Key Takeaways
- Dedicated servers ensure top security and performance for online transactions.
- They offer unparalleled control, customization, and exclusive resource use.
- Advanced encryption, firewalls, and DDoS protection bolster cyber defense.
- Scalability allows for growth and adaptation to fluctuating demands.
- Regular security audits and updates maintain high defense levels.
- Redswitches provides robust dedicated servers, ideal for secure transactions.
- Choosing the correct server involves assessing hardware, support, and pricing.
The security of transactions is more important than ever in the digital age when online transactions have taken center stage in our economy. As cyber threats are quickly changing, organizations need to strengthen their defenses. A dedicated server is the unsung hero of cyber security.
Dedicated servers offer unmatched security, performance, and dependability. They are essential for secure online transactions and are a big step up from shared hosting. This blog examines how important servers are for making transactions secure. They provide a glimmer of light in the dark seas of cyberattacks.
As we make our way through the maze of internet security, servers become increasingly important. They are resilient protectors of the digital sphere. Additionally, they offer a stronghold and a shield. They defend from the constant barrage of assaults that threaten the security of online transactions.
Come learn how utilizing dedicated server for transactions security.
Table of Contents
- Key Takeaways
- What are Dedicated Servers?
- Key Features of Secure Dedicated Servers
- Advantages of Servers for Online Transactions
- Common Threats to Online Transactions
- How to Secure Your Online Transactions with Robust Dedicated Server Solutions
- Use Dedicated Servers to Adopt More In-Depth Encryption techniques
- Make Use of Intrusion Detection Systems and Dedicated Firewalls
- Turn on DDoS Protection
- Update and Patch Servers Frequently
- Put Strict Access Controls in Place
- Conduct Regular Security Audits
- Use Secure Payment Gateways
- Educate Users and Staff
- Factors to Consider When Choosing the Right Dedicated Server Provider
- Conclusion
- FAQs
What are Dedicated Servers?
Credits: Freepik
A dedicated hosting server is for a single client. In shared hosting, several clients share CPU time, RAM, and disc space on one server. On the contrary, a dedicated hosted server provides the client with access to all server resources. This exclusivity enables an unmatched degree of personalization and control over the server environment.
One of its most significant advantages is the exclusive use of a server’s resources. This guarantees the customer’s site works well. It works well even during high traffic. The client does not share server bandwidth, processing power, or storage with other clients. Having exclusive access to resources is very important for sites with lots of traffic. It’s critical for e-commerce systems handling secure transactions or any app needing lots of processing and storage.
Dedicated servers also provide an excellent level of control and customization. With root or administrative access, clients can install any program and make necessary configurations. This degree of access is crucial for companies who need to adhere to tight data handling standards, have specific software requirements, or just want to maximize the speed of their server environment. Customizing the server configuration guarantees that companies may create a hosting environment. It will precisely match their requirements.
