Do you know that the first firewall was developed in the 1980s by DEC and Cisco?
Since then, firewalls have been an integral part of network defenses. Over the years, firewalls evolved to keep pace with the emerging network technologies. But, more than that, firewalls grew in complexity and implementation as the frequency and sophistication of cyberattacks increased.
Given the variety in firewall technology, choosing the right type of firewall for your specific security requirements can be challenging.
So, in this guide, we’ll go over the different types of firewalls in some detail so that you have a clear understanding of how they operate and which one to pick up to defend your networks.
But let’s start with the most fundamental question:
Table Of Content
- What is a Firewall?
- How Does a Firewall Work?
- Types of Firewalls
- Firewall Deployment Strategies
- Conclusion
- FAQs
What is a Firewall?
A firewall is a security platform that observes incoming and outgoing network traffic in order to identify and block harmful data packets based on specified criteria, letting only genuine traffic into your private network.
Whether deployed as hardware, software, or both, firewalls are often among the first lines of defense against malware, viruses, and intruders trying to access your organization’s internal network and systems.
How Does a Firewall Work?
A firewall protects your network by operating as a continuous filter that scans incoming data and blocks anything that appears to be suspicious.
A firewall, whether hardware or software, builds a wall between your network and the internet. Optionally, firewalls can isolate specific network components from the rest of your system.
When active, a firewall can block an attacker from taking advantage of your system and using it to mount further attacks. Similarly, it stops harmful code from entering your network by analyzing data as it enters and leaves your system.
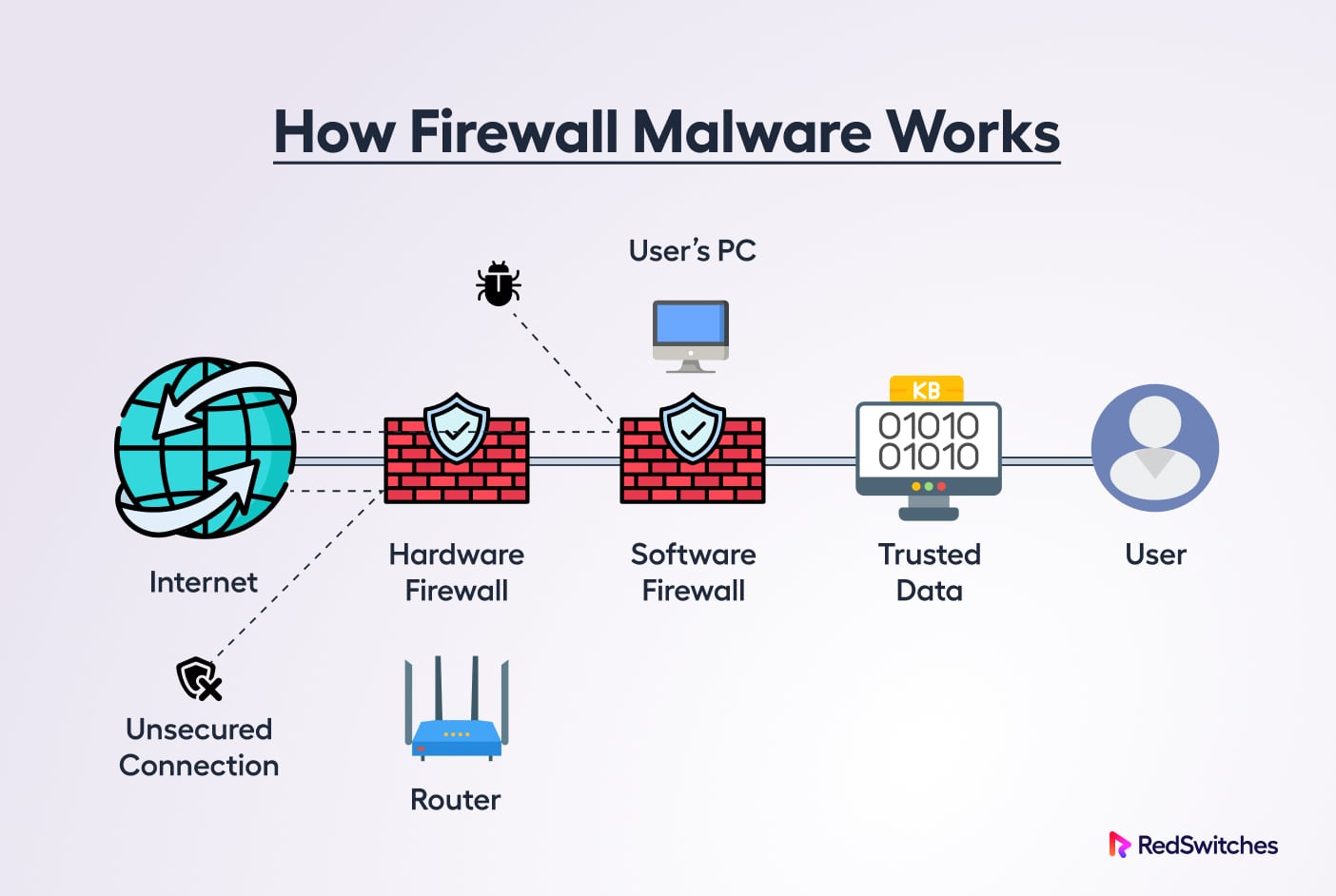
It scans the source and destination addresses and, using established criteria, decides whether a data packet should pass through.
