Key Takeaways
- A DDoS attack is an attempt to disrupt the regular traffic of the target by overwhelming it with excessive internet traffic.
- Prolonged network performance, unresponsive sites or services, and a sudden surge in traffic are signs of a DDoS attack.
- DDoS attacks can be categorized into volume-based (volumetric), application-layer, and protocol attacks.
- DDoS protection safeguards dedicated servers from disruptive attacks, ensuring uninterrupted service availability and maintaining network integrity.
- DDoS protection mechanisms such as traffic filtering, rate limiting, and network scrubbing are implemented to mitigate the impact of DDoS attacks on dedicated hosted servers.
- DDoS attack tools include LOIC, HOIC, Slowloris, etc.
Did you know that the US, UK, and China are among the top countries where businesses face an increasing threat of DDoS attacks? Cybercrime has become a major issue in the digital age.
Thankfully, server hosting is a major defense against this battle, offering protection against these malicious onslaughts. The role of DDoS protection in dedicated hosted server environments has become crucial as businesses increasingly depend on web-based services.
This blog will discuss the importance of DDoS protection in maintaining the integrity and performance of dedicated servers. It will also explain why DDoS attack protection in Dedicated Server hosting is necessary.
Let’s begin!
Table of Contents
- Key Takeaways
- DDoS Attack Meaning
- How to Identify a DDoS Attack?
- Types of DDoS Attacks
- The Role of DDoS Protection in Dedicated Hosting
- Implementing DDoS Mitigation in Dedicated Server Hosting
- Step 1: Assess Your Risk and Vulnerabilities
- Step 2: Choose the Right DDoS Protection Solution
- Step 3: Implement Network Security Measures
- Step 4: Establish a Baseline of Normal Traffic Patterns
- Step 5: Create a Response Plan
- Step 6: Deploy DDoS Protection Tools and Services
- Step 7: Continuously Monitor and Update Your Security Measures
- Step 8: Train Your Staff
- What are Commonly Used DoS/DDoS Attack Tools?
- Latest Trends in DDoS Attacks
- Questions to Ask When Choosing a DDoS Prevention Provider for Dedicated Servers
- Conclusion
- FAQs
DDoS Attack Meaning
Credits: FreePik
Before discussing DDoS mitigation’s role in dedicated hosting environments, you must learn what a DDoS attack is.
A DDoS attack stands for Distributed Denial-of-Service attack. It can be described as a cyber-attack in which DDoS attackers target a server, site, or network and send extensive DDoS traffic to overwhelm its bandwidth and resources.
This flood of traffic prevents legitimate users from accessing the service or resource by exhausting the target’s capacity to handle incoming requests. The attack involves numerous compromised computer systems, often infected with malware, which are used as a network to carry out the assault. These factors make it distributed and more challenging to mitigate.
