Iptables is a powerful and flexible utility controlling firewall rules in Linux-based systems.
Administrators may implement fine-grained controls over network traffic by altering the rules of this security utility. This ensures that the traffic entering the network originated from secure sources.
For this, admins must focus on optimizing the firewall to fit the current operational requirements. The process includes knowing how to add and delete iptables rules.
In this article, we’ll cover the complexities of deleting iptables rules. You’ll get step-by-step instructions on successfully removing unused or out-of-date rules from the firewall configuration
Table Of Content
- Prerequisites
- Working with iptables Rules
- List Packet Counts
- Delete iptables Rules
- Remove All Rules in a Chain
- Flush All Chains
- Some Useful iptables Commands
- Conclusion
- FAQ’s
Let’s start with the prerequisites of working with iptables.
Prerequisites
- A Linux-powered system.
- A non-root user with sudo privileges.
- Access to the terminal or CLI
Now that you’ve fulfilled the prerequisites, let’s start working with iptables (especially deleting iptables rules).
Working with iptables Rules
We’ll now demonstrate how to optimize iptables settings and configurations to get the expected results. Note that since the data in the config files is structured differently, the results may be further filtered to only display rules for particular sequences.
List iptables Rules Based on User Specifications
Let’s start with listing the current firewall rules.
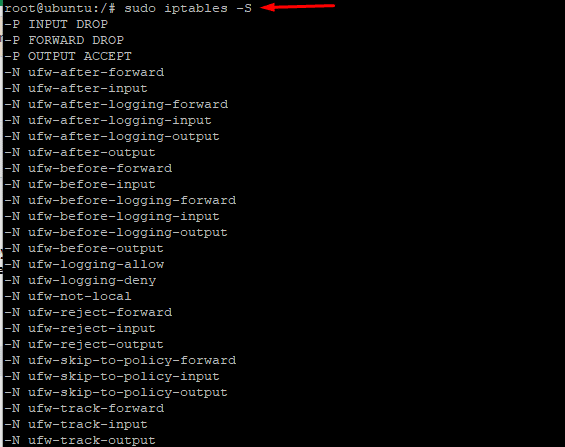
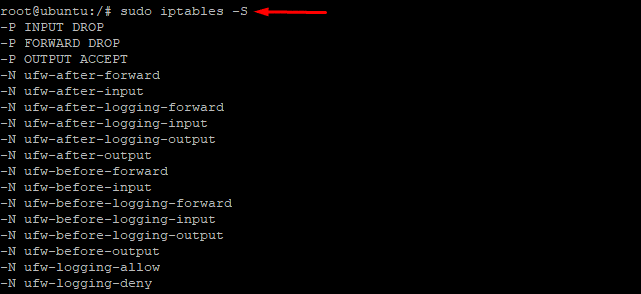
# sudo iptables -S
As you can see in the above screenshot, the rules are shown as a specification list in the output.
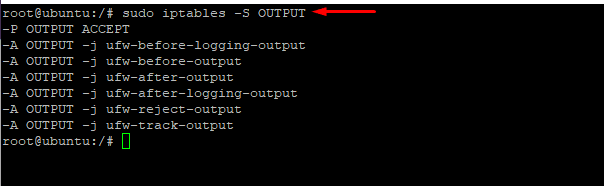
If you wish to include the name of the chains in the listing, use a slightly modified version of the command:
# sudo iptables -S OUTPUT
List Rules as a Table
Chances are you might not get all the information from the list version of the chains.
