Key Takeaways
- Dedicated hosted servers boost security and control, which is key for businesses with sensitive data that need to follow rules like GDPR, HIPAA, or PCI-DSS.
- They provide better performance, dependability, and customizable security, ideal for busy websites or online stores.
- Following data protection laws helps avoid big fines and loss of trust.
- With dedicated hosted servers, companies can fully manage their hosting to meet specific rules through custom setups.
- Keeping servers updated and maintained is important to stay secure and compliant.
- Setting up strong backup and recovery plans on dedicated hosted servers ensures data is safe and meets regulations.
- Continuously watching and checking servers helps find and fix security risks, keeping in line with regulations.
- Teaching employees about security and compliance is crucial, showing the human side of protecting data.
- Choosing a hosting provider that understands compliance, like RedSwitches, means getting help meeting and keeping up with regulations.
- RedSwitches dedicated hosted servers are designed to offer specific security, regular checks, and setups that meet different industry rules, helping businesses stay compliant.
In today’s world, keeping information safe is more important than ever. When discussing sensitive data like health records or credit card details, the stakes are even higher. That’s where dedicated hosted servers come into play. They are like strong, private vaults for your digital data. Unlike shared hosting, where you share space with others, a dedicated server compliance is just for you. This setup makes meeting strict rules set by laws like HIPAA for health info and PCI-DSS for payment details easier.
The market for Server Hosting was estimated to be worth $14.26 billion in 2022. It is projected to expand at a compound annual growth rate (CAGR) of 18.9% during the forecast period.
This stat is crucial in an age where digital threats are growing daily. Our guide to private server compliance will help you understand these rules and why they matter. With simple steps and clear advice, we’ll show you how to make your server a safe place for your valuable data.
Table of Contents
- Key Takeaways
- Understanding Dedicated Hosted Servers
- Compliance and Data Protection: An Overview
- The Role of Dedicated Hosted Servers in Compliance
- Implementing Compliance on Dedicated Exclusive Servers
- The Role of Technology Solutions
- Ensuring Compliance with RedSwitches Dedicated Hosted Servers
- Conclusion
- FAQs
Understanding Dedicated Hosted Servers
Credits: Freepik
In web hosting, a dedicated server plays a vital role, especially for businesses. In this type of hosting, a single server is dedicated to a single client or organization. This means the entire server’s resources are for one user’s needs. Let’s dive deeper into what dedicated private servers are and why they matter.
What is a Dedicated Server?
A dedicated private server is a powerful computer that hosts websites, applications, or services for a single client. Unlike shared hosting, where multiple clients share resources, a server offers one user all its power and storage. This setup provides more control, security, and performance.
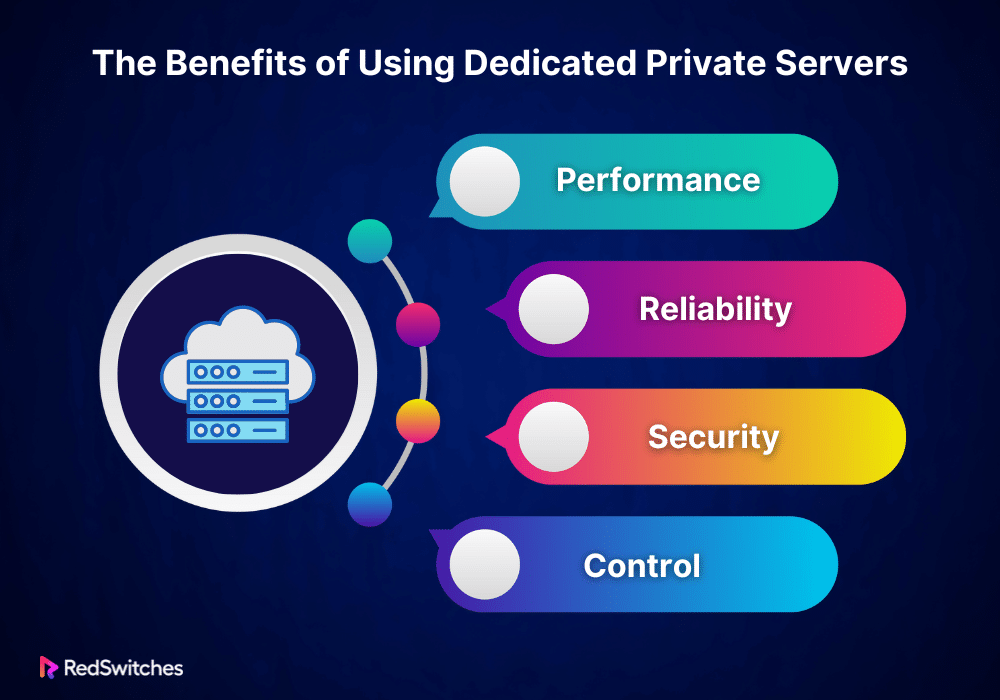
The Benefits of Using Dedicated Private Servers
Servers come with several advantages. Here are the main ones:
Performance
With all resources dedicated to one user, websites and applications run smoothly. There’s no need to worry about other users clogging up the server’s bandwidth or processing power.
