a consensus method. This approach differs greatly from the older Proof of Work (PoW) mechanism that powers networks like Bitcoin. Staking keeps a blockchain network secure and working. It involves holding and locking up a specific amount of cryptocurrency.
Staking is a PoS mechanism whereby users lock their tokens as a security deposit to validate transactions and build new blocks. These users are called validators. They are chosen to suggest and vote on new blocks based on the amount of cryptocurrency they have staked. Sometimes, their selection is also based on how long they have held the currency.
Staking is a tempting option for cryptocurrency owners to profit from their holdings. They get staking rewards. They get them to help maintain the network by staking their currencies. These incentives resemble interest from a conventional bank savings account. The blockchain’s economic model determines the benefits. They usually come from new tokens or transaction fees.
Furthermore, staking helps the blockchain network become more decentralized. It allows a broader variety of users to participate in network governance, strengthening its defenses against potential intrusions or malfunctions. Staking is growing in popularity. It substitutes for those who want to support network security and earn a passive income. This is while cryptocurrencies and blockchain technology continue to advance.
What are Dedicated Servers?
Credits: Freepik
Dedicated servers are robust computer systems. They are set aside for a single client, company, or application. A dedicated hosted server caters to the needs of a single user. This is different from shared hosting. In shared hosting, resources like CPU, memory, and storage are shared among many users. Due to their exclusivity, dedicated hosted servers are the go-to option for demanding applications and enterprises because they provide better security, increased control, and superior performance.
One of the main benefits of employing a server is its strong performance. The actions of other users bring on no performance variations because the entire server’s resources are dedicated to only one user. This steady performance is critical for apps that need lots of processing power and reliable connectivity. They include enormous databases, complex websites, and growing bitcoin-staking operations.
Another essential advantage of servers is security. The server is not shared with other users. So, cross-contamination from other compromised websites or programs is impossible. Users can customize security measures to meet their needs because they have complete control over the server’s security procedures. Advanced firewall configurations, security patches, and intrusion detection systems are a few examples.
Moreover, dedicated hosted servers provide unmatched freedom and customization. Customers can customize their server environment to meet their needs by selecting the operating system, software, and hardware configurations that best suit them. This customization level benefits specialized operations like cryptocurrency staking, where optimizing server speed can directly influence the profits collected.
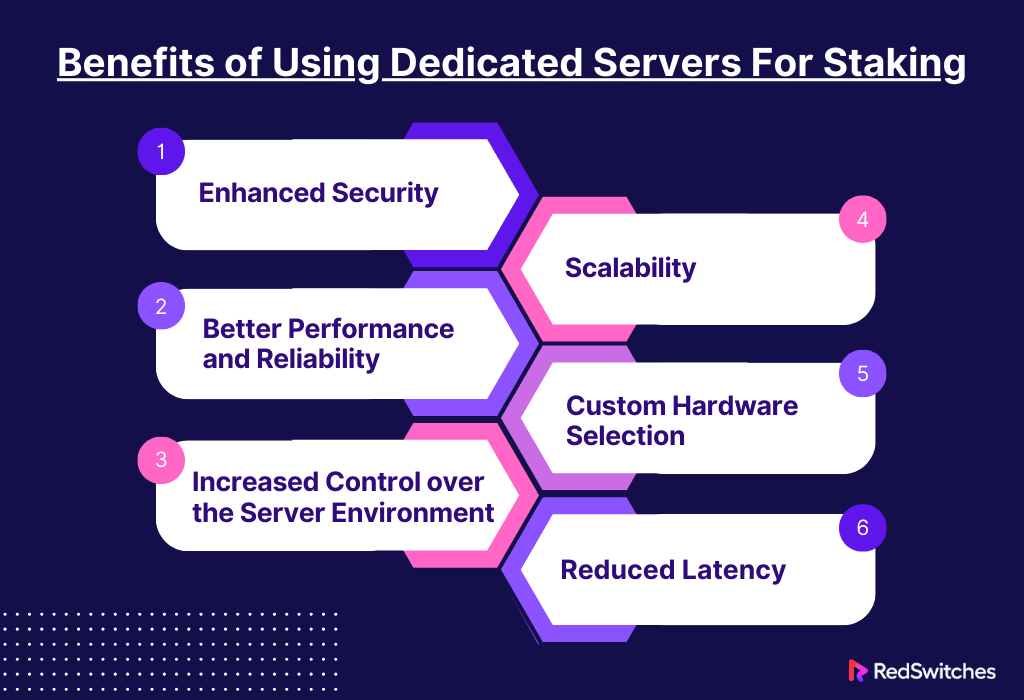
Benefits of Using Dedicated Servers For Staking
Staking in cryptocurrency networks is especially true for those who use Proof of Stake (PoS) techniques. It can be made more profitable and efficient by using dedicated hosted servers. These servers come with several key advantages. The main advantages are listed as follows:
Enhanced Security
Security is crucial in cryptocurrencies, where the stakes equal the currency’s value held or staked. Dedicated private servers offer a secure environment, lowering the risk of threats like DDoS attacks and cross-site contamination. These are common in shared hosting platforms. Users can implement strong security measures, including sophisticated firewalls and intrusion detection systems. Hosting companies supply physical security measures, and users can choose security measures to match their needs. We must protect stakeholder assets from cyber threats. This will preserve potential rewards in this insecure environment.