Do you want to learn about expert tips on DDoS preventon? Read our informative blog, ‘How To Prevent DDoS Attacks: 8 Best Practices.’
How to Identify a DDoS Attack?
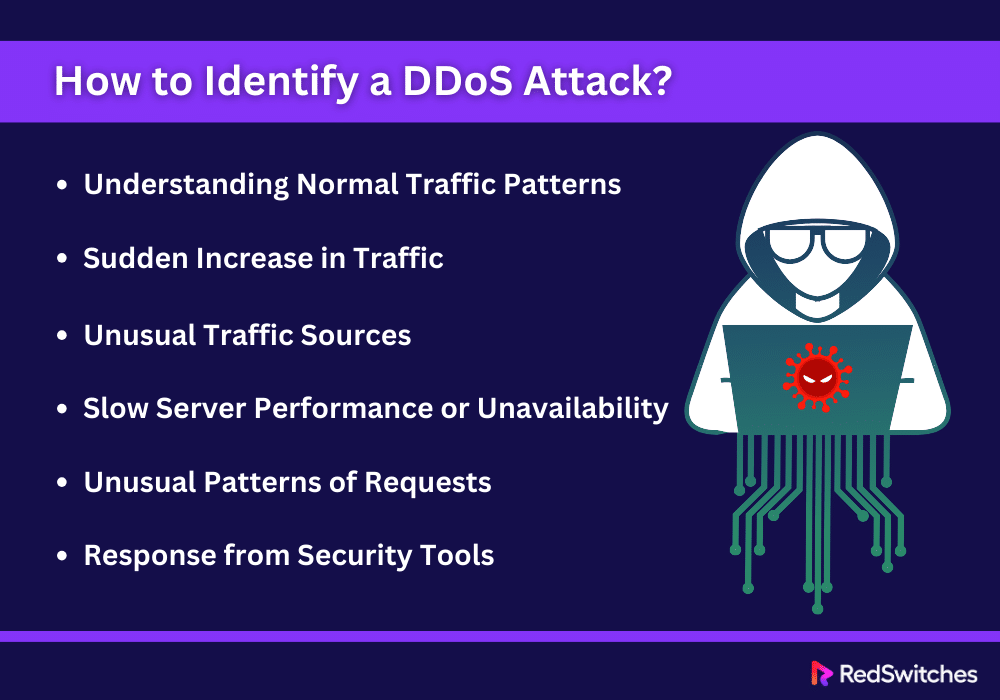
Early detection of DDoS attacks can dictate how much damage you face. In a dedicated private server hosting environment, recognizing the signs of a DDoS attack involves monitoring unusual activity and understanding the standard performance metrics of your server. Here’s how you can identify a DDoS attack on your dedicated hosted server:
Understanding Normal Traffic Patterns
A key requirement for efficiently identifying a DDoS attack is to know what normal traffic looks like for your server. This involves understanding regular traffic volume, peak periods, and the usual geographical distribution of your visitors. Establishing a baseline for normal traffic behavior helps spot abnormalities that may suggest a potential DDoS attack.
Sudden Increase in Traffic
One of the clearest indicators of a DDoS attack is a rapid and unaccounted-for surge in traffic. Suppose your dedicated server typically accommodates 1,000 visitors daily, but unexpectedly, this number jumps to 10,000 without any logical explanation, such as special promotions or events. In that case, it’s a strong sign that your server might be experiencing a DDoS attack.
Using monitoring tools to track these unusual spikes in traffic is crucial, as they can facilitate immediate evaluation and prompt action to mitigate the potential threat.
Unusual Traffic Sources
DDoS attacks often originate from many IP addresses across several geographical locations. If you notice an increase in traffic from regions that do not usually visit your site or if many requests from IP addresses have never accessed your server, this could be a sign of a DDoS attack.
Slow Server Performance or Unavailability
If your dedicated hosted server suddenly becomes unresponsive or slow for no reason like scheduled maintenance or expected traffic surges, it may be experiencing a DDoS attack. This performance issue occurs because the server resources are overwhelmed by malicious traffic.
Unusual Patterns of Requests
DDoS attacks can also be identified by examining the patterns of requests made to your server. An attack may involve repetitive requests to the same endpoint or page within short intervals, which is not characteristic of normal user behavior. Tools that analyze the rate and type of requests can help detect these patterns.
Response from Security Tools