A software firewall can further filter the traffic when a data packet enters your company’s network to allow or restrict access to specific ports and applications on a computer system, enhancing control and protecting against insider threats.
Why Should You Use a Firewall?
Installing a firewall for your network provides several advantages, including monitoring network traffic, stopping virus attacks, preventing hacking, stopping spyware, and promoting privacy.
Monitors Network Traffic
The first benefit of firewall security is the ability to monitor network traffic. By analyzing data from your systems, firewalls can leverage pre-established rules and filters to protect your systems. Then, with a well-trained IT team, you can manage your levels of protection based on what you see coming in and out through your firewall.
Stop Viruses
Another benefit of firewalls is the ability to stop virus attacks. With the constant development of new threats, it is crucial to put defenses in place to keep your systems healthy. Firewalls control your system’s entry points and can prevent virus attacks that could cause immeasurable damage to your networks and connected devices.
Prevent Unauthorized Access Through Spyware
Firewalls also prevent hacking, as they are a critical blockade against unauthorized access to your data, emails, systems, and more. Criminals often use spyware and malware to gain access to your network, but firewalls can stop them entirely or deter them from targeting your business.
Improved Privacy
In addition, firewalls provide privacy protection by proactively working to keep your data and your customer’s data safe. This builds trust for your clients, as they can rely on your business to protect their sensitive information from being stolen.
Understanding and implementing firewall security is crucial for businesses in today’s digital age to protect their systems, data, and clients.
Types of Firewalls
Firewalls come in several different types to cater to specific security scenarios. The following is the list of the most common types of firewalls used for network defense.
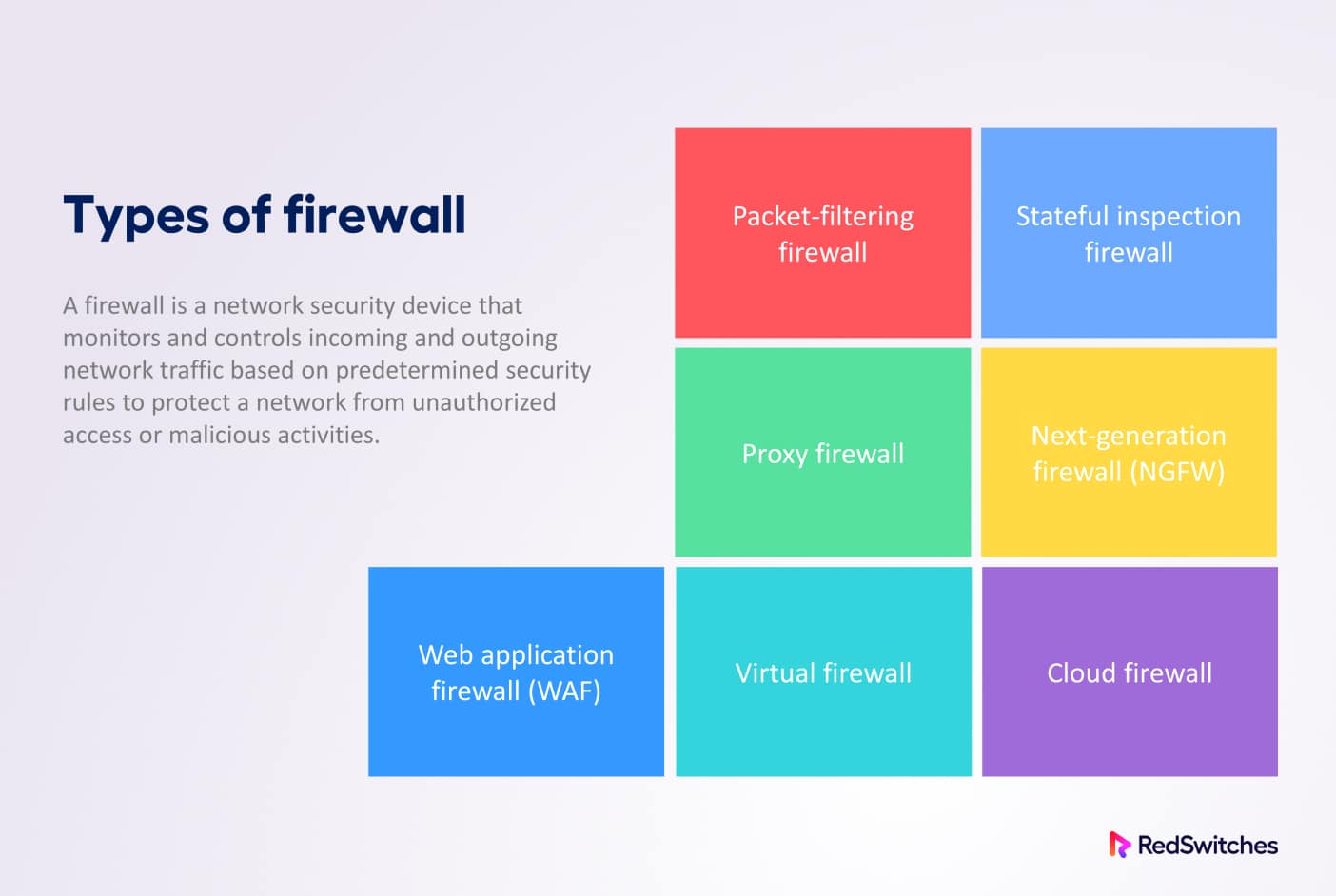
Packet-filtering Firewall
The earliest and most fundamental type is the packet-filtering firewall.
Operating at the Network layer, these firewalls examine a data packet’s source and destination IP addresses, protocol, source and destination ports, and other details against pre-established rules to decide whether to pass or discard it.