Better Performance and Reliability
Credits: Freepik
Dedicated private servers provide sole access to resources like CPU, RAM, and bandwidth. This reduces the chance of resource congestion from other users, a common problem in shared hosting. So, staking activities can go more smoothly. This unique resource allocation ensures adequate staking. It is essential for maintaining a validator’s dependability and uptime. High uptime is crucial in many proof-of-stake (PoS) networks because it prevents validators from losing out on chances to create blocks and validate transactions, which immediately affects their staking rewards.
Increased Control over the Server Environment
Users can customize their servers’ operating system, software, and network settings. This degree of control is essential to maximize staking operations’ performance. Staker settings allow them to do many things. For example, they can optimize for the best sync with the blockchain. They can tune network settings for top throughput. And they can install software or security fixes that improve staking.
Scalability
The requirement for scalable solutions grows as the demands of staking operations rise. In this sense, servers excel. They provide the flexibility to add or increase hardware. This includes RAM, storage, and CPU power. And, they do this with the least amount of downtime. This scalability guarantees that infrastructure may grow with stakers’ assets. It lets them diversify into staking many currencies without reconfiguring or moving the system. Furthermore, the capacity to expand or improve redundant systems and backup solutions aids in continuity maintenance and minimizes potential downtime, guaranteeing that business operations stay dependable and stable even as they grow.
Custom Hardware Selection
The customizability of servers adds to their power in addition to their exclusivity. Stakers can pick hardware parts. They should be ideal for their needs. Choosing Solid-State Drives (SSDs) with high speeds, for example, can significantly reduce the time it takes a node to obtain transaction data and engage in consensus, which is essential in times of high-frequency trading. Similarly, using strong CPUs helps speed up the cryptographic computations required to secure the blockchain, improving the server’s speed at processing transactions and validating blocks.
Reduced Latency
In networks where validators are rewarded for responding to consensus requests quickly, latency plays a crucial role in the effectiveness of staking. Stakeholders can deliberately locate their activities closer to the network’s key nodes or even in areas that offer the best connectivity to most users by carefully considering the dedicated private server’s geographic location. This proximity minimizes latency and increases the probability of being chosen to forge or validate new blocks by drastically reducing the time it takes for data to travel between the blockchain and the server. Lowering latency increases the likelihood of receiving rewards and makes it easier for the server to keep up with blockchain changes, preserving the integrity and dependability of the staking process.
Also Read: What Is the Minimum Lockup Period for Crypto Staking?
