Encryption lies at the heart of data security.
While encryption algorithms and products based on these algorithms have been available since the start of the PC revolution, the idea really took root as the internet went mainstream.
The rise of crime in the digitally interconnected world only highlighted the importance of encryption in securing data and deterring cybercrime.
As a reminder, encryption is the technique of converting data into seemingly meaningless text that an unauthorized individual (or machine) cannot understand.
This article will build on this definition and give you a comprehensive overview of encryption at rest. We’ll also go into the details of the types of encryption at rest and then round off with some best practices when it comes to applying encryption at rest.
However, before going into the details of encryption at rest, it’s absolutely essential that you have a clear understanding of data at rest.
Table Of Content
- What Exactly is Data at Rest?
- What is Encryption at Rest
- Encryption at Rest Vs. In-Transit
- Types of Encryption at Rest
- The Importance of Encryption at Rest
- Best Practises for Encryption at Rest
- Conclusion
What Exactly is Data at Rest?
Data in any digital form maintained on a storage device is referred to as data at rest.
This data is dormant and not transferred between network points or devices. Any application, service, tool, third party application, or employee does not actively use this information.
Now, you should note that “at-rest” isn’t a constant state for data. When a file is requested, the data that makes up the contents of the file immediately travels across a network and transforms into “in-transit” data. A file enters the “in-use” state once something (or someone) starts processing it.
Data at rest can be both structured and unstructured.
Popular Data Storage Options
Here are some examples of places where a company can store data at rest:
- PC and laptop hard drives and SSD drives
- Servers for databases.
- The Cloud, in the case of a third-party colocation facility
- Portable storage and edge-point devices (mobile phones, USBs, tablets, portable HDDs)
- Network-attached storage (NAS)
Hackers often choose to attack data that is at rest. In contrast to individual packets moving through a network, static data storage typically has a logical structure and descriptive file names. Additionally, the most valuable and private information about the business is typically included in data at rest. These data items include:
- Financial records (previous transactions, bank accounts, credit card numbers, and so on)
- Intellectual property (product data, business ideas, schematics, code)
- Contacts
- Marketing data (interactions with users, strategies, directions, leads)
- Data on healthcare
- Personal information about employees and clients
- Data on the supply chain
This kind of data “moves” around, in contrast to data that is at rest, which is static. Companies frequently allow employees to take laptops home, back up drives to off-site facilities, replicate files at rest in virtualized environments, transfer data via portable devices, etc.
A company should use data encryption to defend the confidentiality and security of data while it is at rest.
This brings us to the idea of encryption at rest.
What is Encryption at Rest
Encryption at Rest is a cybersecurity practice of encrypting stored data against unauthorized access.
Encryption scrambles data into ciphertext, and the decryption key is the only means to restore files to their original state.
