Key Takeaways
- Unlike shared hosting environments, dedicated servers offer enhanced control, security, and performance for a single client.
- Various dedicated hosted servers cater to different needs, including managed/unmanaged, Windows/Linux, high-performance, GPU, and storage servers.
- Securing a dedicated hosted server involves limiting access, changing default service ports, removing unused software, employing DDoS mitigation, and updating software.
- Regular software updates and patches protect the server from new vulnerabilities and cyber threats.
- Customizable security settings allow businesses to tailor their server’s protection to fit specific needs and threats.
- Physical security at data centers protects servers from unauthorized access and natural disasters, enhancing overall security.
- Isolation from ‘bad neighbors’ on a dedicated hosted server eliminates risks associated with shared resources and compromised sites on shared servers.
- Compliance with legal and industry-specific security standards is more manageable on dedicated hosted servers due to customizable security and data sovereignty.
- Redswitches dedicated hosted servers provide top-tier security solutions, including advanced network protection, regular software updates, and customizable security settings.
- Reliable customer support from providers like Redswitches ensures quick and effective responses to security concerns, offering businesses peace of mind.
In today’s world, where cyber threats loom large, ensuring the security of dedicated hosted servers is crucial. This article aims to provide an in-depth look at how to safeguard these powerful online assets. With the rise of digital data breaches, no one can overlook server security.
A report by Cybersecurity Ventures predicted that Cybercrime will cost The World $10.5 Trillion Annually By 2025. This figure underscores the pressing need for robust security measures. Dedicated hosted servers, known for their reliability and high performance, are a prime target for hackers.
This guide will explore the essential security features that can protect your server from unauthorized access, data theft, and other cyber threats. From basic setups to advanced protection strategies, we aim to equip you with the knowledge to keep your dedicated hosted server safe and secure.
Join us as we dive into the dedicated hosted server security world, making it accessible and understandable for all.
Table of Contents
- Key Takeaways
- What Are Dedicated Servers?
- How Do You Secure a Dedicated Hosted Server?
- How Dedicated Servers Improve Security
- Top-Tier Security Solutions with Redswitches Dedicated Private Servers
- Conclusion
- FAQs
What Are Dedicated Servers?
Credits: Freepik
Dedicated hosted servers are powerful computers used exclusively by one organization or website. Unlike shared hosting, where multiple users utilize the same server, a server serves a single client. This setup offers more control, security, and performance. It’s like having your own house instead of sharing an apartment. You don’t have to worry about neighbors using up resources or affecting your security. Servers are ideal for businesses with high traffic, needing robust security, or requiring special software.
Also Read: The Beginner’s Checklist for Choosing a Dedicated Server Provider
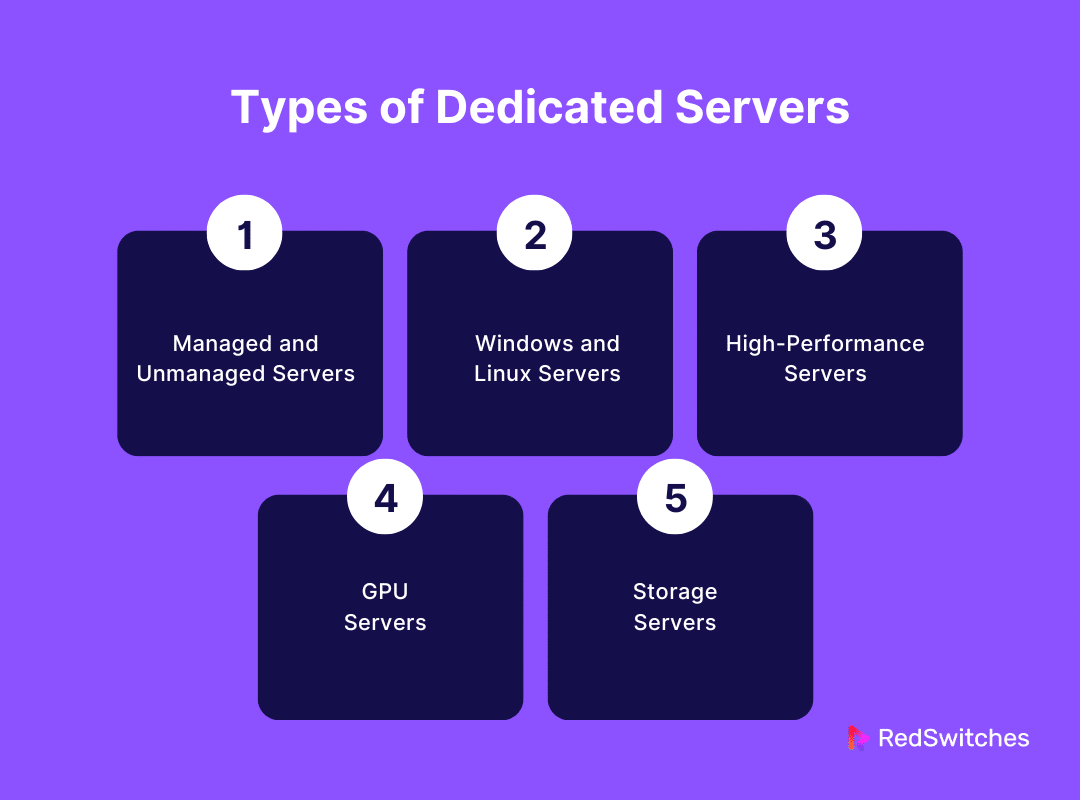
Types of Dedicated Hosted Servers
Dedicated hosted servers come in various forms to meet different needs. Here are some common types:
Managed and Unmanaged Servers
Managed Servers are like a full-service hotel. The hosting provider takes care of everything from security updates to software installations. It’s perfect for businesses without a big IT team.
