Key Takeaways
- HITRUST is a comprehensive framework for managing and securing sensitive data.
- HIPAA focuses specifically on protecting healthcare information.
- Achieving HITRUST compliance involves implementing rigorous security measures and undergoing an assessment process.
- HIPAA compliance requires sticking to specific regulations outlined in HIPAA. It may vary depending on the organization’s handling of protected health information.
- Differences between HITRUST and HIPAA include their purposes, cost, certification process, flexibility, etc.
- HITRUST offers more advantages, like flexibility, tailored solutions, and comprehensive security measures.
- HIPAA is legally mandated for healthcare organizations.
- HITRUST and HIPAA aim to enhance data security and compliance, albeit with different focuses and approaches.
- Choosing between HIPAA and HITRUST depends on industry, compliance requirements, and organizational needs.
Did you know that, on average, around 1.94 healthcare data breaches of 500+ records were reported daily in 2022? HITRUST and HIPAA are two prominent names when discussing healthcare information security.
While both play an essential role in protecting health information, it’s crucial to understand that they serve varying purposes and have unique implications for healthcare organizations.
This blog aims to demystify these two standards. It will highlight the differences between HITRUST vs HIPAA, helping you understand which suits your organization’s needs best.
Table Of Contents
- Key Takeaways
- What is HITRUST?
- What is HIPAA?
- HITRUST vs HIPAA: The Differences
- HITRUST and HIPAA have Varying Purposes
- HITRUST and HIPAA Differ in Terms of Cost
- There is No HIPAA Certification
- A Third Party does Not Regularly audit HIPAA
- HITRUST is a Comprehensive Solution
- Law requires HIPAA
- HITRUST is Flexible and Tailored to Each Company
- HITRUST is More Prescriptive
- HITRUST Offers More Advantages
- HIPAA is Only for Healthcare
- HITRUST vs HIPAA: The Similarities
- HITRUST vs HIPAA: Pros and Cons
- How HIPAA and HITRUST Both Enhance Data Security and Compliance
- HITRUST vs HIPAA: Which is better?
- Conclusion – HITRUST vs HIPAA
- FAQs
What is HITRUST?
Credits: Created with Canva
Before we discuss the differences between HITRUST vs HIPAA, it is important to go over their definitions.
HITRUST (Health Information Trust Alliance) is a widely recognized security framework. It was developed to protect sensitive data, mainly in healthcare. HITRUST was established to address the growing need for data protection in the face of evolving cyber threats and regulatory requirements. It integrates and harmonizes various standards and regulatory requirements into one overaching framework. This includes HIPAA, NIST, ISO, and GDPR.
The HITRUST CSF (Common Security Framework) provides organizations with a structured approach to managing data security and compliance. It offers a certifiable framework that is both flexible and scalable. This certification is often seen as a gold standard for healthcare data protection. It assures certified organizations are committed to effectively managing data privacy and security risks.
Also Read: Azure Security Vs AWS Security: Exploring 8 Key Differences.
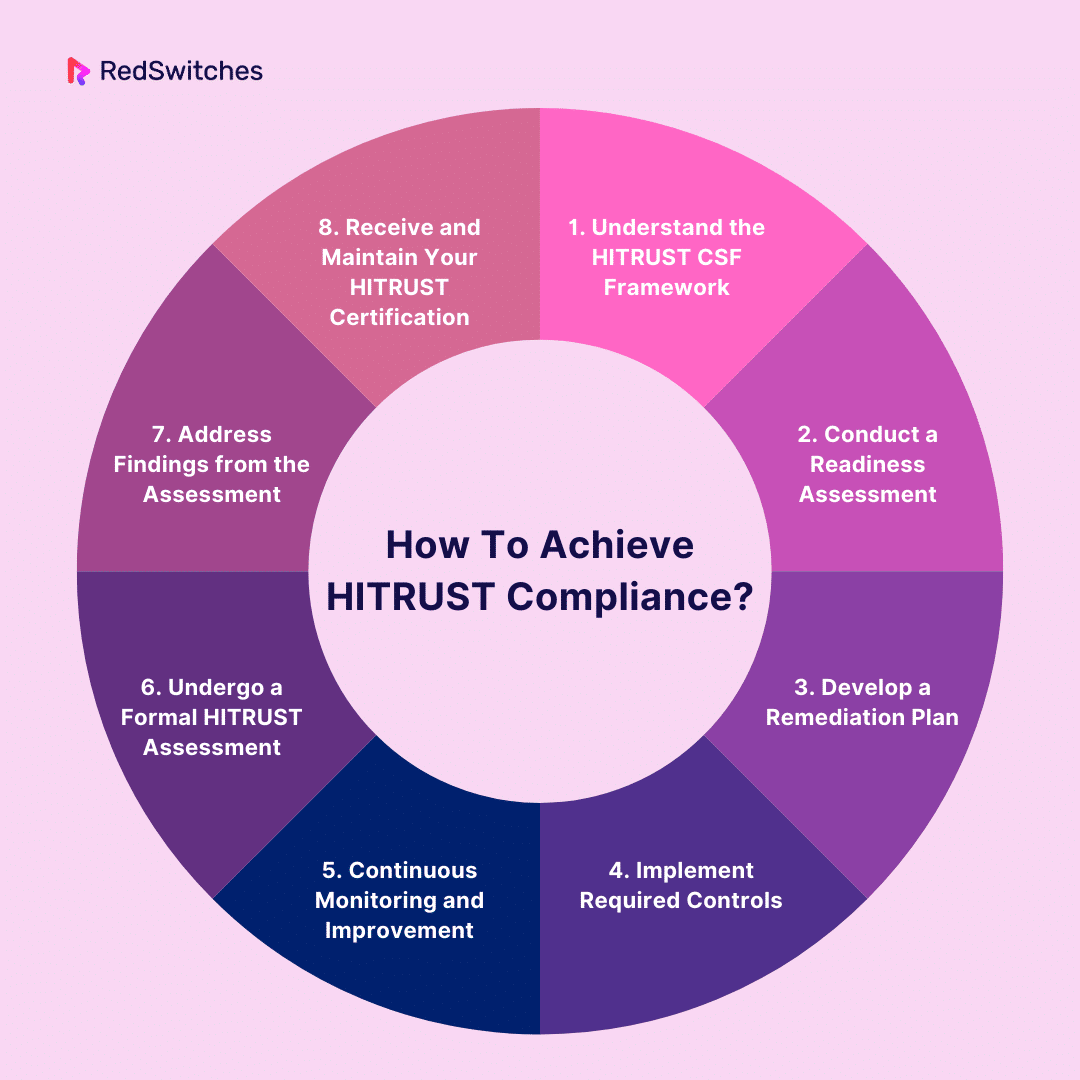
How To Achieve HITRUST Compliance?
