Let’s consider a hypothetical situation involving an eCommerce website where customers can log into their accounts with a login page. The website relies on an SQL database to store critical information such as usernames and passwords.
Now, envision an individual with malicious intent who seeks to exploit a vulnerability in how the website accepts and processes user input.
The attacker initiates a SQL injection attack by adding a customized input string to the login form. A common way is to insert a string like “‘ OR ‘1’=’1′ –“into the field instead of providing a legitimate username and password. This input manipulates the executed SQL query, causing it to evaluate the condition ‘1’=’1′ as true. This bypasses the login scrutiny process, and the attacker can gain access without providing accurate login credentials.
The website’s security is compromised at this point, and the attacker can download critical information or deface the SQL database.
This is how a typical SQL injection attack scenario plays out.
Since SQL injection attacks can be devastating, prevention is often the best action. This blog is all about SQL injection prevention. We’ll discuss the types of SQL injection attacks, the best practices for SQL injection prevention, and how you can prevent SQL injection attacks.
Table Of Contents
- What Are SQL Injection Attacks?
- Types of SQL Injection Attacks
- Seven Ways To Prevent SQL Injection Attacks
- Best Applications and Site-Level Practices for SQL Injection Prevention
- RedSwitches Help You Prevent SQL Injection Attacks
- Conclusion
- FAQs
What Are SQL Injection Attacks?
SQL injection (SQLi) is a critical flaw in web security that enables attackers to manipulate the queries sent by an application to its database.
By exploiting this vulnerability, attackers can gain unauthorized access to sensitive data that would typically be inaccessible to them. This includes data from other users and other information within the application’s database. During the attack, attackers can modify or delete data, leading to temporary or permanent damage to the application’s content or functionality.
As a result, SQL injection attacks are a severe problem for any business. Successful exploitation leads to outcomes that invariably damage the operations, reputation, and revenue generation capacity.
Most importantly, when assessing the impact of an SQL injection, businesses must consider the loss of customer trust that may arise if hackers successfully steal sensitive data like phone numbers, addresses, and credit card details.