As they don’t keep account of the established network connections or the packets that have already flowed through it, packet filtering firewalls monitor each packet separately.
As a result, these firewalls have very little ability to defend against sophisticated threats and assaults.
Example of Packet filtering Firewalls
Cisco ASA: The Cisco Adaptive Security Appliance (ASA) is a packet filtering and Checkpoint firewall. Depending on several variables (source and destination IP addresses, port numbers, and protocols), these can block or permit traffic.
Advantages
- Firewalls with packet filtering are quick, inexpensive, and efficient.
- Packet filtering firewalls are often the foundation of more secure network security processes.
Limitations
- These firewalls only provide a basic level of security.
- They cannot defend against malicious data packets from trusted sources or IP addresses.
Circuit-level Gateway Firewalls
Circuit-level gateways monitor active sessions and confirm established Transmission Control Protocol (TCP) connections while operating at the Session layer or between the Application and Transport layers.
They share many features with Packet-filtering firewalls, such as the single check they run and the low resource use. However, they operate at the higher layers of the standard OSI model.
Examples of Circuit level GatewayFirewalls
A great example is the line of circuit-level gateway firewalls from SonicWall called the TZ Series. Barracuda CloudGen Firewalls are also a popular example of circuit level-gateway firewalls.
Advantages
- These are inexpensive and straightforward and minimally affect network performance.
- Easy to set up and manage.
- Efficient Resource usage
Limitation
- These types of firewalls are an incomplete security solution since inspecting the content of data packets is impossible.
Application-level Gateway Firewall
These firewalls are more commonly known as proxy firewalls. They operate at the Application layer and are usually implemented as a software firewall.
When these firewalls are in action, an external source cannot connect directly to your internal network. Instead, it connects to the proxy firewall.
The proxy firewall verifies the request’s legitimacy before sending it to one of the internal servers or devices on behalf of the client.