When comparing HITRUST vs HIPAA, the two healthcare industry standards significantly vary in achieving compliance. Achieving HITRUST Compliance involves a detailed process. Below is a step-by-step guide to help you navigate the process:
1. Understand the HITRUST CSF Framework
- Familiarize Yourself with the Framework
The HITRUST CSF is a cornerstone in healthcare data security. It combines aspects from various standards to create a holistic set of security controls. Understanding how these standards intersect and apply to your organization is essential.
- Assess Your Specific Needs
The HITRUST CSF is not one-size-fits-all; it varies depending on your organization’s size, type, and the nature of the data you handle. An initial step is determining which framework parts are most relevant to your organization.
2. Conduct a Readiness Assessment
- Self-Assessment
Begin by conducting a thorough self-assessment. This involves reviewing your current security and compliance posture against the HITRUST CSF requirements. It’s a critical step in identifying any existing gaps.
- External Assessment (Optional)
While not mandatory, some organizations opt for an external expert assessment. This can objectively evaluate your current compliance state and highlight areas that might have been overlooked.
3. Develop a Remediation Plan
- Identify Gaps
Using the findings from your assessment, pinpoint specific areas that fall short of the HITRUST requirements.
- Plan Remediation
Develop a comprehensive plan to bridge these gaps. This could entail policy revisions, adopting new technologies, enhancing security infrastructure, or comprehensive employee training programs.
4. Implement Required Controls
- Security Controls
Implement the necessary controls as stipulated by the HITRUST CSF. This includes a range of measures, from technical solutions like encryption and access controls to administrative policies and physical security enhancements.
- Documentation
Carefully document all implemented controls and procedures. This documentation is crucial for assessing and maintaining an ongoing compliance record.
5. Continuous Monitoring and Improvement
- Monitor Compliance
Consistently monitor your compliance status. This involves regular checks to ensure that all HITRUST standards are continuously met.
- Continuous Improvement
The digital landscape and threat vectors are constantly evolving. Adopt a proactive stance toward continuous improvement, addressing new risks and updating compliance strategies regularly.
6. Undergo a Formal HITRUST Assessment
- Engage a HITRUST CSF Assessor
To achieve certification, you must work with an authorized HITRUST CSF Assessor. They will conduct a comprehensive formal assessment of your compliance with the HITRUST standards.
- Prepare for Assessment
Collaborate closely with the assessor. Provide them with access to all necessary documentation, systems, and personnel. This step is crucial for a thorough and accurate assessment.
7. Address Findings from the Assessment
- Review Findings
Post-assessment, thoroughly review any gaps or findings identified by the assessor.
- Remediate Issues
Swiftly address and remediate these issues. This step is critical to achieving compliance with the required standards.
8. Receive and Maintain Your HITRUST Certification
- Certification
Upon completing the assessment and addressing all findings, your organization will receive its HITRUST certification.
- Maintain Compliance
Remember, HITRUST certification is not a one-time accomplishment but an ongoing commitment. Regularly oversee and update your security measures to maintain compliance with the evolving HITRUST standards.
Data privacy and protection laws and regulations like HIPAA demand data security. Read our informative blog, ‘Cloud Data Security: 5 Important Things To Know,’ to learn more.
What is HIPAA?
Credits: Created with Canva
HIPAA (Health Insurance Portability and Accountability Act) is a US legislation introduced in 1996. It offers data privacy and security provisions for protecting medical information. The act is significant in the digital age as it addresses the use and disclosure of individuals’ health information by entities subject to the regulation. These are often called ‘covered entities.’
HIPAA was created to make it simpler to keep health insurance, safeguard the security and privacy of healthcare data. Its key aim was to help the healthcare industry control administrative expenses. It establishes national standards for electronic healthcare transactions and national identifiers for health insurance plans, providers, and employers.
HIPAA includes provisions to safeguard individuals’ health information privacy. It does so while allowing the health data flow needed to ensure high-quality health care and protect the public’s health and well-being.
