According to a 2021 survey by Sucuri, 1 in 25 WordPress websites has been compromised in some way. Now, given that there are more than 800 million websites powered by WordPress, the number of affected websites is simply mind-boggling.
WordPress is the most approved CMS in the market. But unfortunately, this makes it a very lucrative target for cybercriminals looking for sensitive user data, such as credit card information.
WordPress security issues happen for several reasons, including human error and malware launched by cybercriminals. The good news is that by following a list of WordPress security best practices, you can harden the overall security of your website. And, in case your website gets compromised, recovering from the incident is reasonably straightforward.
This article explores the 14 most common WordPress security issues. It presents simple fixes that you can apply to prevent these issues from happening or recover the website from the incident as quickly as possible.
So without delay, let’s jump into the list of WordPress security issues.
Table Of Contents
- The 14 WordPress Security Issues You Can Easily Fix
- Outdated Core Software
- Outdated Themes and Plugins
- Malware
- Credit Card Skimming Attacks
- Unauthorized Website Access
- Undefined User Roles
- Structured Query Language (SQL) Injections
- Search Engine Optimization (SEO) Spam
- Cross-Site Scripting
- Denial-of-Service Attacks
- Phishing
- Supply Chain Attacks
- Hotlinking
- Cross-site Request Forgery (CSRF)
- So – Is WordPress Secure If You Follow Best Practices?
- How Can Your Hosting Provider Help Secure Your WordPress Websites?
- Conclusion
- FAQs
The 14 WordPress Security Issues You Can Easily Fix
As a WordPress website owner, the following are the 14 most common WordPress security issues you’d encounter.
#1. Outdated Core Software
One of the biggest security issues with WordPress sites. Users and security experts regularly identify loopholes and related security challenges in WordPress core software. That’s why every new WordPress core version fixes most of the previously identified issues.
So, if you continue to run an older version of the WordPress core software, you are inviting hackers to exploit and gain access to your site and damage it.
Why Are WordPress Sites Vulnerable?
Hackers continuously try to take advantage of any known vulnerabilities in outdated WordPress core software. Popular attacks involve unauthorized access to your site or the installation of malicious code.
How Can You Fix This?
The fix is simple enough – make sure you are running the most recent stable version of the WordPress core software.
WordPress releases major versions (with new features and fixes) and minor versions (urgent fixes and minor updates) on a consistent schedule.