This makes SQL injection prevention a critical website security consideration. The main challenge here is the multiple ways this class of attacks can be executed. Protecting against SQL injection attacks is not a simple one-shot solution. Website builders and administrators should apply a multi-tier protection strategy covering all major attack types.
Before we go into the details of such a strategy, it is crucial to understand the types of SQL injection attacks.
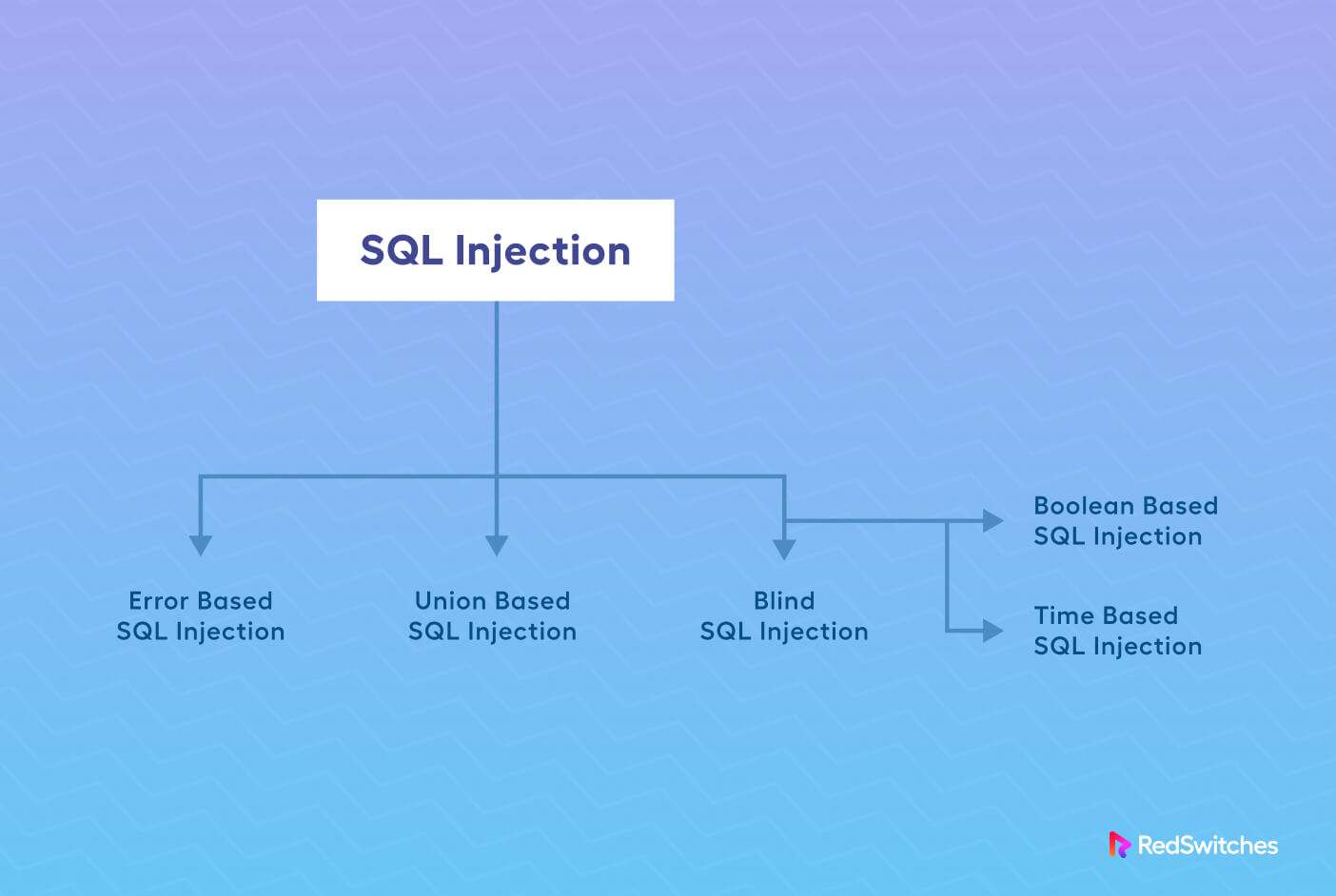
Types of SQL Injection Attacks
SQL injection attacks have remained a favorite of cyber criminals because of the several ways they can deploy the attack on the database. We’ll discuss the three most common types of these attacks to help you understand how attackers target your website.
Error-based SQL Injections
Error-based SQL injections exploit error messages generated by the database server to gather information about the database structure. An attacker can enumerate an entire database solely through error-based SQL injection techniques in certain exceptional cases.
Let’s run through an example scenario to understand this attack better:
Consider a scenario where a web application features a search functionality that users can use to search for products by their names. This application dynamically constructs an SQL query based on the user’s input and retrieves the corresponding products from the database.
Consider the following code snippet that this search function uses to get product information from the database:
$searchTerm = $_GET['search'];
// Construct the SQL query
$query = "SELECT * FROM products WHERE name = '" . $searchTerm . "'";
// Execute the query and retrieve the results
$result = mysql_query($query);
As you can see, the user’s input (stored in the variable $searchTerm) is directly merged into the SQL query (stored in the $query variable) without proper sanitization or parameterization. This lack of security measures creates a vulnerability attackers can exploit in an injection attack.
A common scenario is when the attacker enters the search term: ‘ OR 1=1; –. As a result, the SQL query in the variable is modified as follows:
SELECT * FROM products WHERE name = '' OR 1=1; --'
The injected portion ‘ OR 1=1; — is intentionally designed always to evaluate to true (1=1) and comment out the remainder of the original query (–). When executed, the modified query retrieves all records from the products table instead of retrieving the results for the intended search term.
This type of attack becomes fruitful when the web application is not suitably configured to handle and suppress database errors. In such cases, a malformed query will present a detailed error message to the attacker.