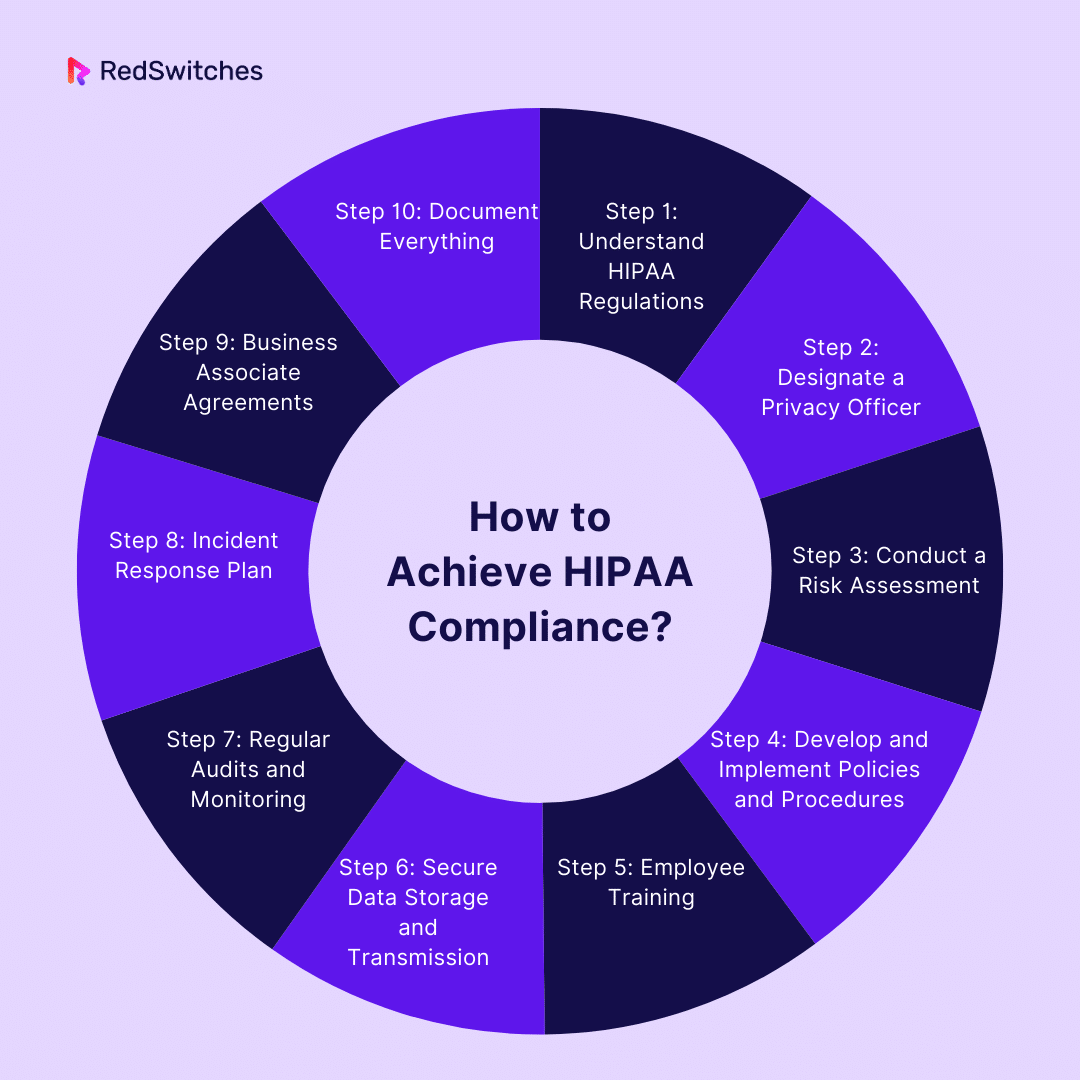
How to Achieve HIPAA Compliance?
When comparing HITRUST vs HIPAA, the two healthcare industry standards vary in terms of achieving compliance. Below is a step-by-step guide to help you navigate the process of achieving HIPAA compliance:
Step 1: Understand HIPAA Regulations
Before you begin the HIPAA compliance process, you must understand the intricacies of HIPAA regulations. This includes understanding the three core components:
Privacy Rule
The Privacy Rule establishes standards for protecting the privacy of individuals’ health information. It governs how PHI can be used and disclosed, requiring healthcare entities to obtain patient consent and provide individuals with rights over their health data.
Security Rule
The security rule focuses on the technical and physical safeguards to protect electronic PHI (ePHI). It mandates implementing security measures to prevent unauthorized access and data breaches. Examples include encryption, access controls, and risk assessments.
Breach Notification Rule
In the event of a breach, covered entities must notify affected individuals. This includes the Department of Health and Human Services (HHS), and, in some cases, the media. The rule defines the criteria and timelines for reporting breaches.
Besides these core components, it is also important to dive into the specifics of protected health information (PHI) and grasp the requirements for its safeguarding.
Safeguarding PHI involves physical, administrative, and technical safeguards. This includes access controls, employee training, encryption, and risk assessments. It helps ensure confidentiality, integrity, and availability. Compliance with these rules is essential to protect patient privacy and avoid legal consequences.
Step 2: Designate a Privacy Officer
Designating a dedicated Privacy Officer is paramount. Some of their responsibilities include:
Overseeing Compliance Efforts
The Privacy Officer is responsible for monitoring and enforcing compliance with HIPAA rules and regulations within the organization. They ensure all procedures and policies are in place and followed.
Staying Updated with Regulations
HIPAA regulations can change, and the Privacy Officer must stay current. They monitor updates, assess their impact, and make necessary adjustments to maintain compliance.
Coordinating Training Programs
The Privacy Officer organizes and conducts in-depth employee training programs. This training ensures all staff members understand their responsibilities in protecting patient data and complying with HIPAA requirements.
Step 3: Conduct a Risk Assessment
Identify potential vulnerabilities within your organization’s processes and systems. Regular risk assessments are instrumental in pinpointing areas that require improvement and facilitating the implementation of necessary safeguards.
Step 4: Develop and Implement Policies and Procedures
Craft meticulous policies and procedures comprehensively addressing PHI access, storage, and transmission. Ensuring all employees understand these protocols and stick to them is crucial.
Step 5: Employee Training
Educate all staff members on the nuances of HIPAA regulations and the utmost importance of safeguarding patient confidentiality. This training should be an ongoing, evolving process. It ensures everyone remains well-informed about the latest compliance requirements.
Step 6: Secure Data Storage and Transmission
Prioritize the security of data at rest and during transmission. Employ encryption measures to prevent unauthorized access alongside robust authentication methods and stringent access controls.
Step 7: Regular Audits and Monitoring
Implement a system of routine internal audits to evaluate compliance thoroughly. Concurrently, establish vigilant system monitoring to detect any irregularities or breaches swiftly.
Step 8: Incident Response Plan
Develop a comprehensive incident response plan to promptly and effectively address security breaches. Fulfilling the legal requirement, report any breaches to the appropriate authorities and impacted individuals.
Step 9: Business Associate Agreements
Maintain rigorous oversight over third-party vendors and partners who handle PHI. Ensure these entities sign HIPAA-compliant Business Associate Agreements (BAAs) to uphold patient data integrity.
Step 10: Document Everything
Maintain exhaustive records of all compliance endeavors, policies, training sessions, audit findings, and incident responses. These records serve as indispensable evidence of compliance during audits and evaluations.
Are you wondering why healthcare cloud security needs to be your first priority? Read our blog, ‘Why Healthcare Cloud Security Need To Prioritize In 2023‘
Now that we have discussed the individual definitions of HITRUST vs HIPAA and explored how to achieve them let’s dive into the differences between HITRUST vs HIPAA.