The auto-update feature is a great help in automating the update process. However, we highly recommend testing new versions at a staging website to make sure things don’t break. Once you’re satisfied, you can update the live site.
#2. Outdated Themes and Plugins
Outdated themes and plugins pose a similar level of threat as outdated WordPress core. Popular WordPress plugins are favorite targets because of their wide user base. For instance, Astra, a very popular WordPress theme, has more than 1 million active users.
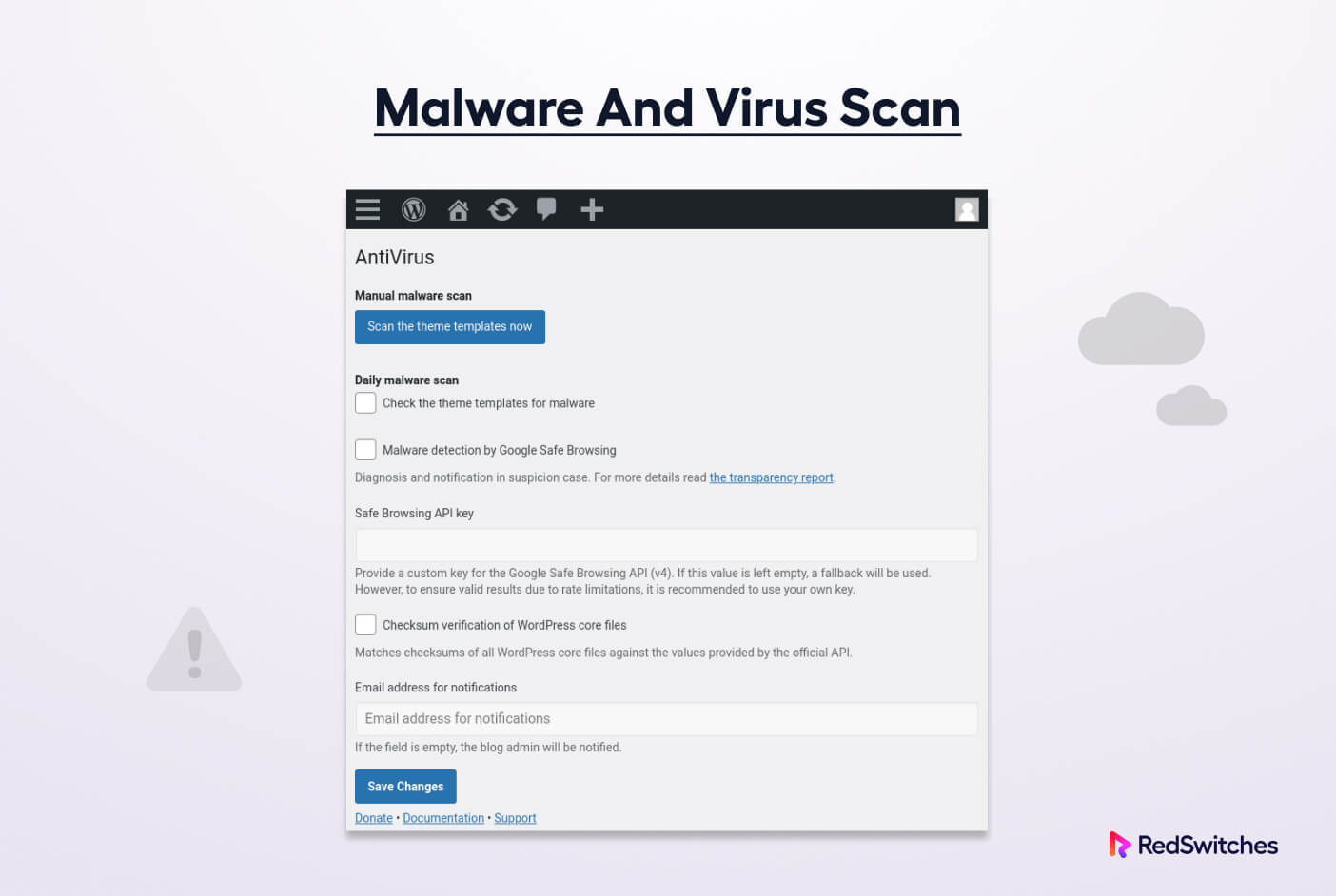
#3. Malware
Malware is a collective term for malicious software that can damage your site, steal sensitive information, or cause other security issues. This is a serious security challenge for WordPress users because it’s easy to inject malware into your website through several channels.
Why Are WordPress Sites Vulnerable?
WordPress sites are especially vulnerable to malware attacks because hackers can introduce malicious code into your site in many ways, including outdated software, plugins or themes containing malicious code, or third-party ads.
You’d be surprised to discover how easy it is to hide malware amongst the many folders found on a typical server hosting a WordPress website. That’s why cleaning an infected website requires the services of an expert.
How Can You Fix This?
Protection against malware is a matter of following a couple of security recommendations.
First, only use products developed and maintained by reputable companies. We know it’s tough to say no to free software, but you must do due diligence by checking out the reviews and user comments to verify that the product is safe to use.
Next, keep every plugin on the website updated to ensure the codebase is updated and free from malware.
We highly recommend setting up a WordPress security plugin to regularly scan the website and increase website security.
If your website gets infected with malware, you can ask a WordPress security expert for removal and restoration. Your hosting provider is an important player in protecting your website against malware by implementing server-level security.
#4. Credit Card Skimming Attacks
Credit card skimming refers to the theft of credit card information from your site’s visitors. Credit card skimming attacks seriously damage your business’s reputation.
Hackers can insert malicious code into your site to capture this information, which they can use for fraudulent purposes.
Why Are WordPress Sites Vulnerable?
WordPress sites can be vulnerable to credit card skimming if they collect customer payment information. Hackers can use any known vulnerabilities in your site’s software or plugins to insert malicious code.