Reliability
Dedicated private servers are known for their reliability. Since you’re the only one using the server, the risk of downtime is much lower. You can also expect more consistent performance.
Security
Security is a top priority for businesses. A server offers a secure environment because you’re not sharing space with potential spammers or malicious websites. You can implement custom security measures tailored to your needs.
Control
Having a server means having full control over your hosting environment. You can choose the operating system, and software, and configure settings. This level of control is crucial for businesses with specific requirements.
Also Read: The Beginner’s Checklist for Choosing a Dedicated Server Provider
Who Needs a Dedicated Private Server?
Not every website or business needs a server. But for those who require high levels of performance, security, and control, it’s an ideal choice. Large e-commerce sites, high-traffic businesses, and organizations handling sensitive data often benefit from dedicated hosting.
Understanding dedicated hosted servers is crucial for businesses looking to improve their web hosting experience. These servers offer unmatched performance, reliability, security, and control. While they may not be necessary for every website, they are a game-changer for those with significant needs. Investing in a server means investing in your business’s online presence and security.
Also Read: Unveiling the Hidden Risks of Dedicated Servers
Compliance and Data Protection: An Overview
Data protection is more important than ever. Businesses of all sizes must navigate a maze of regulations to keep sensitive information safe. Understanding the key regulatory frameworks is the first step. Failing to comply can have serious consequences. Let’s break down what you need to know.
Key Regulatory Frameworks
Several regulatory frameworks set the standards for data protection. Each has its specific focus, but all aim to ensure businesses handle data responsibly.
General Data Protection Regulation (GDPR)
The GDPR is a comprehensive data protection law that affects businesses within and dealing with the European Union. It focuses on giving individuals control over their data. Under GDPR, businesses must ensure the privacy and protection of EU citizens’ data, no matter where the company is based. This regulation emphasizes consent, data rights, and strict handling and processing of personal data.
Health Insurance Portability and Accountability Act (HIPAA)
HIPAA is a law for the US healthcare sector. It keeps patient health information safe. Only the patient can agree to share their information. Doctors, insurance companies, and businesses must follow HIPAA to protect this information.
Payment Card Industry Data Security Standard (PCI DSS)
PCI DSS is for any group that uses credit card details. It aims to keep credit and debit card details safe. It stops people from misusing personal information. To follow PCI DSS, businesses need to have a secure network. They must keep card details safe, handle risks well, and control who can access information.
Consequences of Non-Compliance
Ignoring these regulations can lead to severe penalties. The consequences of non-compliance include:
Financial Penalties
Credits: Freepik
Businesses can face hefty fines for failing to comply with data protection regulations. For example, GDPR violations can result in fines of up to 4% of annual global turnover or €20 million, whichever is higher. HIPAA fines can reach up to $1.5 million per violation category annually. PCI DSS non-compliance can lead to monthly fines ranging from $5,000 to $100,000.
Legal Repercussions
Beyond fines, non-compliance can lead to legal action. Affected individuals or entities may sue businesses for breaches that compromise their data. This can result in long, costly legal battles and further financial damages.
Loss of Trust
One of the most damaging consequences of non-compliance is the loss of customer trust. Customers who learn that a business failed to protect their data are less likely to continue using its services. Rebuilding this trust can be difficult and expensive.
Business Disruption
Compliance investigations and legal actions can disrupt business operations. They can divert resources from regular activities, leading to a loss of productivity and revenue. In severe cases, businesses might be forced to cease operations temporarily or permanently.
Understanding and adhering to data protection regulations is crucial for businesses. Compliance is not just about avoiding fines but protecting customers’ data and maintaining their trust. Investing time and resources into compliance is an investment in your business’s future and reputation.
The Role of Dedicated Hosted Servers in Compliance
In today’s digital age, protecting sensitive data is more crucial than ever. Businesses face a complex web of data protection laws and compliance standards. Meeting these requirements is a matter of ethical responsibility and a legal necessity. Dedicated hosted servers play a pivotal role in helping organizations achieve and maintain compliance. Let’s explore how.
Compliance involves adhering to laws and regulations related to data protection and privacy. These standards ensure that businesses handle customer and client information responsibly and securely. The consequences of non-compliance can be severe, including hefty fines and damage to reputation.