Modern dedicated server hosting environments often include security tools and monitoring systems that can detect potential DDoS activities. These tools can provide alerts based on predefined thresholds of traffic behavior, unusual request patterns, or other indicators of a DDoS attack.
Types of DDoS Attacks
Credits: FreePik
One must understand the different DDoS attacks before implementing security measures. Here are the three primary categories of DDoS attacks:
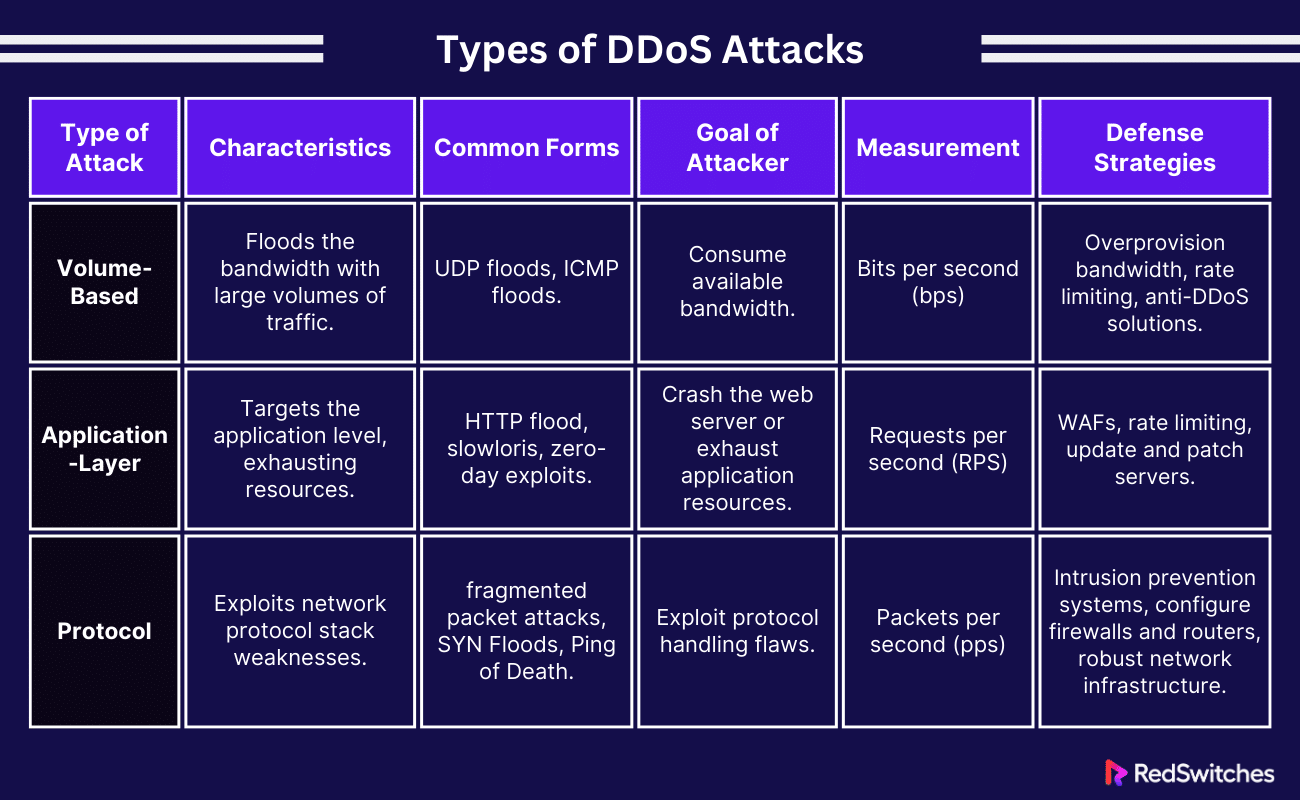
Volume-Based or Volumetric Attacks
If you’re facing a DDoS attack, it is likely a Volume-based attack. This is because these are the most common DDoS. They aim to saturate the bandwidth of the targeted site or network. Attackers generate large volumes of traffic to flood the system, blocking real traffic from accessing the site or service.
Characteristics
- Measured in bits per second (bps).
- Includes ICMP floods, UDP floods, and other spoofed-packet floods.
- The attacker’s goal is to consume the bandwidth available to the target network.
Defense Strategies
- Overprovision bandwidth to absorb the influx of traffic.
- Use rate limiting to control incoming traffic.
- Employ anti-DDoS solutions that can detect and mitigate large traffic spikes.
Application-Layer Attacks
Application-layer attacks impact the layer where web pages are generated on the server and provided in response to HTTP requests. These attacks are more sophisticated and aim to exhaust resources at the application level.
Characteristics
- Measured in requests per second (RPS).
- Includes attacks like HTTP flood, slowloris, and zero-day exploits.
- The attacker aims to crash the web server or exhaust application resources.
Defense Strategies
- Implement web application firewalls (WAFs) to inspect and filter HTTP traffic.
- Use rate limiting for incoming application requests.
- Regularly update and patch servers and applications to mitigate zero-day vulnerabilities.
Protocol Attacks
Protocol attacks exploit weaknesses in the network protocol stack to disrupt service. These attacks consume actual server resources or those of intermediate communication equipment, like load balancers and firewalls.
Characteristics
- Includes SYN floods, fragmented packet attacks, and Ping of Death.
- The attacker aims to exploit protocol handling flaws to create processing overhead.
- Measured in packets per second (pps).
Defense Strategies
- Employ advanced intrusion prevention and threat management systems that can identify and mitigate protocol anomalies.
- Configure firewalls and routers to rate-limit connections and filter malicious packets.
- Implement robust network infrastructure with redundancy to handle unexpected traffic loads.
Want to learn exactly what to do in case of a DDoS attack? Read our blog, ‘Emergency Procedures To Responding To DDoS Attacks.’