HITRUST vs HIPAA: The Differences
Credits: Created with Canva
Wondering what is the difference between HIPAA and HITRUST? Read on below:
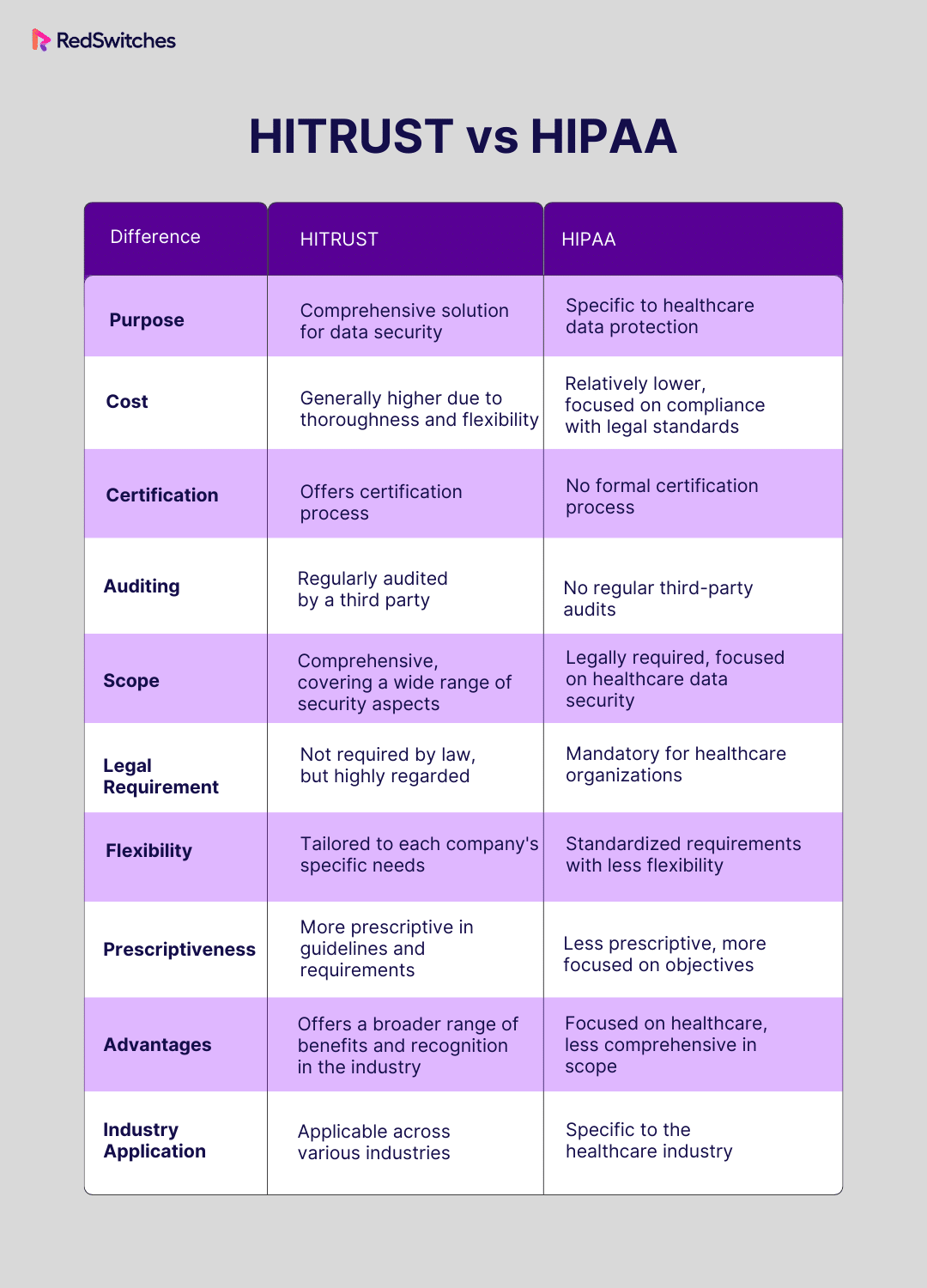
HITRUST and HIPAA have Varying Purposes
Although both are relevant to the healthcare industry, HITRUST vs HIPAA are different in terms of purpose. HITRUST is a framework for managing and safeguarding healthcare data. It mainly focuses on risk management and cybersecurity.
HIPAA is a federal law primarily addressing the privacy and security of patients’ protected health information. While both aim to enhance data security, HITRUST provides a broader, adaptable approach. Organizations often use HITRUST to meet HIPAA’s security standards and other industry-specific needs.
HITRUST and HIPAA Differ in Terms of Cost
The cost of HIPAA compliance varies based on the size and complexity of the organization. It includes expenses for implementing necessary physical, network, and process security measures, employee training, and potential auditing costs. There is no direct fee associated with being HIPAA compliant.
When comparing the cost of HITRUST vs HIPAA, the cost of obtaining HITRUST certification is typically higher. It involves an initial certification fee, annual renewal fees, and potentially significant costs related to meeting the more strict and extensive requirements of the HITRUST CSF. Organizations might also need additional technologies, consultant services, and training to meet these standards.
There is No HIPAA Certification
Another major difference between HITRUST vs HIPAA is that while HITRUST provides a certification program that allows organizations to attain HITRUST CSF Certification, HIPAA, as a regulatory framework, does not offer a certification program.
Instead, organizations must assess their compliance through self-assessment and undergo audits to ensure compliance with HIPAA regulations. This distinction shows HITRUST’s proactive approach to certification. It also highlights its role in boosting healthcare data security practices.
A Third Party does Not Regularly audit HIPAA
HIPAA is a federal law that creates standards for protecting and confidential handling of protected health information. One key aspect of HIPAA is that it does not mandate regular third-party audits. Instead, HIPAA compliance is mainly self-regulated, with occasional audits conducted by the OCR.
Organizations are responsible for ensuring their compliance through internal audits and assessments. However, a formal investigation may be initiated in case of a breach or complaint, leading to significant penalties if non-compliance is discovered.
HITRUST is a Comprehensive Solution
HITRUST offers an extensive framework integrating various standards and regulatory requirements, including HIPAA. Unlike HIPAA, HITRUST provides a certifiable framework that organizations can use to show their compliance with various security and privacy standards. It involves a rigorous third-party audit process that ensures continuous health information compliance and security.