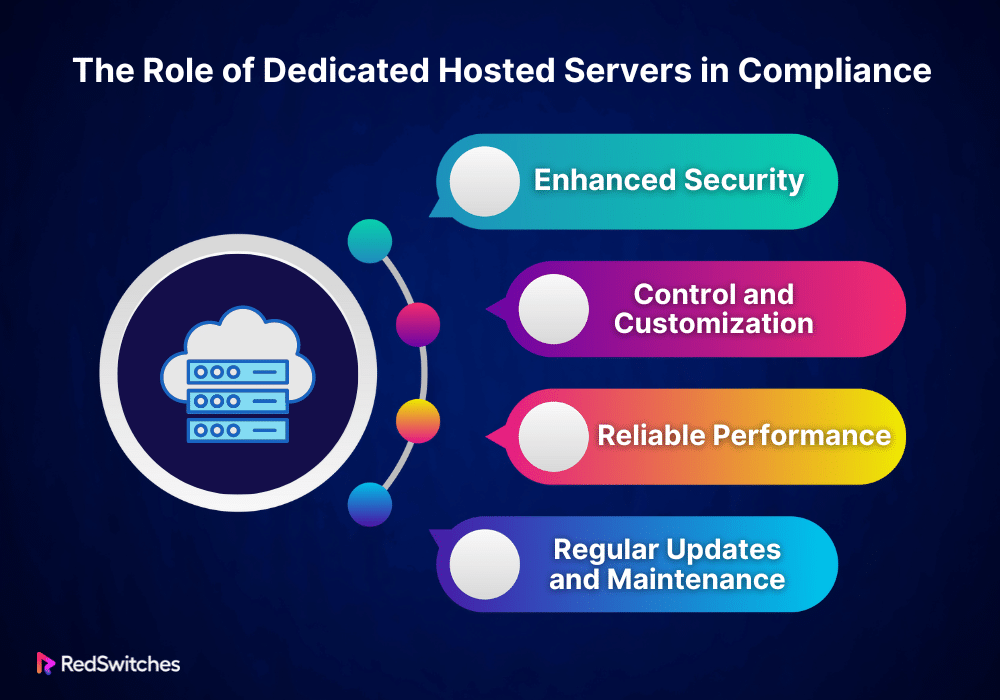
Dedicated Hosted Servers: A Compliance Ally
Dedicated hosted servers offer unique features that make them ideal for businesses meeting strict compliance standards. Here’s how they help:
Enhanced Security
Credits: Freepik
Security is at the heart of compliance. Servers provide a secure environment for sensitive data. Since the server is dedicated to a single client, the risk of unauthorized access is significantly lower than in shared hosting environments. Businesses can implement custom security measures tailored to specific compliance requirements, such as firewalls, encryption, and intrusion detection systems.
Control and Customization
Compliance often requires impossible configurations and settings in a shared hosting environment. With a server, organizations have full control over the server setup. This flexibility allows them to configure the server in a way that meets compliance standards, from the operating system and software to data storage practices.
Reliable Performance
Compliance is not just about securing data; it’s also about ensuring data is accessible when needed. Dedicated hosted servers offer reliable performance, vital for maintaining access to critical data. High uptime rates are essential for businesses that must ensure data availability as part of their compliance requirements.
Regular Updates and Maintenance
Keeping software and systems updated is crucial for compliance. Dedicated exclusive servers make it easier for businesses to implement regular updates and maintenance routines. This ensures that security vulnerabilities are addressed promptly, keeping the server compliant with the latest standards.
Also Read: Dedicated Server Security Features: A Comprehensive Guide
Who Benefits from Compliance-Focused Dedicated Hosting?
Any organization that handles sensitive information can benefit from dedicated exclusive servers for compliance. This includes healthcare organizations subject to HIPAA, e-commerce sites needing to adhere to PCI-DSS, and any business operating under GDPR. Dedicated exclusive servers offer a solid foundation for building a compliant IT infrastructure.
The role of servers in achieving and maintaining compliance cannot be overstated. Dedicated exclusive servers provide safety, control, dependability, and personalization. These features help meet strict data protection rules. For companies dealing with complicated rules, servers are a smart choice. They protect data and follow the law.
When you pick a server, you are actively protecting your business. This means keeping your customers’ information safe. It also protects your business’s good name and money.