The Role of DDoS Protection in Dedicated Hosting
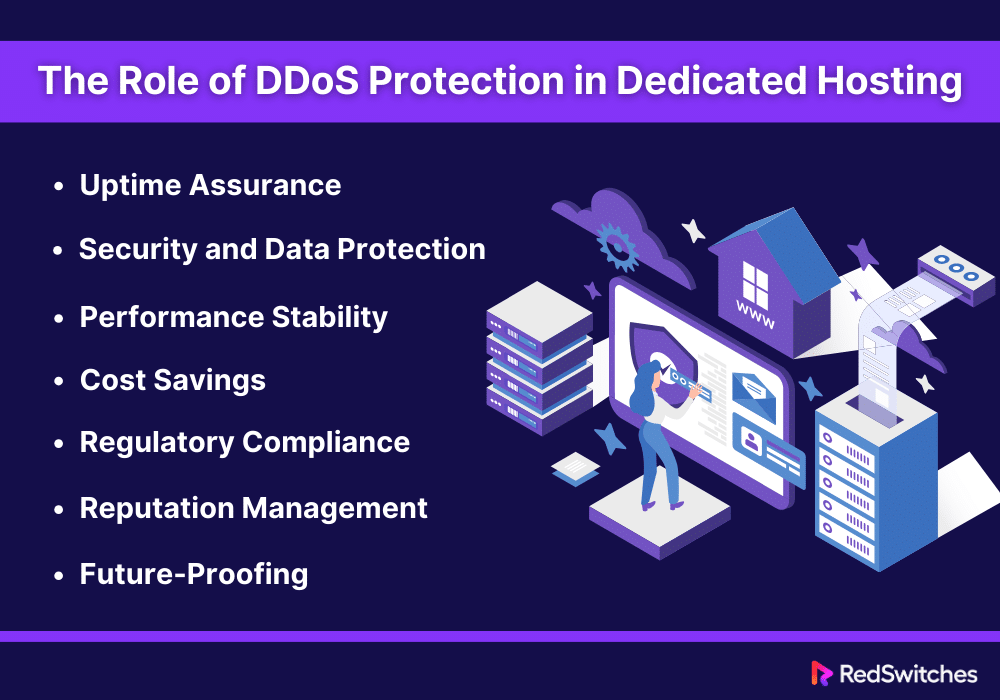
Dedicated hosting, with its benefits, becomes vulnerable if it lacks robust DDoS protection. Here are a few reasons for explaining the important role of DDoS protection in dedicated server hosting environments:
Uptime Assurance
DDoS protection in dedicated hosting offers uptime assurance. A DDoS attack aims to make online services unavailable by overpowering them with traffic.
Effective DDoS protection can mitigate these attacks. It ensures the server remains open and operational for legitimate users. This is important for businesses where downtime directly translates to lost revenue and damaged reputation.
Security and Data Protection
DDoS attacks can be a smokescreen for dangerous activities like data breaches or malware infections. By securing a dedicated hosted server against DDoS attacks, businesses protect their sensitive data from unauthorized access or theft. DDoS protection helps preserve the integrity and confidentiality of data stored on the server.
Performance Stability
Consistent performance is an aim for any business operating online. Unfortunately, DDoS attacks can bring severe performance issues. Even when not completely successful, DDoS attacks can still strain server resources, causing performance issues.
DDoS protection ensures that resources are reserved for real traffic. It also maintains the performance stability of the dedicated private server, which is a must-have for a consistent user experience and operational efficiency.
Cost Savings
The aftermath of a DDoS attack can be financially taxing. The costs associated with downtime, recovery, and potential ransom demands can be substantial. Investing in DDoS protection for dedicated hosting is a proactive measure that can help avoid these expenses, offering long-term cost savings compared to the potential financial impact of an attack.
Regulatory Compliance
Many industries have regulatory requirements that mandate certain levels of cybersecurity, including protection against DDoS attacks. By implementing DDoS protection, businesses can ensure compliance with these regulations, avoid fines and legal consequences, and protect customer data.
Reputation Management
The reputation of a business is closely tied to its online presence and reliability. Frequent downtimes or security breaches due to DDoS attacks can tarnish a company’s image. DDoS protection helps maintain the trust and confidence of customers and partners by demonstrating a commitment to cybersecurity.
Future-Proofing
Attackers are constantly working on making DDoS attacks more sophisticated and challenging to detect. DDoS protection allows businesses to adjust to these changes. It offers a future-proof solution that can evolve with the changing threats. This ensures that dedicated hosting environments remain secure against new DDoS attacks.
Now that we have discussed exactly how important DDoS protection is for dedicated hosting let’s go over its implementation steps.