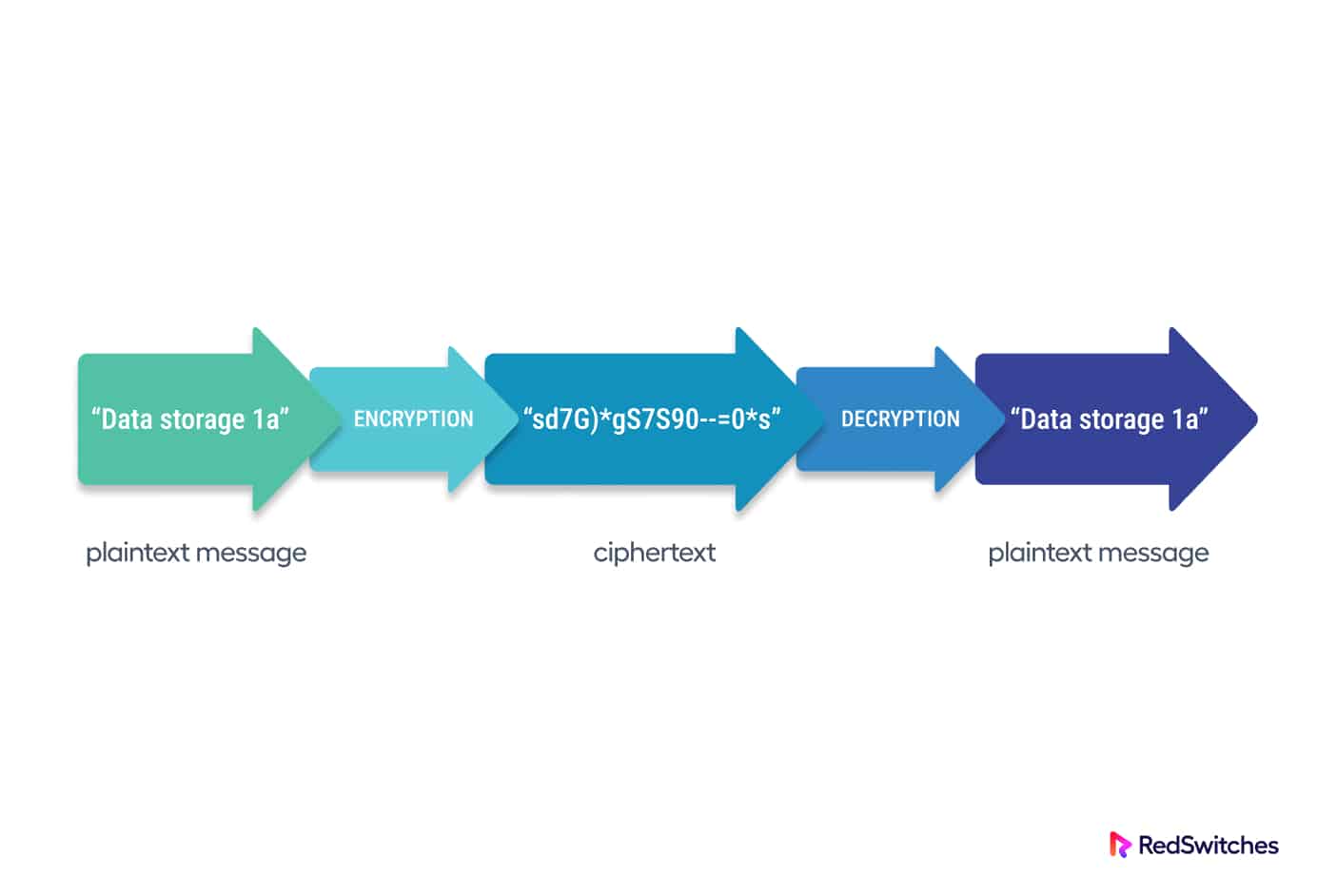
When an unauthorized person accesses encrypted data without the decryption key, the intruder must beat the encryption to decipher the data. This process is far more complicated and resource-intensive than accessing unencrypted data on a hard disk drive.
Encryption at rest is critical to cybersecurity because it prevents stored data from becoming an easy target for hackers. As hackers resort to increasingly sophisticated methods to access and steal data, encrypting data at rest has become a must-have precaution for any security-conscious organization.
Encrypting data at rest is critical for data security, and the practice minimizes the probability of data loss or theft in the following scenarios:
- A data breach has occurred
- Devices have been misplaced or stolen
- Passwords go public
- Permissions were granted by accident
- Leakage of data
Important Encryption Techniques
Most of the time, symmetric cryptography is used for at-rest encryption. In contrast to asymmetric encryption, which uses a public key for data scrambling and a private key for file decryption, symmetric encryption uses the same key to encrypt and decrypt data.
Security teams typically opt for symmetric cryptography when securing data at rest because speed and responsiveness are crucial considerations.
Unfortunately, data encryption is more than just a defensive measure. Criminals utilize cryptography to carry out ransomware attacks, encrypt company data, and force organizations to pay a ransom for the decryption key.
Even with a solid response plan, ransomware attacks frequently result in irreversible data loss, so many organizations invest extensively in ransomware prevention techniques.
Encryption at Rest Vs. In-Transit
While both encryptions in-transit and at rest rely on cryptography to protect data, the two procedures are very different. The key distinctions are shown in the table below:
| Encryption at Rest | In Transit Encryption | |
| Cryptography type | Usually uses symmetric keys to make sure data storage keeps moving along at a reasonable rate. | Typically uses asymmetric keys to provide additional security for data in transit. |
| The primary goal | Safeguard stored static data. | Safeguard data when it travels from one point to another. |
| The primary vulnerability | Data storage holds more helpful information than a single in-transit packet, making these files an appealing target for hackers. | In-transit data files are more vulnerable than at-rest data; you cannot reliably prevent eavesdropping when sending communications over the Internet. |
| How does it work? | Encrypts data until a human (or system) supplies the decryption key required to view the data. | Encrypts messages before transmission; decrypts them when they arrive at the destination. |
The two known encryption types do not compete with one another. To keep corporate data secure, a corporation should rely on both encryption at rest and encryption in transit.
Types of Encryption at Rest
A business can use encryption at rest at four different levels:
Application-level Encryption
The software that edits or generates data also does encryption at client workstations or servers. This encryption type is ideal for tailoring the encryption procedure to each user’s role and rights.
Database Encryption
Businesses can opt to encrypt the entire database (or significant portions of it) to protect critical information.