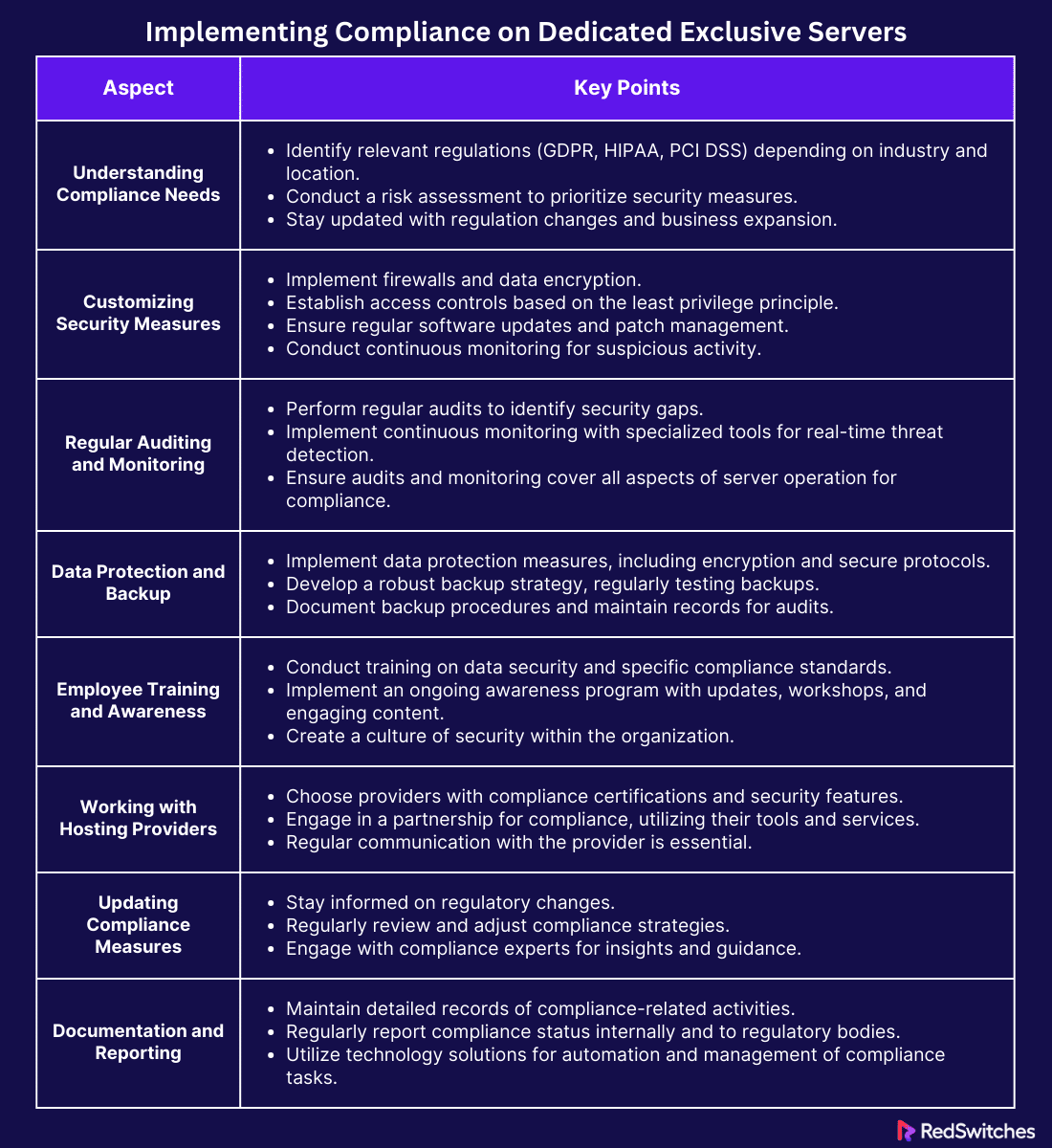
Implementing Compliance on Dedicated Exclusive Servers
Ensuring compliance on dedicated exclusive servers is crucial for businesses handling sensitive data. This process involves several key steps. First, understand the specific compliance standards your business must meet. Depending on your industry and location, these could include GDPR, HIPAA, or PCI DSS.
Assessing Compliance Needs
You must first understand your specific requirements to ensure your dedicated exclusive server meets all necessary compliance standards. Different industries and data types are subject to various regulations. The first step is identifying which laws and standards apply to your business. For example, if you handle customer data from the European Union, GDPR applies to you. If you process healthcare information in the United States, you must comply with HIPAA. And PCI DSS is a must if you deal with credit card information.
The next step is conducting a risk assessment after figuring out which regulations you must follow. This process involves identifying the data you need to protect and evaluating potential vulnerabilities. It’s about understanding where your data lives on your server and how it’s accessed and used. This assessment helps prioritize security measures and compliance efforts.
Understanding your compliance needs is an ongoing process. Regulations can change, and your business might expand into new areas with different requirements. Keeping up-to-date with these changes ensures your server remains compliant over time.
Customizing Security Measures
Credit: Freepik
Once you know your compliance needs, the next step is to customize your server’s security measures. The goal is to protect sensitive data according to the standards you’re required to meet. Here’s how to approach this customization:
Implementing Firewalls
Firewalls are your first line of defense. They control incoming and outgoing network traffic based on predetermined security rules. Setting up a firewall tailored to your compliance needs helps prevent unauthorized access to your server.