Implementing DDoS Mitigation in Dedicated Server Hosting
Credits: FreePik
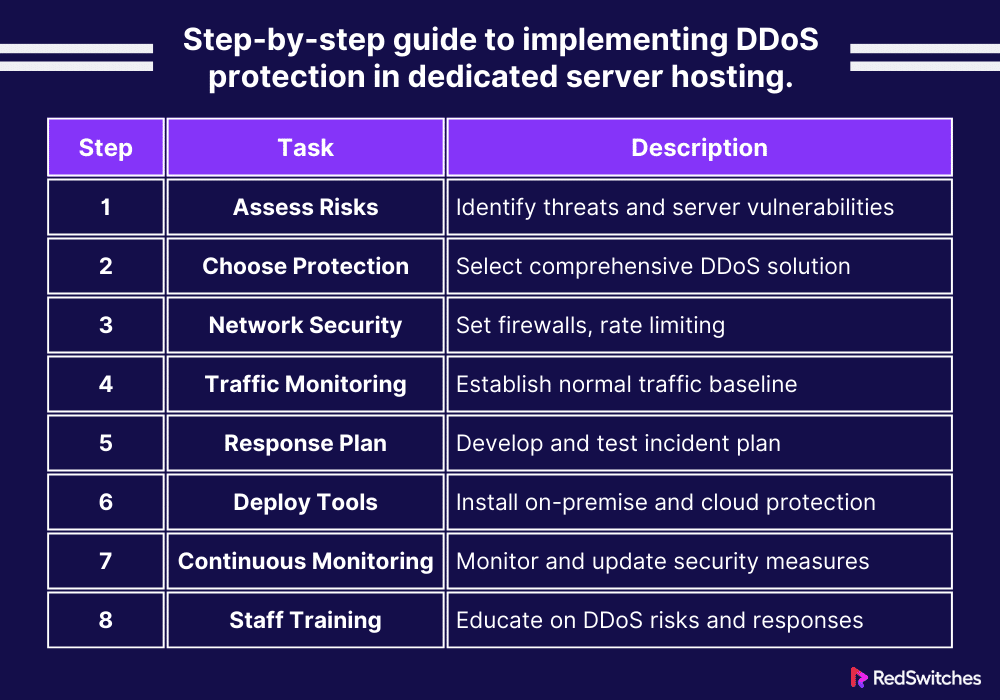
Here’s a step-by-step guide to implementing DDoS protection in dedicated private server hosting.
Step 1: Assess Your Risk and Vulnerabilities
Before you implement DDoS protection, you must take the time to understand your server’s potential risks and threats. Determine which assets are most critical and could be targets for DDoS attacks. It is also advisable to perform regular security audits to identify any vulnerabilities in your server’s infrastructure that could be exploited in a DDoS attack.
Step 2: Choose the Right DDoS Protection Solution
Different solutions have different offerings. Your goal is to look for solutions that offer comprehensive protection against various DDoS attack types, including volumetric, protocol, and application layer attacks. Ensure the solution you choose can scale to handle large-scale attacks. It should match the capacity of your dedicated server’s bandwidth.
Step 3: Implement Network Security Measures
The third step involves setting up firewalls and routers to reject DDoS-related traffic and limit an attack’s impact. It is also important to Implement rate limiting. Rate limiting controls a user’s requests to a server in a given timeframe. This helps prevent overuse and protects against DDoS attacks.
Step 4: Establish a Baseline of Normal Traffic Patterns
Continuously monitor network traffic using network traffic monitoring tools to establish a baseline for your server’s normal traffic. You can also use monitoring tools to receive alerts for unusual traffic spikes or patterns that could signal a DDoS attack.
Step 5: Create a Response Plan
This is one of the most important steps of DDoS implementation. It involves outlining the steps to take when a DDoS attack is detected. This includes who to contact, how to mitigate the attack, and how to communicate with stakeholders. Experts advise conducting regular drills to test your response plan. This helps ensure your team is prepared to act quickly in an attack.
Step 6: Deploy DDoS Protection Tools and Services
Now, install DDoS protection appliances on your network to mitigate DDoS attacks before they reach your server. Consider using cloud-based DDoS protection services that can absorb large-scale attacks and distribute the traffic across a global network of servers.
Step 7: Continuously Monitor and Update Your Security Measures
Continuous Monitoring is the key. Monitor your network and server performance constantly to find and respond to DDoS attacks promptly. You must also update your security systems, software, and protocols to protect against new and evolving DDoS attack methods.
Step 8: Train Your Staff
The last step involves training your IT staff and employees on DDoS risks and following security best practices. As part of your incident response plan, ensure your team knows what to do in case of a DDoS attack.