This error message unintentionally discloses information about the underlying database structure. For instance, an error message stating “Unknown column ‘password’ in ‘field list'” implies the password column exists in the PRODUCTS table. The attacker can then concentrate on this table because they know it contains sensitive information such as user passwords.
Union-Based SQL Injections
Union-based SQL injections leverage the UNION SQL operator to combine the results of multiple SELECT queries into a unified result set, which is then included in the HTTP response.
Consider a scenario where a web application provides product information based on user input. The application constructs an SQL query to fetch the relevant product data from the database.
Here’s a simplified representation of the vulnerable code:
$productID = $_GET['id'];
// Construct the SQL query
$query = "SELECT id, name, price FROM products WHERE id = " . $productID;
// Execute the query and retrieve the result
$result = mysql_query($query);
Within this code, the user’s input (stored in the variable $productID) is directly concatenated into the SQL query without undergoing proper sanitization or validation. As a result, the attacker can use this opportunity to inject SQL statement(s) into the execution process.
Now, imagine the situation where an attacker knows the existence of the database’s PRODUCTS and USERS tables.
They supply the following input for the “id” parameter:
1 UNION SELECT username, password, email FROM users.
This modifies the query as:
SELECT id, name, price FROM products WHERE id = 1 UNION SELECT username, password, email FROM users
In this particular case, the injected portion, 1 UNION SELECT username, password, and email FROM users, is appended to the original query. The intention behind this injection is to retrieve sensitive information such as usernames, passwords, and email addresses) from the USERS table.
If the union-based SQL injection proves successful, the result set will merge the results from the columns in the initial PRODUCTS table query with those obtained from the injected USERS table query. This combined result set is then included in the web application’s HTTP response.
The attacker can extract the retrieved sensitive information from the response and exploit it for their purposes, including unauthorized access to user accounts.
Preventing union-based SQL injections requires implementing secure coding practices, such as parameterized queries or prepared statements. These techniques effectively isolate user input from the structure of the SQL query. These practices ensure that the input is treated purely as data, not as executable code. This reduces the risk associated with injected queries.
Blind Boolean-Based SQL Injections
Boolean-based SQL Injection operates by submitting a SQL query to the database and manipulating the application’s response based on whether the query evaluates to TRUE or FALSE.
Consider a scenario where a web application has a login form where users can authenticate themselves by providing a username and password. The application then constructs an SQL query to verify the user’s credentials.
Here’s a simplified representation of the code vulnerable to boolean-based SQL Injection:
$username = $_POST['username'];
$password = $_POST['password'];
// Construct the SQL query
$query = "SELECT * FROM users WHERE username = '" . $username . "' AND password = '" . $password . "'";
// Execute the query and check the result
$result = mysql_query($query);
As you can see, the user’s input for the username and password fields is directly concatenated into the SQL query without prior sanitization or validation. As a result, attackers can use this input to inject a boolean-based SQL query.
For instance, an attacker submits the following input for the username field:
‘ OR 1=1 –
Now, the modified query would appear as follows:
SELECT * FROM users WHERE username = ” OR 1=1 –‘ AND password = ‘<user-provided-password>’
This injected portion is specifically designed to manipulate the query and always yields TRUE as a result.
In this case, the injected portion ‘ OR 1=1 — acts as a condition that consistently evaluates to TRUE. The double dash (–) is utilized to comment out the remainder of the original query, ensuring that the injected code does not cause syntax errors.
If the injected query evaluates to TRUE, the application may return a successful authentication response, providing the attacker with unauthorized access. On the contrary, if the query evaluates to FALSE, the application may return an error message or deny access.
By observing these two responses, the attacker can deduce the success or failure of the injection. Subsequently, the attacker can proceed to further exploit the vulnerability by changing the injected code or gathering sensitive information in the case of a successful attack.
Input sanitization and using parameterized queries are two ways to protect the application against boolean-based SQL injection. These practices separate user input from the structure of the SQL query and thus prevent the injection of malicious code. Additionally, implementing robust input validation and sanitization mechanisms helps maintain the overall integrity of user-supplied data.
Seven Ways To Prevent SQL Injection Attacks
After discussing the types of SQL attacks, let’s discuss the SQL injection prevention tactics.