Data Encryption
Encrypting data is critical for protecting sensitive information. It ensures that even if data is intercepted, it remains unreadable without the correct decryption key. For compliance, you’ll need to encrypt data both in transit (as it moves across networks) and at rest (stored on your server).
Access Controls
Access controls define who can access what data and what they can do with it. This means setting up user permissions and roles according to the principle of least privilege. Each user should have the minimum access necessary to perform their job. This minimizes the risk of accidental or malicious data breaches.
Regular Updates and Patch Management
Software vulnerabilities are a significant risk. Hackers exploit these weaknesses to gain unauthorized access. Keeping your server’s operating system and applications up-to-date with the latest patches is essential. Regular updates close these vulnerabilities, helping to maintain compliance.
Continuous Monitoring
Monitoring your server’s activities helps detect potential security incidents early. This involves logging and analyzing access attempts, data usage, and system changes. Continuous monitoring enables you to respond quickly to any suspicious activity, minimizing the impact of a breach.
Customizing security measures for your server isn’t a one-time task. As technology evolves and threats change, you must update your security practices. Regularly reviewing and adjusting your security measures ensures ongoing compliance and protects your data against emerging threats.
Regular Auditing and Monitoring
Regular auditing and monitoring are critical for maintaining compliance on dedicated exclusive servers. These processes help ensure that security measures are effective and that data remains protected. Let’s break down why they’re essential and how to implement them.
The Importance of Regular Audits
Audits involve thoroughly examining your server’s security practices, policies, and procedures. They check if you’re following the compliance standards relevant to your business. Regular audits help identify gaps in your security measures before they become serious issues. They ensure that you’re not only compliant today but continue to be so as regulations evolve and your business grows.
Conducting an audit involves reviewing access logs, ensuring that data encryption practices are up to date, and verifying that data protection policies are being followed. It’s about ensuring that every aspect of your server’s operation aligns with compliance requirements.
Implementing Continuous Monitoring
Audits check if you’re following rules at a certain time. Continuous monitoring keeps an eye on rules all the time. It watches everything on your server to catch security risks or rule breaks.
You need to use special tools to monitor the system continuously. These tools track who accesses the system, any changes to files, and all network activity. If they find something odd, they tell you immediately, helping you quickly deal with any dangers. Continuous monitoring stops data theft and ensures your server always meets the rules.
Good monitoring and audits aren’t just about using technology. You also need to make clear rules for using data and train your team about these rules often. Doing this ensures your server is safe and follows the rules.
Data Protection and Backup Strategies
Credits: Freepik
Protecting the data stored on your server is paramount. Compliance regulations often require specific data protection and backup strategies to ensure data integrity and availability. Here’s how to approach this:
Implementing Data Protection Measures
Data protection involves more than just securing data from unauthorized access. It also means ensuring that data is accurate, complete, and available when needed. Implementing strong access controls, encrypting data, and using secure protocols for data transmission are all part of protecting data.
Additionally, it’s important to manage data effectively. This means knowing your data, where it’s stored, and who has access to it. Effective data management helps prevent data loss and ensures that sensitive information is only available to authorized users.
Developing a Robust Backup Strategy
Backup strategies are a critical component of data protection. They ensure you can recover data quickly during a data loss incident, whether due to technical failure, human error, or a cyberattack.
A robust backup strategy involves regularly backing up data and storing backup copies in a secure, off-site location. This protects against data loss from server failures or disasters affecting your primary location. Testing your backups regularly is also important to ensure they can be restored successfully.
For following rules, your backup plan needs to fit certain needs for keeping data and how fast you need to get it back. Writing down your backup steps and keeping track of all backup and restore actions is key. This shows you’re following rules during checks.
Regular checking, monitoring of your server and having good data protection and backup plans are crucial for adhering to rules on servers. These steps keep your data safe from danger, and your business can bounce back quickly if data gets lost.
Employee Training and Awareness
Employee training and awareness are crucial for maintaining compliance on dedicated exclusive servers. Every team member plays a role in protecting sensitive data and ensuring your business meets regulatory requirements. Let’s explore why training is important and how to implement an effective program.
The Importance of Employee Training
Even the most secure dedicated exclusive server can be compromised by human error. Employees might accidentally expose sensitive data or fall victim to phishing attacks. Training helps mitigate these risks by educating your team on the importance of data protection and the specific compliance standards your business must follow.
An effective training program covers the basics of data security, including password management, recognizing phishing emails, and safely handling customer data. It should also provide detailed instructions on employees’ procedures and policies to maintain compliance.