Examples of Application-level Gateway Firewalls
Symantec ProxySG and F5-BIG-IP are examples of application-level gateway firewalls providing excellent control over web traffic.
F5 BIG-IP offers sophisticated application security, acceleration, and load-balancing features.
Advantages
- The context and content of data packets are examined by proxy firewalls using stateful and deep packet inspection and then compared to user-defined rules.
- By restricting a direct link between internal systems and external networks, they protect the location and identity of your resources.
Limitations
- They are expensive in terms of resources due to higher processing requirements.
- Higher network latency due to additional steps in packet checks.
- Not compatible with all network protocols and complex to set up.
Stateful Inspection Firewall
Stateful inspection firewalls offer a higher degree of protection thanks to thorough packet inspection.
These firewalls confirm and track connections and are considered much better than circuit-level gateways.
After a client makes a connection, the firewall creates a state table comprising the source IP, destination IP, source port, and destination port.
So, instead of depending on a hardcoded set of rules, the firewall generates its own rules dynamically to check and verify incoming network traffic.
Example of Stateful Inspection Firewalls
Cisco Firepower is a stateful inspection firewall with unified management and automation features that deliver advanced threat protection. It tracks the status of network connections and applies security policies based on the context of the traffic flow using a stateful inspection engine.
Advantages
- These firewalls provide advanced security by checking for legitimate connections.
- Reduced interaction with port scanners.
Limitations
- These firewalls consume more resources.
- You need good technical skills for the setup and maintenance.
- Often, these could be more expensive than packet-filtering firewalls.
Next-generation Firewall (NGFW)
The Next-generation firewalls are designed to deal with the increasing cases of data breaches and related attacks.
NGFW comes with several innovative features to ensure protection in the event of multiple attacks.
A firewall is considered next-generation if it can do deep packet inspection in addition to port/protocol and surface-level packet inspection, and TCP handshake checks, despite having flexible features and architectures.
Examples of NGFW
Palo Alto Networks, Cisco Firepower, and Fortinet FortiGate are next-generation firewalls. These firewalls provide advanced threat protection and better control over network traffic.
Advantages
- NGFWs provide application awareness capability for intelligent traffic and resource analysis (protocol-based detections, anomaly-based detections, etc.)
- Deep packet inspection is better able to find abnormalities and malware.
- These firewalls can prevent or block the impact of DDOS attacks.
- Integrate traditional firewall features with cybersecurity skills.
Limitations
- NGFW often costs more than other popular types of firewalls.
- You need serious technical skills to set up and maintain these firewalls.
- Users have reported higher network latency when these firewalls are active.
Network Address Translation (NAT) Firewall
A Network Address Translation (NAT) firewall runs on a router to better protect private networks. It only lets internet traffic through when a private network device requests it. In addition, a NAT firewall hides internal IP addresses from external contacts to protect a network’s identity.
When a NAT firewall is active, data packets are sent from your device to a web server as a request. These packets contain data like the IP addresses of the sender and receiver, port numbers, and the requested information.
As the packets pass through a router running the NAT firewall, the firewall changes the private IP address of the data packet to the router’s public IP address. This change is noted and added to the NAT forwarding table.
The web server receives data packets that contain the required information. The data is transmitted back to the router, which then uses the NAT forwarding table to determine which device on the private network requested the data.
Examples of NAT Firewalls
Cisco ASA (Adaptive Security Appliance), SonicWall TZ Series, and Fortinet FortiGate are well-known firewalls that provide NAT functionality to defend against network-based threats.
Advantages
- NAT keeps the internal IP addresses hidden from all external contacts for improved network security.
- The firewall reuses private IP addresses and conserves IP address space.
Limitations
- Hackers can deploy viruses and trojans to track incoming messages to a device on the internal network.
- NAT may not help to protect your device from Man-in-Middle attacks and phishing scams.
Web Application Firewall (WAF)
A Web Application Firewall, or WAF, protects networks by filtering and keeping track of HTTP traffic between a web application and the Internet.
Typically, it defends web applications against attacks like SQL injection, file inclusion, Cross-site Scripting (XSS), and cross-site forgery.
A WAF can often only handle some types of attacks. This is because it operates at the Application layer. A WAF is deployed before a web application to create a wall between the application and the Internet. It can protect against multiple vectors.
WAF works based on the policies added in negative and positive security models, also known as blocklists & allowlists. It denies access to requests which do not match the rules mentioned in the allowlists.