As a general rule, web application developers must implement input filtering, restrict database access, and ensure ongoing maintenance and monitoring of the application and database.
Although these approaches are effective, they are primarily applicable during the development phase, as existing code is often too extensive to review line by line.
If that’s the case with you, you can opt for several open-source and commercial tools to assist development teams in identifying SQLi vulnerabilities.
We’ll discuss seven simple ways you can SQLi-proof your web application.
Strictly Implement Input Filtering
A crucial strategy for mitigating SQL injection attacks involves implementing input filtering mechanisms.
This broad set of techniques covers the validation and sanitization of user inputs before they are processed and executed as SQL queries. Developers can ensure that user-provided data is not treated as executable query code by employing effective input filtering techniques like parameterized queries and prepared statements. This significantly reduces the likelihood of SQL injection vulnerabilities.
Implement Strong Input Validation and Whitelisting
Developers should combine input filtering with equally robust input validation to prevent SQL injection attacks. Developers should establish multiple validation checks to ensure user inputs conform to the expected format and fall within the expected “safe” range.
Employing input whitelisting can be particularly powerful, as it only permits approved characters and patterns in the input areas. This validation method effectively rejects any potentially harmful input that deviates from the predefined safe criteria.
Database Code Restriction
Another fundamental protective measure is to restrict the database code itself.
This is another broad set of code-level precautions, such as NOT using dynamically constructing SQL queries by concatenating user inputs with the query string. Instead, developers should focus on implementing parameterized queries or stored procedures to minimize the instances of unauthorized SQL code manipulation.
Limit Access to the Database
Effectively controlling access to the database is critical in preventing SQL injection attacks. Developers should adhere to the principle of Least Privilege, ensuring that database users possess only the necessary permissions to perform their intended tasks. By implementing robust authentication and authorization mechanisms, developers can restrict database access to authorized users, thereby minimizing the risk of unauthorized SQL injections.
Regular Application and Database Maintenance
Consistent maintenance of both applications and databases is critical to safeguarding against SQL injection attacks. Maintenance activities include promptly applying security patches and updates to frameworks, libraries, and database systems. Outdated software components can harbor known vulnerabilities that attackers can easily exploit. Developers can significantly decrease the likelihood of SQL injection vulnerabilities by keeping all software components up to date.
Continuous Monitoring of Application Inputs and Database Communications
Monitoring plays a pivotal role in the prevention of SQL injection attacks.
Developers can identify suspicious or unexpected behavior that may indicate an ongoing SQL injection attack by diligently monitoring application inputs and database communications. We recommend setting up intrusion detection and prevention systems, and logging and analyzing database queries, to promptly identify and mitigate SQL injection attempts in (near) real-time.
Utilize Web Application Firewalls (WAFs)
Deploying a Web Application Firewall (WAF) can prove highly effective in protecting the application against SQL injection attacks. Positioned between the application server and users, a WAF scrutinizes incoming requests to identify and filter out malicious or suspicious ones. By examining the request payload and enforcing predefined security rules and patterns, WAFs can detect and block SQL injection attempts and enhance the overall application defense.
Best Applications and Site-Level Practices for SQL Injection Prevention
SQL injection attacks are a serious security challenge that can cost your business revenue and reputation.
However, the good news is that you can follow several server and application-level best practices to better structure your security measures.
Let’s start with the application-level measures first.
Application Level Best Practices
SQL injection attacks are deployed at the application level. Thus, applying the following application-level best practices for SQL injection prevention makes a lot of sense.
Input Validation and Sanitization
It’s crucial to validate and sanitize user input on the application side to safeguard against injection attacks. This involves checking the input against predefined criteria such as data types, length limits, and expected formats.
By validating input, you ensure that it meets the required constraints. Sanitization involves removing or escaping potentially malicious characters from the input to prevent them from being interpreted as executable code.
Prepared Statements and Parameterized Queries
Prepared statements, or parameterized queries, provide a powerful defense against SQL injection attacks.