Unmanaged Servers are more like renting an empty apartment. You have total freedom, but managing everything is up to you. This option suits tech-savvy users or those with IT support.
Windows and Linux Servers
Windows Servers run on Microsoft’s operating system. They are compatible with many business applications. You’ll need a Windows server if your website relies on ASP.NET or other Microsoft technologies.
Linux Servers use the Linux operating system. They are popular due to their stability and security features. Because Linux is open-source, Linux servers are often cheaper than Windows servers.
High-Performance Servers
High-Performance Servers are built for speed and power. They use the latest technology to handle vast amounts of data and traffic. These servers are ideal for big online stores, gaming sites, or websites with high demand.
GPU Servers
GPU Servers have powerful graphics processing units. These servers are not just for gaming or video processing. They’re also used in AI, machine learning, and data analysis. GPU servers can process complex calculations much faster than regular CPUs.
Storage Servers
Storage Servers focus on storing large amounts of data securely. They are optimized for data access and backup. Businesses that need to store videos, large databases, or digital archives use these servers.
Choosing the Right Type
Picking the correct dedicated hosted server depends on your needs. Consider what your website requires. Do you need lots of server storage? Is speed a priority? Security may be your top concern. Also, think about your team’s technical skills. Do you have the expertise to manage a server, or would you prefer a managed solution? Understanding these factors will help you make the best choice for your business.
Dedicated hosted servers offer a reliable, secure, and high-performance hosting solution. With the various types available, you can find one that perfectly matches your requirements. You can have a server, whether running a bustling online store, a corporate website, or a gaming service.
Also Read: Mastering the Dedicated Server Hosting Provider Selection Process in 2024 | An Expert’s Guide
How Do You Secure a Dedicated Hosted Server?
Securing a dedicated hosted server is like locking up your house before leaving. You wouldn’t leave the door open, right? The same goes for your server. In the digital world, threats are everywhere. Hackers are always looking for an open door to sneak through. A secure server keeps your data safe, just like a locked door keeps your home safe. This is important for any business or individual who wants to keep their information away from prying eyes.
We’ll explore how to bolt your digital doors, shut your virtual windows, and ensure your server is as secure as a fortified castle. This means protecting it from outside attacks, unauthorized access, and unexpected threats. You can ensure that your server remains safe for your valuable data with suitable measures.