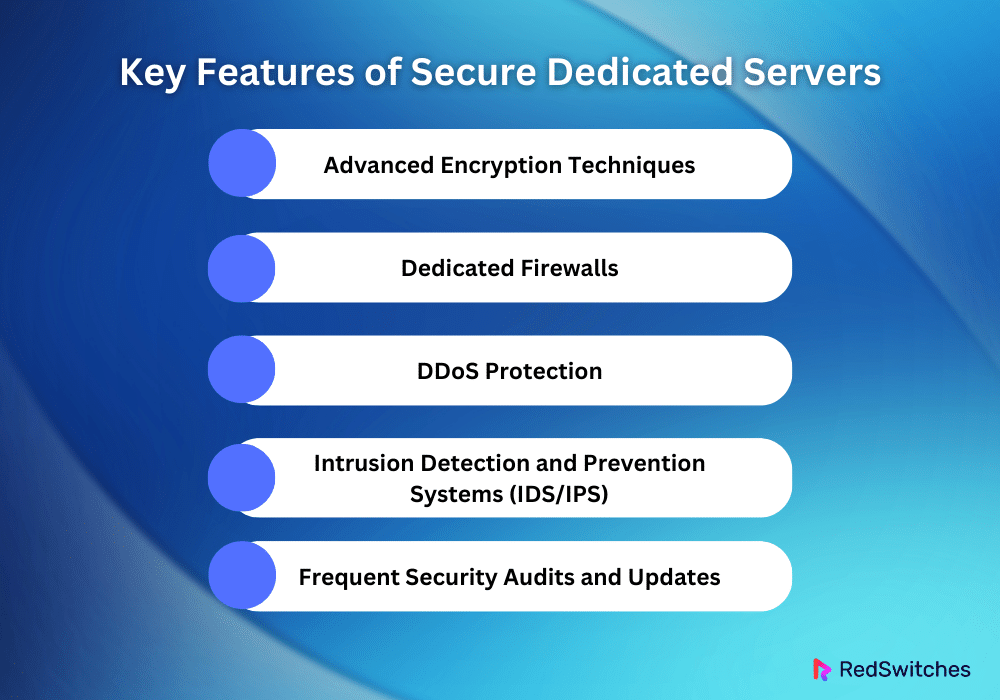
Key Features of Secure Dedicated Servers
Secure servers provide the best performance and security. They are designed to host vital applications and handle sensitive data. The servers have many security mechanisms. They guard against cyber threats like DDoS attacks and data breaches. The following are the main characteristics that make servers very safe:
Advanced Encryption Techniques
Secure servers use top encryption. They do this to ensure data integrity and secrecy. An essential part of this procedure is installing SSL/TLS (Secure Sockets Layer/Transport Layer Security) certificates. They make a secure path for data and protect private data from interception and man-in-the-middle attacks.
Disc encryption protects data on a server’s hard discs. It does this by encrypting the data. This keeps the data safe while it’s not in use by making it unreadable to unauthorized users. This dual-layer encryption guarantees complete data safety. It protects data when it leaves the user’s device and when it is stored on the server.
Also Read: Unveiling the Hidden Risks of Dedicated Servers
Dedicated Firewalls
Dedicated firewall systems have a significant benefit: their customization capacity. This lets them make exact security setups tailored to the company’s unique needs and threat profiles. These firewalls serve as the initial defense against various cyberattacks and unauthorized access.
Administrators can protect the server environment from untrusted networks. They can ensure that only genuine communication is permitted. They do this by carefully designing rules that control both inbound and outbound traffic. Robust network security requires constant monitoring. It needs firewall rule changes to respond to changing cyber threats.
DDoS Protection
DDoS attacks are a persistent threat to internet businesses. So, safe servers must have DDoS protection. These systems are made to keep service running. They absorb and lessen the deluge of traffic in DDoS attacks.
Advanced filtering techniques tell valid from bad traffic. They let us quickly process good requests. This protection requires using advanced traffic analysis tools. They are used to quickly find and stop threats. Also, it requires having extra bandwidth for unexpected spikes.
Intrusion Detection and Prevention Systems (IDS/IPS)
Before they can compromise server security, IDS/IPS systems are essential. They find and stop unauthorized access and other cyberattacks. The IDS is an early warning system. It monitors system and network activity for signs of lousy activity or policy violations.
The intrusion prevention system (IPS) component goes further. It actively blocks recognized threats to stop possible assaults from using weaknesses. The systems are constantly evolving. They can defend against new threats. They ensure a proactive and robust security posture for the server.
Frequent Security Audits and Updates
You need to monitor and apply security patches and updates often. This is key for keeping a secure server. These tasks are essential for locating and fixing security holes that hackers might use against you. Security audits provide a complete analysis of server security. They point out weaknesses and ensure compliance with legal and best practice standards.
Regularly updating installed software and the operating system is equally vital because it fixes security holes and improves the server’s defenses. This improvement cycle is critical. It keeps the security of servers high. It protects them from the changing array of cyber threats.