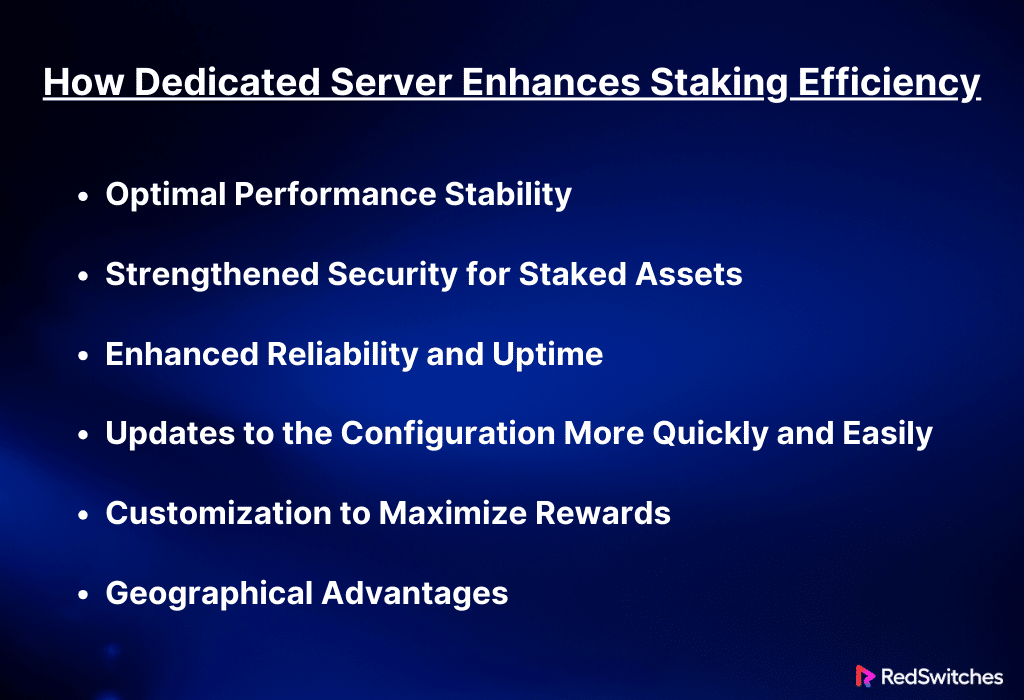
How Dedicated Server Enhances Staking Efficiency
For bitcoin staking, especially on networks using a Proof of Stake (PoS) consensus method, using a dedicated private server dramatically improves staking reliability and efficiency. The following provides thorough explanations of how dedicated private servers aid in these advancements:
Crypto Staking Rewards: Optimal Performance Stability
Dedicated private servers offer a separate environment. In this environment, all resources, including bandwidth, CPU power, and RAM, are allocated only to one user’s staking activity. This exclusivity removes the unpredictability of shared hosting. In shared hosting, the actions of other users may hurt your system’s stability and performance. Staking requires steady connectivity and fast reaction times. These are needed to participate in consensus and collect rewards. Dedicated private servers provide stability to keep these operations running well.
Crypto Staking Rewards: Strengthened Security for Staked Assets
Credits: Freepik
Because cyberattacks could steal staked assets, security is a critical consideration while staking. Dedicated private servers improve security. They offer a regulated environment. Security measures on them may be strictly customized and controlled. To protect their staking activities, users might use complex intrusion detection systems. They can also apply specific firewall settings and set up other security procedures. Physical security measures protect the hardware from unwanted access. Dedicated hosted servers are housed in data centers. The centers have biometric access restrictions, surveillance, and on-site security guards.
Crypto Staking Rewards: Enhanced Reliability and Uptime
A node’s uptime in a proof-of-stake network (PoS) directly affects its chance of being picked to approve transactions. It also affects its chance of generating new blocks. Dedicated hosted servers have high-quality hardware and expert support. The hosting provider includes them as standard features. They reduce the chance of downtime. Uptime guarantees are another feature that many providers offer. They guarantee that the server will keep working with few disruptions. A node’s reputation and efficacy in the network depend on its dependability. Dependability also directly impacts a node’s profitability.
Also Read Validator Node Configuration and Maintenance: A Comprehensive Guide
Crypto Staking Rewards: Updates to the Configuration More Quickly and Easily
By updating system settings on a server, stakers can swiftly adjust to changes in network protocols. They can also improve performance in response to dynamic network conditions. Dedicated hosted servers offer a flexible environment. It can be quickly changed without needing provider approval or bothering other users. This includes changing security in response to new threats. It also includes upgrading the staking software and modifying network settings to improve connectivity.
Crypto Staking Rewards: Customization to Maximize Rewards
Stakers can maximize their rewards by aligning their hardware and software with specific blockchain requirements. They can do this using dedicated hosted servers. This can mean installing staking apps. It can also mean changing the operating system or tuning the server. These steps make the server work best for a cryptocurrency network. With this kind of customization, the server can process transactions more quickly, contribute to consensus more skillfully, and raise the likelihood of receiving rewards.
Crypto Staking Rewards: Geographical Advantages
The location of your dedicated hosted server can significantly impact response times and network latency. Stakeholders can reduce delays by placing the server in areas with the best internet. They can also put it closer to most network nodes. This latency reduction is essential for networks where validators are selected based on timing or where the first responders have a higher chance of receiving transaction fees or block rewards.