If you wish, you can use the following syntax to list all iptables rules in a table, ordered by chains:
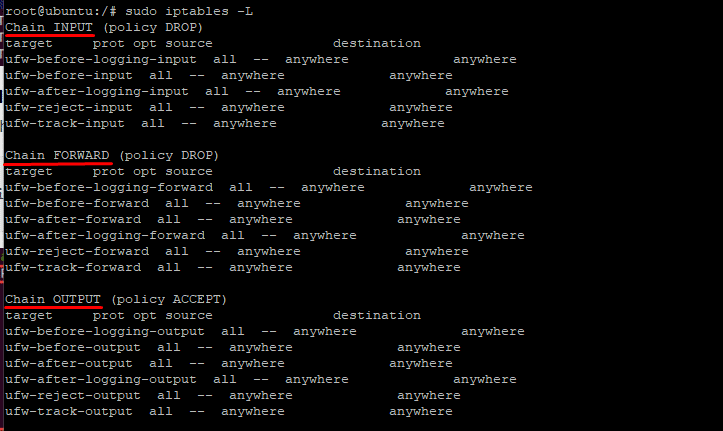
# sudo iptables -L
In the above screenshot, you can see three important chains – INPUT, FORWARD, and OUTPUT – are used to sort the rules in the output. You can print the details of a chain by using the chain’s name in the following command:
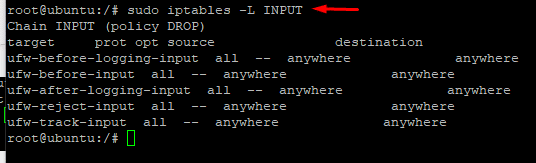
# sudo iptables -L INPUT
You can see in the following screenshot that the command prints details of the INPUT chain.
List Packet Counts
So far, you have seen chain name, default policy, target, protocol, IP option, and source and destination IP addresses as the parameters when you list the rules in a table format or via specifications.
You can get further information, including the number of packets that adhere to each rule and the overall size of the packets, by using the -L and -v parameters.
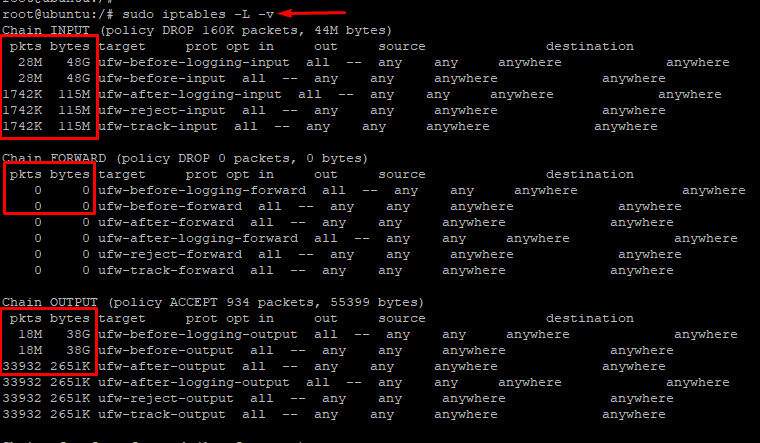
# sudo iptables -L -v
As you can see in the following screenshot, the command displays two additional columns – the number of packets and the size (in bytes) of the packets that adhere to each chain.
You can apply the -L and -v options to a single chain to produce similar results. Here’s the sample command and the output:
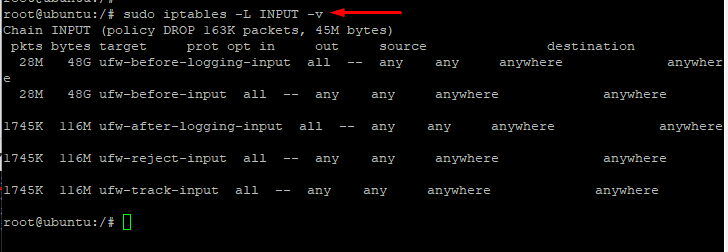
# sudo iptables -L INPUT -v
Here’s the output of the command:
Reset Packet Counts
There are times when you need to reset the package count. This often happens when you delete or change a rule. Rebooting the computer is the quickest way to reset the iptables byte counters. However, admins can’t simply reboot a server without affecting the processes and connected users.
The -Z option resets the counter without requiring server reboot. :
# sudo iptables -Z
As you can see, the command resets all chain counters, including the package size counter.