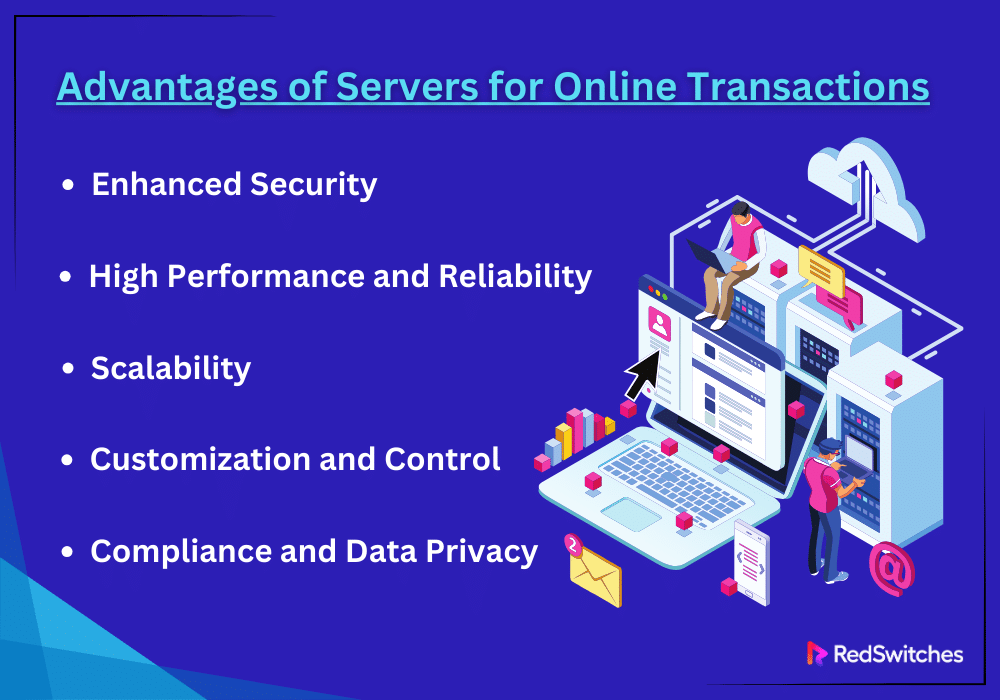
Advantages of Servers for Online Transactions
Dedicated servers are the favored option for companies. They value security, dependability, and performance. This is because these servers offer many benefits for managing online transactions. These servers offer a setting where transactions are fast and secure. They guarantee a good user experience and protect private data.
The specific benefits of utilizing servers for online transactions are listed below:
Enhanced Security
Server Security for online transactions is critical. Dedicated servers are essential for protecting against a wide range of online dangers. Dedicated servers allow businesses to install advanced security methods. They can tailor these to meet their unique needs beyond basic security. This can mean making intelligent intrusion detection and prevention systems. They act as a second line of defense. They scan for and remove threats. Customizing security settings helps. It enables you to install strict access restrictions. This further reduces the risk of internal threats by ensuring that only authorized staff can access important data. Dedicated servers are isolated from other users. This causes a natural decrease in the attack surface. It gives them a stronghold against attempts to undermine data integrity and confidentiality.
High Performance and Reliability
Dedicated servers offer the best performance and dependability. They give organizations that rely on online transactions a robust platform. The exclusive resource allotment removes the risk of server overload. It guarantees that websites and applications are still accessible, even during high traffic. The reliability comes from top-notch hardware and a well-optimized network. They reduce latency and ensure quick transactions. Dedicated servers are vital for e-commerce. They have high performance and dependability. They can directly impact consumer happiness and loyalty. They do this by offering a seamless, uninterrupted user experience.
Scalability
Dedicated servers are great for hosting. They adjust to fluctuating demands. E-commerce is a dynamic domain. In addition to managing more traffic, servers’ scalability allows them to accommodate new features and applications as companies grow. This might mean adding more payment options. It could also mean using new technology or growing the online stock. Dedicated servers are vital for business growth. They allow firms to grow without being held back by their IT. They can increase resources as needed.
Customization and Control
Credits: Freepik
Businesses may establish an optimized hosting environment that satisfies their operational requirements thanks to the degree of customization and control that servers offer. This covers hardware components, network configuration, performance optimization, security settings, and software. It can be used for data-intensive applications, multimedia-rich websites, or high-transaction e-commerce sites. This customization makes sure the server is tuned to fit the specific workload. This control improves security and performance. It gives companies the flexibility to adjust quickly to changing consumer demands and market conditions.