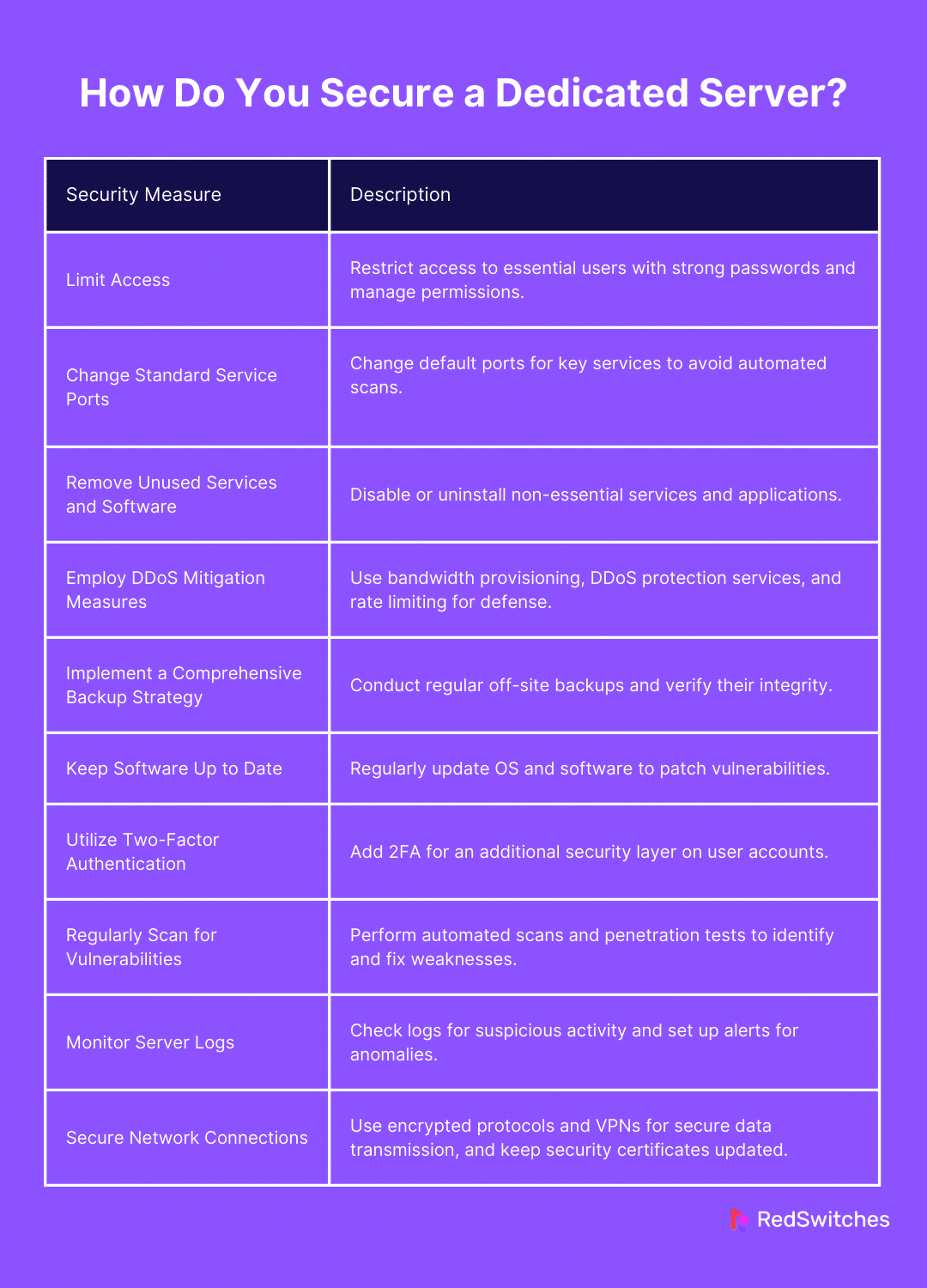
Limit Access
Limiting access to your server is fundamental. Server access should only be given to those who need it.
- Use Strong Passwords: Start with strong passwords. They’re like sturdy locks on your doors. A good password uses a mix of letters, numbers, and symbols. It’s unique and challenging to guess.
- Implement Two-Factor Authentication (2FA): Two-factor authentication adds an extra layer of security. It’s like having a security guard check IDs at the door and needing a key to get in. We will discuss 2FA in detail later.
- Restrict User Privileges: Only some people need full access. Just as only some in a building need a key to every room, users should only have the permissions necessary for their role. This minimizes risk if an account is compromised.
Change Standard Service Ports
Hackers often use automated tools to scan for servers using default ports for services like SSH (port 22) and FTP (port 21). Changing these ports is like moving the entrance to your building to a less obvious location.
- Why Change Ports? Changing ports can deter automated attacks. If a hacker’s scan doesn’t find the expected service on the default port, they might move on to an easier target.
- How to Change Ports: To change a port, you need to edit the service’s configuration file (such as /etc/ssh/sshd_config for SSH) and specify a different port number. After making the change, you’ll need to restart the service for it to take effect.
- Choose Non-Standard Ports Wisely: When selecting new ports, choose ones above 1024 (as ports below these are well-known), but avoid using ports known for other services.
Remove Unused Services and Software
Credits: Freepik
If unused services and software are not properly secured, they can provide an entry point for intruders.