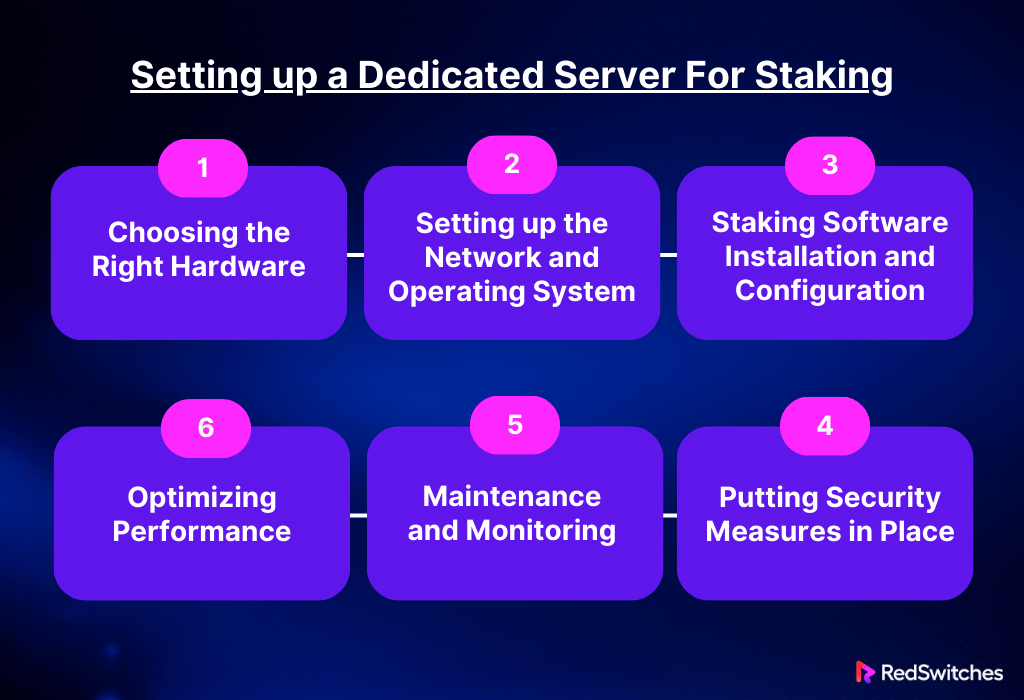
Setting up a Dedicated Server For Staking
Numerous critical processes are involved in setting up a dedicated hosted server for staking, all intended to maximize the server’s capacity for dependable and effective cryptocurrency staking. Here’s how to set up a server, divided into essential sections:
Choosing the Right Hardware
Creating a stable staking server requires careful consideration of the hardware you choose. Essential elements include a strong CPU, enough RAM, and quick storage choices like SSDs. The CPU should be fast enough. It needs to process cryptographic computations and verify transactions quickly. RAM is vital to blockchain software. This is especially true when it handles big ledgers or many transactions. Solid-state drives (SSDs) are preferred over hard drives. They are faster for syncing with the blockchain because they have higher data access speed. Also, think about backup power sources. Consider network connections too. They ensure that the server keeps running if hardware breaks.
Setting up the Network and Operating System
Installing and configuring the operating system (OS) comes after hardware setup. Because of its reliability, security features, and affordability, Linux is frequently chosen. However, Windows can also be utilized, depending on your level of experience and the needs of the staking program. Security should come first when installing the operating system. Ensure the firewall is set up correctly. Turn off unused services and apply all available security updates. Make sure the server is in a data center with low-latency internet. This is especially important for blockchain nodes you plan to stake on. Also, ensure it has a static IP address when setting up the network.
Staking Software Installation and Configuration
Select a staking program compatible with the coin you intend to stake. The blockchain network will determine how this software is implemented. Configure the software according to the network’s requirements once the software has been downloaded and installed from a reputable source. This entails connecting to the blockchain network and configuring the wallet, which will store your money and let you collect incentives. It is essential to back up any required access keys or seed phrases in a safe place and secure the wallet with strong, one-of-a-kind passwords.
Putting Security Measures in Place
Security is essential for shielding your invested money from dangers. Consider adding extra layers of protection to your OS security configuration beyond the basics. For example, you should set up a thorough intrusion detection system, use a secure shell (SSH) with key-based authentication for remote access, and update all software regularly to prevent vulnerabilities. Using encryption to safeguard backups and data storage is also a brilliant idea. To prevent unwanted access, physical security measures at the data centre, like restricted access and surveillance, are equally crucial.
Maintenance and Monitoring
After your server is operational, it must be continuously observed to ensure it runs effectively and safely. Install monitoring software to monitor the server’s disc utilization, CPU load, and network activities. Check the node logs and staking software regularly for any unexpected activity that might point to a malfunction or security issue. Updating the operating system and any essential software to the most recent versions, checking the integrity of backups, and auditing security procedures are all considered maintenance.