File System Encryption
An administrator can choose to encrypt specific file systems (or directories within a file system). With this encryption, anyone can boot the device, but accessing the encrypted file system(s) requires additional credentials, such as a second password.
Encryption of the Entire Storage Device
This security approach encrypts all the data on the storage device (usually hard drives).
Full disk encryption is the most secure method of securing data on a device. However, it’s important to note that full disk encryption only works for new storage devices. If you apply it to old devices, there’s a strong chance that the process can wipe the device clean.
The Importance of Encryption at Rest
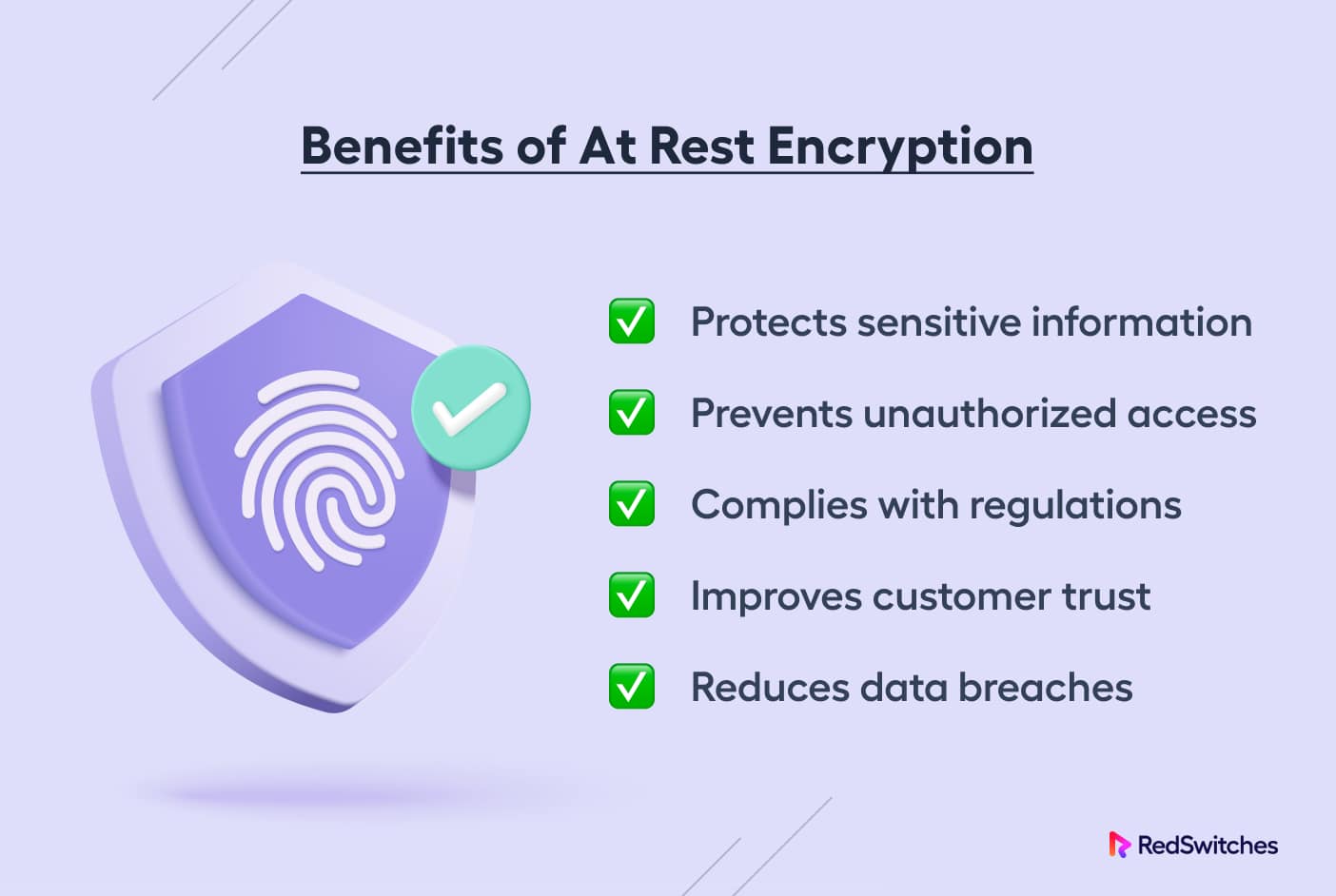
No comprehensive data protection plan is complete without encryption at rest. This is a critical business decision because encrypting valuable at-rest business data:
- Prevents unauthorized access to critical data, whether from within or outside the organization.
- Prevents unauthorized users from quickly identifying, understanding, and copying valuable data.
- Limits the “blast radius” if an attack gets successful.
