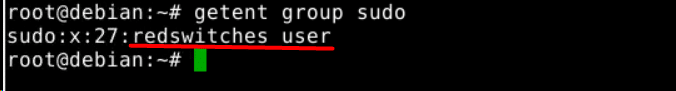IT administrators sometimes need privileged access to specific OS and system areas to perform upgrades, apply patches, and carry out system modifications.
Unix-based systems have a superuser account that offers unrestricted access to the system. Superusers can alter every part of a system and change user access and privileges.
The downside of this freedom is the possibility of abuse in the event of the compromise of the superuser credentials. Any malicious user with superuser access can wreak havoc on the system and significantly damage system operations.
Linux offers a great solution to this challenge.
A sudo user account is a regular user account that can perform specific administrative tasks using the sudo command. It gives users in the sudo group exclusive access to specific areas of the system (that are often restricted to normal users) and can prevent users from tampering with sensitive data.
In this tutorial, we will discuss the idea of sudo accounts. More specifically, we will describe the steps in the process of creating a sudo account in Debian-based Linux distributions.
Let’s start with a quick look at the features of a sudo account.
The Core Features of Sudo User Accounts
Before learning how to create sudo accounts, you should first learn about the features that make these accounts an integral part of Debian system operations.
Permission Management
Adding users to the sudo group can help you better manage system security by controlling which users can perform certain actions requiring administrative capabilities.
Temporary Privilege Elevation
Users can use the sudo command to temporarily execute particular commands or actions with elevated administrator capabilities without maintaining a continuous administrative login (a critical security vulnerability in Linux systems).
Granular Control
By making changes to the configuration of the sudoers file, admins can grant varying sudo capabilities to specific users. As a result, admins gain very fine-grained control over system resources and functionality.
Logging and Auditing
Every time the sudo command is used, the system records it, tracking users who executed the commands. This makes system activity tracking and auditing easier.
Create a Debian Sudo User
Creating a Debian sudo user involves a few steps.
Note that you don’t necessarily need to alter the sudoers file to create the sudo user. Additionally, if you have an existing user for whom you want to grant sudo privileges, you can skip step #2.
Step #1: Log in as a Root User
Before adding a new user to the sudo group, log in to your system as the root user. We recommend the following SSH command:
# ssh root@ip_address
Here, replace ip_address with your server’s IP address. The system will ask you for your password.
Step #2: Add a New Debian User
At this point, we will use the adduser command to create a new user.
# adduser username
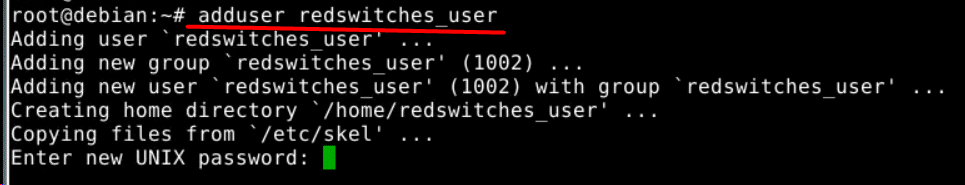
For instance, run the following command to add a new account named redswitches_user:
# adduser redswitches_user
The output will be:
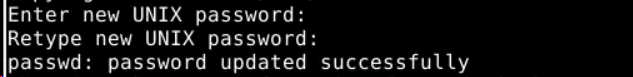
The command copies the required files and sets up the user’s home directory. Following this, the system prompts you to set up a new user account password. Enter the password and confirm it.
Remember that for accounts with sudo access, we strongly recommend following the best practices for strong passwords.
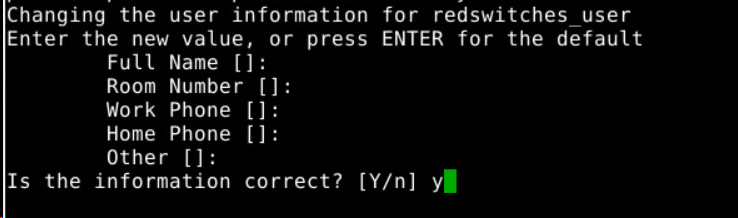
The command will also prompt you to update the user details, such as an associated email address. Optionally, you can press Enter to leave the fields empty and fill in the details later.