The HITRUST CSF (Common Security Framework) is designed to protect sensitive information more robustly. It focuses on a broader range of risks and compliance requirements. This makes HITRUST a more extensive solution for organizations looking to ensure the highest data protection and compliance levels.
Law requires HIPAA
HIPAA is a federal law enacted in the United States in 1996. It sets standards for protecting sensitive patient health data from being shared without the patient’s consent or knowledge. HIPAA compliance is mandatory for all healthcare clearinghouses, providers, health plans, and business associates to these entities in the US.
It establishes requirements for using, disclosing, and safeguarding protected health information (PHI). Non-compliance with HIPAA can result in significant legal and financial penalties.
HITRUST is Flexible and Tailored to Each Company
Another key distinction between HITRUST vs HIPAA is that HITRUST offers a more flexible framework than HIPAA. This flexibility allows HITRUST to be tailored to each company’s specific needs. It provides a risk management framework that can adapt to any organization’s size.
Whether a company is a small healthcare provider or a large health system, the HITRUST framework can be adjusted to fit its unique environment and risk factors. It incorporates elements from various compliance frameworks. This adds additional layers of security and data protection protocols.
HITRUST is More Prescriptive
Unlike HIPAA, HITRUST provides a more prescriptive set of controls and benchmarks. HITRUST’s Common Security Framework (CSF) includes specific, detailed requirements that organizations must meet.
These requirements are based on the type of data handled and various risk factors, including organizational, system, and regulatory aspects. By having more detailed guidelines, HITRUST helps organizations implement concrete and measurable security controls. This prescriptive nature makes it easier for companies to address all data security and compliance aspects. Thus lowers the likelihood of gaps in their security protocols.
HITRUST Offers More Advantages
HITRUST offers a more robust and detailed approach to managing data security and compliance. HITRUST integrates a variety of standards. This includes HIPAA, NIST, ISO, and others, into one overarching framework. This integration allows for a more comprehensive risk management process. It makes it advantageous for organizations looking to ensure the highest data protection level.
The HITRUST CSF is particularly beneficial for organizations that handle sensitive health information. It offers a flexible and scalable framework that can be adapted to the size and complexity of an organization. Small clinics and large healthcare systems can implement HITRUST to enhance their security posture. Obtaining HITRUST certification can give an organization a competitive edge. It shows a serious commitment to maintaining high data security and privacy standards.
HIPAA is Only for Healthcare
HIPAA is a set of regulations designed to protect patient health information in the United States. It establishes national standards for protecting individual medical records and other personal health information. HIPAA is mandatory for:
- Healthcare providers.
- Health plans.
- Healthcare clearinghouses.
- Business associates of the above entities.
The primary focus of HIPAA is on the privacy and security of health information. It sets rules for how health information should be handled and shared. This ensures that patient data is kept confidential and secure. HIPAA provides a critical foundation for protecting patient information. However, it does not include the many security and privacy practices HITRUST covers.
HIPAA is more narrowly focused on healthcare entities and does not offer the same comprehensive framework as HITRUST. This can be applied to a broader range of industries dealing with health information.
Also Read: Top 10 Cybersecurity Frameworks To Reduce Cyber Risk.
Here’s a quick summary of all the differences mentioned above:
HITRUST vs HIPAA: The Similarities
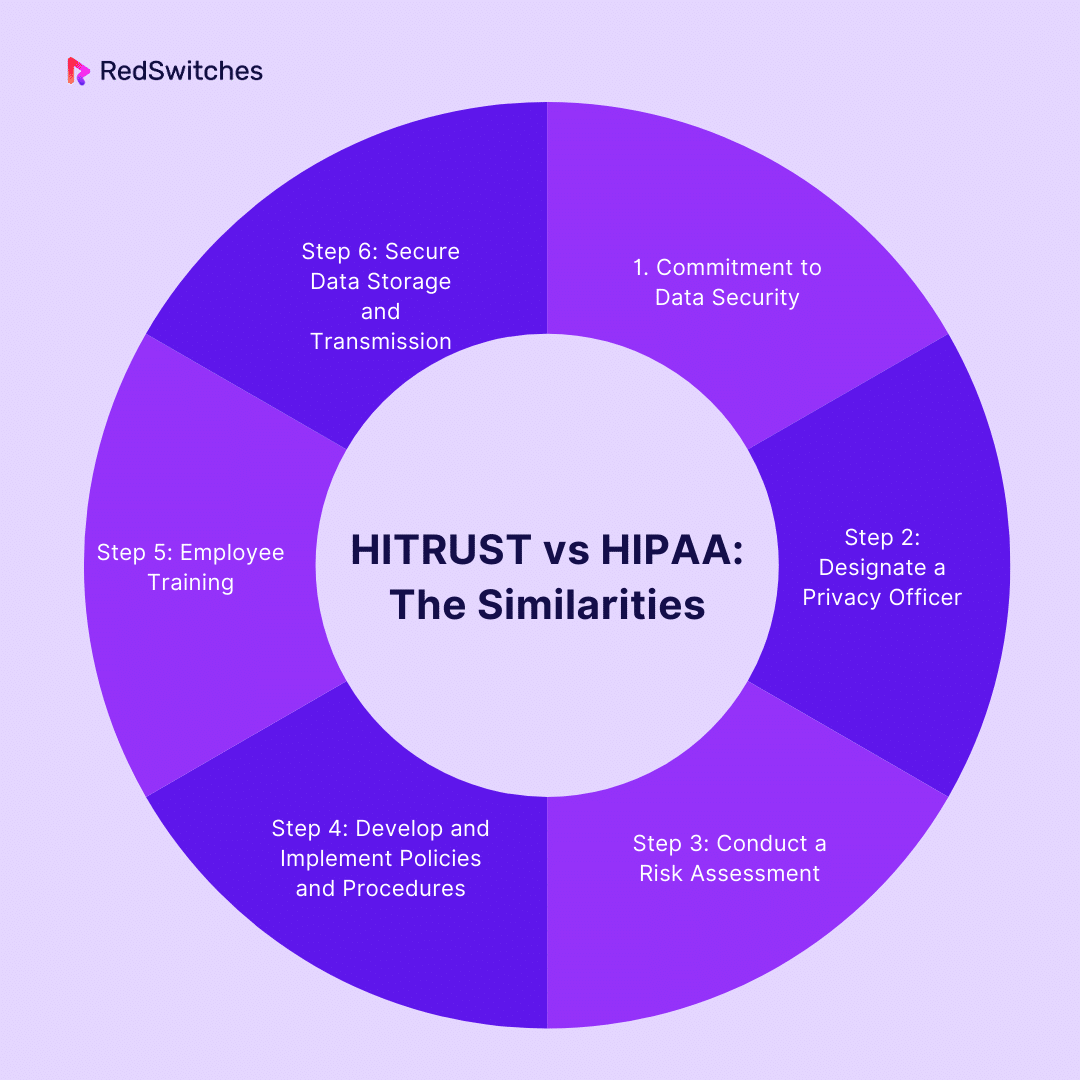
Although there are several differences between HITRUST vs HIPAA, they are also similar in several ways, including:
Commitment to Data Security
HITRUST and HIPAA are fundamentally dedicated to upholding the security and confidentiality of healthcare data. They recognize the critical need to protect patient information and reduce the risk of data breaches, ensuring that healthcare organizations prioritize data security as a fundamental principle.