- Identify Unnecessary Services: Use tools like netstat to see what services are running. Look for anything that’s not essential to your server’s operation.
- Disable or Uninstall Unneeded Services: Once you’ve identified services that aren’t needed, disable them. If you’re sure they won’t be needed, uninstall them entirely. This reduces the number of potential vulnerabilities on your server.
- Keep Software Updated: Keep the software and services you use up to date. Software updates often include security patches. Staying current is like fixing broken locks as soon as you know about them.
- Regular Checks: Make it a routine to check for and remove unused services and software. This practice keeps the server environment clean and secure.
Employ DDoS Mitigation Measures
Credits: Freepik
DDoS (Distributed Denial of Service) attacks can overwhelm your server, making it inaccessible. Employing DDoS mitigation measures is like setting up flood defenses for your digital property.
- Overprovision Bandwidth: Have more bandwidth than you usually need. It gives you a buffer to handle sudden traffic spikes without shutting down.
- Use DDoS Protection Services: Many third-party services specialize in detecting and mitigating DDoS attacks. They act as a shield, filtering out malicious traffic before it reaches your server.
- Configure Rate Limiting: Set up rate limiting to control how much traffic a user can send to your server in a given timeframe. It helps prevent single sources from flooding your server.
- Blackhole and Sinkhole Routing: In extreme cases, redirect traffic to a “blackhole” to drop malicious traffic or to a “sinkhole” for analysis.
- Emergency Response Plan: Have a plan in place. Know whom to contact and what steps to take if you’re under attack. Quick action can mitigate damage.
Implement a Comprehensive Backup Strategy
A comprehensive backup strategy is your safety net. If data is lost or corrupted, backups ensure you can recover quickly.
- Regular Backups: Schedule regular backups of critical data. You can set up daily, weekly, or monthly backups depending on how frequently your data changes.
- Offsite Storage: Store backups in a location separate from your server. This could be in the cloud or at a different physical location. It protects your backups from physical disasters.
- Test Your Backups: Regularly test your backups to ensure they can be restored. This practice verifies both the backups’ integrity and the restore process’s effectiveness.
- Use Backup Tools: Many tools and services can automate the backup process. They can handle everything from creating backups to encrypting and transferring them to offsite storage.
- Backup Configuration Files: Remember to backup server configuration files and data. Restoring a server is easier when you have the original configurations handy.
Keep Software Up to Date
Updating software and protecting against new viruses is crucial. When software companies find security holes, they fix them in new updates.
- Automatic Updates: Many operating systems and applications offer automatic updates. Turning this feature on ensures you’re protected without remembering to check for updates.
- Security Patches: Pay special attention to security patches. They specifically address vulnerabilities that attackers could exploit.
- Software Vendor Alerts: Sign up for alerts from your software vendors. They’ll let you know when critical updates are available.
- Update Regularly: Make a schedule for updating non-critical software. This keeps everything current without disrupting your operations.
Utilize Two-Factor Authentication
Credits: Freepik
Two-factor authentication (2FA) adds an extra step to your login process. It’s like having a second lock on your door. Even if someone has your key (password), they can’t get in without the second key (a code sent to your phone, for example).
- Types of 2FA: Use something you know (password) plus something you have (a phone that receives a code) or something you are (fingerprint or facial recognition).
- Implementation: Many services offer 2FA options. Enable them whenever possible, especially for access to sensitive systems.
- Educate Users: Make sure everyone understands how to use 2FA. Provide clear instructions and support.
Regularly Scan for Vulnerabilities
Scanning for vulnerabilities helps you find and fix problems before an intruder does.
- Use Scanning Tools: Many tools are available to scan your systems for known vulnerabilities. Some are free, and others are paid services.
- Penetration Testing: This is a more aggressive form of scanning. It simulates an attack to see how well your defenses hold up. It’s a good idea to hire outside experts for this.
- Fix Vulnerabilities: When you find a vulnerability, fix it immediately. This might mean applying a patch or changing your configuration.
- Regular Schedule: Scan on a regular schedule. How often depends on your specific needs, but monthly is a good general guideline.
Monitor Server Logs
Monitoring server logs is like recording your server’s health and activities. It’s crucial to understand what’s happening under the hood.
- What to Look For: Look for repeated failed login attempts, errors, and warnings. These can indicate security issues or operational problems.
- Tools Can Help: Use log management tools. They can sort through the mass of data, highlight what matters, and even alert you to specific issues.