Wondering how websites get hacked? Read our blog, ‘How Do Websites Get Hacked – 11 Security Challenges,’ for answer.
What are Commonly Used DoS/DDoS Attack Tools?
Credits: FreePik
Understanding the tools commonly used in these attacks can help organizations better prepare and protect their digital assets. Here are some of the most widely used DDoS attack tools.
LOIC (Low Orbit Ion Cannon)
LOIC is among the most popular DoS attacking tools. It enables users to flood a server with UDP, TCP, or HTTP requests to overwhelm the target and cause a denial of service. Its ease of use has made LOIC a favorite tool among hackers, even those with limited technical knowledge.
Prevention: A well-configured firewall with connection rate limiting can block basic LOIC attacks. DDoS protection services can also further shield your server from large-scale assaults.
HOIC (High Orbit Ion Cannon)
HOIC is an upgraded version of LOIC and can launch a more powerful attack. It allows attackers to target up to 256 websites simultaneously, increasing the scope and impact of DDoS attacks. HOIC’s use of HTTP flood makes the traffic difficult to differentiate from legitimate traffic, complicating mitigation efforts.
Prevention: HOIC can look like legitimate traffic. Advanced intrusion detection systems (IDS) and intrusion prevention systems (IPS) can help spot and prevent these attacks. Behavioral analysis tools are also helpful in distinguishing between normal and malicious traffic patterns.
Slowloris
Slowloris is a highly effective tool for executing DoS attacks. It works by opening numerous connections to the target server and keeping them open as long as possible, using minimal bandwidth. Slowloris can take down a web server by exhausting its connection pool without needing a high rate of traffic.
Prevention: Configuring server settings to limit the simultaneous connections or the time each connection can remain open can mitigate Slowloris attacks. Load balancers and reverse proxies can also help evenly allocate the traffic.
UDP Flood
A UDP flood attack uses the User Datagram Protocol (UDP) to flood a target with packets, overwhelming the target and causing denial of service. Attackers often use this method because it does not require completing a handshake protocol, making it easier to anonymize the source of the attack.
Prevention: Anti-flood measures like rate limiting on a network’s perimeter can help mitigate UDP flood attacks. Firewalls and routers configured to block UDP traffic based on unusual patterns or volumes can also help.
SYN Flood
SYN flood attacks involve the attacker sending a rapid succession of SYN requests to a target’s server in an attempt to overwhelm it and deplete its resources. This type of attack exploits the TCP handshake process, leaving connections half-open and exhausting server resources.
Prevention: Enabling SYN cookies helps servers handle requests more efficiently. This way, they only complete connections when legitimate responses are returned. Firewalls that spot and filter out malicious SYN packets are also effective.
Botnets
Botnets, networks of compromised computers controlled by an attacker, are often used to conduct massive DDoS attacks. These networks can generate significant amounts of traffic, overwhelming targets with the sheer volume of data. Notable botnets include Mirai and Zeus, which have been responsible for some of the most notable DDoS attacks in history.
Prevention: Keeping systems up-to-date and secure is crucial to prevent them from becoming part of a botnet. Network segmentation, endpoint protection, and anti-malware solutions can also help.
NTP Amplification
NTP Amplification is a reflection-based volumetric DDoS attack that exploits public Network Time Protocol (NTP). It overwhelms a targeted server with UDP traffic. This method amplifies the attacker’s bandwidth, making the attack more potent without requiring extensive resources from the attacker’s side.
Prevention: Configuring NTP servers to bypass external queries or to answer only to known clients can stop them from being used in amplification attacks. Filtering and rate limiting can also help effectively manage NTP responses and prevent attacks.
Every business must know the cybercrime security challenges to implement mitigation strategies. Read our piece, ‘15 Top Cyber Security Challenges Businesses Must Know,’ to prepare yourself.