Protection of Patient Privacy
As a U.S. federal law, HIPAA sets stringent standards for safeguarding patients’ privacy rights. HITRUST incorporates these privacy requirements. Both frameworks emphasize the importance of obtaining patient consent, restricting the disclosure of sensitive medical information, and respecting the sanctity of patient privacy. This ensures that patient confidentiality remains a top priority in healthcare settings.
Risk Assessment and Management
HITRUST and HIPAA stress the significance of conducting detailed risk assessments. Organizations under both frameworks must identify potential threats and vulnerabilities to their healthcare data systems. They must implement risk management strategies to mitigate these risks effectively.
Policies and Procedures
Organizations are obligated to establish and document policies and procedures related to data security and privacy to achieve compliance with HITRUST and HIPAA. These policies cover data access control, employee training, incident response, and more.
Business Associate Agreements
Recognizing the important role played by third-party service providers (business associates) in healthcare data processing, HITRUST and HIPAA necessitate the formation of formal agreements with these entities. These agreements serve as vital safeguards. They ensure patient data’s secure and confidential handling, reinforcing the commitment to data security and privacy.
Ongoing Compliance Monitoring
HITRUST and HIPAA emphasize the importance of continuous compliance monitoring. Regular assessments and audits are conducted to verify that organizations adhere to the established standards and regulations.
Also Read: Data Privacy Vs Data Security: Data Protection Guide 2024.
HITRUST vs HIPAA: Pros and Cons
Credits: Created with Canva,
Understanding the pros and cons of HITRUST vs HIPAA can offer helpful insight into which is better for your requirements. Below are the pros and cons of HITRUST vs HIPAA:
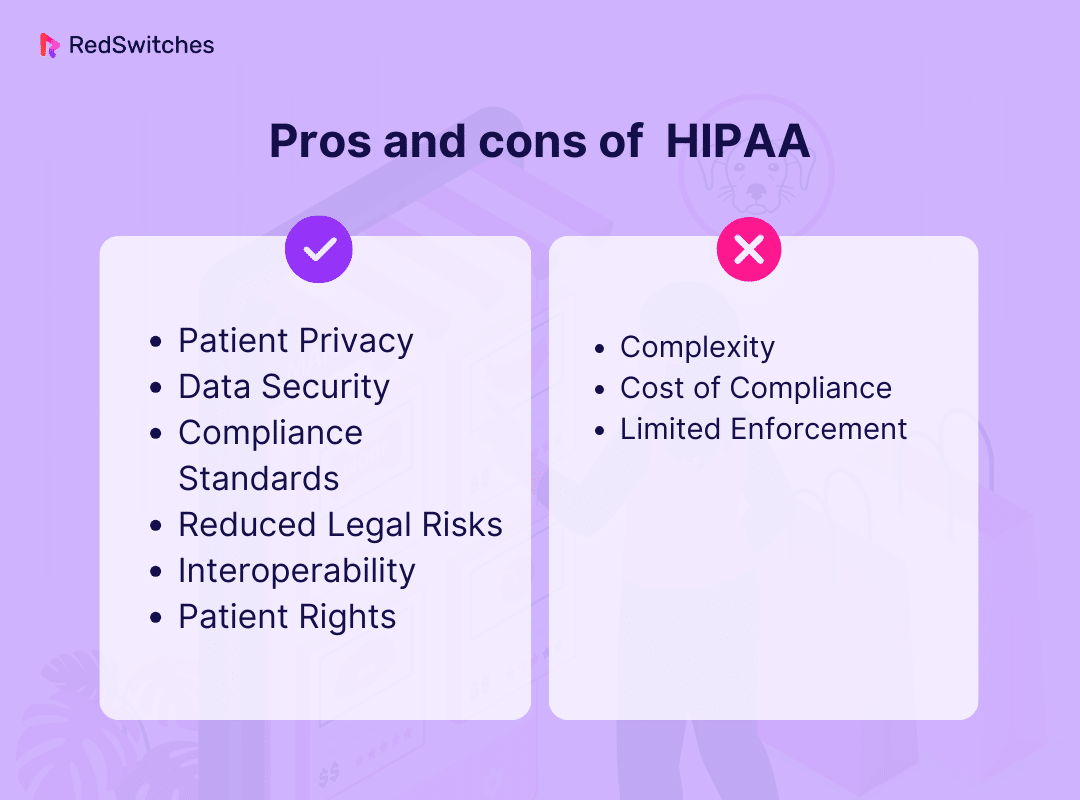
HIPAA Pros
Patient Privacy
HIPAA ensures the confidentiality of patient information. This helps offer patients peace of mind and fosters trust between healthcare providers and patients.
Data Security
HIPAA mandates robust security measures, safeguarding electronic health records (EHRs) against unauthorized access and breaches.
Compliance Standards
HIPAA has implemented clear guidelines to make implementing compliance measures easier for healthcare organizations.