Compliance and Data Privacy
For online companies, compliance, and data privacy are now most important. This is because data breaches can be costly and harm a brand’s reputation. Servers provide a regulated environment. It makes it easier to handle compliance with rules like PCI DSS. This means being able to put strict data security procedures in place. You must also do frequent security audits. You must ensure that all transactional data is encrypted and kept in a safe location. Also, the privacy of servers is crucial. It helps build trust with clients. They are more worried about how data is handled and its security.
Common Threats to Online Transactions
Credits: Freepik
Even if they are handy and necessary in the current digital era, online transactions are vulnerable to various security risks. These dangers threaten personal financial data. They also threaten companies’ integrity and good name. It is essential to comprehend these typical hazards to implement efficient security measures. A thorough examination of some of the most common risks to online transactions is provided below:
Phishing Attacks
Phishing is a serious cybersecurity risk. It uses advanced social engineering to attack people. Attackers frequently use urgent language in their emails to pressure the recipient to respond immediately, eschewing caution and security awareness. The misleading emails can have attachments with malware or links that take users to dangerous websites. Spear phishing uses highly customized tactics to target specific people or organizations. Whaling targets prominent targets like executives. Both are examples of how phishing has changed. Using advanced email filters and teaching people to spot phishing are vital defenses.
Attacks Known as “man-in-the-middle” (MitM)
These attacks are very sneaky since they can obtain much private data without the victims’ knowledge. These assaults can happen on unprotected Wi-Fi networks. They can also happen on compromised websites or devices infected with malware. Attackers infiltrate the communication channel. Important defenses against MitM attacks include using virtual private networks (VPNs) for secure connections. Also, they include using robust encryption protocols like TLS (Transport Layer Security). And, they include routine security software updates.
Distributed Denial of Service or DDoS
They are gaining popularity as a tactic in cyber warfare. They can interrupt operations or demand ransom. They target the government, financial institutions, and enterprises. These assaults use the internet’s interconnectedness. They often use botnets, which are networks of compromised computers. Botnets create vast amounts of traffic. DDoS attacks have become more complex. Attackers use methods like DNS amplification to significantly increase the volume of strikes. A multi-layered strategy is needed to defend against these attacks. These strategies include actively exchanging threat intelligence to foresee and prevent attacks before they happen, using advanced behavioral analysis to distinguish between legitimate users and attack traffic, and over-provisioning bandwidth to handle sudden spikes in traffic.
SQL Injection
The effects of SQL Injection attacks go beyond just losing data right once. They can cause severe financial and legal ramifications, erode user confidence, and harm a company’s brand. Even harder to identify and avoid are advanced SQL Injection techniques like Blind SQL Injection, which use the database’s logic to extract data without apparent flaws. In addition to safe coding techniques, effective defense tactics include using web application firewalls (WAFs), which can identify and prevent SQL Injection attacks. Regular security awareness training is essential for developers to have a thorough understanding of the most recent attack vectors and mitigation strategies. Furthermore, using the least privilege principle for database access reduces the possible consequences of an SQL Injection incident.
Cross-Site Scripting (XSS)
XSS attacks can result in more than instantaneous data alteration or theft. They may also weaken the fundamental trust between a customer and a service, resulting in long-term harm to the company’s reputation and decreased revenue. Because rich Internet applications and frameworks are becoming increasingly common, XSS vulnerabilities have found new homes, necessitating increased awareness and proactive security measures. Content Security Policies (CSP) can be adjusted to limit the origins of executable scripts, effectively neutralizing the effects of cross-site scripting (XSS) attacks in addition to input validation and sanitization. Finding and fixing XSS vulnerabilities is essential to protecting web apps from ever-changing threats. Regular penetration testing and security assessments help achieve this.