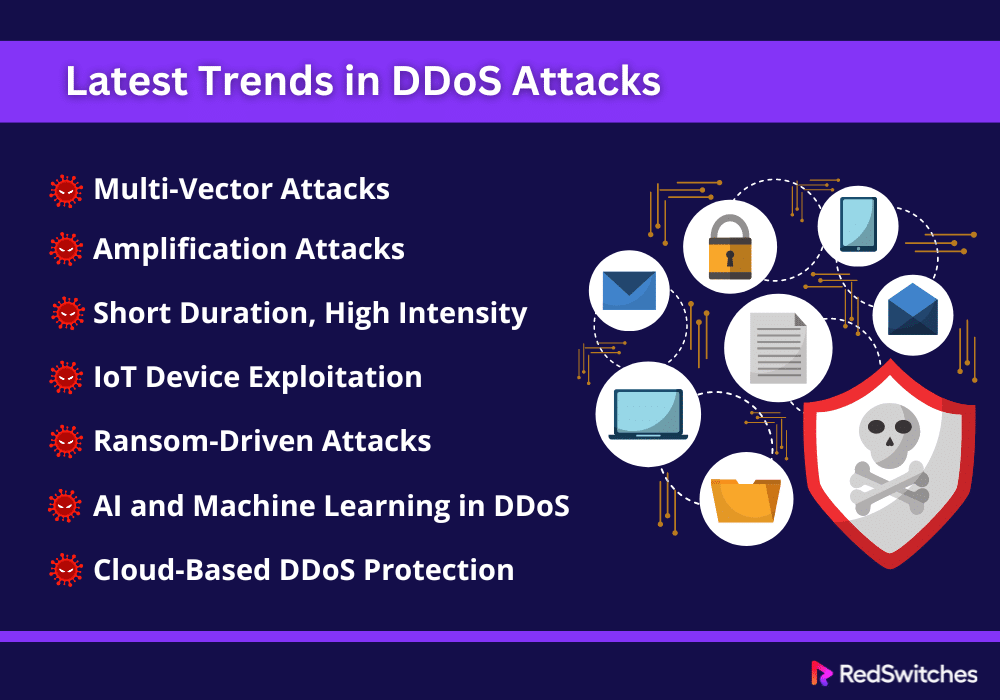
Latest Trends in DDoS Attacks
As discussed above, DDoS attacks are rapidly evolving. Keeping this in mind, we have compiled a list of the latest trends in DDoS attacks. Understanding these trends highlights what organizations must watch out for to protect their digital assets.
Multi-Vector Attacks
One of the most notable trends is the rise of multi-vector DDoS attacks. Attackers no longer rely on a single method to disrupt services but combine several attack vectors to increase complexity and effectiveness. This approach makes it harder for defense mechanisms to detect and mitigate the attacks, as they must contend with simultaneous threats on different fronts.
Amplification Attacks
Amplification attacks have gained traction, exploiting the bandwidth of compromised systems to magnify the attack’s impact. Techniques like DNS amplification or NTP amplification allow attackers to send small queries to a server, which then responds with much larger replies, thus exhausting the target’s resources more efficiently.
Short Duration, High Intensity
The trend towards shorter, more intense attacks is becoming more prevalent. These hit-and-run” style attacks can cause considerable disruption while going undetected under traditional detection systems, which are often configured to spot prolonged attack patterns.
IoT Device Exploitation
The popularity of Internet of Things (IoT) devices has opened new avenues for attackers. Now poorly secured devices are becoming prime targets for botnet recruitment. These botnets are then used to launch massive DDoS attacks, using the collective bandwidth of thousands of compromised devices.
Ransom-Driven Attacks
Ransom-based DDoS attacks are on the rise. There have been an increasing number of cases of attackers threatening or launching DDoS attacks against organizations. The key motive behind these is to secure a payment to cease the attack. This extortion tactic pressures businesses to work on their defenses or risk facing repeated attacks.
AI and Machine Learning in DDoS
Credits: FreePik
Both attackers and defenders increasingly use artificial intelligence (AI) and machine learning (ML) in their strategies. Attackers use AI to automate attack processes and identify new vulnerabilities. Defenders employ ML algorithms to predict and mitigate attacks more effectively.
Cloud-Based DDoS Protection
Cloud-based DDoS protection services are becoming more common as DDoS attacks grow in complexity and volume. These services offer scalable, on-demand resources to absorb and mitigate large-scale DDoS attacks. They provide a robust defense mechanism for businesses of all sizes.
Have you been experiencing excessive server downtime lately? For advice on prevention, read our blog, ‘Server Downtime: Causes, Effects, And How To Prevent It. ‘
Questions to Ask When Choosing a DDoS Prevention Provider for Dedicated Servers
Credits: FreePik
When selecting a DDoS prevention provider for dedicated private servers, asking the right questions is crucial to ensure you choose a service that meets your security needs. Here are some important questions to consider:
- What types of DDoS attacks can you protect against?
Understand the range of attacks the provider can defend against, including volumetric, protocol, and application layer attacks.
- How do you detect and respond to DDoS attacks?
Inquire about the detection methods and the response time once an attack is identified.