Implementing an Awareness Program
Awareness programs go beyond initial training sessions. They keep security and compliance at the forefront of your employees’ minds. Regular updates, newsletters, and workshops reinforce key concepts and inform staff about new threats and compliance changes.
Key components of an effective awareness program include:
- Regular training sessions that cover both basic security practices and specific compliance requirements.
- Updates on new security threats and reminders about safe online behavior.
- Clear communication about the role each employee plays in maintaining compliance.
- Engaging content, such as quizzes or games, to make learning about compliance more interactive.
Creating a culture of security within your organization is essential for compliance. When employees understand the importance of their actions and how they can prevent data breaches, they become active participants in your compliance efforts.
Working with Compliant Hosting Providers
Choosing the right hosting provider is critical for ensuring your dedicated private server remains compliant. A compliant hosting provider understands the specific requirements of the regulations your business must adhere to and offers the tools and services to help you meet those standards. Here’s how to select and work with a compliant hosting provider.
Selecting a Compliant Hosting Provider
When choosing a hosting provider, look for one with a strong track record of compliance. They should offer:
- Certifications that demonstrate adherence to relevant compliance standards.
- Security features that meet or exceed the requirements of the regulations you’re subject to.
- Experience working with businesses in your industry or with similar compliance needs.
Ask potential providers about their compliance policies and procedures. Ensure they can offer the level of support and security your business requires.
Collaborating for Compliance
Working with a compliant hosting provider is a partnership. While the provider offers the infrastructure and security measures, your business must still manage data and access controls effectively.
Communicate regularly with your provider to stay informed about changes in compliance requirements or security threats. Take advantage of their compliance tools or services, such as automated backups or security audits.
You can enhance your dedicated private server’s security and compliance by choosing the right provider and actively collaborating with them. This partnership allows you to leverage the provider’s expertise while controlling compliance efforts.
Updating Compliance Measures
Credits: Freepik
Compliance is not a one-time task. It evolves as regulations change and as your business grows. Staying updated with compliance measures is crucial for maintaining the integrity of your dedicated private server and the safety of sensitive data. Let’s look at how to keep your compliance measures up-to-date.
Keeping Abreast of Regulatory Changes
The first step is to stay informed about changes in compliance regulations. This involves monitoring updates from regulatory bodies and industry news. Joining relevant forums and attending webinars can also keep you in the loop. When you know of upcoming changes, you can plan adjustments to your compliance strategy.
Regular Review and Adjustment
Schedule regular reviews of your compliance measures. This could be quarterly or bi-annually, depending on your business needs. During these reviews, assess whether your current measures meet the latest regulatory requirements. It’s also a chance to evaluate the effectiveness of your compliance efforts. If you identify gaps or areas for improvement, adjust your measures accordingly.
Engaging with Compliance Experts
Sometimes, the best way to stay updated is to consult with experts. Compliance consultants or legal advisors specializing in your industry can provide valuable insights. They can help you navigate complex regulations and ensure your compliance measures are effective and up-to-date.
Documentation and Reporting
Documentation and reporting are vital components of a robust compliance program. They prove your commitment to compliance and can be critical during audits or investigations. Let’s dive into the importance of these practices and how to implement them effectively.
Maintaining Comprehensive Records
Keep detailed records of all your compliance-related activities. This includes audits, employee training sessions, security updates, and any data breaches or security threats incidents. Documentation should also cover the steps taken to address and resolve such incidents. This demonstrates your proactive approach to compliance and provides a roadmap for addressing future issues.
Reporting Compliance Status
Regular reporting on your compliance status is important internally and to relevant regulatory bodies when required. These reports should summarize your compliance efforts, highlight issues, and document resolutions. Internal reports keep stakeholders informed and engaged with your compliance journey. External reports may be necessary to meet regulatory requirements or to renew certifications.
Also read When to Upgrade to a Dedicated Server for Your Business
The Role of Technology Solutions
Credits: Freepik
Technology solutions can significantly ease the compliance burden. Automation and software tools are invaluable for managing the complex tasks associated with compliance. Let’s look at how technology can support your efforts.
Automating Compliance Tasks
Automation tools can handle repetitive tasks such as monitoring for security threats, managing access controls, and performing regular backups. This reduces the risk of human error and frees up your team to focus on more strategic compliance activities.
Compliance Management Software
There are software solutions designed specifically for compliance management. These tools can help you stay organized and ensure that nothing slips through the cracks. Features might include automated alerts for regulatory changes, task management for compliance activities, and templates for documentation and reporting.
Leveraging Cloud Services
Some cloud services offer built-in compliance features. They can automatically enforce certain compliance standards and provide secure data storage options. Cloud services can be a powerful ally in your compliance strategy when used correctly.