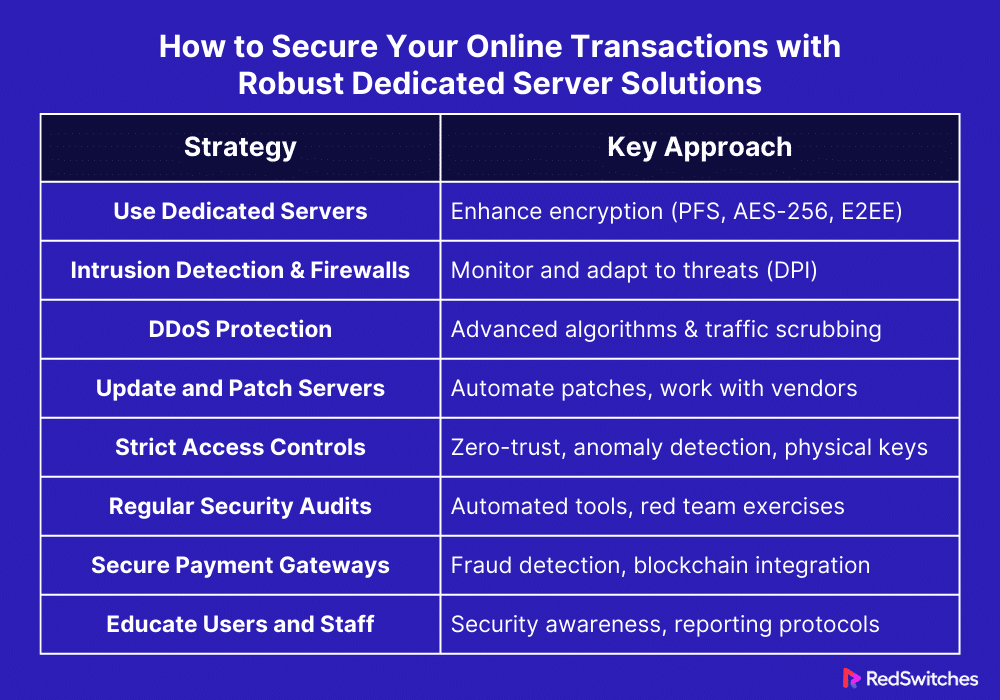
How to Secure Your Online Transactions with Robust Dedicated Server Solutions
Credits: Freepik
Today’s digital world has significant risks to the integrity and privacy of data. These risks exist while data is moving and when it’s still. The security of online transactions is critical. Sturdy server solutions are vital. They protect online transactions from many cyberattacks. The following are some ways that companies can use server solutions to safeguard their online transactions:
Use Dedicated Servers to Adopt More In-Depth Encryption techniques
Dedicated servers let firms use better encryption, like perfect forward secrecy (PFS). PFS guarantees a session key cannot be compromised if the private key is. This goes beyond standard TLS encryption. Businesses can also encrypt data in transit with end-to-end encryption (E2EE). It ensures that only the recipient can decrypt the data. Using modern encryption, such as AES-256, can protect data at rest. It can make it very hard for hackers to read critical data without the right keys.
Make Use of Intrusion Detection Systems and Dedicated Firewalls
Dedicated firewalls and intrusion detection systems (IDS) can improve security. They do this by ongoing monitoring and changing settings to respond to new threats. DPI allows firewalls to inspect data packets. They look at the packets’ contents and headers. DPI is for thoroughly checking incoming and outgoing traffic. This research helps find and stop complex threats. They could block less strict security. IDS, on the other hand, can be integrated with international threat intelligence networks to refresh its signature database in real time, enabling it to identify and address emerging threats.
Turn on DDoS Protection
It can use advanced algorithms and machine learning. This way, DDoS protection can tell apart real and bad attack traffic better. This reduces false positives and ensures it does not block real users. On-site DDoS appliances can do initial traffic scrubbing. They can also do external DDoS mitigation. This provides an extra line of defense. These solutions are beneficial for stopping complex, multi-vector DDoS attacks. These attacks include volumetric, protocol, and application layer attacks. Their DDoS protection is scalable and adaptable. It helps businesses adapt their defense to changing threats and traffic.
