Do you know that the File Transfer Protocol (FTP) was originally introduced in 1971?
Since then, the protocol has remained a mainstay of building private and public networks for sharing information and files. Even when most of the internet works on HTTPS and HTTP, FTP remains a popular option for setting up file-sharing channels.
Security is a critical consideration in setting up an FTP server. That’s why we recommend Very Secure FTP Daemon (vsftpd) to set up an FTP server in an Ubuntu environment. In fact, it is the standard FTP server option in all popular Debian and RHEL-based Linux distributions.
In this tutorial, we will show you how to set up and configure vsftpd to install Ubuntu FTP server.
Table Of Contents
Install and Configure an Ubuntu FTP Server with vsftpd
Before going into the details of installing an FTP server, let’s look at the prerequisites for the process.
The Prerequisites
- A system running a stable Ubuntu version
- A user account with root and sudo privileges
Installation Of Ubuntu FTP Server
To install the vsftpd program on Ubuntu, follow these steps.
Step #1: Update the Repository of System Packages
Start by updating the system package index by running the following command into the terminal:
# sudo apt update
Step #2: Install vsftpd on Ubuntu OS
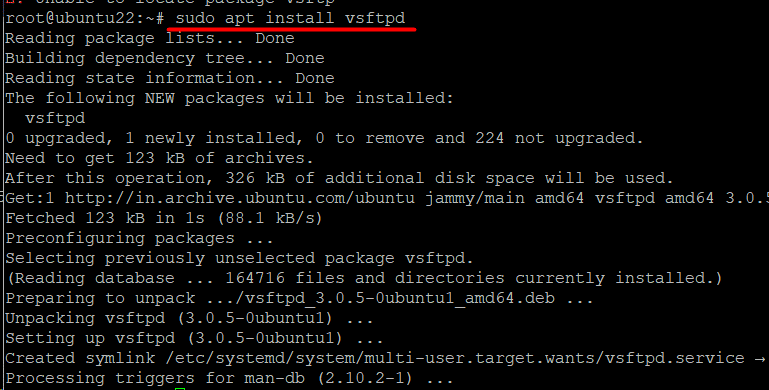
vsftpd is an open-source FTP program that you can install from the official Ubuntu package repository. Start with the following command that gets the official package and installs it on your Ubuntu system:
# sudo apt install vsftpd
Step #3: Start the vsftpd Service
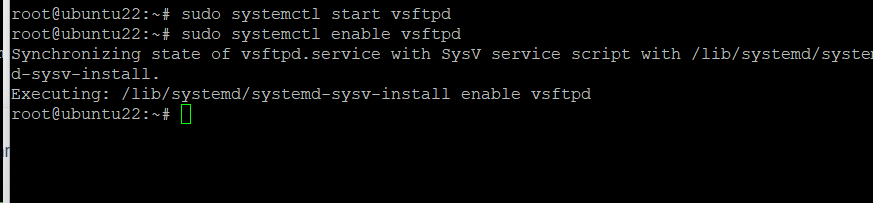
Use the following commands to start the service and set it to run automatically when the machine starts up:
# sudo systemctl start vsftpd
# sudo systemctl enable vsftpd
Step #4: Back up the Configuration Files
Make a backup copy of the configuration files before making any changes. We recommend the following version of the cp command to back up the default vsftpd configuration file:
# sudo cp /etc/vsftpd.conf /etc/vsftpd.conf_default
This command copies the vsftpd.conf file from the /etc/ directory and stores it in the same directory as vsftpd.conf_default.
Step #5 : Create an FTP User
Now that we have installed vsftpd on the system, let’s create an FTP user to demonstrate the capabilities of the FTP operation.
Important: If you want to grant an existing user FTP access, skip this step and go on to the next one.
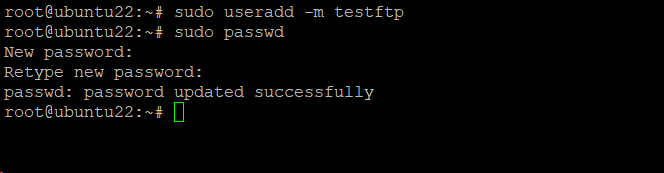
To create a new user and set the password, use the following commands:
# sudo useradd -m [username]
# sudo passwd [username]
Enter the name of the user account you wish to set up in place of [username].