You can implement WAF in 3 different configurations:
- Network-based WAF is generally hardware-based to reduce latency.
- Host-based WAF is implemented as a software firewall that offers multiple customizing options.
- Cloud-based WAF is easy to implement, reduces cost, and requires a DNS change.
Examples of WAF
ModSecurity is open-source software WAF that allows admins to set flexible rules.
Cloudflare WAF is the most popular WAF Content Delivery Network.
Advantages
- It can detect when malicious content comes through HTTP traffic. It can monitor, filter and easily block these threats.
- Network admins can easily customize WAF rules to allow or block specific traffic sources.
- WAF can be used to set up a Content delivery network(CDN) that helps improve website performance.
- WAF helps protect the hosted applications from bots, crawlers, and related cyberattacks.
Limitations
- Changes in WAF might block legitimate traffic.
- WAF’s cost and performance can be drawbacks as WAF must be actively maintained & configured frequently to achieve maximum security.
Firewall Deployment Strategies
Firewalls are such an essential part of network security that engineers and developers have devised several ways of implementing firewalls for network protection.
We’ll now discuss three ways of deploying firewalls that you can choose to protect your network.
Software Firewalls
You need to install a software firewall on most of the network devices (ideally all the devices). As a result, a software firewall can only protect one system at a time.
Since they use the CPU and memory of the devices installed on them, software firewalls can quickly get expensive regarding resources. Thus, administrators should carefully consider the deployment of these firewalls.
Additionally, software firewalls offer precise control over traffic, and administrators can allow or deny traffic based on usernames or access privileges.
Hardware Firewalls
A hardware firewall is a device that runs independently of the network and connected devices. It protects the network by filtering data entering the system through the internet access points.
The broadband internet router you use likely has a firewall.
Hardware firewalls that use packet filtering examine each data packet to ascertain its origin and destination. The firewall examines and collects each packet’s information and compares it to see if it fits the criteria set by the network administrators.
Since hardware firewalls run on physical devices, there is no need to worry about resource consumption.
Cloud-based Firewalls
Cloud firewalls are software-based network filters placed in the cloud to prevent or limit illegal access to private networks.
These software components usually sit outside the network and control access to internet network resources based on the pre-set rules.
Usually, these firewall components are implemented as part of a web-based application. As a result, cloud firewalls can be easily integrated into projects without worrying about integration issues.
A popular example of a cloud-based firewall is Cloudflare Magic Firewall.
Conclusion
Firewalls play a crucial role in network security by helping to protect networks from unauthorized access, malware attacks, and other security threats. The importance of having a firewall cannot be overstated, as it acts as the first line of defense against potential cyber-attacks.
Seven types of firewalls are available, each with its strengths and weaknesses. These include packet filtering firewalls, stateful inspection firewalls, application firewalls, proxy firewalls, network address translation firewalls, next-generation firewalls, and cloud firewalls. Understanding the different types of firewalls can help organizations choose the best option for their specific security needs.
Firewalls analyze incoming and outgoing traffic and either allow or block it based on predefined rules.
By using a combination of firewalls, organizations can create a multi-layered security strategy that helps ensure their networks’ safety and sensitive data.
By understanding the different types of firewalls available and how they work, organizations can choose the proper firewall for their needs and create a layered defense against cyber threats. It is essential to stay vigilant and proactive in implementing and managing firewalls.
Frequently Asked Questions :
1. How to pick a firewall for your network?
You may consider these points when evaluating a firewall for your network :
- Before choosing the best firewall form, conduct a thorough vulnerability assessment.
- Ensure the new firewall keeps the network from slowing down and affecting the user experience.
- Prioritize more affordable choices first.
- If you need security at the app layer, don’t just rely on packet-filtering and stateful inspection firewalls.
A universally applicable solution is often a good fit for most network security requirements.
2. What are the two main types of firewalls?
The two main types are network-based and host-based firewalls
3. Which is the most common type of firewall used?
The application gateway or proxy firewall is the most commonly used firewall because it allows content filtering and works at the Application layer of the OSI model.
4. How do we categorize the ten types of firewalls?
The software, hardware, and cloud-based firewalls are categorized into delivery method firewalls. And packet filtering, circuit-level gateway, application gateway, stateful inspection, next-generation firewalls, NAT, and WAF.