Update and Patch Servers Frequently
Automating patch management for servers reduces the chance of human mistakes. It ensures that updates are installed as soon as they are available. This prevents attackers from exploiting vulnerabilities. Centralized patch management systems enable scheduled updates during off-peak hours to reduce disturbance. They also give visibility into the patch status of all servers. They can help achieve this automation. You must work closely with hardware vendors. They will tell you about firmware updates. You must know the possible effects these updates may have on server performance. The patch management procedure should be routinely audited to guarantee that no software or devices are missed.
Put Strict Access Controls in Place
The zero-trust approach goes beyond ID checks. It also monitors user behavior for signs of compromise or insider threats. Anomaly detection systems may be used to notify users of anomalous access patterns or data usage. Using physical authentication tools, like security keys or smart cards, adds an extra layer of protection. They are for highly sensitive systems. They are hard to duplicate or steal. You should document all-access policies. You should routinely review access logs. They can show policy violations or where access restrictions need to be strengthened.
Conduct Regular Security Audits
To ensure security, we use automated tools. They can search for vulnerabilities more often. This is part of continuous security audits. Red team exercises and other attack simulations can evaluate how well security procedures and incident response plans work. These tools are used for that purpose. The entire supply chain is made secure by including in these audits the assessment of third-party vendors and their access to the server environment. To guarantee that the company not only reacts to present dangers but also proactively fortifies its defenses against future difficulties, the insights obtained from routine audits and penetration testing should be incorporated into a continuous development process for security procedures.
Use Secure Payment Gateways
Companies should think about putting in place sophisticated fraud detection and prevention systems that can function in conjunction with their payment gateways, in addition to the initial establishment of secure, isolated environments for payment processing on servers. These systems examine transaction patterns in real-time to spot and report possible fraudulent activity, such as odd purchase quantities or a sudden string of transactions from the same user. With its decentralized and unchangeable ledger system, blockchain technology can provide additional protection to payment processing, guaranteeing transparency and lowering the possibility of fraud.
Educate Users and Staff
Companies can create a comprehensive security awareness program that includes regular newsletters, security bulletins, and workshops highlighting the newest cybersecurity trends and threats to emphasize further the value of security awareness among users and staff. Establishing a security-conscious culture within the company empowers staff members to assume responsibility for protecting the business’s digital assets. Real-world case studies and the lessons discovered from current security breaches can offer valuable insights into the repercussions of security lapses and the significance of being vigilant. To ensure that staff members know who to call and what to do in the event of a possible security breach, businesses should also set clear policies and procedures for reporting suspected security events.
Let’s summarize it in a tabular format.
Factors to Consider When Choosing the Right Dedicated Server Provider
Credits: Freepik
When choosing a dedicated server provider, you need to consider several key factors. They ensure the best performance, security, and scalability for your needs. A thorough understanding of these issues will make making an informed choice easier.
Performance and Quality of Hardware
The hardware requirements of your server are the foundation of its performance. Thanks to a strong CPU, your apps and the traffic they manage will operate smoothly without lag or downtime. The amount of RAM is also significant. Enough memory is needed for reliable functioning under various loads. Storage options are also important. SSDs can improve performance a lot. This is especially true for data-intensive applications. It’s because SSDs have faster data access speeds than HDDs. Finally, fast data transfer rates are guaranteed by network performance. It is defined by high bandwidth and low latency. This is essential for preserving good service quality and user happiness.
Reliability and Uptime
Credits: Freepik
Uptime and reliability directly impact your online presence’s operational continuity and trustworthiness. Providers who pledge 99.9% or more uptime show they are dedicated to minimizing downtime. Redundancy and failover systems’ design adds extra protection. It guards against possible hardware failures. It ensures that services will continue. Also, the location and quality of data centers are crucial. Good design improves servers by managing connections and the environment. It also supports reliability.
Security Features
To protect your server from a variety of attacks, security features are a must. DDoS defense is necessary to fend off attack tactics that have the potential to obliterate your online business. The first lines of defense against unwanted access are good firewalls. They are also intrusion detection systems. SSL certificates are essential for safely transferring sensitive data since they guarantee encrypted and secure interactions between your server and its customers.