After executing the second command, the system prompts you to set a password for the newly created account.
In the following screenshot, you can see that we used the above commands to add an account for a user named testftp.
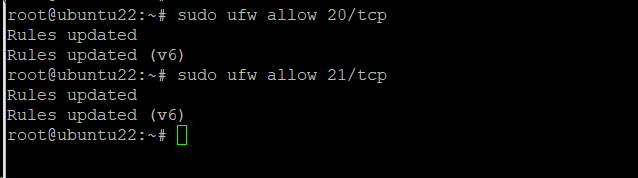
Step #6: Update the Firewall to Permit FTP Connection(s)
Since we are on an Ubuntu machine, UFW is the default firewall. This firewall is configured to restrict FTP traffic by default.
You can allow FTP traffic on ports 20 and 21 through the firewall, execute the following commands:
# sudo ufw allow 20/tcp
# sudo ufw allow 21/tcp
Important: If you have a different firewall on your Ubuntu machine, We recommend following the official documentation to grant access to ports 20 and 21.
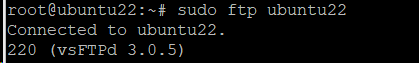
Step #7: Connect to the FTP Server
In the terminal, run the following command to connect to the FTP server:
# sudo ftp [system_name]
Change [system_name] to your system’s name (as obtained from the command line). For instance, we used # sudo ftp ubuntu22 to connect to the FTP server we created on our test machine.
Once the server is running, log in with the password and account you created in Step 5 or the account you want to use for file transfers.
Set up the vsftpd Server
Setting up the server is essential because you can adjust specific parameters to maximize efficiency, activate inactive functions, and make the server more compatible with your requirements.
Modify the Default Directory
The default directory used by the FTP server is /srv/ftp. You can change the FTP user’s home directory to further harden the system’s security.
Follow these steps to change the user’s FTP home directory.
- Use the mkdir command syntax to create a new directory:
# sudo mkdir /srv/ftp/[new_location]
Remember to replace [new_location] with the location you want for the directory.
- Now, modify the default directory that the ftp user will be logged into upon login with the following command syntax:
# sudo usermod -d /srv/ftp/[new_location] ftp
- Finally, restart the vsftpd service to implement the modifications:
# sudo systemctl restart vsftpd.service
Any files you want to make available via FTP can now be placed in either the /srv/ftp/[new_location] directory (if you modified it) or the /srv/ftp directory (if you left it unchanged).
Allow Users to Upload Files
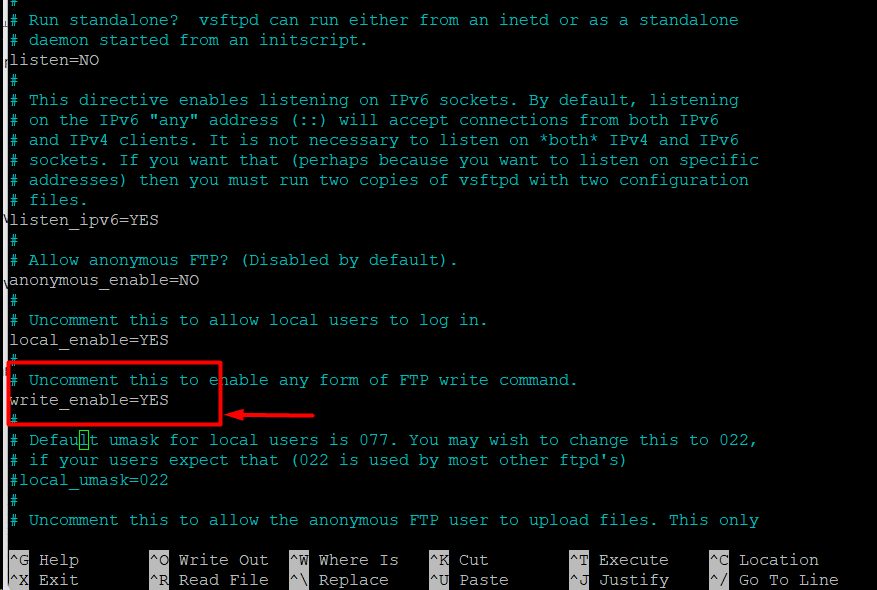
You can modify the vsftpd.conf file to allow users to upload files to the server. Note that only authenticated users will be allowed this privilege:
Start by opening the vsftpd.conf configuration file in your preferred editor. On our test system, we will open the command in Nano:
# sudo nano /etc/vsftpd.conf
Scroll down and locate the write_enable=YES entry and uncomment it (take out the # before the line):
Save the file, close it, then use the following commands to restart the FTP service:
# sudo systemctl restart vsftpd.service
Secure the FTP Server
Unprotected FTP servers are a favorite target of cyber criminals because they can yield sensitive information.