Step #3: Add the User to the Sudo Group
The final step is to add a user to the sudo group. Members of the sudo group have root capabilities. In Debian distributions, such as Ubuntu, all group members have automatic sudo access.
Start by including a user in the sudo group with the following command:
# usermod -aG sudo username
Here,
- usermod alters the user account.
- -aG flags assign the user to a certain group. The -a option adds the user to the group without being removed from the other ones. The -G option specifies the group to which to add the user. Note that these flags are always compatible in this situation.
- sudo specifies the group to which the user is being added.
- The user account you wish to add to the sudo group is the username.
We recommend confirming the details by using the following getent command to get the details of the sudo group:
# getent group sudo
As you can see from the output of the command on our test system, the user redswitches_user is included in the sudo group.
We have covered the idea and processes associated with working with the sudoers file in a comprehensive tutorial.
Verify Sudo Access
Once you’ve added the user to the sudo group, you should always verify their sudo access.
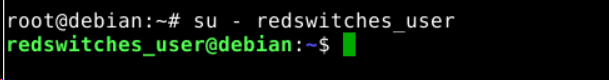
Use the su command to switch to the user account you just created, replacing the username with the user’s name:
# su - username
Enter the password if prompted by the command.
Run any command that needs sudo privileges. Alternatively, you can run the id command to print the list of groups the user belongs to.
Using Sudo
To execute a command with root privileges, type sudo followed by the desired command.
For instance, to get details of the root directory using the ls utility, run:
# sudo ls -la /root
The command will ask for your password. Once verified, the command will display the contents of the root directory in the terminal.
Note: Use sudo cautiously, especially for critical system commands. Once you are verified as a sudo user, the system will execute your commands without further verification, unless there’s a significant time gap between the sudo commands.
Conclusion
Setting up a sudo user on Debian offers a quick and safe solution to give trusted users administrative access without compromising system integrity. Users can guarantee the safe and efficient completion of crucial administrative activities by adhering to the guidelines provided in this comprehensive guide.
Empower your system management with Redswitches, your trusted global dedicated hosting provider.
At RedSwitches, we’re dedicated to helping you discover the perfect server solutions to drive your business to new heights. So, if you’re looking for a robust server, we offer the best-dedicated server pricing and deliver instant dedicated servers, usually on the same day the order gets approved. Whether you need a dedicated server, a traffic-friendly 10Gbps dedicated server, or a powerful bare metal server, we are your trusted hosting partner.
Leverage our trusted services to experience seamless collaboration and enhanced security measures on Debian systems. Elevate your administrative privileges and streamline your operations today with Redswitches.
FAQs
Q. What is a sudo user?
A regular user account on Debian that can run administrative commands using the sudo command is known as a sudo user.
Q. Why create a sudo user?
Creating a sudo user allows you to delegate administrative tasks to trusted users while maintaining control over system security.
Q. How do I create a new user on Debian?
With the adduser command, a new user can be established. For instance, run, #sudo adduser username
Q. How do I add a user to the sudo group?
The command sudo usermod -aG sudo username can be used to add a user to the sudo group.
Q. How do I grant sudo privileges to a user?
By default, Debian grants sudo privileges to users of the sudo group. After being assigned to the sudo group, a user can use sudo to run administrative commands.
Q. Can I customize sudo privileges for a user?
Using the visudo command, you can alter the /etc/sudoers file to change the sudo rights. When making changes to this file, exercise caution to prevent unexpected outcomes.
Q. Are there any security considerations when creating a sudo user?
Yes, granting sudo privileges only to trusted users and restricting access to sensitive administrative commands is essential. Regularly review sudo access permissions to ensure proper security measures are in place.
Q. Can I revoke sudo privileges from a user?
Yes, you can revoke a user’s sudo privileges by removing them from the sudo group or modifying their permissions in the /etc/sudoers file.
Q. Can I create multiple sudo users on Debian?
You may use the same procedure to establish several sudo users on Debian.
Q. What if I encounter issues when creating a sudo user?
If you encounter any issues, refer to the Debian documentation or seek assistance from the Debian community for troubleshooting steps and solutions.