To steal card information, such as the card number and PIN code, attackers usually access the website backend, where they insert a “skimmer” that attacks the third-party payment processing scripts. During this process, the skimmer copies the credit card information that a visitor enters in the website payment form. This data is usually sent to an anonymous location where the hacker can use it in any way they please.
How Can You Fix This?
Preventing credit card skimming attacks is about hardening the security of the website. Here’re the specific steps you can take to secure your website.
Always ensure that your WordPress website and any installed plugins and themes are updated to the most recent version. This closes off known security holes that attackers might use to gain access to your website and plant the skimmer.
Instead of installing a skimmer, hackers often intercept data as it moves from your website to the payment processing portal. To counter this, install an SSL certificate on your website This simple measure encrypts all data going out from your website. So even if the hackers manage to intercept the data from your website, they won’t be able to use it to get credit card information.
#5. Unauthorized Website Access
Unauthorized access refers to hackers gaining access to your site’s backend without your permission. Hackers can gain access to your site in various ways, including weak passwords, phishing, or brute force attacks.
Why Are WordPress Sites Vulnerable?
Attacks to gain unauthorized access to your website works because of two main reasons.
First off, it’s rather simple to identify the default WordPress admin login page for a WordPress site. Anyone can access this page by adding /wp-admin or /wp-login.php to the end of the website’s primary URL. Once there, attackers try a brute-force entry attack to gain access.
During his WCEU 2021 presentation, Santoyo emphasized the brimportance of altering the default settings and the wp-admin file. Retaining the default configurations invites attacks because these settings are easily available to all.
Another aspect of unsecured websites is using weak and popularly-known usernames and passwords. Two infamous examples are admin/admin or admin/password.
How Can You Fix This?
The simplest and best defense against brute-force attacks is a strong password that is challenging to crack even with the sophisticated technologies straight out of The Matrix.
To give you an idea of how strong passwords protect your website, consider the fact that a hacker needs 1.5 years to crack a 10-digit all-numeric password.
In addition, you can take the following steps to protect your website from unauthorized logins:
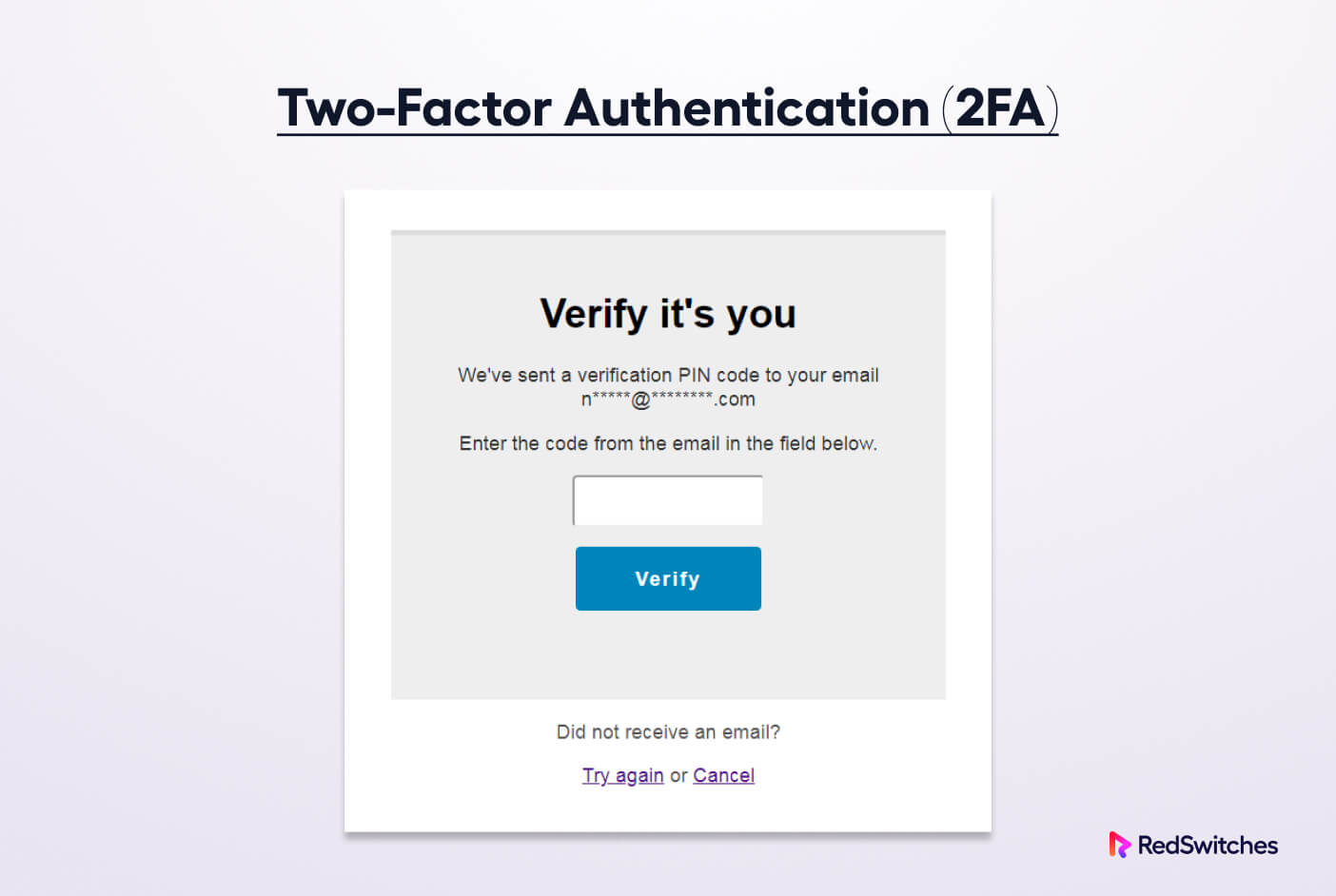
- Set up two-factor authentication for each user so that they need to provide additional credentials generated on a separate device.
- Consider creating a new admin account with a secret username instead of keeping the WordPress default account with the username “admin” (which is the first thing hackers will guess).