You can secure your FTP server by editing parameters in the vsftpd.conf to protect against unwanted access, possible data breaches, and system vulnerabilities.
User Access Limitation
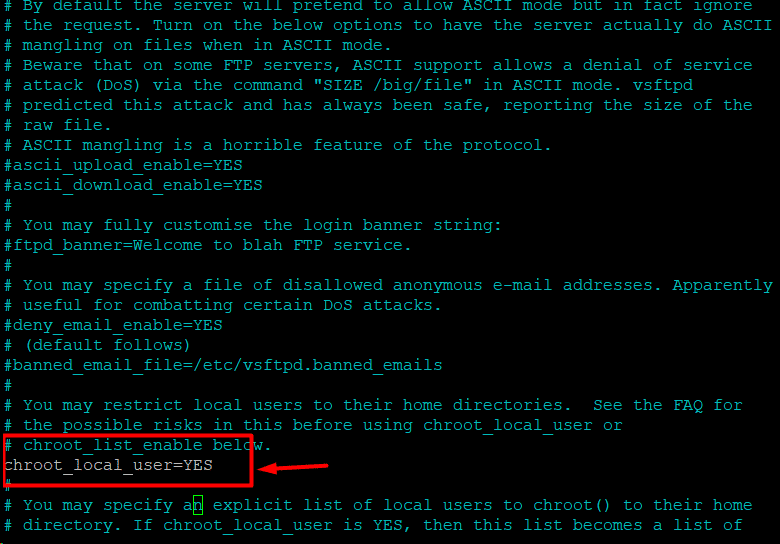
A simple way of ensuring FTP server security is to restrict users to their home directory. Implement this precaution by following these steps:
Open vsftpd.conf in your preferred text editor (we are using Nano):
# sudo nano /etc/vsftpd.conf
Remove the hash (#) symbol from the following line to uncomment it:
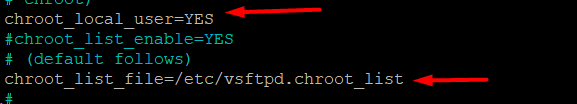
chroot_local_user=YES
Save the file to and close the editor.
Create a User List File
vsftpd can refer to a user list to determine whether a user can access (or not) the system. This list is a critical aspect of securing the FTP server. A user not on this list is restricted to their home directory.
Start by opening the /etc/vsftpd.chroot_list file in a text editor and add one user per line.
Save the file.
Next, open the vsftpd.conf file, and remove the # symbol from the following lines:
chroot_local_user=YES
chroot_list_file=/etc/vsftpd.chroot_list
Save the file.
Finally, restart the vsftpd service with the following command:
# sudo systemctl restart vsftpd.service
Conversely, the /etc/ftpusers file contains a list of users prohibited from accessing FTP. You can edit this file and add one user on each line to add users that you wish to restrict.
Encryption of Traffic with FTPS
Encrypting the communication is another way to keep your FTP server safe. FTP provides a dedicated File Transfer Protocol over SSL, or FTPS, to secure communication between the FTP server and the client.