Ensuring Compliance with RedSwitches Dedicated Hosted Servers
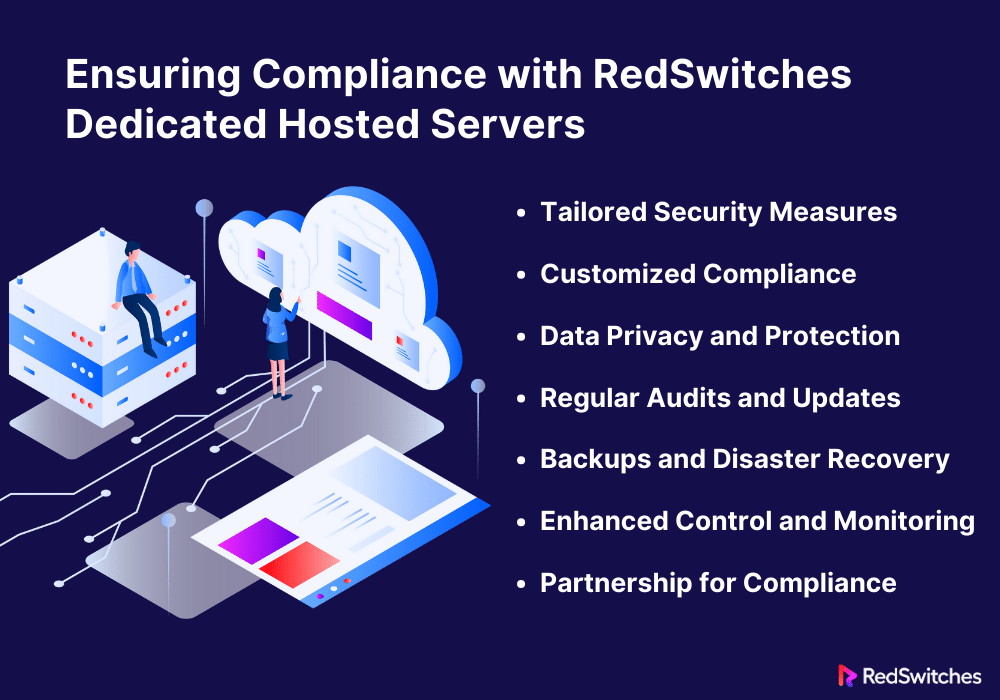
In today’s digital landscape, compliance is not just a checkbox. It’s a crucial element of business operations. This is where RedSwitches dedicated hosted servers shine. They offer robust compliance solutions tailored to meet various regulatory standards. Let’s break down how RedSwitches servers ensure compliance, making it simpler for businesses to protect data and adhere to regulations.
Tailored Security Measures
Security is the foundation of compliance. RedSwitches servers come equipped with advanced security features. These include firewalls, intrusion detection systems, and SSL encryption. Each of these plays a critical role in safeguarding data. Firewalls block unauthorized access. Intrusion detection systems monitor for suspicious activities. SSL encryption secures data transfers. Together, they create a secure environment that meets compliance standards.
Customized Compliance
No two businesses are the same. RedSwitches understands this. That’s why they offer customized solutions. Compliance requirements vary depending on your industry, whether it’s healthcare, finance, or e-commerce. RedSwitches works with you to tailor your server setup. This ensures it meets specific regulations like GDPR, HIPAA, or PCI-DSS. Customization means your dedicated private server aligns with your unique compliance needs.
Data Privacy and Protection
Credits: Freepik
Protecting sensitive information is at the heart of compliance. RedSwitches servers ensure data privacy through encrypted storage and secure access protocols. This means only authorized personnel can access sensitive data. Encryption ensures that, even if data is intercepted, it remains unreadable. This level of data protection helps businesses comply with strict privacy regulations.
Regular Audits and Updates
Compliance is not a set-and-forget task. Regulations evolve, and so do security threats. RedSwitches servers are regularly audited and updated to ensure ongoing compliance. These audits check for vulnerabilities and ensure all security measures are current. Regular updates patch these vulnerabilities, keeping your server secure and compliant.
Also Read Exploring Customization and Flexibility in Dedicated Server Hosting
Backups and Disaster Recovery
Data loss can have serious compliance implications. RedSwitches servers include comprehensive backup and disaster recovery solutions. Regular backups ensure data is not lost. In the event of a system failure, disaster recovery capabilities enable quick data restoration. This ensures business continuity and compliance, even in unexpected events.
Enhanced Control and Monitoring
With RedSwitches servers, you have full control over your hosting environment. This includes access controls, which limit who can see and edit data. Monitoring tools keep track of who accesses what data and when. This level of control and monitoring is essential for compliance. It ensures that data is handled securely and responsibly.
Partnership for Compliance
RedSwitches views compliance as a partnership. They offer support and guidance to ensure your server meets all necessary regulations. This support includes consulting on the best practices for data protection and compliance. With RedSwitches, you’re not just getting a server. You’re getting a partner committed to helping you achieve and maintain compliance.