Optimizing Performance
Keep improving the server’s performance to increase staking profits. This could entail replacing hardware components, modifying the staking software’s parameters to maximize efficiency, or fine-tuning the network settings to reduce latency. Continuous performance optimization can significantly impact the success of your staking activities.
By carefully following these steps to set up a dedicated hosted server that is safe, effective, and optimized for staking, you can maximize possible rewards while lowering risks.
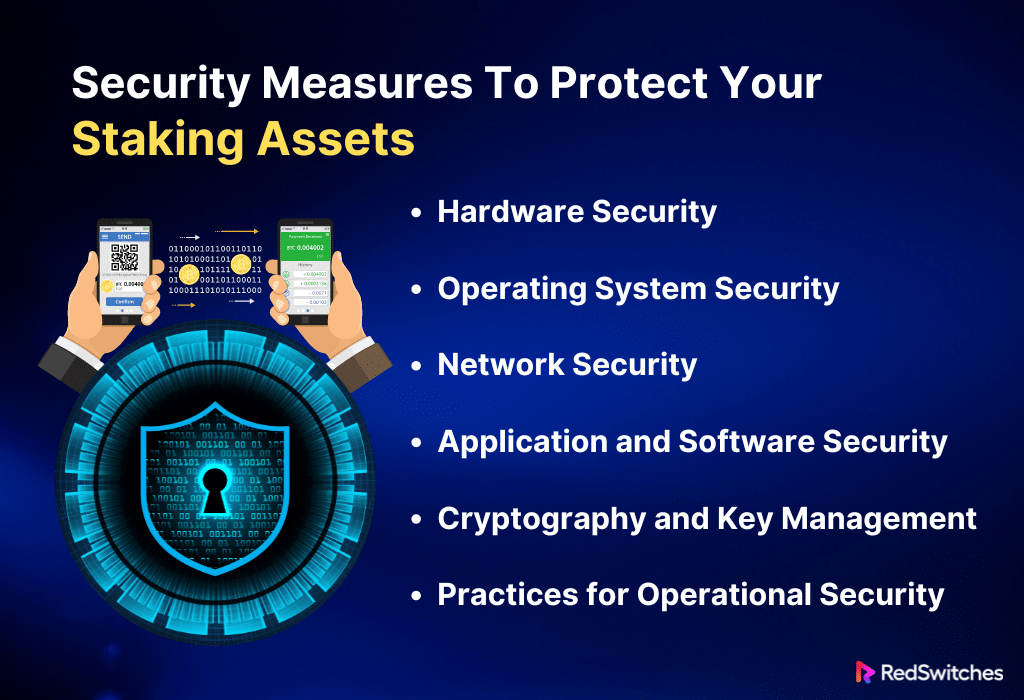
Security Measures To Protect Your Staking Assets
Because staking Bitcoin might involve large bets, it is essential to secure your staking assets. To adequately safeguard your assets, you should put these comprehensive security procedures into place:
Hardware Security
Protecting your server’s physical and hardware security is the first line of defense. It protects your assets. Use dedicated hosted servers. They are housed in safe data centers. Workers there are committed to security. They do surveillance and control access. These facilities also need environmental controls. These controls protect against floods and fires. You should consider using hardware security modules (HSMs). They manage and protect cryptographic keys and activities. You may also avoid downtime and security breaches. Do this by ensuring your server has backup power and network connections in case of hardware failure.
Also read Server Downtime: Causes, Effects, and How to Prevent It
Operating System Security
It’s critical to protect the operating system. Installing a basic operating system version will minimize possible points of attack. Update the operating system frequently to fix any security flaws. Set up the firewall to deny access to unused ports and services. Adhere to OS-specific best practices to ensure that configurations are safe. AppArmor and SELinux are examples. They add more protection by imposing strict access rules on processes.
Also Read: Cost-benefit Analysis of Crypto Staking Using Dedicated Servers
Network Security
Credits: Freepik
You should use a mix of software and hardware firewalls. This will improve your network’s security. A hardware firewall is a solid first line of defense at the network perimeter. Software firewalls on the server can control traffic unique to a given application. Use an advanced intrusion detection system (IDS) like Suricata or Snort. They analyze patterns and spot anomalies in network traffic. This gives more profound insights into possible security breaches. Use a virtual private network (VPN) to secure all remote connections. Make sure that robust protocols like OpenVPN or WireGuard are used to encrypt all communications to and from the server.
Application and Software Security
To guarantee that all software is up to date and secure, strictly adhere to version control and patch management protocols and install only necessary apps. Use solutions such as Ansible or Patch Manager Plus for uniformity throughout your infrastructure and automated software updates. Use application whitelisting technologies, such as AppLocker or the targeted policy mode of SELinux, to stop unauthorized software from running. Using technologies such as Nessus or OpenVAS, regular vulnerability scanning can find possible security flaws before they are exploited.