- To prevent brute-force attacks, install login rate-limiting plugins that restrict login attempts after three or five attempts.
#6. Undefined User Roles
Undefined user roles refer to users with access to your site that are not assigned a specific role or permission. Such users can create security issues by accessing sensitive information or installing malicious code.
Why Are WordPress Sites Vulnerable?
In the rare worst cases, undefined users with admin privileges can wreak havoc on a website. However, generally, attackers who use this attack often deploy malware on the website so that they can further exploit the visitors’ information.
Similarly, if brute-force attacks are successful against your website, poorly defined admin roles put your site in greater danger since hackers can gain full control of the website. Additionally, cross-site scripting attacks (discussed below) allow access to front-end features that can be used to collect more data from visitors.
How Can You Fix This?
For starters, you should immediately audit roles and permissions on your website. Make this a regular security check by monitoring new user registration and role assignments.
Each user, regardless of their role, should have a strong password and TFA enabled by default. Additionally, make sure each user is assigned the lowest permission by default. For instance, make sure that the Contributors on your website can’t delete published posts. You can review the user and allocate additional permissions manually.
#7. Structured Query Language (SQL) Injections
SQL injection is an attack where a hacker inserts malicious SQL statements into a form field. When the form is submitted or processed, the query is executed on the website database with disastrous results.
Why Are WordPress Sites Vulnerable?
WordPress sites are vulnerable to SQL injections because forms are commonly used at several places on WordPress websites. If the input from these forms is not properly vetted, they can provide an entry point for attackers.
How Can You Fix This?
The wisest course of action is to treat all user input with a large pinch of salt. All forms and text fields on your website should be “sanitized” before further processing and execution for the site’s database.
Sanitization is usually handled by the form or security plugins. This is a multi-step process that ensures that the data from the forms is free of malicious SQL statements. For instance, During the process, all special characters in the user input are removed or substituted to minimize damage from properly formatted malicious SQL queries.
Character escaping (the process of pre-cleaning user input by removing or “escaping” special characters) in visitor submissions should be enabled by default. To make this process easier, consider utilizing a WordPress form plugin that offers user input validation. As a final check before submission, you can employ a CAPTCHA to stop bots from attempting injection.