- Regular Reviews: Make it a habit to check your logs regularly. How often depends on your setup and concerns, but daily checks are a good baseline for critical systems.
- Automate Alerts: Set up alerts for unusual activities, such as multiple failed login attempts or changes to critical files. It’s like having a guard dog that barks if something is off.
Secure Network Connections
Securing network connections is about making sure data travels safely.
- Use Encrypted Protocols: Always use protocols like HTTPS, SFTP, or SSH. They encrypt data in transit, making it unreadable to eavesdroppers.
- Virtual Private Networks (VPNs): VPNs create a secure “tunnel” between your server and the Internet. They’re handy for remote access and add an extra layer of security.
- Firewalls Are Key: Think of firewalls as bouncers at the door. They can block unwanted traffic based on the rules you set. Both software and hardware firewalls have their place.
- Regularly Update Security Certificates: If using HTTPS, keep your certificates current. Expired certificates can trigger warnings in browsers, eroding trust with your visitors.
How Dedicated Servers Improve Security
Dedicated hosted servers are like having your security guard for your website or online service. Unlike shared hosting, where you share space with others, a server is all yours. This setup gives you more control over your online environment. With this control, you can tighten security as much as you need. Imagine your online data as valuables in a vault. A server is like a vault that only you can access. This means fewer chances for unwanted visitors or attacks.
Safety is crucial in the digital world. Let’s explore how servers step up their security game. This approach keeps your information safer than ever.
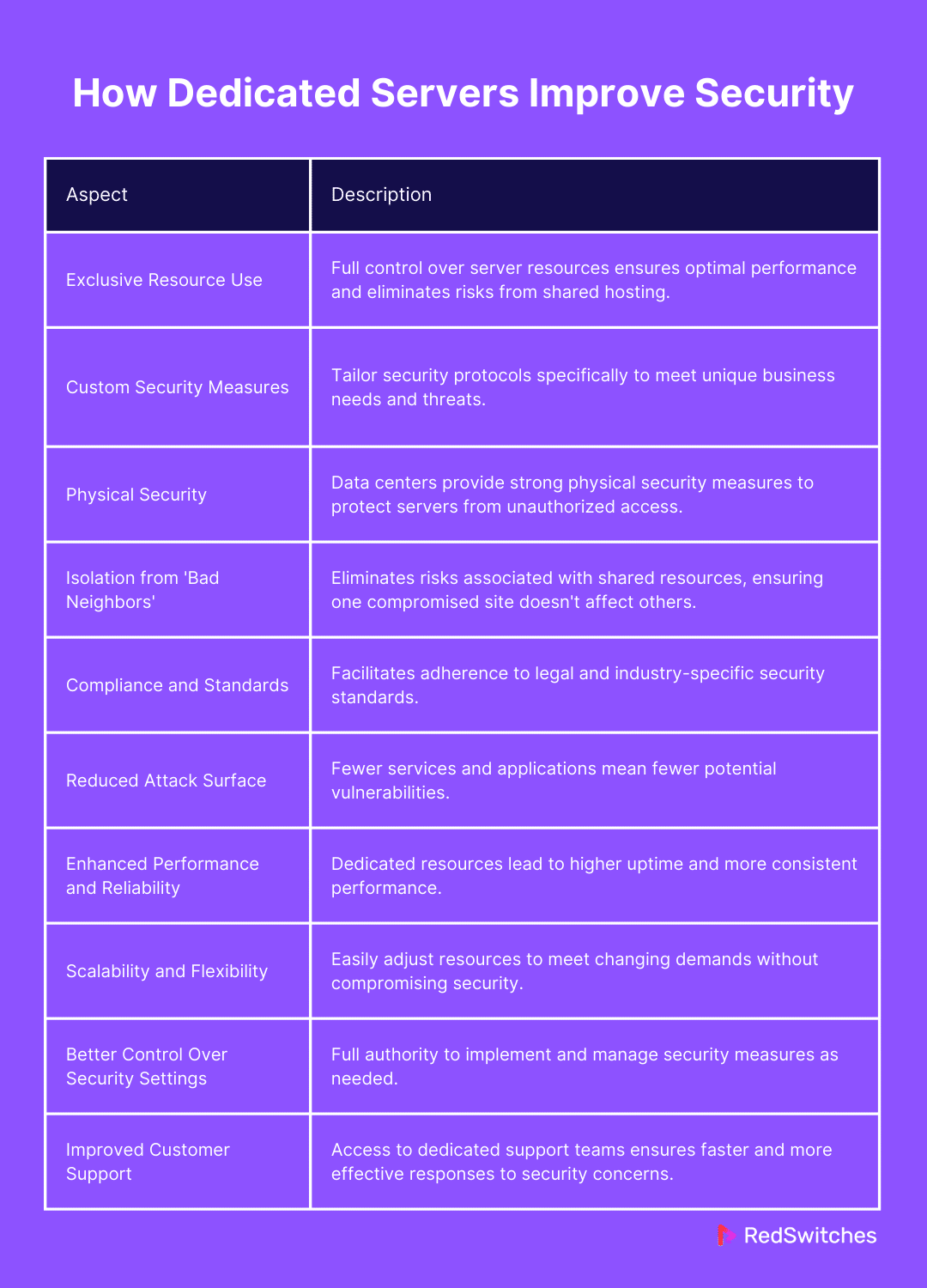
Exclusive Resource Use
When you have a dedicated hosted server, it’s all yours. This means all the server’s resources are for your use only. This exclusivity has big benefits for security.