Reduced Legal Risks
Compliance with HIPAA reduces the risk of legal actions and penalties associated with data breaches.
Interoperability
HIPAA promotes interoperability. It enables the exchange of patient data among authorized entities for improved care coordination.
Patient Rights
HIPAA empowers patients by allowing them to access and control their health information.
Industry Standard
HIPAA has become an industry standard. It can help enhance the reputation of compliant healthcare organizations.
HIPAA Cons
Complexity
HIPAA regulations can be complex and challenging to interpret. This can lead to potential confusion and compliance issues for healthcare organizations.
Cost of Compliance
Implementing HIPAA-compliant measures can be expensive. This is especially true for small healthcare providers who may struggle financially.
Limited Enforcement
Some critics argue that HIPAA lacks strong enforcement mechanisms. This can result in inconsistent compliance and data breaches going undetected.
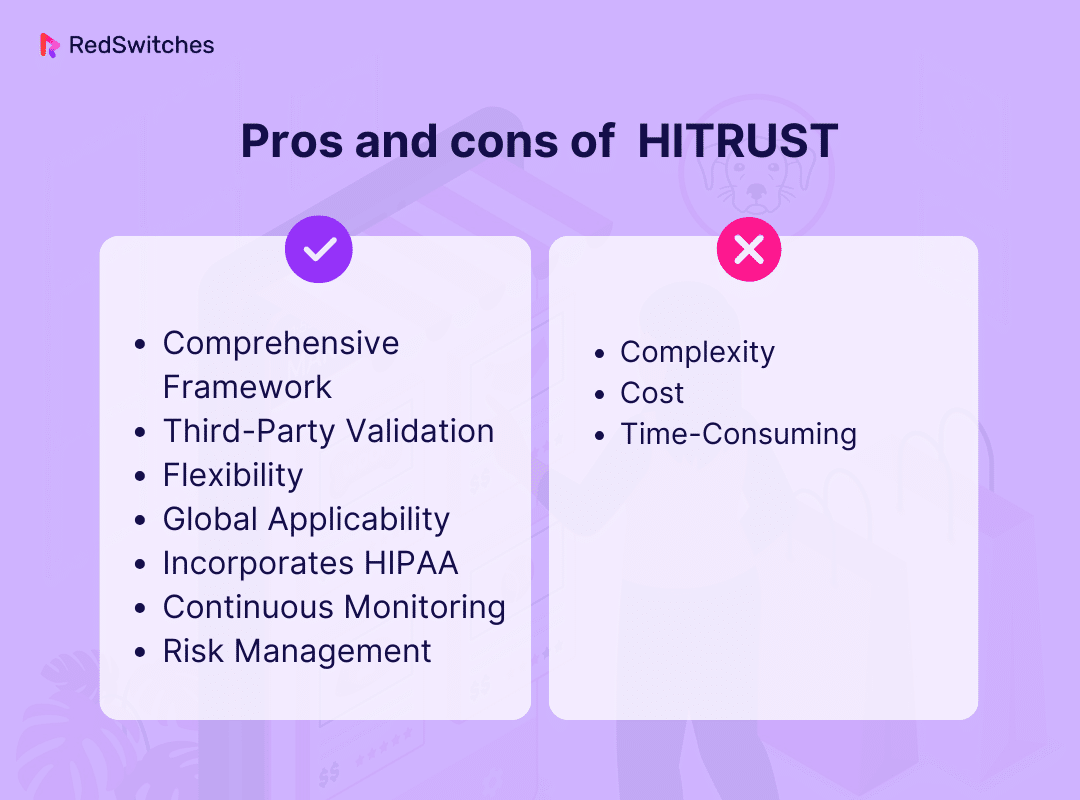
HITRUST Pros
Comprehensive Framework
HITRUST provides a detailed framework. It covers data security, risk management, and compliance with multiple regulations.
Third-Party Validation
HITRUST certification involves third-party assessments. This adds an extra layer of credibility and trust to them.
Flexibility
It allows organizations to tailor controls to their needs, accommodating various healthcare entities.
Global Applicability
HITRUST is recognized internationally. This makes it suitable for healthcare organizations with a global presence.
Incorporates HIPAA
HITRUST incorporates HIPAA requirements, ensuring compliance with this crucial regulation.
Continuous Monitoring
It promotes continuous monitoring and updates to address evolving security threats. This ensures optimal protection of sensitive healthcare data.
Risk Management
HITRUST emphasizes risk management. It helps organizations proactively address security vulnerabilities and threats.
HITRUST Cons
Complexity
HITRUST is known for its complexity and rigorous requirements. This makes the implementation process challenging and resource-intensive.
Cost
Achieving HITRUST compliance often comes with significant financial costs. This includes fees for assessments, audits, and ongoing maintenance.
Time-Consuming
Obtaining HITRUST certification can be time-consuming. It diverts resources and focus from other critical healthcare initiatives.
Also Read: What Is Healthcare In Cloud Computing.
How HIPAA and HITRUST Both Enhance Data Security and Compliance
Credits: FreePik
Lets discuss how HIPAA and HITRUST work together to safeguard sensitive health information.
HIPAA: The Cornerstone of Patient Data Privacy and Security
HIPAA sets the standard for safeguarding sensitive patient data in the US. It applies to all entities that handle health information. It mandates them to ensure patient data’s confidentiality, integrity, and availability. HIPAA’s Privacy Rule and Security Rule are its key components.
The Privacy Rule focuses on individuals’ rights over their health information. The Security Rule sets standards for securing electronic protected health information (ePHI).
HITRUST: Bolstering Security Through Comprehensive Frameworks
HITRUST is not a government-mandated regulation but a privately-held certification. It integrates various standards, including HIPAA, to provide a comprehensive framework for data security.
HITRUST CSF (Common Security Framework) is tailored to the healthcare industry. It incorporates globally recognized standards. His includes ISO 27001, NIST, PCI, and COBIT. This makes it more extensive than HIPAA, covering extensive security and privacy controls.
Complementary Roles in Enhancing Data Security and Compliance
HIPAA lays down the legal requirements for protecting health information. It is often criticized for being too general and not providing specific guidance on achieving compliance. This is where HITRUST steps in. It offers a detailed set of controls. This helps organizations implement the safeguards required by HIPAA in a more structured manner.