Support and Services
Suppliers’ support and services can significantly impact your management workload and mental well-being. We need around-the-clock technical support. It gives fast help for any problems. Depending on how capable you handle server maintenance, you can choose between managed and unmanaged services. Managed services provide total control over maintenance. Unmanaged services give you more technical know-how. Also, reliable backup services are essential for disaster recovery. They allow for quick data restoration to lessen the effects of data loss.
Flexibility and Scalability
It guarantees that your server infrastructure may change to meet your needs. If it is simple to update its CPU, RAM, and storage without experiencing a significant loss of functionality, your server may expand with your company. Options for customization are vital for users with specific needs. They ensure the server can be adapted to fit particular workloads or applications. This makes a platform that can meet various demands.
Pricing and Contract Terms
These factors affect your budget. They are essential when choosing a server supplier. Transparent pricing structures are crucial. They prevent unexpected fees that could raise costs beyond your budget. It’s critical to comprehend the whole cost breakdown, which includes startup fees, recurring expenses, and any possible expenditures for extra services or overages. Contract terms are also essential to read carefully because they specify the criteria for renewal, the time commitment, and how services can be upgraded or downgraded. Flexible contract terms allow providers to more readily adapt to changing needs or corporate growth. Furthermore, a money-back guarantee can act as a safety net, providing comfort and a risk-free means of testing services to ensure they fulfill your needs.
Conclusion
In conclusion, companies that prioritize safe, dependable, high-performance transaction processing must carefully consider their dedicated server provider options. Thanks to several factors, including scalability, transparent pricing, security features, hardware quality, and uptime reliability, your online transactions are performed securely and swiftly.
Redswitches stands out as a notable supplier when considering these important factors, providing reliable dedicated server solutions designed to satisfy the demanding requirements of applications with a high transaction volume. Our dedication to top-notch hardware, outstanding uptime, all-encompassing security protocols, and expandable server options sets us apart as a leading option for companies looking for a dedicated server platform.
RedSwitches empowers you to create a secure and seamless client experience while ensuring your online transactions remain reliable and efficient. Contact us today to explore our dedicated server solutions and discover how we can elevate your online business!
FAQs
Q. What is an example of a dedicated server?
A dedicated server can be a high-end HP ProLiant DL380 Gen10 server that is only utilized for web hosting or intensive data processing by one company.
Q. Is a dedicated server private?
Indeed, a dedicated server offers unrivaled control and privacy through shared hosting options, as it is solely designated for one client.
Q. Are dedicated servers online?
Dedicated servers, which are kept in data centers to guarantee continuous internet access and availability for hosting websites or services, are, in fact, always online.
Q. What is the role of servers in mastering transaction security?
Servers play a crucial role in ensuring transaction security by providing a dedicated hosting environment where sensitive data and transactions are processed securely.
Q. Why do I need a server for transaction security?
Unlike shared hosting or VPS hosting, a server provides exclusive access and control over the server, making it ideal for handling sensitive customer data and ensuring a high level of security.
Q. What are the advantages of dedicated hosting for transaction security?
Dedicated hosting ensures that the server is a physical entity dedicated solely to your business, offering enhanced security, performance, and customization options compared to shared hosting or VPS hosting.
Q. How to choose a dedicated hosting provider for transaction security?
When selecting a server hosting provider, consider factors such as server administration capabilities, level of security provided, managed hosting options, and whether the hosting plan suits your specific security needs.
Q. What are the uses of servers in ensuring transaction security?
Businesses commonly use servers that handle sensitive transactions, such as e-commerce sites, financial institutions, and healthcare organizations, to ensure the secure processing of customer data.
Q. What are the benefits of a server in enhancing transaction security?
Utilizing a server allows you to have full control over the security measures implemented, including encryption, firewall settings, and access permissions, thereby enhancing the overall security of transactions handled on the server.
Q. What makes a server hosting solution the best choice for transaction security?
A dedicated hosting solution offers a robust and reliable platform for processing transactions securely, with features such as physical server isolation, dedicated resources, and customizable security configurations tailored to your business’s needs.