- No Neighbors, No Problems: Shared servers have many users. If one user makes a mistake, it can affect everyone. On a dedicated hosted server, this risk is gone. You control the environment completely.
- Better Performance, Better Security: With all resources for you, your server runs faster and smoother. This performance boost also means security tools work better. They can scan and protect without slowing down your site or service.
- Tailored to Your Needs: Since the server is yours, you can set it up exactly how you like. This lets you focus resources on what matters most, including security features.
Custom Security Measures
Custom security means making a security plan that fits your needs perfectly. Here’s why custom security measures are a big win:
- Pick Your Protections: You can choose your security tools and settings. You’re not stuck with generic options that might not suit your situation.
- Stay Ahead of Threats: With the ability to customize, you can quickly adapt to new security threats. You’re not waiting for a shared host to update things for you.
- Expert Setup: You can bring security experts to set up your server. They can make sure everything is as tight as a drum.
- Ongoing Adjustments: Security isn’t a one-time deal. You can keep tweaking your setup with a dedicated hosted server to deal with new challenges.
Physical Security
Physical security is about protecting your server’s hardware. Here’s how dedicated private servers help:
- Controlled Access: Data centers with servers have tight security. This includes things like security guards, surveillance cameras, and biometric scans. Not just anyone can walk in.
- Protected from Disasters: These centers also have measures to deal with fires, floods, and power outages, so your server is safe from more than just hackers.
- Location Matters: You can choose a data center in a place known for stability and low risk of natural disasters. This adds another layer of protection.
- Hardware Safety: Your hardware isn’t shared on a server. There’s no risk of another user accidentally or intentionally damaging your server.
Isolation from ‘Bad Neighbors’
In shared hosting, one compromised website could pose risks to others on the same server. Dedicated private servers are different.
- Your Own Space: With a server, your resources are entirely yours. Other sites on the server do not affect your performance or security.
- No Shared Risks: If a cyber attack targets another site on a shared server, all sites on that server could be at risk. Servers eliminate this problem by isolating your site from others.
- Better Control: You have full control over your server environment. This means you can implement security measures that suit your needs without compromise.
Compliance and Standards
Credits: Freepik
Meeting compliance standards is crucial for many businesses. Dedicated private servers make complying with GDPR, HIPAA, or PCI-DSS regulations easier.
- Customizable Security: You can tailor your server’s security settings to meet the specific requirements of different compliance standards. This is harder to do on shared hosting.
- Data Sovereignty: You can choose the server’s location with dedicated private servers. This choice helps you meet the data residency requirements of certain laws and regulations.
- Audit-Friendly: Servers offer better logging and monitoring capabilities. This makes it easier to provide the necessary documentation during audits.
- Dedicated IP Address: A dedicated IP can be required for certain compliance standards. It also adds a layer of security and professionalism to your operations.
Reduced Attack Surface
The attack surface is all the possible points where an unauthorized user can try to enter your system. Dedicated private servers naturally have a smaller attack surface.
- Less Software Means Fewer Vulnerabilities: By only installing the software you need, you reduce the number of potential vulnerabilities on your server.
- Control Over Updates: On a server, you decide when and how to update your software. This control lets you close security gaps quickly without waiting for a provider to do it.
- No Multi-Tenant Issues: Since you don’t share the server with anyone, there are no risks from other tenants’ actions. This situation significantly reduces an attacker’s paths to compromise your server.
- Custom Firewalls: You can configure firewalls specifically for your use case. This customization allows for tighter security than the more generic setups often found on shared servers.