Delete iptables Rules
Now, let’s try to delete a specific rule from iptables.
For this, we’ll use the -D parameter.
If you wish to remove all the rules in the chain, try the -F option. You can also remove rules based on specifications, chains, or numbers or flush the entire chain.
Let’s see some of these commands in action:
Delete a Specific iptables Rule
As mentioned earlier, you can use the -D option with the rule specification to remove a specific rule.
However, first we recommend using the -S parameter to list down the chains. This greatly simplifies the procedure.
sudo iptables -S
All the available rules are now listed on your screen.
Select a rule to remove, and then copy and paste the specification into the following command:
# sudo iptables -D [specification]
We tried using the above command to remove the -A INPUT -j DROP rule from the list.
# sudo iptables -D INPUT -j DROP
The output in the following screenshot showed that the -A INPUT -j DROP specification and rule are no longer included in the list.
Remove Rules by Chains and Numbers:
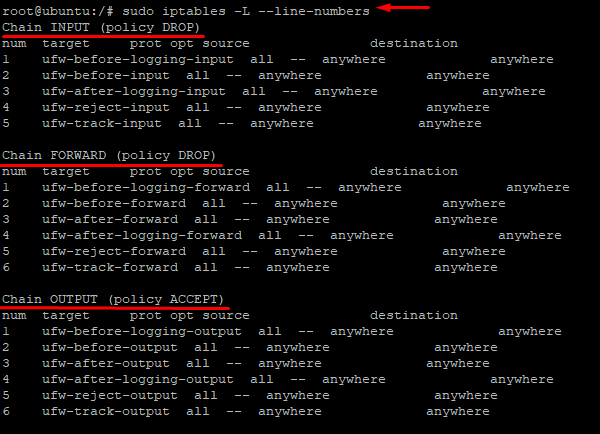
Using line numbers for chains is a simpler method of deleting rules. iptables rules are usually listed in a table format, but you can add line numbers with the –line-numbers parameter. Here the full command:
# sudo iptables -L --line-numbers
The output is pretty similar to the table output, but there’s the addition of line numbers.
Now that you can see the line numbers for the three chains – INPUT, FORWARD, and OUTPUT, you can use them to remove a rule.
For this, use the following command to specify the chain name and line number to remove a particular rule:
# sudo iptables -D [CHAIN] [LINE_NUMBER]
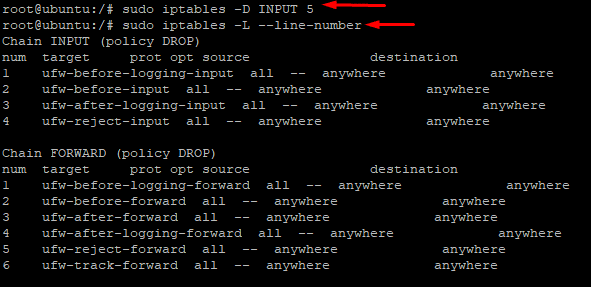
For instance, run the following command to remove the rule at line 5 from the INPUT chain:
# sudo iptables -D INPUT 5
Like most iptables commands, the -D option does not provide any output. As a result, you need to manually confirm successful execution by using the iptables -L command:
Remove All Rules in a Chain
We can use the -F option to remove all rules from a chain and essentially delete it. By default, the -F parameter without any mention of a chain removes all chains. If you
want to remove any particular chain, use -F and the chain name.