With prepared statements, SQL queries are pre-compiled with placeholders for input values. The input values are then supplied separately and securely bound to the placeholders, ensuring they are treated as data and not executable code. This approach prevents attackers from injecting malicious SQL code into the queries.
Stored Procedures
Stored procedures are predefined and stored SQL code in the database. Encapsulating SQL logic within stored procedures reduces the risk of injection attacks.
Instead of dynamically constructing queries in the application code, you call the appropriate stored procedure, passing only the necessary parameters. This approach limits the attack surface by restricting direct interaction with the database and promotes code reusability and maintainability.
Use ORM Libraries
ORM (Object-Relational Mapping) libraries provide a higher-level interface to interact with databases. These libraries abstract the SQL code and facilitate secure database operations. ORM frameworks typically include parameter binding and query construction mechanisms, which inherently protect against SQL injection attacks. The ORM handles generating SQL queries, ensuring that input values are properly escaped or bound to prevent injection vulnerabilities.
Always Remember the Least Privilege Principle
When planning access and permissions for database user accounts, always remember the rule of least privilege. Each user should be assigned the minimum privileges necessary to perform their required tasks.
You mitigate the potential impact of an injection attack by limiting access rights. We recommend regular reviews and updates to user privileges to ensure they align with the application’s needs. During the review process, remember to revoke unnecessary privileges.
Apply Secure Coding Practices
Secure coding practices play a vital role in preventing injection attacks. Developers should be trained to follow guidelines and best practices for secure coding. This includes implementing input validation, output encoding, and secure data handling techniques. Additional practices you can integrate include avoiding dynamic SQL construction, using parameterized queries, and leveraging secure coding libraries and frameworks to significantly reduce the risk of injection vulnerabilities.
Handling Errors and Error Messages
Proper error handling is essential for preventing information leakage that could help attackers refine their approach.
Error messages should be generic and avoid disclosing sensitive information about the application or database. Detailed error messages should not be displayed directly to users, as they can provide valuable insights into the application’s structure and potential vulnerabilities.
Instead, log detailed error information for troubleshooting purposes while presenting user-friendly error messages to users.
Site-Level Practices
In addition to the application-level best practices, we highly recommend applying site-wide best practices that harden website security and ensure protection against a wide range of threats.
Focus on Proper Configuration
Securing your web server, application server, and database server configuration is crucial to site-level security. Follow the security best practices recommended by the vendors, such as disabling or removing unnecessary services, securing administrative interfaces, and enabling encryption (HTTPS, in particular) to protect data in transit. Regularly review and update the server configurations to maintain a secure environment.
Web Application Firewalls (WAFs)
Web Application Firewalls (WAFs) provide additional protection against injection attacks. WAFs sit between your application and the network, inspecting incoming and outgoing traffic. They analyze HTTP requests and responses in real-time, detecting and blocking suspicious requests containing potential SQL injection payloads. WAFs can be configured with predefined rules and heuristics to identify and mitigate various injection attacks.
Regular Updates and Patching
Keeping your application frameworks, libraries, and database management systems up to date is essential for addressing known vulnerabilities. Vendors regularly release security patches and updates targeting vulnerabilities, including those related to injection attacks.
Access Controls
Implement strong access controls for your application and database servers. Enforce strict authentication mechanisms, such as strong passwords, multi-factor authentication, and secure password storage. Grant access rights and permissions based on the principle of least privilege, allowing users only the minimum privileges necessary to perform their tasks. Review and audit user accounts and privileges to ensure they align with the required access levels.
Schedule Security Testing Processes
Regular security testing is crucial for identifying and mitigating vulnerabilities in your application and database configuration. These processes include vulnerability scanning, penetration testing, and code reviews.
Vulnerability scanning tools identify common security issues, while penetration testing simulates real-world attacks to discover potential injection vulnerabilities. Regular reviews of code and static code analysis tools help identify coding errors that could lead to injection vulnerabilities.