Enhanced Performance and Reliability
Imagine a highway with no traffic; that’s the level of performance and reliability you get with a dedicated private server. Your website or application runs smoothly without the slowdowns common in shared hosting environments.
- Dedicated Resources: You own all the server’s processing power, memory, and storage. This means your operations aren’t affected by other users’ demands, leading to faster load times and a more reliable service.
- Optimized Setup: Tailor your server’s configuration to meet your specific needs. This customization ensures optimal application performance.
- Uptime: Providers often guarantee high uptime rates with servers. This reliability is crucial for businesses where downtime directly translates to lost revenue.
Scalability and Flexibility
Businesses change and grow; your server should, too. Dedicated private servers allow for easy storage, RAM, and CPU upgrades, so you can expand your resources without migrating to a new server.
- Adaptability: Adjust your server’s environment as needed. Whether it’s installing new software or adjusting configurations, you have the freedom to adapt your setup to new requirements.
- Bursting Capabilities: Some providers offer the option to access additional resources temporarily to handle spikes in traffic. This feature is like having an extra gear in a car for when you need to speed up.
Better Control Over Security Settings
Credits: Freepik
You can implement security measures that fit your specific needs on a dedicated private server. This could mean installing advanced firewalls, intrusion detection systems, or encryption protocols.
- Software Choices: Choose the security software you trust. You’re not limited to the options provided by a shared hosting platform. This freedom lets you use tools that align with your security policies.
- Immediate Updates: Apply security patches and updates on your schedule, ensuring vulnerabilities are addressed immediately. You might have to wait for the hosting provider in a shared environment.
Improved Customer Support
With dedicated private servers, providers often offer higher customer support. This includes access to a team of experts who understand your specific setup.
- Faster Response Times: Dedicated support means quicker resolutions when issues arise. You’re not in a long queue of shared hosting customers; you’re a priority.
- Custom Solutions: Customer support can work with you to create solutions tailored to your server’s setup. This personalized assistance is invaluable for complex or critical issues.
- Proactive Monitoring: Some providers offer proactive monitoring services, monitoring your server’s health and performance. They can alert you to potential issues before they become problems.
Here’s a table summarizing how servers improve security across various aspects:
Top-Tier Security Solutions with Redswitches Dedicated Private Servers
Redswitches dedicated hosted servers stand at the forefront of delivering top-tier security solutions. These servers are designed to offer the highest level of protection for your data and applications. Let’s explore what makes Redswitches servers a cut above the rest in ensuring your online presence is secure and reliable.
Unmatched Physical Security
Physical security is the first defense in protecting a dedicated private server. RedSwitches understands this. Our server data centers are equipped with state-of-the-art security measures. These include round-the-clock surveillance, biometric access controls, and secure entry points. Only authorized personnel can access the hardware, ensuring your dedicated private server is well-guarded against any physical threats.
Advanced Network Protection
Advanced network protection tools back Redswitches dedicated private servers. These include sophisticated firewalls and intrusion detection systems (IDS). The firewalls act as gatekeepers, allowing only legitimate traffic to pass through. Meanwhile, IDS monitors for suspicious activities, providing an additional layer of security. Together, they safeguard your server against potential cyber threats, from DDoS attacks to unauthorized access attempts.
Regular Software Updates
Keeping software up-to-date is crucial in mitigating security risks. Redswitches dedicated hosted servers receive regular software updates and patches, ensuring vulnerabilities are promptly addressed. Your server remains protected against known exploits and attacks by staying current with the latest security patches.
Customizable Security Settings
Every business has unique security needs. Redswitches recognizes this, offering customizable security settings on its dedicated hosted servers. You can configure firewalls, install security software, and set access controls according to your requirements. This flexibility allows you to tailor your server’s security measures to fit your needs, providing a personalized defense strategy.
Enhanced Data Privacy
Credits: Freepik
Data privacy is a top priority. RedSwitches dedicated hosted servers store your data on isolated hardware. This isolation from ‘bad neighbors’ ensures your sensitive information is not compromised. Furthermore, the dedicated environment allows for strict data access policies, enhancing the privacy and integrity of your data.
Also Read: Unveiling the Hidden Risks of Dedicated Servers
Reliable Support
Prompt support can make all the difference in a security concern. Redswitches offers reliable customer support, ready to assist with any security issues that may arise. Our team of experts is available 24/7, providing peace of mind that help is just a call or click away.