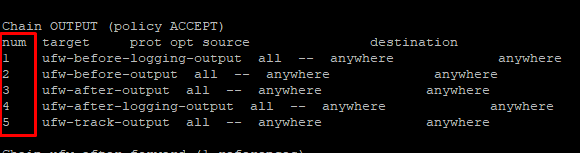
For instance, here are the rules in the OUTPUT chain:
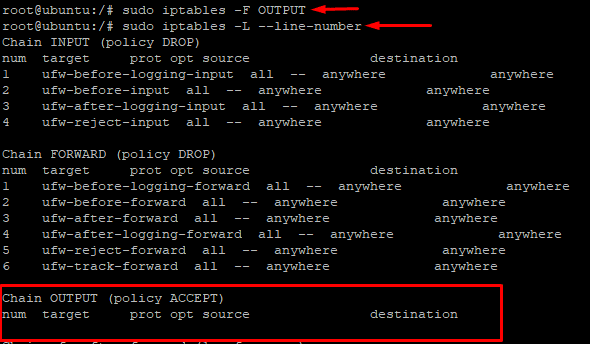
Now to delete the entire OUTPUT chain, run the following command:
# sudo iptables -F OUTPUT
Since there is no message about the success or failure of the command, you need to confirm the result using line numbers. As you can see, there are no entries under the OUTPUT chain:
Flush All Chains
The Flush option is used to turn off the firewall and remove all iptables rules by flushing all chains.
A common use of flushing the chains is to launch or restart the firewall setup. Use the following command to flush the chains:
# sudo iptables -F
Some Useful iptables Commands
Here are some other commands you can use to further optimize your iptables firewall.
Use the following commands to change the default policy for built-in chains to
ACCEPT.
# sudo iptables -P INPUT ACCEPT
# sudo iptables -P FORWARD ACCEPT
# sudo iptables -P OUTPUT ACCEPT
Use the following commands to flush all NAT and mangle tables.
# sudo iptables -t mangle -F
# sudo iptables -t nat -F
Use the following command to delete every non-default chain.
# sudo iptables -X
Keep in mind that none of these instructions produce any status report. So you need to run the following command to make sure all chains have been flushed:
# sudo iptables -L --line-numbers
Conclusion
We hope now you know how to use the iptables command-line tool to delete an iptables rule (it’s a fairly simple operation).
You can now delete unwanted rules from your iptables firewall setup by using the commands we discussed above. We strongly urge you to backup your settings before you execute any command. This often-overlooked step is a lifesaver when you misconfigure a rule and destabilize the system. Additionally, keeping the configuration in a method that will be loaded on system startup is necessary to ensure that the latest changes are applied permanently to the iptables rules.
Now, if you’re looking for a secure platform for your projects, RedSwitches offers the most flexible lineup of bare metal dedicated servers. All our servers are protected by multiple layers of Linux security utilities (such as iptables) to ensure a robust and secure platform for your projects.
FAQ’s
Q: How can I view the existing iptables rules on my system?
A: To view the current iptables rules, you can use the command: iptables -L.
Q: What is the syntax for deleting an iptables rule?
A: The syntax for deleting a specific iptables rule is iptables -D <chain> <rule_number>.
Q: How do I determine the rule number I want to delete?
A: You can use the iptables -L –line-numbers command to display the rules with their corresponding rule numbers.
Q: Can I delete multiple iptables rules at once?
A: You can delete multiple rules simultaneously by specifying their rule numbers separated by a comma.
Q: What happens if I delete a rule without specifying the chain?
A: If you omit the chain, iptables assumes the default chain, which is usually “INPUT”.
Q: Can I delete all iptables rules at once?
A: You can delete all rules by flushing the iptables configuration using the command: iptables -F.
Q: How can I delete a rule based on its specific criteria?
A: You can use the -m and -d options with appropriate parameters to match specific criteria and delete the corresponding rule.
Q: What if I accidentally delete an important rule?
A: If you accidentally delete an important rule, you may lose connectivity or compromise system security. Having a backup or a way to restore the rules is crucial.
Q: How do I back up iptables rules?
A: It’s advisable to have a backup of your current iptables configuration, especially if you’re unfamiliar with the existing rules. Additionally, make sure you understand the consequences of deleting a particular rule.
Q: How can I make changes to iptables rules permanent?
A: To change iptables rules persistent across system reboots, you must save the configuration. The exact method depends on your Linux distribution. One common approach is using the iptables-save command and redirecting the output to a file that is loaded during system startup.