Cryptography and Key Management
To manage cryptographic keys at every stage of their lifecycle, from generation to retirement, consider implementing a centralized key management system (KMS). Use robust encryption protocols like TLS 1.3 for data in transit and AES-256 for data at rest. To perform sensitive processes in a tamper-resistant environment and physically secure cryptographic keys, think about hardware-based solutions like HSMs (Hardware Security Modules) for increased security. In addition to providing an additional layer of security, multi-signature wallets also offer recovery and audit capabilities. By requiring many parties to approve transactions before they are carried out, they lower the possibility of fraud or theft.
Practices for Operational Security
Improve operational security, trace access, and modify the stake environment with extensive logging and monitoring tools. Logs can be compiled using security information and event management (SIEM) systems for in-the-moment analysis and suspicious activity alerts. To further secure access to vital systems, promote the usage of hardware tokens or biometric verification as part of two-factor authentication. By holding frequent training sessions and updates, keep team members informed on the most recent cybersecurity dangers and best practices. Since human error is still one of the biggest security threats, it is imperative to establish a strong security culture.
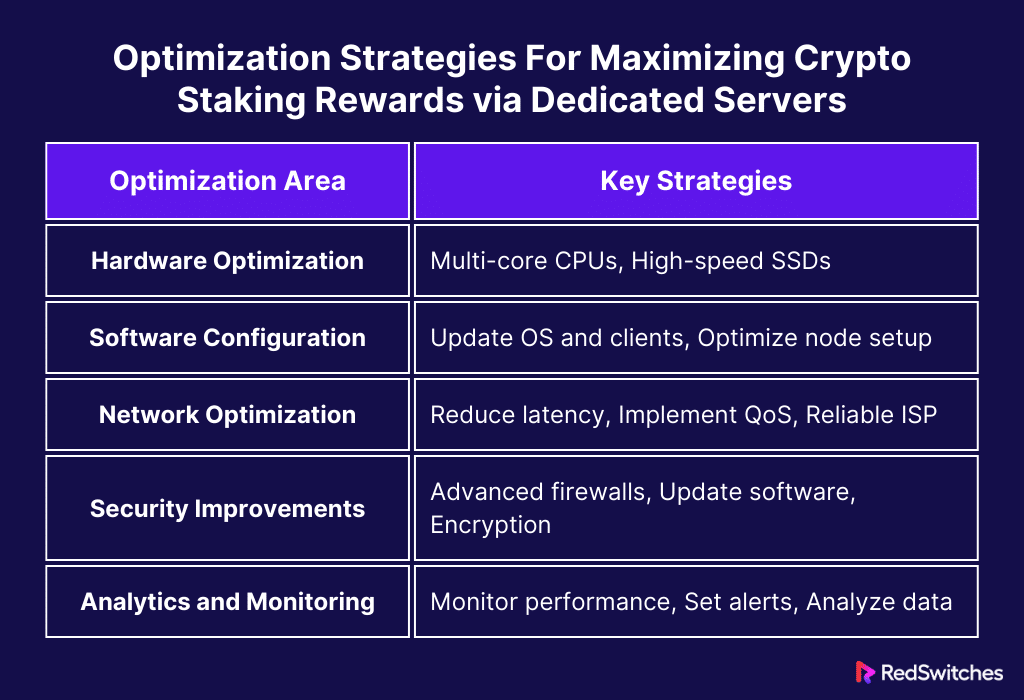
Optimization Strategies For Maximizing Crypto Staking Rewards via Dedicated Servers
Credits: Freepik
Staking-optimized server configuration is essential for optimizing payouts in cryptocurrency networks, especially those that employ Proof of Stake (PoS) techniques.
Crypto Staking Rewards: Hardware Optimization
The hardware you use affects your staking activities. It impacts their performance and dependability. They must have many cores. And, they must have high clock speeds. The blockchain needs a lot of RAM. It uses it for memory-heavy operations to keep working nonstop. SSDs have higher data access speeds. So, they are preferred over hard disc drives for syncing with the blockchain and quickly getting transaction data. Also, buying high-speed network interfaces can quickly improve your server’s ability to talk to the blockchain. These can significantly cut network delays.