Conclusion
In a world where data breaches can damage reputations and hefty fines for non-compliance are common, ensuring your data is secure and compliant is essential. RedSwitches servers offer a powerful solution. They provide the security, customization, and support your business needs to meet complex compliance requirements. With RedSwitches, you’re not just getting a service; you’re gaining a partner dedicated to your security and compliance success.
Don’t let the complexities of compliance slow down your business. Choose RedSwitches servers for peace of mind and focus on confidently growing your business. Visit RedSwitches today to learn more about how we can help secure your data and ensure you’re always compliant. Let us take care of the technicalities so you can concentrate on what you do best.
FAQs
Q. What is server compliance?
Server compliance means making sure a server follows certain rules and standards. These rules come from industry groups or the government. They cover data safety, privacy, server work, and setup. The goal is to keep the server running safely and securely, which meets legal and industry needs.
Q. What are the system requirements for a dedicated hosted server?
The need for a server changes based on what you’re using it for, like web hosting, gaming, or business apps. In general, you need:
- CPU: A strong processor with many cores to handle tasks well.
- RAM: Enough memory for your server’s apps and services. This usually starts at 8GB but may need to be much more for demanding apps.
- Storage: Plenty of space on hard drives (HDDs) or faster solid-state drives (SSDs) to keep your files and data.
- Network: A fast and reliable internet connection that can handle lots of data moving in and out.
- Operating System: A server-specific OS, such as Windows Server, Linux (like Ubuntu Server or CentOS), or another, depending on what the server needs to do.
Q. What are the risks of dedicated hosted servers?
- Security Vulnerabilities: Exposure to cyberattacks if not properly secured.
- Hardware Failure: Physical components can fail, leading to downtime.
- Cost: Generally more expensive than shared hosting due to the dedicated resources.
- Maintenance and Management: Requires technical expertise to manage and maintain the server software and hardware.
Q. What additional requirements are associated with a dedicated private server?
In addition to the basic system requirements, servers may have additional requirements, such as:
- Advanced Security Measures including firewalls, intrusion detection/prevention systems (IDS/IPS), and regular security auditing.
- Backup Solutions: Systems for data backup and recovery to prevent data loss.
- Monitoring Tools: Software to monitor server performance resource usage and detect potential issues in real-time.
- Technical Expertise: Skilled personnel to manage and troubleshoot the server.
Q. What is server compliance?
Server compliance refers to a server’s adherence to established rules, regulations, and standards to ensure data security, privacy, and integrity.
Q. How does dedicated private server hosting contribute to server compliance?
Dedicated private server hosting provides businesses with exclusive use of a physical server, offering enhanced security features and the ability to implement robust security measures to ensure compliance with regulations.
Q. What security measures can be implemented to enhance server compliance?
Implementing server security best practices, such as regular audits, server configuration hardening, encrypted communication, and access control mechanisms, is essential to ensuring compliance and protecting sensitive data.
Q. How does a dedicated hosted server provide better performance and security than shared hosting?
A dedicated hosted server offers exclusive server resources, server environment control, and dedicated IP address, resulting in enhanced security, performance, and compliance capabilities compared to shared hosting environments.
Q. What role does server compliance play in data center operations?
Ensuring security and compliance within a data center is critical to maintaining the integrity of stored data, protecting against breaches, and upholding regulatory standards governing server security.
Q. How can managed dedicated server solutions assist with server compliance?
Managed dedicated server providers offer expertise in server administration, management, and best practices, helping businesses secure and comply with industry regulations.
Q. What is a dedicated hosted server?
A dedicated hosted server is a type of hosting service in which an entire physical server is dedicated solely to one client. This means that the client has full control over the server, including the choice of server resources and server configuration.
Q. Why choose a dedicated hosted server over shared hosting?
A dedicated private server provides better performance and security than shared hosting as you are not sharing resources with other users. This is ideal for businesses with high traffic websites or sensitive data that require robust security measures.
Q. What security features are offered by dedicated servers?
Dedicated servers offer dedicated server security measures such as server security configurations, server environment isolation, and secure your dedicated server services to protect your data from unauthorized access.
Q. How does a dedicated hosted server ensure compliance?
A dedicated hosted server ensures security and compliance by providing a secure data center environment where compliance standards are met to safeguard sensitive data and adhere to industry regulations.
Q. What are the benefits of using a managed dedicated server?
A managed dedicated server offers server management services such as server administration, server hardware maintenance, and web server optimization to ensure the smooth operation of your hosting server.
Q. How can I secure my dedicated hosted server?
To secure your server, you can implement server security best practices, use robust security measures, and opt for managed server services that include server security monitoring and maintenance.