- Protects the organization if a storage device is stolen or lost.
- Prevents extortion efforts in the aftermath of data theft.
Encrypting data at rest is also a critical requirement for complying with the current regulatory standards. Strong at-rest encryption is required by standards such as PCI & HIPAA.
Best Practises for Encryption at Rest
The best practices for developing, executing, and administering an organization’s encryption at rest strategy are included below.

Mapping and Classification of Valuable Data
You should map your most critical company and customer data before applying encryption at rest (or any other form of security solution). The classification of data varies for every business. However, an appropriate beginning point is to determine the following:
- The importance of every piece of information in your hands
- The digital spot where useful data can be found
- Your organization’s data storage types
- All storage devices’ physical location
- All personnel, applications, and systems with access to sensitive data.
This research establishes which files don’t need as much security and which data needs encryption. With this knowledge, you can begin developing your encryption strategy and coordinating your efforts with the special requirements and use cases of your company.
Data classification is a continuous process that only finishes with the initial assessment. A company’s data sensitivity levels should be re-evaluated regularly, and its encryption strategy should be adjusted accordingly.
Strong Key Management
The reliability and security of your encryption strategy are only as good as your key management. It is critical to keep keys safe throughout their lifecycle (creation, usage, storage, maintenance, and deletion), which is why you should implement the key management best practices listed below:
- Keys should be updated frequently
- Never store encrypted data alongside the associated decryption key
- Use a range of keys for various systems and subsystems
- Store keys on a hardware security module
- Use zero trust security for securing keys
- Never utilizes keys that are already used
- Have reliable key backups and recovery protocols
- Never hard-code your keys
- Centralized encryption management of keys to make operations more secure, effective, and visible.
Configure Confidential Computing
Consider confidential computing if your company uses cloud services and wants to protect data using encryption. This new cloud security model combines at-rest and in-transit encryptions with data in-use security, ensuring end-to-end data security and safety.
Confidential computing decreases the risk of a compromise or leak by encrypting workloads while processing. Among the many advantages of this method are as below:
- Encryption throughout the data lifecycle.
- The attack surface has been reduced.
- Reduced the risk of external and insider threats.
- Improved environmental controls and increased transparency.
- Improved security in multi-cloud environments.
Know When You’re Hitting the “Too Much” Encryption Point
There are more viable solutions than encrypting all data in your organization. Decrypting data requires substantially more time than obtaining plaintext data.
Too much encryption can lead to the following:
- Operations start to get slow.
- Degraded app performance.
- Make simple chores complicated.
- Significantly affect corporate scalability and team agility.
To avoid performance concerns, limit the quantity of data you encrypt.
If a database has non-critical files containing sensitive data, you can use selective encryption of database fields (columns or rows) instead of encrypting the entire data.
Similarly, it would help to be cautious with key sizes, as oversized keys might cause problems. For instance, if you utilize AES symmetric type encryption, there is no need to use the top AES 256 cryptography.
Encrypt Devices with Full Disk Encryption
While file, application, and database-level encryption have their uses, full disk encryption is the safest option in most cases.
Full disk encryption is the most secure strategy because it protects data even if a device containing sensitive information is stolen or lost. If your employer has a Bring-Your-Own-Device (BYOD) policy, full-disk encryption becomes even more important to mitigate the overall risk.
Do Not Underestimate Infrastructure Security
Encryption at rest is only as safe as the infrastructure that enables it. Assure that the team does proper patching for:
- Servers.
- Services for networking (IP addressing, satellite, DSL, wireless protocols, and so on).
- System software.
- Network software (both on-premises and cloud-based).
- Network security applications.
- Firewalls.
Conclusion
Encryption at rest is an essential and much-needed security measure that should be implemented to protect sensitive data. It can help prevent data breaches, unauthorized access, and data theft. However, it should be used in connection with other security measures to ensure a comprehensive security solution.
A business can utilize data encryption at rest to reduce the possibility of data loss and minimize the impact of security incidents. As such, encryption at rest, in-transit, and in-use encryption should be the cornerstone of any cybersecurity approach.
FAQ:
Q: Is data encryption at rest sufficient to assure data security?
While encryption at rest is an important security measure, it should be used with other security measures, such as firewalls, access controls, and intrusion detection systems, to ensure complete data security.
Q: What impact does encryption at rest have on system performance?
Answer: Encryption at rest can impact system performance, particularly data access and retrieval. On the other hand, modern encryption algorithms have been optimized to minimize performance consequences.
Q: How can I ensure that my data is safe, secured in transit, and encrypted at rest?
Answer: Encryption can ensure your data is encrypted at rest. Many modern operating systems and devices include encryption features that can be turned on to protect data in transit.