Crypto Staking Rewards: Software and Node Configuration
One way to optimize the software is to choose a stable, lightweight operating system. These systems, such as CentOS or Ubuntu Server, can be adjusted for performance. The staking software should be the most reliable. It should be the best client for your chosen cryptocurrency. It must also be updated to take advantage of new features and security improvements. It is essential to properly configure your node so that it can be in constant and quick communication with reliable peers in the network. This will minimize the likelihood of downtime and guarantee that your server will always be involved in consensus processes and transaction validations.
Crypto Staking Rewards: Network Optimization
The network’s performance dramatically impacts how well your staking operation runs. Locating the data center near the central nodes of the blockchain network is helpful. It reduces latency and improves responsiveness. You can prioritize staking-related traffic on your network. Do this by putting Quality of Service (QoS) policies in place. This will guarantee fast data processing when network traffic is at its peak. It’s essential to collaborate with a reputable Internet service provider (ISP) to guarantee consistent, quick Internet access to avoid any potential downtime and maintain the functionality of your server inside the blockchain network.
Crypto Staking Rewards: Improvements in Security
Staking activities depend heavily on security since they shield your assets from online attacks. Advanced firewalls and intrusion detection systems can improve server security. They do this by thwarting threats and preventing unwanted access. To defend against new vulnerabilities, update all software components. This includes the operating system and staking client. Other ways to protect your staking activities from security breaches include: putting in strong access controls. Also, use encryption for communication and data storage.
Crypto Staking Rewards: Analytics and Monitoring
Constantly monitoring the server’s performance makes it easier to spot problems early on and take quick action to fix them, guaranteeing steady staking operations. Performance monitoring tools can be used to troubleshoot issues immediately, tracking metrics like CPU usage, disc activity, RAM consumption, and network speed in real-time. The efficiency and profitability of your staking operations can be further increased by setting up alert systems for anomalies in system operations and regularly analyzing performance data to gain insights into trends and possible areas for system optimization.
Let’s summarize it in a tabular format.
Risks Involved with Crypto Staking Rewards and How Dedicated Servers Can Mitigate it
Although it is profitable to earn passive income from Bitcoin crypto holdings, cryptocurrency staking carries many hazards. Anyone participating in staking must comprehend these hazards and how installing dedicated hosted servers can reduce them.
Crypto Staking Rewards Danger of Slashing
To preserve network integrity in Proof of Stake (PoS) networks, validators must behave honorably and uphold strict operational requirements. Validators can be punished by cutting, which involves forfeiting some of the staked tokens, if their node goes down, double-signs transactions, or engages in malicious activity. Dedicated hosted servers can significantly reduce this risk with uptime assurances and dependability. Suitable hardware and expert maintenance guarantee that the server stays online and functions properly, reducing the possibility of unintentional errors that could cause slashing.
Crypto Staking Rewards Risk of Security Breach
Since attackers could try to acquire private keys or target the staking infrastructure directly to reroute staking payments, security is a big worry with crypto staking. Dedicated hosted servers offer more protection than home setups or shared hosting. They make it possible to put strong security measures in place at data centre locations, like sophisticated firewalls, intrusion detection systems, and physical security. By preventing unwanted access and external threats, these safeguards help preserve staked assets and the profits they produce.
Crypto Staking Rewards Risk of Downtime
In Proof of Stake (PoS) systems, validators must ensure continuous access to the blockchain network. Any interruption can lead to lost opportunities for validating blocks and staking rewards. Service Level Agreements, or SLAs, are often included with dedicated hosted servers, ensuring high uptime. Furthermore, redundancy in networking, cooling, and power supply is a feature of dedicated hosting facilities’ physical architecture that lowers the chance of downtime.
Crypto Staking Rewards Risk of Performance Inefficiency
A staking node’s capacity to process transactions and efficiently suggest new blocks may impact the benefits derived from staking. Dedicated hosted servers provide several benefits in terms of memory, processing power, and network capabilities—all of which are essential for preserving optimal operating efficiency. Resource starvation is a typical problem in shared environments, and our specialized resource allocation ensures that the staking activities are not hampered.
Crypto Staking Rewards Risk of Software Mistakes
Software mistakes or bugs in the staking program can cause misconduct that may inadvertently result in punishment. Before being implemented on the production node, a dedicated hosted server can thoroughly evaluate updates and modifications in a controlled environment. In this regulated environment, it is less likely to run corrupted or defective software, which could result in money losses.
Future Trends in Staking and Server Technology
Developments in blockchain technology have caused the rise of cryptocurrencies. The creation of decentralized apps has also played a part. These things have changed Bitcoin staking and server tech. Here are some big future changes. They could affect server technology and staking.