Database Auditing and Monitoring
Enable auditing and monitoring features provided by your database management system. These features record and track database activities, such as executed queries, login attempts, and access patterns. Regularly review and analyze the database logs to identify any signs of suspicious activities or attempted injection attacks. Proactive monitoring allows you to detect and respond to potential security incidents promptly.
Backup and Recovery
Implement a robust backup and recovery strategy for your SQL databases. Regularly backing up your databases ensures you have recent archives that you can use to restore the database in case of a successful injection attack, data corruption, or system failure.
We recommend storing backups securely and testing the restoration process periodically to ensure its effectiveness. Backups provide a safety net to recover data and minimize the impact of attacks or data loss incidents.
RedSwitches Help You Prevent SQL Injection Attacks
RedSwitches offers a range of services to enhance the security and performance of your online presence. For starters, we provide a secure hosting environment that helps you protect your application from SQL injection attacks and similar threats. Our support teams are on 24/7 standby to help you deal with any security crisis and safely get your web presence back online with minimum downtime.
Here’re some RedSwitches services and features that help you with SQL injection attacks.
Secure Hosting Environment: We ensure a secure hosting environment by implementing robust infrastructure and network security measures. These include the usage of firewalls, intrusion detection and prevention systems, and other related technologies that effectively safeguard against unauthorized access and attacks.
Regular Updates and Patching: Our teams diligently keep server software, including the database management system, up to date with the new/latest security patches and updates. We help mitigate the risk of SQL injection attacks by regularly addressing known vulnerabilities.
Network Security: We employ comprehensive security measures to oversee and regulate incoming and outgoing data. These measures cover traffic analysis, access control mechanisms, and advanced threat detection systems that identify and thwart suspicious activities, including attempts at SQL injection.
DDoS Mitigation: We provide robust distributed denial-of-service (DDoS) mitigation services to defend against large-scale attacks that may disrupt your services’ availability. We ensure that your infrastructure remains accessible and secure.
Backup and Disaster Recovery: All our servers come with reliable backup and disaster recovery solutions to safeguard your data and ensure quick recovery from security incidents. Regular backups and dependable recovery options are instrumental in restoring your data and minimizing the potential damage caused by such attacks.
While we provide these security measures at the infrastructure level, it is important to implement proper application-level practices to secure your applications against SQL injection attacks.
We highly recommend employing techniques such as input validation, parameterized queries, secure coding practices, and regular security testing to enhance the overall security of your databases and applications.
Conclusion
SQL injection prevention is critical to maintaining the security and integrity of SQL databases.
By understanding the tactics and risks associated with injection attacks, you can opt to deploy a range of effective methods to prevent SQL injection attacks. Implementing best practices at both the application and site levels, such as input validation, parameterized queries, secure coding, and regular security testing, significantly reduces the vulnerability to injection attacks.
Moreover, partnering with RedSwitches, a reliable web hosting and infrastructure provider, adds an extra layer of security through their secure hosting environment, network security measures, regular updates and patching, DDoS mitigation, and backup and disaster recovery solutions. By combining these practices and leveraging RedSwitches’ expertise, organizations can fortify their defenses against SQL injection attacks and safeguard their valuable data and applications.
FAQs
Q: Why is SQL injection prevention important?
A: SQL injection attacks can lead to unauthorized access, data breaches, data manipulation, and other security risks. Implementing SQL injection prevention measures is crucial to the security and integrity of databases. These measures prevent data loss or corruption, protect sensitive information, and ensure the proper functioning of applications.
Q: What are some best practices for SQL injection prevention at the application level?
A: Application-level SQL injection prevention practices include input validation through parameterized queries or prepared statements to ensure only valid data is accepted into the system. You should consider implementing secure coding practices to handle user input securely and regularly conducting security testing and code reviews to identify and fix vulnerabilities.
Q: What are some best practices for SQL injection prevention at the site or infrastructure level?
A: Site-level SQL injection prevention practices involve securing the hosting environment, regularly updating and patching server software, implementing network security measures like firewalls and intrusion detection systems, employing web application firewalls (WAFs), implementing access controls and strong authentication mechanisms, and ensuring reliable backup and disaster recovery solutions are in place.