#8. Search Engine Optimization (SEO) Spam
SEO spam is a type of spamming technique that involves injecting unwanted content into a website to manipulate search engine rankings. This can be achieved by adding hidden links or text or adding irrelevant keywords.
Why Are WordPress Sites Vulnerable?
As with the other WordPress security issues discussed in this article, outdated plugins, themes, and core software make WordPress sites vulnerable to these attacks.
Once your website gets compromised as a result of successful brute-force attacks or similar challenges, SEO spam attacks are easy to deploy.
These hacks are specifically riskier because it is difficult to spot them. Hackers frequently wait a while before modifying website content to avoid detection.
You should note that spammy keyword-focused changes are usually added to high-ranking pages. During the process of making these changes, hackers add cloaked keywords, like “cheap Chanel bags,” so that the changes remain undetected on the front-end.
How Can You Fix This?
When fixing an SEO Spam attack, you should first realize that these attacks occur because hackers have gained access to your website’s backend.
So to prevent these attacks, you should follow the fixes and preventive measures for preventing unauthorized access to your website.
Next, you should use a WordPress security plugin to scan for malware as an additional security option.
If you’re determined to identify these attacks, start by carefully monitoring your website analytics data and note any abrupt changes in SERP positions or unexpected increases in site traffic. Next, carefully go through the identified pages to find out and eliminate inserted keywords.
If you are familiar with website code, you can search through the highly ranked pages that appear affected and try to spot the keywords.
Regardless of what approach you apply, it’s critical to identify and remove the insertions as soon as possible because SEO crawlers may penalize your site for using spammy techniques.
#9. Cross-Site Scripting
Cross-site scripting (XSS) is a set of attacks where an attacker inserts malicious code into a website, which can then be executed by other users who visit the site. This can result in data theft or modification, as well as other damaging activities.
Why Are WordPress Sites Vulnerable?
Again, the problem here is compromised WordPress plugins and themes. An attacker can take advantage of an out-of-date or carelessly maintained plugin on your website to access the files that control your website’s front-end.
XSS attacks can get serious and result in account impersonation, loading data from other websites, and further use of your website as part of a larger attack.
How Can You Fix This?
The best fix for XSS attacks is to close off as many security loopholes on your website. This ensures that attackers can find no vulnerabilities to exploit and insert malicious code into your website.
Be wary of adding or installing third-party software, especially plugins from unknown sources.
If you haven’t already, set up a Web Application Firewall (WAF), which examines traffic coming to your website and stops unauthorized users from accessing your system from external networks.
A WAF is also a great tool for protecting against similar attacks, such as SQL injections.
#10. Denial-of-Service Attacks
A denial-of-service (DoS) attack is a type of attack where an attacker floods a website with traffic or requests, causing it to become unresponsive or crash. This can result in a loss of service and revenue for the website owner.
Why Are WordPress Sites Vulnerable?
During a DoS attack, the attacker used automated bots and traffic generation scripts to send a large number of requests to the website. Since the server hosting the WordPress website dedicates a small volume of resources to processing a request, the large volume of requests quickly overwhelms the server.
As a result, the server crashes, and the website becomes inaccessible to the visitors. You can probably guess the loss this outage causes to the business’s reputation and revenue.
How Can You Fix This?
Secure WordPress hosting is the best defense against DoS/DDoS attacks. You should harden the security offered by these hosting solutions by installing a WordPress security plugin.
If you’re running a critical WordPress website or an eCommerce store, you should look into bare metal hosting that delivers a highly secure hosting platform for your website. Additionally, these hosting providers can deploy DDoS attack protection by limiting or blocking traffic coming in from suspicious sources.
#11. Phishing
Phishing is a category of cybercrimes that uses social engineering tactics to trick victims into taking actions such as sending money or giving out personal information. Phishing attacks are usually executed via electronic communication, such as emails, texts, or websites.
Usually, victims receive links that pretend to lead to reliable websites and portals. The victim enters sensitive information into the forms on these links. Often, victims don’t realize that they are being targeted and only realize the truth after they see credit card charges or their fake identities being used online.
Why Are WordPress Sites Vulnerable?