Redswitches dedicated hosted servers bring together robust physical security, advanced network protection, and customizable security settings. We offer a solid foundation for businesses looking to secure their online presence. With regular software updates, enhanced data privacy, and reliable support, RedSwitches dedicated hosted servers are a top-tier choice for those seeking comprehensive security solutions.
Conclusion
Keeping your dedicated hosted server safe is a must in today’s world of cyber threats. These servers are great for businesses because they work well and are reliable. However, they can also attract hackers.
By setting strong passwords, keeping software up-to-date, protecting against DDoS attacks, and using encryption, businesses can build a strong shield against cyber dangers. Dedicated hosted servers have great benefits, like using all the server’s resources, having security setup just how you need it, being physically secure, and helping you follow the rules and regulations.
These servers help keep your online space safe, limit hackers’ attempts to break in, and let you change settings to fit your business needs. With careful planning and constant monitoring, businesses can ensure their servers are strong and secure online spots.
Choose RedSwitches today to protect your digital world! With RedSwitches, you get the best security for your server, designed just for you. You get to use all the server’s resources, enjoy the security that fits your needs perfectly and have support from our top team. Don’t wait. Make your online space safer with RedSwitches now!
FAQs
Q. How do I protect my dedicated server?
Limit access with strong passwords and two-factor authentication, change default service ports, remove unused services and software, employ DDoS mitigation measures, keep software up to date, utilize encryption, and regularly scan for vulnerabilities.
Q. Are dedicated servers more secure?
Yes, dedicated hosted servers offer more security because they provide exclusive resource use, allow for custom security measures, and isolate your data and operations from other users, reducing the risk of cross-contamination from other compromised sites.
Q. What is the purpose of a dedicated server?
A dedicated hosted server provides a powerful, exclusive computing resource for a single client or organization, offering enhanced control, security, and performance for websites, applications, and databases, especially suitable for high traffic, resource-intensive, or sensitive operations.
Q. What is server security?
Server security encompasses the processes, tools, and protocols used to protect data, applications, and the integrity of the server from unauthorized access, cyberattacks, and other vulnerabilities, ensuring the server remains safe and operational.
Q. Why is security important in servers?
Security is crucial in servers to protect sensitive data from theft, loss, or corruption, ensure the continuity of services and operations, maintain customer trust, and comply with legal and regulatory requirements, ultimately safeguarding the organization’s reputation and financial health.
Q. How does a dedicated hosted server enhance data security compared to shared hosting servers?
A dedicated hosted server provides an isolated environment, reducing the security risk associated with shared resources and allowing the implementation of robust security measures tailored to specific needs.
Q. What are the key best dedicated server security practices to prevent security breaches?
Implementing regular security updates, employing strong access controls, using firewalls and intrusion detection systems, and conducting scanning and real-time server monitoring are critical practices.
Q. How does managed dedicated server hosting improve the security of your server?
Managed dedicated hosting providers take responsibility for security updates, patches, and monitoring, ensuring the server is protected against the latest security threats with expert oversight.
Q. Why is choosing a dedicated server important for enhancing web hosting security?
Affordable dedicated servers offer exclusive use of server resources, allowing for customized security settings, dedicated IP addresses, and minimized exposure to potential security threats from other users.
Q. What steps can I take to secure my dedicated hosted server against potential security vulnerabilities?
Regularly update software, install the latest security patches, configure firewalls, enable SSL for a secure connection, and employ data encryption to secure data in transit and at rest.
Q. How can I ensure the physical security of my dedicated hosting server?
Choose a hosting provider with data centers equipped with comprehensive physical security measures, such as surveillance cameras, biometric access controls, and secure, disaster-resistant facilities.
Q. What role do security updates play in maintaining a secure dedicated private server hosting environment?
Security updates address vulnerabilities, providing fixes to potential security risks that could be exploited by cyber attackers, ensuring the server remains protected against known threats.
Q. How can data backups contribute to the overall security strategy of a satisfactory dedicated server?
Regular data backups ensure data security by allowing for the recovery of critical information in the event of data loss, corruption, or a security breach, minimizing the impact on operations.
Q. Why is installing software from reputable sources essential on your affordable dedicated server?
Installing software only from trusted sources minimizes the risk of introducing malware or vulnerabilities into the server environment, contributing to the overall security of your dedicated hosted server.
Q. What are effective ways to secure a dedicated server for a business relying heavily on server hosting?
Employing a combination of security best practices such as securing network connections, enabling DDoS protection, conducting regular vulnerability assessments, and engaging in continuous monitoring and real-time alerting to identify and mitigate threats promptly.