- What is the scale of protection you offer?
Determine the maximum attack size they can mitigate and whether it matches your bandwidth requirements.
- Is your DDoS protection always on, or is it activated on demand?
Inquire if the protection is continuously active or needs to be manually enabled during an attack, affecting response time.
- How do you handle false positives and legitimate traffic during an attack?
Understand their process for distinguishing between legitimate traffic and attack traffic to minimize potential disruptions to your service.
- Can you provide case studies or references from current clients?
Request examples of previous incidents where they successfully mitigated DDoS attacks to gauge their experience and effectiveness.
- What are your service level agreements (SLAs) regarding DDoS attack mitigation?
Look at the guarantees they offer in terms of uptime, attack mitigation, and response times.
- What reporting and alerting mechanisms are in place?
Ensure they provide detailed reports and real-time alerts during and after DDoS attack incidents.
- Is there a limit to how many attacks you can mitigate each month?
Check if there are any caps on the attacks they will mitigate and what happens if this limit is exceeded.
- What is the cost of your DDoS protection service?
Discuss pricing models to understand the total cost, including additional charges for large-scale attacks or overages.
- How does your DDoS protection integrate with our existing security infrastructure?
Understand how their solution fits your security setup to ensure seamless protection and functionality.
- What is your policy on upgrading and updating your DDoS protection capabilities?
Inquire about how they keep their system current with evolving DDoS tactics and technologies.
Asking these questions will provide a comprehensive view of each DDoS prevention provider’s offerings, allowing you to make an informed decision that aligns with your dedicated server’s security requirements.
Conclusion
The increase in DDoS attacks calls for fortified protection in dedicated hosting. Implementing advanced security measures becomes critical for organizations leveraging dedicated server solutions.
This is where RedSwitches steps in as a bulwark against these cyber threats. Our dedicated hosted servers have advanced DDoS attack protection mechanisms to spot and prevent attacks before they can inflict damage.
By choosing RedSwitches, businesses secure a reliable and high-performance hosting environment and gain peace of mind, knowing their digital assets are well-protected. Explore how we can strengthen your online presence against evolving cyber threats and ensure that your business remains resilient in adversity.
Visit our website today to learn more.
FAQs
Q. What is a DDoS attack?
A DDoS or Distributed Denial of Service attack is a malicious attempt to disrupt normal traffic on a targeted service, network, or server by overwhelming it with a flood of attack traffic from several sources.
Q. What is the DDoS attack method?
DDoS attacks involve various methods, but the most common include:
- Volumetric attacks (flooding the target with excessive traffic).
- Protocol attacks (exploiting vulnerabilities in the server’s protocol).
- Application layer attacks (targeting specific aspects of an application or service to disable it).
Q. What can happen in a DDoS attack?
The website or network under a DDoS attack can experience severe slowdowns, become unresponsive, or crash altogether. If the attack is part of a multi-faceted cyber threat, this can lead to significant downtime. It can also cause revenue loss, damaged brand reputation, and data leaks.
Q. How does DDoS attack work?
In a DDoS attack, attackers exploit vulnerabilities to flood the target with traffic, making it inaccessible to legitimate users.
Q. How can I protect against DDoS attacks?
Organizations can implement DDoS protection solutions to mitigate DDoS attacks that help detect and filter out malicious traffic before it reaches the target.
Q. How do attackers mitigate a DDoS attack?
Attackers can mitigate a DDoS attack by deploying tools and techniques that generate and direct a large amount of malicious traffic towards the target.
Q. What is a source IP address in DDoS attacks?
A source IP address is a numerical label assigned to each device connected to a network that identifies the source of data packets in a DDoS attack.
Q. How can a business identify a DDoS attack?
Businesses can identify a DDoS attack by monitoring unusual traffic spikes, degraded network performance, and service unavailability.
Q. What are layer 7 DDoS attacks?
A Layer 7 attack, also known as an application-layer DDoS attack, is a sophisticated form of DDoS threat that targets the OSI model’s application layer. These attacks mimic legitimate user behavior, overwhelming web servers with malicious requests.
Q. What is the role of DDoS protection in dedicated server hosting?
DDoS protection in dedicated private server hosting safeguards your online presence by mitigating the impact of cyber-attacks. It ensures uninterrupted business operations and enhanced server security.
Q. How does DDoS protection benefit dedicated hosting clients?
DDoS protection offers dedicated hosting clients robust security, minimizing downtime and potential data loss from attacks. It also maintains the performance and reliability of its online services.