While you may not use your WordPress website for phishing attacks, chances are that visitors to your website may become victims of these attacks by clicking on cloaked links on your website.
Usually, phishing attacks are the next stage of unauthorized website access attacks. Once the attackers gain access to your pages, they can place links leading to pages involved in phishing attacks. Alternatively, hackers can place these links in the comment section of your website, along with persuasive comments about the benefits of visiting these links.
Since visitors trust your website, they click these fishy links without hesitation. This is the start of the phishing attack that usually happens outside of your website.
How Can You Fix This?
It goes without saying that protecting your website against unauthorized access is the best defense against phishing attacks directed at your website visitors.
You should also carry out frequent SEO audits where all the links on your website are evaluated for relevancy. It is always advisable to remove any fishy-looking links immediately.
Adding a bot protection measure such as reCAPTCHA to deter bots from adding comments to your blog posts. In all cases, manually review comments with links to ensure a clean comments section.
#12. Supply Chain Attacks
Supply chain attacks are the class of attacks that target the supply chain or the stack of tools used to develop, test, and distribute software. In a supply chain attack, the attackers take control of a reliable software provider or vendor and then use that confidence to spread malicious malware to the supplier’s consumers or clients.
Why Are WordPress Sites Vulnerable?
A supply chain attack is when a malicious user targets a third-party vendor or service provider that is used by a large user base. Usually, the attackers contaminate product code with malware that gets pushed to the users in the upcoming updates.
WordPress websites are especially vulnerable to supply chain attacks because they use a lot of third-party components.
Imagine the damage a piece of malware can cause if it gets included in the next update of a popular plugin.
How Can You Fix This?
Fortunately, supply chain attacks are frequently stopped in their tracks because the WordPress community actively seeks out these phony plugins and themes and swiftly bans them. However, if one manages to slip between the cracks, adding security plugins that periodically scan your website will rapidly reveal any flaws.
As an additional security precaution, always back up your website before installing a plugin. So, if things go wrong, you can easily recover your website by reverting to the most recent backup point.
#13. Hotlinking
In a hotlinking scenario, an external website places a direct link to an asset hosted on your server.
This usually happens when another website places a direct (hot) link to an image that is hosted on your server. Now every time a user on that website clicks the links, a request is sent to your server.
Why Are WordPress Sites Vulnerable?
Since hotlinking makes unauthorized use of the bandwidth and resources of the original website (yours in this case), it might be considered a kind of content theft. The performance of the original website may suffer as a result, and the website owner (that would be you) may incur additional expenses as a result.
Many website owners create hotlinks unintentionally by adding a direct link to an asset hosted on another server. This wastes the server resources (especially bandwidth) of the target server and causes performance slowdowns.
How Can You Fix This?
There are several ways to prevent hotlinkers from using your content.
A simple way is to disable right-clicking on your website. This will prevent users from copying links. However, this is a very bad move for the site’s user experience.
We highly recommend working with a CDN provider that offers hotlinking protection. This gives all the benefits of a CDN and protects your website from slowing down because of hotlinks.
For repeat offenders who do not honor your link takedown requests, you can block the IP addresses at the server level so that the hotlinks cease to work.
#14. Cross-site Request Forgery (CSRF)
A type of online application vulnerability known as cross-site request forgery (CSRF) enables an attacker to deceive a victim into taking action they did not want to take on a website or web application. When a victim is logged into a website or web application and clicks on a malicious link or goes to a malicious website, CSRF attacks frequently take place.
Why Are WordPress Sites Vulnerable?
Cross-site Request Forgery (CSRF) is when a malicious user tricks a website user into performing an action on their behalf, such as making a purchase or changing a password, without their knowledge or consent. WordPress sites can be vulnerable to CSRF attacks if they do not have proper security measures in place.
Particularly susceptible to CSRF attacks are WordPress sites using some of the most widely used plugins. More particularly, plugins like WP Fastest Cache that employ the check_url() method are susceptible to CSRF attacks. A thorough explanation can be found on this page on plugin vulnerabilities.
How Can You Fix This?