Increased Adoption of Proof of Stake Protocols
People worry about the environmental effects of Proof of Work (PoW) Systems like Bitcoin. This has led to a major movement favoring Proof of Stake (PoS) and other more energy-efficient techniques. PoS not only lowers the needed energy. It also lets more people participate. It makes the process of preserving the blockchain fairer. This change is anticipated to raise the demand for staking services, which will drive server technology to become more specialized and task-specific.
Staking-as-a-Service (SaaS) platforms
They are growing in popularity. They make it easier for private investors to stake. This is true even if they lack the resources or know-how to manage their nodes. This trend will likely drive server advancements. They will focus on providing more secure, scalable, and intuitive systems. These platforms must guarantee strong security, high availability, and regulatory compliance to draw and keep a large user base.
Improvements to Server Hardware and settings
Efforts will be made to improve server hardware and settings. These changes will manage the higher load and security needs of cryptocurrency networks that are active 24/7. Future servers may include advanced CPUs, faster memory, and better networks. This is to meet the needs of modern blockchain apps, which require high throughput and low latency. They may also use hardware security modules (HSMs) to secure stake servers’ cryptographic operations further.
Decentralization of Staking Networks
Staking networks are increasingly being decentralized. This is to prevent central points of failure and reduce trust issues. This trend could cause the use of decentralized cloud technologies and edge computing. It could also cause the development of more distributed and resilient server systems. These technologies can improve the networks’ failure tolerance and aid in more effectively distributing the stake load.
Integration of Artificial Intelligence and Machine Learning
Integrating AI and machine learning technology with server administration may change how staking operations are tracked, optimized, and secured. AI might be applied to dynamic resource allocation based on real-time network demands or predictive maintenance, which would identify possible hardware issues before they happen. By identifying odd patterns that might point to a security issue, machine learning models have the potential to improve security systems as well.
Regulatory Compliance and Security Standards
As the staking sector expands, regulators will probably monitor it more closely, which may result in stricter compliance and security requirements. Better data protection technologies, audit trails, and compliance monitoring tools will all need to be incorporated into server technology as it evolves to meet these regulatory requirements.
Also Read: Mastering Best Practices for Blockchain Monitoring in Staking Nodes
Conclusion
Using dedicated hosted servers to maximize crypto staking rewards offers a compelling advantage for cryptocurrency fans. Servers offer the dependability, security, and performance optimization essential for staking operations to be successful and efficient. Servers can greatly increase the profitability and stability of staking activities by guaranteeing high uptime, strong security measures, and ideal hardware configurations.
RedSwitches provides dedicated server options to satisfy crypto staking rewards for anyone wishing to start or advance their staking journey. RedSwitches is a great option for anyone serious about optimizing their staking returns in the exciting world of cryptocurrencies since we offer stakers top-notch hardware, outstanding uptime, and performance- and security-focused customer service.
FAQs
Q. Which crypto has the highest staking rewards?
Incentives for the highest stakes can differ. But, cryptocurrencies with competitive returns include Ethereum, Solana, and Cardano.
Q. How much can you earn with crypto staking?
Profits from crypto staking can range from 5% to 20% a year, depending on the coin, staked amount, and network circumstances.
Q. Is staking crypto high risk?
Yes, staking cryptocurrency has risks. These include market swings, slashing, and security worries. They might affect capital and returns.
Q. How does staking work in the world of cryptocurrencies?
Staking involves holding cryptocurrency in a wallet to support the operations of a blockchain network. In return, stakers can earn rewards for helping to secure the network.
Q. What are the risks of staking crypto?
Staking has risks. They include the loss of staked assets due to network issues, slashing penalties for bad behavior, and market volatility.
Q. What is a staking platform?
A staking platform is a service or software that allows users to stake their cryptocurrencies without technical knowledge or hardware setup.
Q. How can I start staking my crypto?
You must pick a platform or supported exchange to start staking your crypto. Then, transfer your crypto to the staking pool and follow the platform’s instructions.
Q. Which cryptocurrencies are considered the best for staking?
Some popular cryptocurrencies for staking include Ethereum, Tezos, Cardano, and Polkadot. The best choice may vary based on reward rates and staking mechanisms.
Q. How can I earn crypto rewards through staking?
By staking your crypto assets, you can earn rewards in the form of extra tokens. These tokens are given as incentives for improving the network’s security and decentralization.
Q. What risks are involved in staking, and how can they be mitigated?
Staking involves risks, including potential financial losses, technical vulnerabilities, and external market factors. To mitigate these risks, you must diversify your staking activities, stay informed, and only invest what you can afford to lose.