Organizations that achieve HITRUST certification are often considered to have met or exceeded the requirements of HIPAA. This is because HITRUST incorporates HIPAA’s mandates and aligns them with other industry standards. It offers a more robust and unified approach to data security and compliance.
Mitigating Risks and Building Trust
In an era where data breaches are increasingly common, HIPAA and HITRUST work together to mitigate risks. HIPAA sets the legal framework. It ensures organizations understand their obligations to protect patient data. HITRUST then provides the tools and guidance to implement these obligations effectively.
This dual approach enhances data security and builds trust among patients. It is especially great for targeting patients more concerned about their health information security.
HIPAA and HITRUST: A Synergistic Approach to Healthcare Data Security
HIPAA and HITRUST provide a synergistic approach to healthcare data security and compliance. While HIPAA establishes the legal groundwork, HITRUST offers a framework to achieve and exceed those standards.
This combination ensures that healthcare organizations are better equipped to protect sensitive health information. It upholds the trust and confidence of patients and stakeholders in the healthcare system.
HITRUST vs HIPAA: Which is better?
Credits: FreePik
Are you still contemplating which is better between HITRUST vs HIPAA? Consider the factors below for well-informed decision-making:
HIPAA
- Legal Requirement
HIPAA is a federal law in the United States. It is a key compliance requirement for covered entities and business associates dealing with PHI.
- Focus
It aims to protect patient health information privacy and set standards for ePHI security.
- Breadth
HIPAA provides a broad framework for privacy and security. It is often criticized for being vague regarding specific implementation guidance.
- Enforcement
Non-compliance with HIPAA can result in significant legal penalties and fines.
HITRUST
- Certification Framework
HITRUST is not a law but a voluntary certification based on the Common Security Framework (CSF). It’s a privately managed certification that integrates elements from various standards, including HIPAA.
- Comprehensiveness
HITRUST CSF is more prescriptive and detailed. It offers specific guidance for organizations to follow.
- Adaptability
It incorporates elements from other frameworks and standards. This makes it a more comprehensive and flexible approach to data security.
- Recognition
While not legally required, HITRUST certification is highly regarded in the healthcare industry. It servers as a symbol of high data security and compliance standards.
Which is Better?
- Context-Dependent
The choice between HITRUST vs HIPAA is not a matter of which is better but what is most appropriate for your organization’s specific needs. HIPAA is mandatory for certain entities. HITRUST is a voluntary certification demonstrating a higher level of commitment to data security.
- Complementary Nature
Many organizations view compliance with HIPAA as the minimum legal requirement. They pursue HITRUST certification to enhance their security posture. HITRUST also helps show its commitment to protecting health information.
- Industry Recognition
HITRUST certification is often seen as a gold standard in the healthcare sector. Hence, achieving it can provide a competitive edge. However, it does not replace the legal requirement to comply with HIPAA.
Conclusion-HITRUST vs HIPAA
When compared, HITRUST vs HIPAA share the goal of enhancing health information’s security and privacy. However, they approach this objective in different ways.
HIPAA sets the federal standard for protecting patient health information. HITRUST offers a comprehensive framework that integrates various standards and regulations. Understanding these differences is critical for healthcare organizations. It helps ensure they comply with legal requirements and adopt the best practices for data security.
Considering a reliable hosting solution is critical. This is even more important for organizations looking to enhance their data security and ensure compliance. RedSwitches offers secure hosting services that align with HIPAA and HITRUST requirements. We can help ensure your patient data is always protected.
Visit our site to learn how we can support your organization’s compliance and security needs.
FAQs
Q. What is HITRUST used for?
HITRUST provides a comprehensive security framework that integrates various standards. It ensures enhanced protection of health information. It also detailed guidelines for organizations to implement effective data security measures.
Q. Is HITRUST for Healthcare?
Yes, HITRUST is designed for healthcare. However, its extensive data security and risk management framework can also be applied in other sectors. Its primary purpose in healthcare is to provide a standardized approach to protecting sensitive health information.
Q. What is the difference between HITRUST and NIST?
HITRUST is a comprehensive framework incorporating aspects of various standards. This includes those from NIST (National Institute of Standards and Technology) for healthcare data security. NIST provides broader cybersecurity guidelines applicable to various industries. HITRUST specifically tailors these guidelines and others to the healthcare sector. It often exceeds the requirements of NIST regarding healthcare-specific risk management.
Q. What is the difference between Hitrust and HIPAA?
Hitrust and HIPAA are two different frameworks for ensuring healthcare data security. HIPAA protects patient data privacy and sets standards for healthcare organizations. Hitrust offers a more comprehensive approach to cybersecurity and risk management.
Q. How does Hitrust CSF differ from HIPAA compliance?
Hitrust CSF (Common Security Framework) is a certification that shows an organization’s compliance with multiple regulations, including HIPAA. HIPAA compliance focuses specifically on healthcare data security. Hitrust CSF provides a broader scope, including other industry standards.
Q. Can Hitrust certification also demonstrate HIPAA compliance?
Achieving Hitrust certification can demonstrate compliance with HIPAA requirements. The framework covers the security and privacy measures needed to meet HIPAA standards.
Q. What is the relationship between HIPAA and Hitrust?
HIPAA is a U.S. law that sets standards for protecting patient health information. Hitrust is known for developing the Hitrust CSF, a framework that helps organizations demonstrate compliance with various regulations.
Q. How does the NIST Cybersecurity Framework relate to Hitrust and HIPAA?
The NIST Cybersecurity Framework provides guidelines for improving cybersecurity measures in various industries, including healthcare. Hitrust incorporates elements of the NIST framework into its own standards. HIPAA compliance may align with NIST recommendations for enhancing data security.
Q. What approach does Hitrust offer for HIPAA compliance?
Hitrust offers a comprehensive approach to HIPAA compliance. It achieves this by providing organizations with the tools and guidelines to implement effective security measures, risk management practices, and regulatory compliance strategies.
Q. How can an organization become Hitrust certified?
To become Hitrust certified, an organization must thoroughly assess its security controls, risk management processes, and compliance with various regulations. The certification process involves audit and validation procedures to ensure adherence to Hitrust standards.