You need to configure a shell account on the FTP server so that users can use FTPS as an extra layer of encryption.
Start by using OpenSSL to create a new certificate by running the following command:
# sudo openssl req -x509 -nodes -days 365 -newkey rsa:2048 -keyout /etc/ssl/private/vsftpd.pem -out /etc/ssl/private/vsftpd.pem
When prompted, provide the relevant information or use the default settings.
Use your preferred editor to open the vsftpd.conf file and modify the line ssl_enable=NO to ssl_enable=YES.
Following that, include the following lines in the configuration file:
rsa_cert_file=/etc/ssl/private/vsftpd.pem
rsa_private_key_file=/etc/ssl/private/vsftpd.pem
allow_anon_ssl=NO
force_local_data_ssl=YES
force_local_logins_ssl=YES
ssl_tlsv1=YES
ssl_sslv2=NO
ssl_sslv3=NO
require_ssl_reuse=NO
ssl_ciphers=HIGH
pasv_min_port=40000
pasv_max_port=50000
Save the file and exit the editor.
Finally, restart the service to apply the changes:
# sudo systemctl restart vsftpd.service
Also Read: Install Ubuntu 20.04 LTS Focal Fossa In 5 Easy Steps
Conclusion
We covered the process of installing an FTP Server on Ubuntu with vsftpd.
Users can create a strong file transfer protocol and facilitate easy data interchange within their network by using vsftpd.
RedSwitches, a dedicated hosting company with clients worldwide, can help you enhance your online presence. Unleash the promise of reliable and flawless performance for your application or website.
We offer the best dedicated server pricing and deliver instant dedicated servers, usually on the same day the order gets approved. Whether you need a dedicated servers, a traffic-friendly 10Gbps dedicated server, or a powerful bare metal server, we are your trusted hosting partner.
FAQs
Q. What is vsftpd, and why is it used for setting up an FTP server on Ubuntu?
vsftpd stands for “Very Secure FTP Daemon.” It is a lightweight and secure FTP server used on Unix-like operating systems. vsftpd is preferred for its focus on security and performance.
Q. Can I install vsftpd on other Linux distributions apart from Ubuntu?
Yes, vsftpd can be installed on various Linux distributions, although the installation steps may vary. The guide primarily focuses on Ubuntu, but the general concepts also apply to other distributions.
Q. How do I check if vsftpd runs on my Ubuntu server after installation?
You can use the command sudo service vsftpd status to check the status of the vsftpd service. If it’s running, it will show as active.
Q. What is the purpose of configuring vsftpd with a chroot jail?
Configuring vsftpd with a chroot jail restricts users to their home directories, enhancing security by limiting access to the rest of the file system.
Q. Can I configure vsftpd to allow anonymous FTP access?
Yes, vsftpd can be configured to allow anonymous FTP access. However, it is generally recommended to disable anonymous access for security reasons.
Q. How do I add new FTP users and set their home directories?
You can add new FTP users using the adduser command and set their home directories accordingly. The guide should cover user creation and home directory configuration.
Q. Is vsftpd a secure choice for FTP servers?
Yes, vsftpd is known for its security features. It includes SSL/TLS encryption options, chroot jails, and various configuration settings contributing to a secure FTP server environment.
Q. Can I customize the vsftpd configuration to suit specific requirements?
The vsftpd configuration file (/etc/vsftpd.conf) allows extensive customization. You can modify various settings to meet specific security, performance, and user access requirements.
Q. What steps should be taken to troubleshoot vsftpd-related issues?
Troubleshooting vsftpd issues involves checking logs (/var/log/vsftpd.log), verifying configurations, and ensuring that necessary ports (usually 21) are open. Detailed steps for troubleshooting should be included in the guide.
Q. Is there a way to enforce encryption (SSL/TLS) for FTP connections with vsftpd?
Yes, vsftpd supports SSL/TLS encryption. You can configure vsftpd to enforce encryption for FTP connections, providing an additional layer of security. Instructions for SSL/TLS configuration should be included in the guide.