Here are a couple of tips you can use to prevent CSRF attacks on your website:
- Never trust a plugin. Always carry out security audits that check all installed plugins and flag suspicious activities on your website.
- Any popular WordPress security plugin is a good defense against cross-site request forgery.
- Another important piece of advice for protection against CSRF is to harden your website with two-factor authentication and block file edits and PHP execution for untrusted files.
So – Is WordPress Secure If You Follow Best Practices?
At this point, you must be wondering if WordPress is a secure platform?
The answer to that question is yes – but only if you follow the best practices for WordPress security.
WordPress is generally as secure as any other piece of software. Most of the WordPress security issues occur when site owners fail to comply with the following tips for WordPress security:
Keep WordPress Up-to-date
WordPress releases security updates regularly, and keeping your website updated with the latest version of WordPress is essential to protecting your site against all forms of cyberattacks.
Use Strong Passwords
Use strong passwords that combine upper and lower-case letters, numbers, and special characters. Avoid using common passwords such as “password” or “123456”. Even when using strong passwords, change them frequently to invalidate passwords that got compromised in a data leak.
Use Two-factor Authentication
Use a two-factor authentication (2FA) plugin to add an extra layer of security to your login process. Alternatively, all popular security plugins have this feature.
Limit Login Attempts
Limit the number of login attempts to your WordPress site to prevent brute-force attacks. You can either use a dedicated rate-limiting plugin or enable the option in your preferred security plugin.
Use WordPress Security Plugins
Use security plugins such as Sucuri or Wordfence to scan your website for vulnerabilities and potential security threats.
Backup Your Website Regularly
Back up your website frequently to ensure you always have a restore archive ready in case of a security incident. You can use this archive to bring your website back online as soon as possible to minimize downtime.
By adhering to these best practices, you may greatly lower the chance of security breaches on your WordPress website.
How Can Your Hosting Provider Help Secure Your WordPress Websites?
Your hosting provider is also responsible for keeping your WordPress websites secure. However, their role is at the server level where they apply security processes to protect the hosting infrastructure from attacks that could harm your website.
Here are some ways in which your hosting provider can help in keeping your WordPress website secure:
Dedicated Server Security
A reputable hosting provider will have robust server security measures to stop unauthorized access to your website’s files and data.
Regular Updates
A competent hosting provider regularly updates the software and hardware components of their hosting infrastructure. The server maintenance teams apply recently-released security patches and software updates to make sure that your website remains protected against potential security threats.
Malware Scanning & Removal
Hosting providers offer malware scanning services that can help detect malicious code or files that may have been injected into your website. At a small additional expense, the support engineers can remove malware from your website files.
Server Firewall
Hosting providers may also offer server-level firewall protection to block suspicious incoming traffic to your website. This is an essential requirement for setting up protection against DDoS attacks.
SSL certificates
An SSL certificate is essential for encrypting data transferred between your website and the visitors. Many hosting providers offer SSL certificates as part of their hosting packages, or you can buy them from reliable vendors.
RedSwitches offer live chat, phone assistance, and hosting companies’ typical email and ticket support. Our customers receive responses in an average of 15 minutes or even less.
Conclusion
WordPress is generally a secure platform for building websites. However, it’s essential to follow best practices for WordPress security, such as keeping WordPress and its plugins up-to-date, using strong passwords and two-factor authentication, limiting login attempts, installing security plugins, and backing up your website regularly.
This blog looked into the 14 most common WordPress security issues and suggested solutions and best practices that you can implement right away. As a result, you’ll see a marked decrease in security incidents and an upward improvement in site performance.
As website owners, it’s essential that you remain vigilant and informed about the latest security threats and best practices for WordPress security to ensure your website remains secure.
FAQs
Q. Why is WordPress not secure?
Most WordPress security issues happen because site administrators disregard the best practices for using plugins and otherwise securing the site. In many instances, most of these issues can be averted by carrying out regular security assessments and fixing the reported flows in website security.
Q. How can I make WordPress website security better?
At the minimum, you should consider the following tips to minimize WordPress security issues:
- Pick a hosting option that prioritizes security at the server level.
- Install an SSL certificate to encrypt traffic on your website.
- Install a trustworthy WordPress security plugin.